WiFi-Pumpkin: Rogue Wi-Fi Access Point Attack with GUI and rich functionality
The purpose of attacks with a rogue access point is not WPA passphrase (password of a Wi-Fi network). The attack targets to the transmitted network traffic, which can contain web site login passwords and another sensitive information. An attacker is able to perform Man-In-The-Middle attacks to extract important data.
Configuring Rogue Access Point is to configure an open wireless access point. It is the same as to set up a Wi-Fi hotspot. But usual Wi-Fi hotspot turns in Rogue Access Point when an attacker starts Man-In-The-Middle attacks.
There are programs that automate the process of creating configuration files for a wireless access point, and also provide the proper traffic routing. For example, it can do create_ap.
The same actions, but across with launching a man-in-the-middle attack, are performed by the mitmAP program.
WiFi-Pumpkin is another program for automatic setting up a wireless rogue access point. Its feature is the graphical interface, which further simplifies the Rogue Wi-Fi Access Point Attack.
The program has built-in plug-ins (other programs) that collect data and perform various attacks.
To install WiFi-Pumpkin in Kali Linux:
git clone https://github.com/P0cL4bs/WiFi-Pumpkin.git cd WiFi-Pumpkin chmod +x installer.sh sudo ./installer.sh --install
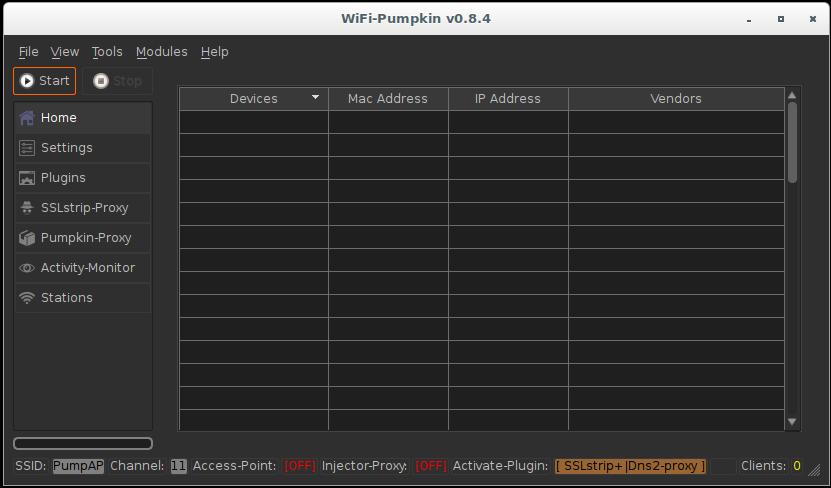
How to start and configure WiFi-Pumpkin
To launch the tool type:
wifi-pumpkin
Note that when you try to start from a normal user (not root), the program does not work.
After the launch, this interface opens:
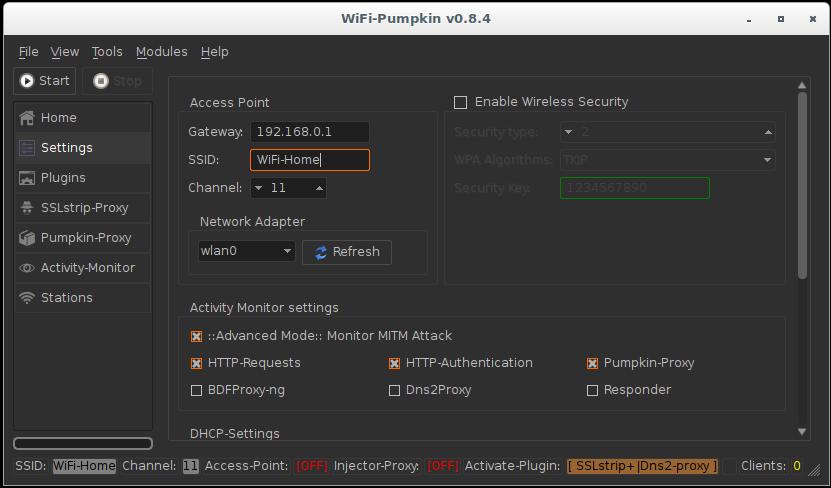
Go to the settings and change the name of the access point (I chose WiFi-Home):
In Activity Monitor settings I set the checkboxes for HTTP-Requests, HTTP-Authentication (credentials from web sites) and Pumpkin-Proxy.
