How to find out the real IP of a site in Cloudflare
Cloudflare is an intermediate between a user and a site. It operates on the principle of reverse proxy, providing additional services, including page caching, protection from DDoS, and protection from bad bots and so on. In addition, Cloudflare hides the real IP address of the server on which the site is hosted.
Cloudflare uses its name servers to resolve DNS requests and convert a host name to an IP address. It works as follows: a site owner configures his domain to use of the Cloudflare Name Servers. They response to DNS requests sending IP belonging to the Cloudflare network. As a result, the request to the site come to Cloudflare, which receives a page from the server where the site is hosted (or from cache) and serve this page to the user who requested it. As a result, the true IP address of the site behind Cloudflare becomes well hidden.
If Cloudflare is configured correctly, then the real IP address of a site is never disclosed and is not recorded anywhere; but how much do you know of people who always do the right thing? For this reason, there are tools that look for holes in your Cloudflare settings. One such program is CloudFail, and this note is devoted to it as well as other methods to find out the hidden IP address.
What is and how CloudFail works
Each site can have subdomains like *.site.com. Where instead of an asterisk different values can be substituted, for example:
- www.site.com
- th.site.com
- forum.site.com
- test.site.com
- admin.site.com
- 111.site.com
- chat.site.com
Such subdomains can be an unlimited number. An important point: each such subdomain can have its own IP address!
That is name servers allow ones to specify IP (or several addresses at once) for site.com, another IP for test.site.com, another IP for th.site.com and so on.
There can be a situation when site.com has IP address of Cloudflare in the DNS records, but test.site.ru has another IP address that is not protected by Cloudflare.
Therefore we get an IP address, which
- can be a real IP address of the site;
- is the IP address of only the subdomain, but gives us information about the owner or a hint for further research.
We cannot just get a list of all the subdomains. Therefore, we need to try the various options. This is what is implemented in CloudFail:
- different versions of subdomains are tried;
- if there is a DNS record for a subdomain, then we get an IP for it;
- it checks whether the received IP is included in the Cloudflare range (that is, it is protected by Cloudflare or not).
In fact, the described process is already the third stage. In the first stage, CloudFail gets a list of possible subdomains from DNSDumpster.com and checks them.
At the second stage, CloudFail accesses the CrimeFlare service, which collected a large IP database for sites protected by Cloudflare. If an IP is known for the site, it is immediately displayed. About CrimeFlare in more detail here.
And in the third stage, the described dictionary attack is performed.
As a result of such an integrated approach, it is often possible to find IP addresses that are not protected by Cloudflare.
It is important to note that we proceed from the assumption that the IP addresses of subdomains belong to or are associated with the owner of the main site. Yes, this is usually true, but you always need to remember that in the DNS records of subdomains, the owner of the main domain can specify ANY IP addresses that do not even belong to him …
How to install CloudFail
To install CloudFail in Ubuntu, Kali Linux, Debian, Linux Mint and their derivatives, run the following commands:
sudo apt update sudo apt install python3-pip git tor git clone https://github.com/m0rtem/CloudFail cd CloudFail/ sudo pip3 install -r requirements.txt
To verify that CloudFail is running, run the following command:
python3 cloudfail.py -h
Before the first launch, and also from time to time (about once a month), it is recommended to update the databases:
sudo python3 cloudfail.py -u
The list of Cloudflare IP addresses will be updated, as well as the CrimeFlare database containing known IP addresses for some sites.
If you want the program to work through the Tor network, you need to start the Tor service:
sudo systemctl start tor
If you do not need Tor to send requests, then this step can be skipped.
If you want, you can add the Tor service to startup (then you will not need to run this service after each reboot of the computer):
sudo systemctl enable tor
How to use CloudFail
The program has only one mandatory -t option, after which you must specify a domain name.
Additionally, you can use the --tor option to make requests through this network.
A list of words (a subdomains.txt file) is already supplied with the program for searching possible subdomains performing the dictionary attack. If you want to use your custom dictionary, specify it using the -s option. The dictionary file must be located in the data folder.
For example, if we want to get data for the anti-malware.com site, then the launch command looks like this:
sudo python3 cloudfail.py -t anti-malware.ru --tor
Analysis of CloudFail results
The is part of the Cloudflare network! string says that the site is protected by the Cloudflare network. If this were not so, then the scan would be stopped here, because it is meaningless.
