How to identify hash types
There is a large number of hash types. Some of them are universal and are used by a wide range of applications, for example, MD5, SHA1, CRC8 and others. Some hashes are used only in certain applications (MySQL, vBulletin) and protocols.
In addition to popular hashes, developers can use different combinations of universal hashes (for example, compute an MD5 hash and then send the result string to SHA1 function), or iterated hashes (for example, MD5 hash is calculated for the password, then the MD5 hash is recalculated for the result string, then MD5 is calculated for the next result string and so on a thousand times).
With regard to the cracking, sometimes a string or a file that is formed in a certain way is called a hash. This hash is not used by the target application, but it was calculated from the source data and it allows you to crack the password of the target file or protocol.
An example of such a line for WinZip: $zip2$*0*3*0*b5d2b7bf57ad5e86a55c400509c672bd*d218*0**ca3d736d03a34165cfa9*$/zip2$
Example of a hash file for hacking VeraCrypt password PBKDF2-HMAC-RIPEMD160 + AES: https://hashcat.net/misc/example_hashes/vc/hashcat_ripemd160_aes_13711.vc
Usually a penetration tester knows the source of a hash and he knows its type. But there are exceptions. In this situation, it is necessary to ‘guess’ what kind of hashes we got.
This can be done by comparing a source hash with samples. Either based on the number of characters and the character set used.
You can also use tools that greatly accelerate this process. Programs to identify the type of hash are hashID and HashTag.
hashID
By default, this program is already installed in Kali Linux. It identifies the different types of hashes used to encrypt data, primarily passwords.
hashID is a tool written in Python 3, it supports the identification of more than 220 unique types of hashes via regular expressions.
Using the program is very simple:
hashid hash_to_identify
A couple of important remarks:
- a hash is always better to specify in single quotes (and not without quotes and not in double quotes)
- there is an option -m, which displays information about the Hashcat mode
Hashcat hash modes is a hash type that you must specify with the -m/--hash-type option,.
hashID usage:
hashid.py [-h] [-e] [-m] [-j] [-o FILE] [--version] INPUT
hashID options
positional arguments:
INPUT input to analyze (default: STDIN)
options:
-e, --extended list all possible hash algorithms including salted
passwords
-m, --mode show corresponding Hashcat mode in output
-j, --john show corresponding JohnTheRipper format in output
-o FILE, --outfile FILE write output to file
-h, --help show this help message and exit
--version show program's version number and exit
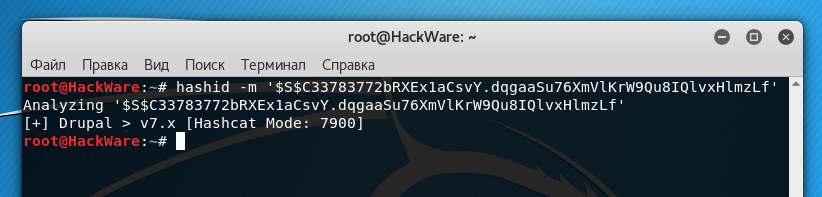
For example, I need to identify a hash $S$C33783772bRXEx1aCsvY.dqgaaSu76XmVlKrW9Qu8IQlvxHlmzLf:
hashid -m '$S$C33783772bRXEx1aCsvY.dqgaaSu76XmVlKrW9Qu8IQlvxHlmzLf'
As you can see from the screenshot, it's Drupal> v7.x in Hashcat to crack this hash, you need to specify 7900 mode.
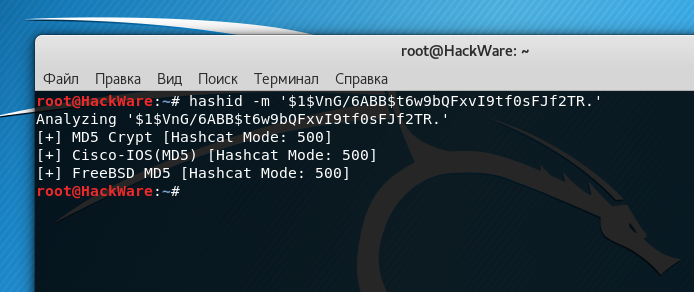
Identify the hash $1$VnG/6ABB$t6w9bQFxvI9tf0sFJf2TR.:
hashid -m '$1$VnG/6ABB$t6w9bQFxvI9tf0sFJf2TR.'
We get several options at once:
MD5cryp is an algorithm that calls a thousand times the standard MD5, to complicate the process.
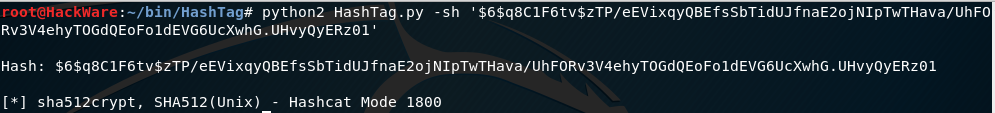
Another hash $6$q8C1F6tv$zTP/eEVixqyQBEfsSbTidUJfnaE2ojNIpTwTHava/UhFORv3V4ehyTOGdQEoFo1dEVG6UcXwhG.UHvyQyERz01:
hashid -m '$6$q8C1F6tv$zTP/eEVixqyQBEfsSbTidUJfnaE2ojNIpTwTHava/UhFORv3V4ehyTOGdQEoFo1dEVG6UcXwhG.UHvyQyERz01'
The program says it's SHA-512 Crypt - i.e. SHA512 (Unix).