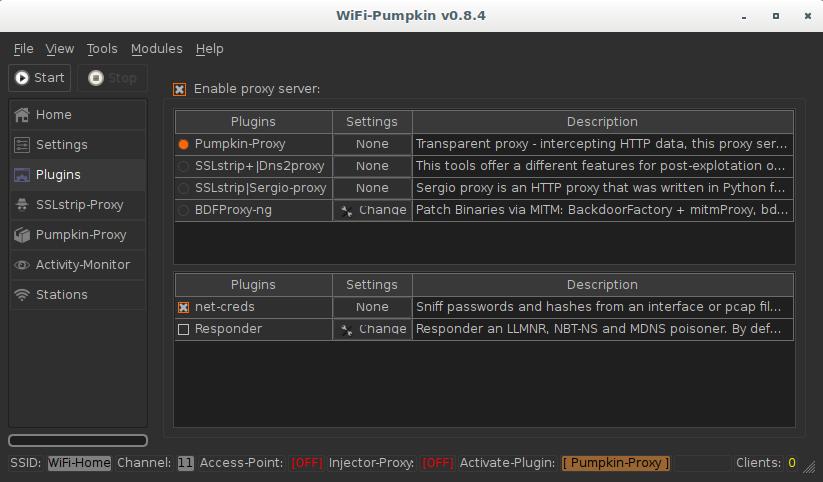
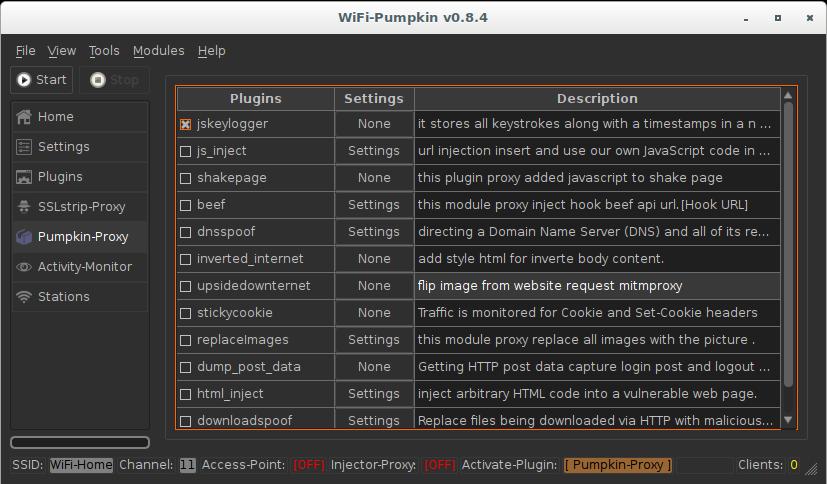
In the Plugins tab, select what is more important to you. Pumpkin-Proxy allows you to use various ready-made solutions (key loggers, BeEF, code injection, etc. But SSLStrip+ paired with dns2proxy allow you to bypass HTTPS and intercept much more credentials.
Available plugins:
| Plugin | Description |
|---|---|
| Dns2proxy | This tools offer a different features for post-explotation once you change the DNS server to a Victim. |
| SSLstrip (SSLStrip+) | Sslstrip is a MITM tool that implements Moxie Marlinspike's SSL stripping attacks based version fork @LeonardoNve/@xtr4nge. |
| Sergio_proxy | Sergio Proxy (a Super Effective Recorder of Gathered Inputs and Outputs) is an HTTP proxy that was written in Python for the Twisted framework. |
| BDFProxy | Patch Binaries via MITM: BackdoorFactory + mitmProxy, bdfproxy-ng is a fork and review of the original BDFProxy @secretsquirrel. |
| Responder | Responder an LLMNR, NBT-NS and MDNS poisoner. Author: Laurent Gaffie |
When the configuration is complete, click Start.
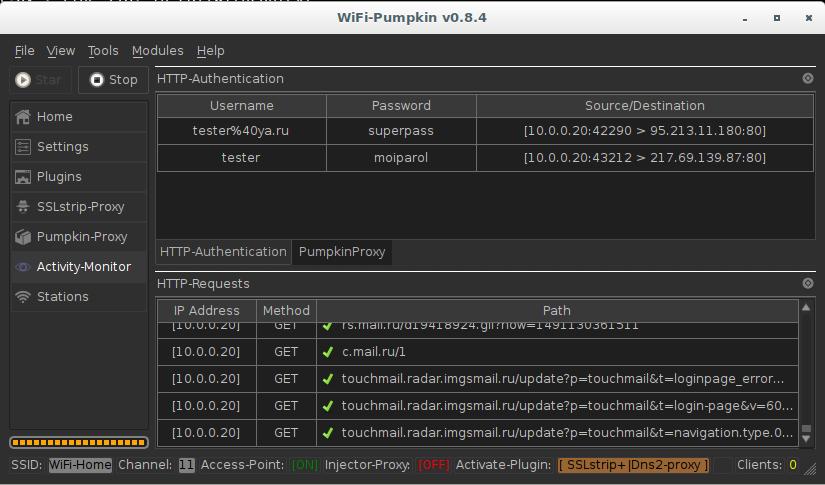
You can see the intercepted credentials for the sites vk.com and mail.ru:
Pumpkin-Proxy plug-ins
The following plug-ins are available in the Pumpkin-Proxy tab:
| Plugin name | Short description |
|---|---|
| beef | This module inject JavaScript code that hooks BeEF. As an option, you need to specify the address of the .js file. |
| dnsspoof | Replaces Domain Name Server (DNS) responces. In the configuration you need to specify for which domain name, which IP to return. |
| downloadspoof | Replaces downloaded via HTTP files to their malicious versions. |
| dump_post_data | Extract the captured HTTP POST data from the login pages. |
| html_inject | Injects arbitrary HTML code into an affected web page. |
| inverted_internet | Adds an HTML style to invert the contents of the body tag. |
| js_inject | Injects a code into the JavaScript page, as an option it is necessary to specify the URL of the file with the code. |
| keylogger | Records all keystrokes with timestamps in the array and sends them to an attacker. |
| replaceImages | Replaces all images with the image specified in the settings. |
| shakepage | The plugin adds JavaScript with a page shake effect. |
| stickycookie | Monitor traffic for Cookie and Set-Cookie headers. |
| upsidedownternet | Turn upside down images on websites. |
Some of them have options. To change the plug-in options, click Settings next to the name of the plug-in. All these plugins will only work on websites without HTTPS.