The Testing for misconfigured DNS using dnsdumpster… string indicates the beginning of the first stage – obtaining the known hosts (subdomains) associated with the analyzed site. This data is taken from dnsdumpster, which, in turn, collects them from a variety of sources (crawls of the Alexa Top 1 Million sites, search engines, popular crawlers, Certificate Transparency, Max Mind, Team Cymru, Shodan and scans.io). However, brute-force attack of subdomains are not used.
As you can see, in our results, among the DNS records, we found MX records that point to mail servers. Note that in this case MX records do not point to the subdomains of the target site, but to Google hosts. These hosts are not protected by Cloudflare, but they are not suitable for open source research to find a real server's IP. We can only conclude that the site uses email based on Google's mail services.
The Scanning crimeflare database… string indicates the beginning of the second stage - a search on the database of sites with known IP from CrimeFlare.
The Did not find anything. Inscription says that nothing has been found in this database.
The Scanning 2897 subdomains (subdomains.txt) line, please wait… line indicates the beginning of the third stage - a search of possible subdomains by the dictionary.
The red line contains information about the found subdomains, but their IP is protected by the Cloudflare network - hence, they are useless for determining the hidden IP (but can be used for other purposes).
The green lines indicate that the IP of the host found is not owned by Cloudflare. Therefore, it can be a real IP of the site that interests us.
An example of a string from our case is mail.anti-malware.ru, unfortunately, the found IP again belongs to Google.
But the test.anti-malware.ru line leads us to success - it's an IP VPS server.
Searching for sites on the same IP confirms that this is the real IP of the domain we are interested in.
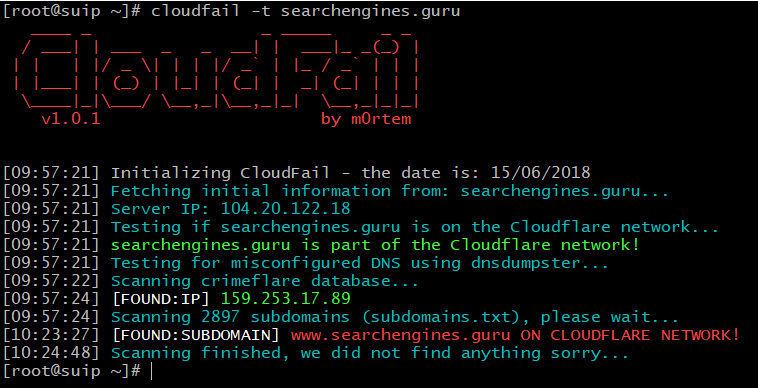
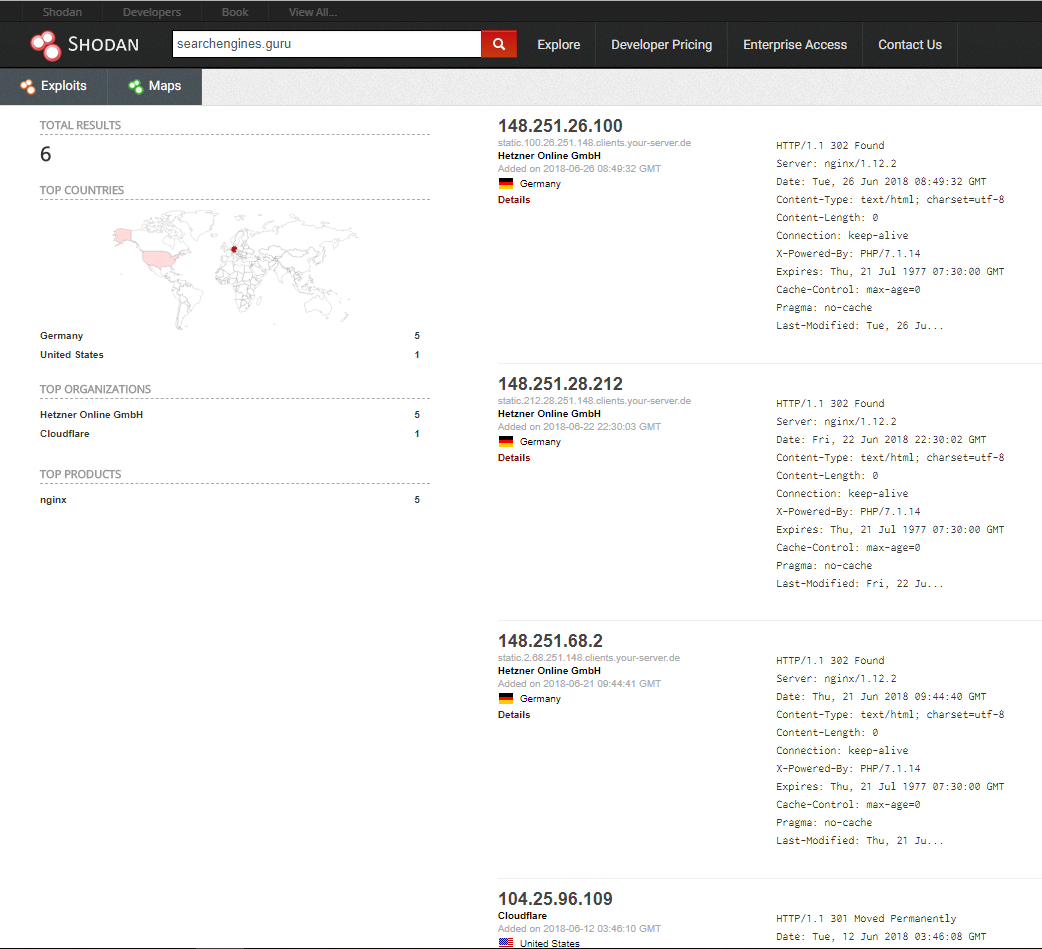
The next example of the scan is the site searchengines.guru.
The results are as follows:
They say that the first and third stages have not yielded results. But in the database CrimeFlare found the real IP of this site, this is 159.253.17.89.
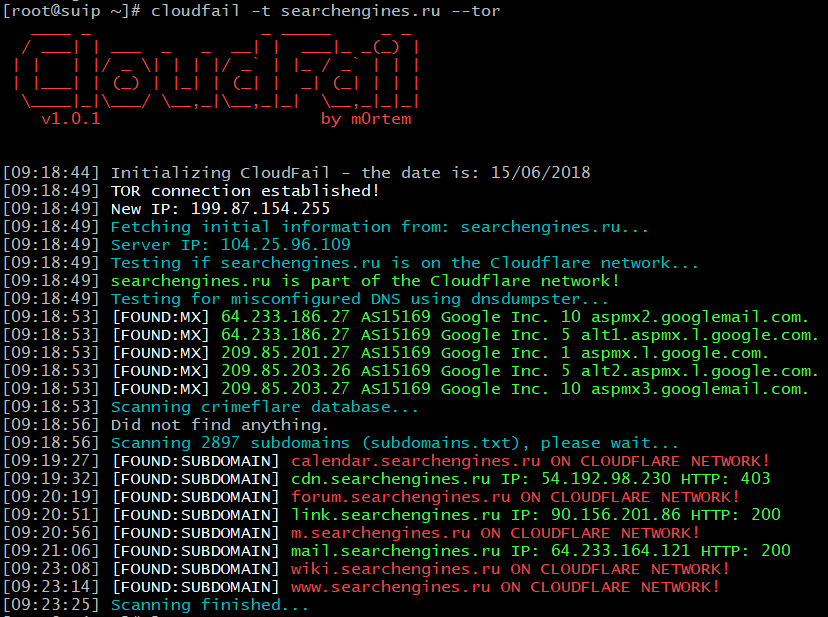
Scanning searchengines.ru:
At the first stage, only Google's mail servers were found. The site was not found in the CrimeFlare database.
In the third stage, the following good data:
[09:19:32] [FOUND:SUBDOMAIN] cdn.searchengines.ru IP: 54.192.98.230 HTTP: 403 [09:20:51] [FOUND:SUBDOMAIN] link.searchengines.ru IP: 90.156.201.86 HTTP: 200 [09:21:06] [FOUND:SUBDOMAIN] mail.searchengines.ru IP: 64.233.164.121 HTTP: 200
mail.searchengines points to the IP of the Google mail server.
cdn.searchengines.ru has an IP address of CloudFront, it is one of Cloudflare services, i.e. it also does not suit for us.