HashTag
HashTag is a python tool that parses and identifies various password hashes based on their type. HashTag supports the definition of more than 250 hash types and maps them to more than 110 hashcat modes. HashTag is able to identify a single hash, parse a single file and determine the hashes inside it or traverses a directory and all subdirectories to look for potential hash files and identify all the hashes found.
Therefore, it is similar to the previous program.
By default in Kali Linux it is missing, so you need to download it:
git clone https://github.com/SmeegeSec/HashTag.git cd HashTag/ python2 HashTag.py -h
A hash for HashTag also need to be placed in single quotes. You need to write a hash after the -sh option. But modes are displayed without additional options.
HashTag usage:
HashTag.py {-sh hash |-f file |-d directory} [-o output_filename] [-hc] [-n]
HashTag options
optional arguments:
-h, --help show this help message and exit
-sh SINGLEHASH, --singleHash SINGLEHASH
Identify a single hash
-f FILE, --file FILE Parse a single file for hashes and identify them
-d DIRECTORY, --directory DIRECTORY
Parse, identify, and categorize hashes within a
directory and all subdirectories
-o OUTPUT, --output OUTPUT
Filename to output full list of all identified hashes.
Default is ./HashTag/HashTag_Output_File.txt
-hc, --hashcatOutput Output a separate file for each hash type based on
hashcat modes
-n, --notFound --file:Include unidentifiable hashes in the output
file.
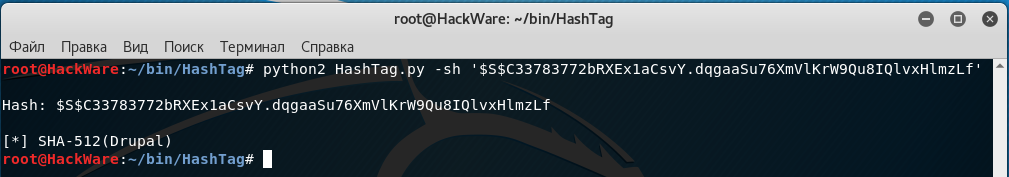
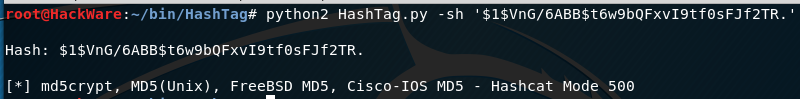
Let's identify the same hashes:
python2 HashTag.py -sh '$S$C33783772bRXEx1aCsvY.dqgaaSu76XmVlKrW9Qu8IQlvxHlmzLf'
python2 HashTag.py -sh '$1$VnG/6ABB$t6w9bQFxvI9tf0sFJf2TR.'
python2 HashTag.py -sh '$6$q8C1F6tv$zTP/eEVixqyQBEfsSbTidUJfnaE2ojNIpTwTHava/UhFORv3V4ehyTOGdQEoFo1dEVG6UcXwhG.UHvyQyERz01'
As you can see, the results are similar.
Example hashes
A large number of classic hashes, as well as hashes, specially designed for hacking passwords and hash files you can find here.
On that page you can:
- try to identify your hash by samples
- find an error in the compiled hash for hacking a password, comparing it with the correct format
- check the work of the hash identification programs
The hashID and HashTag programs do not always correctly identify the hash (at least in the obvious errors hashID is noticed).
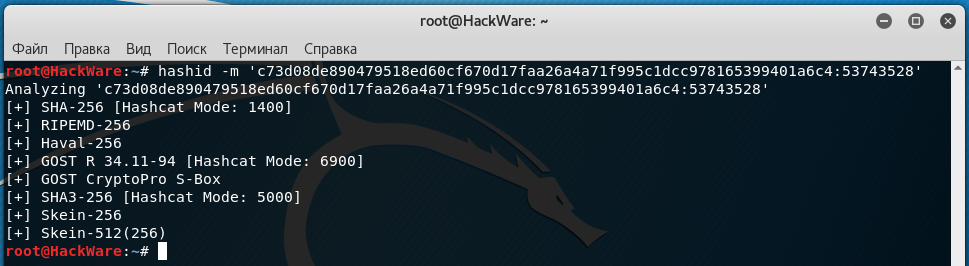
For example, I'm interested in a hash c73d08de890479518ed60cf670d17faa26a4a71f995c1dcc978165399401a6c4:53743528:
hashid -m 'c73d08de890479518ed60cf670d17faa26a4a71f995c1dcc978165399401a6c4:53743528'
I got:
This is obviously an erroneous result, since the salt after the colon was discarded when the hash was identified.
python2 HashTag.py -sh 'c73d08de890479518ed60cf670d17faa26a4a71f995c1dcc978165399401a6c4:5374'
We get a more correct result:
In fact, this is sha256($pass.$salt).
Online hash identification service
The methods of identifying the hash type described above is implemented as a free online service on SuIP.biz: https://suip.biz/?act=hashtag
Related articles:
- How to identify hash types – new tools with modern hashes support (98.1%)
- Hash-generation software (54.8%)
- How to hack a Windows password (54.8%)
- How to decrypt stored Windows passwords using mimikatz and DAPA (54.8%)
- Comprehensive Guide to John the Ripper. Part 6: How to brute force non-standard hashes (54.8%)
- Programs for generating wordlists (RANDOM - 52%)