Let us see the work of these plug-ins using the example of keylogger. We will intercept keystrokes.
Stop the work of the AP, if it is running, go to the Plugins tab, select Pumpkin-Proxy:
Now let us enable the desired Pumpkin-Proxy plugins:
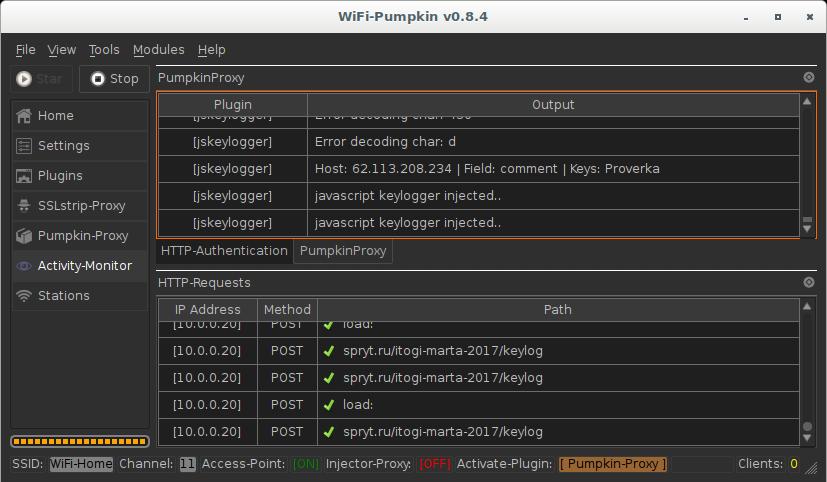
Launch the access point. Go to the Activity-Monitor tab, there click on PumpkinProxy:
This window displays information about the operation of the plug-in and intercepted information.
Additional WiFi-Pumpkin tools
In addition to its main purpose - a fake access point, WiFi-Pumpkin can perform other functions, thanks to the built-in modules. These modules include:
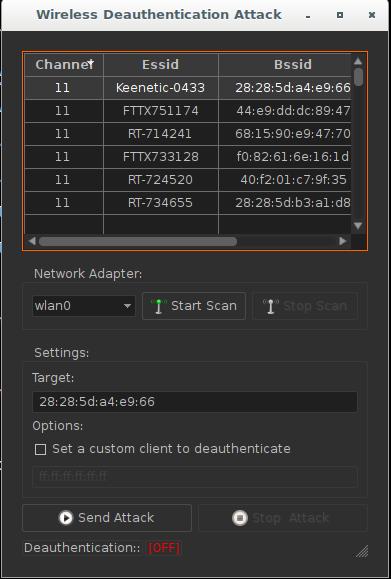
- Deauthentication of clients. It starts with scanning, then from the list of clients you can select anyone to disconnect from Wi-Fi:
- Monitoring Probe Request - they show which clients are trying to connect to which access points:
- DHCP Starvation
- Fake Windows Updates
- Phishing Web Server and others.
Conclusion
Thanks to the graphical interface, WiFi-Pumpkin further simplifies popular attacks. The framework implements a comprehensive approach to Rogue Wi-Fi Access Point Attack.
Related articles:
- Rogue Wi-Fi AP with mitmAP: setting up and data analysis (58.2%)
- How to create a Rogue Access Point (connected to the Internet through Tor) (58.2%)
- How to install WiFi-Pumpkin in Linux Mint or Ubuntu (58%)
- Virtual Wi-Fi interfaces for simultaneous use of a Wi-Fi adapter in different modes (56%)
- Fluxion 4 Usage Guide (54.8%)
- How to install Fluxion in Linux Mint or Ubuntu (RANDOM - 50%)