But link.searchengines.ru has an IP address (90.156.201.86) of a third-party server. You can open the page link.searchengines.ru - there is some forgotten, apparently, for many years not used online service. This IP can be the address, including, searchengines.ru. In any case, this IP is connected with the owners of searchengines.ru, even if this host itself is on another server.
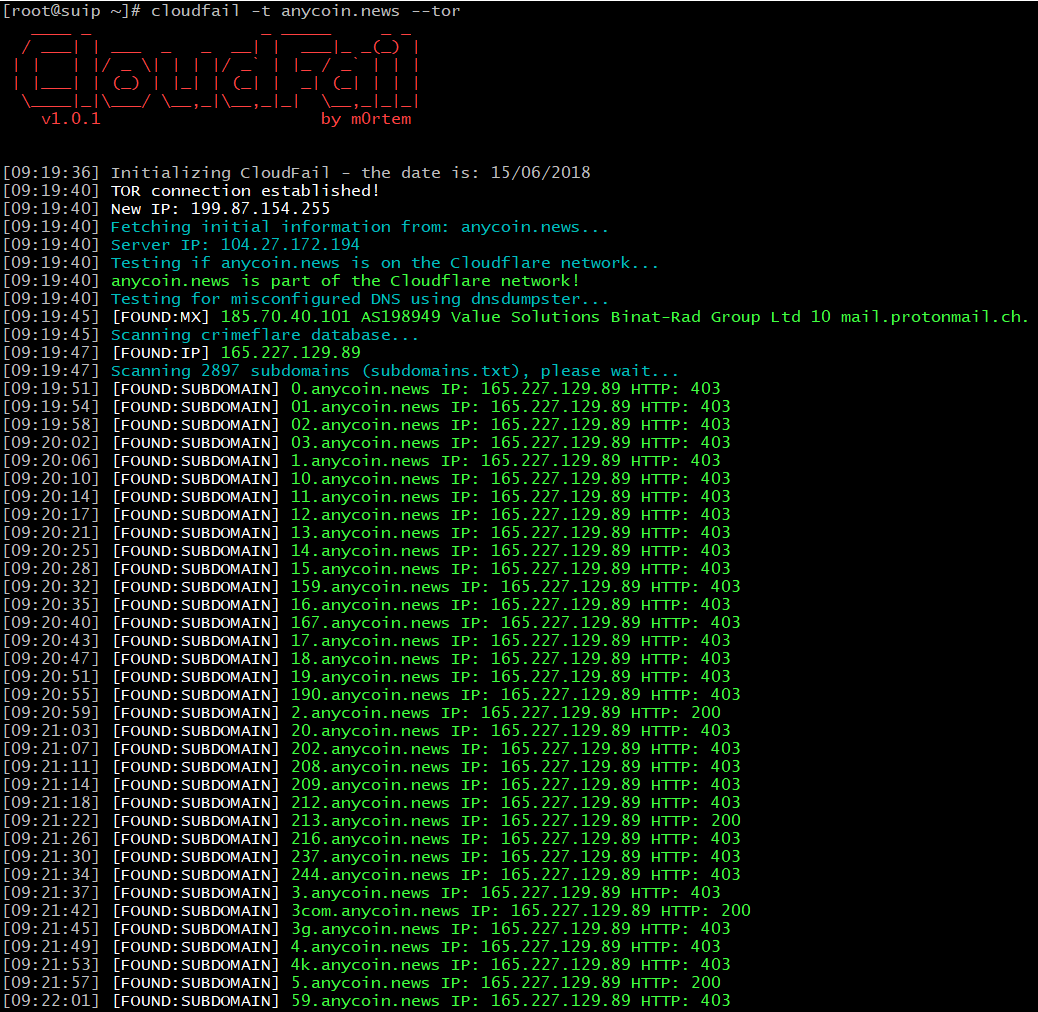
Scanning anycoin.news
Results:
Found an IP in the CrimeFlare base. On the same IP (165.227.129.89) there are a lot of subdomains; probably these subdomains do not exist, but because of the DNS configuration features (using wildcard characters), each requested subdomain is resolved to a real server’s IP.
In this case, Google mail servers are not used, but the services of another service - protonmail are used. Therefore, IP 185.70.40.101 does not give us useful information.
Scanning codeby.net
Results:
This domain has very interesting MX records:
[FOUND:MX] 46.8.158.106 Russian Federation 10 mail.codeby.net [FOUND:MX] 46.8.158.106 Russian Federation 20 mail.codeby.net.
The IP address 46.8.158.106 cannot only be a real server address. But it gives us very interesting information about the Internet service provider:
And whois gives us his address and phone number.
The subdomain found is also useful:
[FOUND:SUBDOMAIN] market.codeby.net IP: 186.2.167.150 HTTP: 200
It contains information about another possible true IP of the site - 186.2.167.150. In any case, this IP is relevant to the owner of the site of interest.
Online service to find out the current IP address of a site for Cloudflare
CloudFail is implemented online, its address: https://suip.biz/ru/?act=cloudfail
Report example: https://suip.biz/ru/?act=report&id=84f16c83f45bcd9a42a16197ee9c2089
Analysis of IP addresses history change
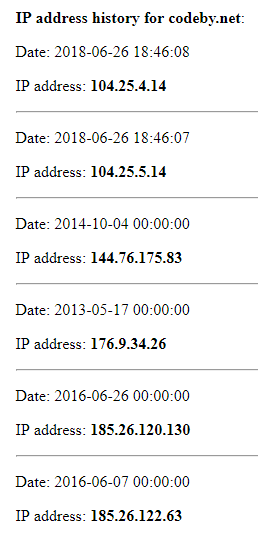
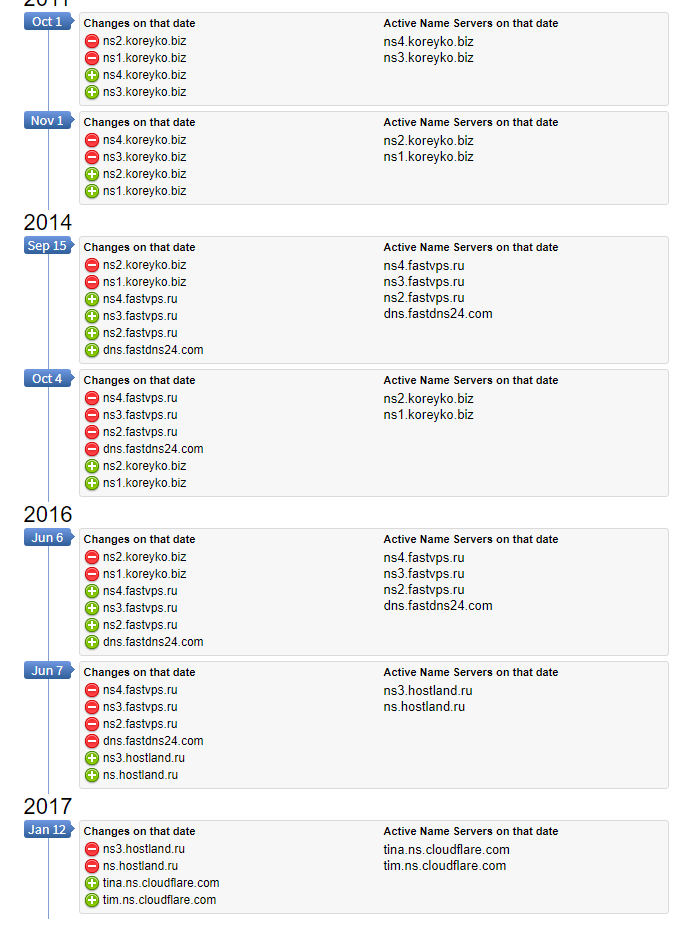
Sometimes a website after creation works for a while directly and only later starts using Cloudflare. In this case, it is likely that numerous IP change history storage services contain information about the source IP address of the site.
On the screenshot an example of the service: https://suip.biz/?act=domainiphistory
Examples of services that have their own databases:
- https://securitytrails.com/dns-trails
- https://dnshistory.org/dns-records/
- http://whoisrequest.com/history/
- http://ptrarchive.com/
VirusTotal data based service:
Search by specialized search engines
Look at the example of searching results for the searchengines.guru domain by shodan.io:
Found several servers on the same subnet.
The fact is that when you request these servers via IP, they redirect to the site of interest to us:
Location: https://searchengines.guru
That is, we did not just find one IP address, we immediately identified all the servers used, apparently, for load balancing.
Revealing an IP address from a previously used name servers
When a site hides behind Cloudflare, it starts using Name Server owned by Cloudflare. However, if the site has a history of work before connecting to Cloudflare, then earlier it used other name servers, for example, of its hosting provider.
If you make a request to these previous name servers, then there is a chance to get the IP address of the site that it names at the time of using these name servers.
To search for previously used nameservers (NS) by the site, you can use the following services:
- https://securitytrails.com/dns-trails
- http://whoisrequest.com/history/
- https://dnshistory.org/
- http://www.whoishistory.ru/ (for .ru, .su and .рф domains)
Then you need to run a command like this:
dig @old_name_server domain
Where it is necessary to enter the domain of interest and its old_name_server which was received for it.
For example, for the domain codeby.net, its previous name server ns.hostland.ru,
then the command will look like this:
dig @ns.hostland.ru codeby.net
As a result, an IP address is obtained, which can be the hidden address of the web server on which the site is hosted.
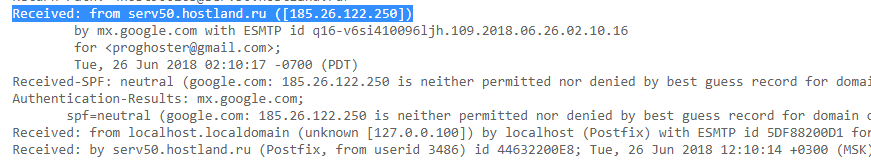
Extracting hidden IP address from email headers
If there is an opportunity to initialize sending a letter from the target site to your mail (confirmation of registration/order/subscription, request for support, etc.), then analyze the email headers (in particular, Recieved:) of the original letter. There is a possibility that the letter contains the real IP address of the server:
IP address disclosure by HTTP request from the target web site
Even more exotic option, but do not miss it. Explore the ability to initialize a request to upload a file to a site of your interest from a remote address. Example: uploading an image (avatars, screenshots) via the link to a remote website. If possible, upload the file to your server (hosting) and after its request it from the target site, examine the logs of your web server - there must be a real IP of the target site.
How to verify whether the found IP address belongs to the site of interest
The easiest way is to enter IP into the address bar of your web browser - there is a chance that you will see the target site. However, this method may not work because the web server is configured to ignore requests that do not contain the correct host name, or multiple sites are hosted on the same web server.
This problem can be circumvented using curl. The curl utility retrieves the source code for a website's web page, while it allows you to send requests with a custom header that you must specify after the -H option.
To query a particular host with curl, the command looks like this:
curl -H "Host: HOST NAME" IP
Where it is necessary to replace the HOST NAME with a real name, and IP - with the IP address of the server to which the request is sent.
For example, I want to check on the server with the address 185.117.153.79, whether there is a host suip.biz, then the command looks like this:
curl -H "Host: suip.biz" 185.117.153.79
Examine the received HTML code - this can be the page of the desired host, or simply information that there is no such host on this server, or even something else.
If you want to connect via HTTPS, simply add the prefix "https://" before the IP address. Also use the -k option, which means "allow unsecured connections" - that is, the data will still be received, despite the problems with the SSL certificate. Such problems can arise just due to the fact that the certificate is issued for a specific host name, but we make a request to the IP address, i.e. host names do not match.
The command will look like:
curl -H "Host: HOST NAME" -k https://IP
For my example:
curl -H "Host: suip.biz" -k https://185.117.153.79
How to configure Cloudflare properly so that it is impossible to find out the real IP of a site
As you can see from the examples above, incorrect DNS configuration leads to the disclosure of hidden site’s IP, even if it is protected by Cloudflare. It is necessary that all hosts that are related to the site be protected by the Cloudflare network. The same applies to wildcard characters in DNS records - such records should not reveal the true IP address of the site.
It is necessary to remember about the possibility of disclosing the owner through the hosts used by the site of mail servers.
The site itself should not contain vulnerabilities that allow an attacker to conduct attacks in other areas.
Related articles:
- How to find out if a site is behind CloudFlare or not (100%)
- How to bypass Cloudflare, Incapsula, SUCURI and another WAF (100%)
- Revealing the perimeter (CASE) (96.8%)
- How to find out all sites at an IP (59.9%)
- How to see locked HTML code, how to bypass social content lockers and other website info gathering countermeasures (59.9%)
- Tor tips and usage examples (RANDOM - 3.6%)





That was awesome and helped me
Thanks