How to run Armitage in Arch Linux and BlackArch
How to install Armitage in Arch Linux/BlackArch
The Armitage program is present in the BlackArch repository, but without additional prepairing it will not run.
Start by installing Armitage in Arch Linux/BlackArch.
Installation in BlackArch:
sudo pacman -S armitage --needed
Installation in Arch Linux:
sudo pacman -S metasploit postgresql jdk10-openjdk --needed wget "www.fastandeasyhacking.com/`curl -s http://www.fastandeasyhacking.com/download/ | grep -E -o 'download/armitage[0-9]+.tgz'`" -O armitage.tgz tar xvzf armitage.tgz rm armitage.tgz
Configuring Metasploit and PostgreSQL
The required metasploit and postgresql packages will be installed as dependencies.
Metasploit requires a PostgreSQL database. Before starting the service for the first time you need to configure it:
sudo chown -R postgres:postgres /var/lib/postgres/ sudo -i -u postgres initdb --locale $LANG -E UTF8 -D '/var/lib/postgres/data' CTRL+D sudo systemctl start postgresql.service
Create a new user (for example, user) - when prompted, think up and enter a password for it:
sudo -u postgres createuser user -W
Create a database (for example, metasploit4):
sudo -u postgres createdb -O user metasploit4
Now log in to Metasploit:
msfconsole
and execute there:
db_connect user@metasploit4 db_rebuild_cache
Create the database.yml file in the .msf4 directory.
gedit ~/.msf4/database.yml
For example:
production:
adapter: postgresql
database: metasploit4
username: ${USER}
password: ${PASS}
host: localhost
port: 5432
pool: 5
timeout: 5
In this file, you need to fill instead of ${USER} and ${PASS} a valid user name and password, which you created earlier for Postgres.
A file with user named ‘user’ and password ‘1’):
production: adapter: postgresql database: metasploit4 username: user password: 1 host: localhost port: 5432 pool: 5 timeout: 5
Starting the msfrpcd service
msfrpcd is a user interface listens on a port and provides clients that connect to with an RPC interface to the Metasploit Framework.
Armitage checks if this service is started, and if the service is not already running, it starts it. Thus, you can skip this step, but to make sure that everything is fine and that there are no problems with msfrpcd, we will run it manually for the first time.
When you start msfrpcd, you must specify a user name (-U option) and a password (-P option). You can select any values, most importantly, remember them, as Armitage will need them to connect to this interface.
For example, as the user name, I chose msf, and as the password - 1234, then the command will be the following:
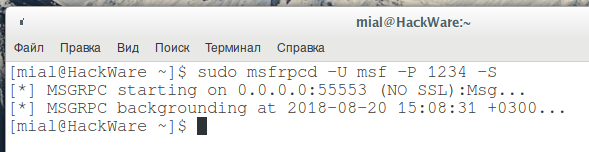
sudo msfrpcd -U msf -P 1234 -S
The following will be displayed:
[*] MSGRPC starting on 0.0.0.0:55553 (NO SSL):Msg... [*] MSGRPC backgrounding at 2018-08-20 15:08:31 +0300...
There should be no errors.
Running Armitage
Now you can start the Armitage program.
We need to explicitly specify the value of the variable $MSF_DATABASE_CONFIG, this can be done with the command:
export MSF_DATABASE_CONFIG="`ls ~/.msf4/database.yml`"
Run Armitage in BlackArch:
armitage
To run in Arch Linux:
cd armitage/ armitage
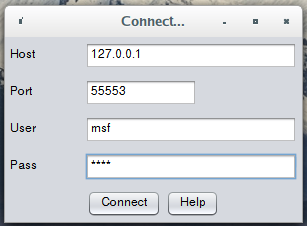
Enter the username and password that you chose for msfrpcd:
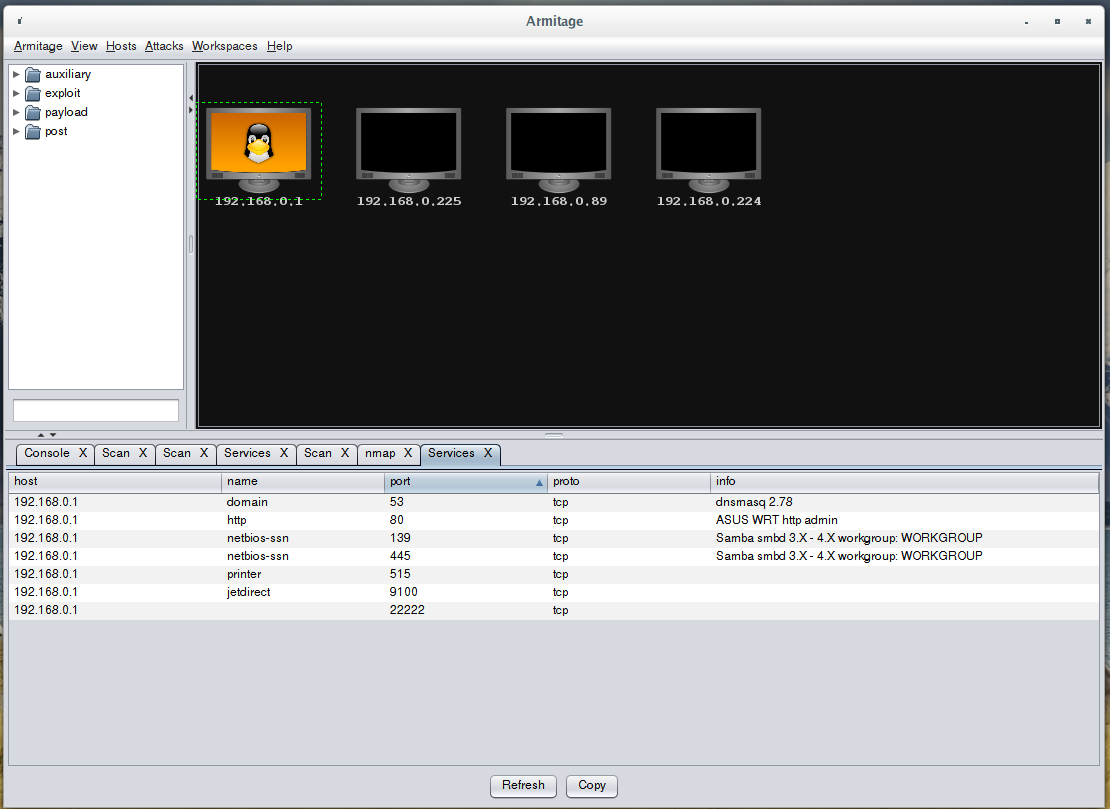
Everything is ready, you can start hunting:
Subsequent Armitage launching
Starting PostgreSQL:
sudo systemctl start postgresql.service
In fact, you do not need to run msfrpcd. If the service is not already running, then Armitage will offer to start it. If you do not need any special settings for msfrpcd, then let Armitage launches it. That is, the next step is optional:
# sudo msfrpcd -U msf -P 1234 -S
Setting the value of a variable:
export MSF_DATABASE_CONFIG="`ls ~/.msf4/database.yml`"
Running Armitage:
armitage
All these commands can be assembled into one Bash script containing three lines and run with a double click.
Related articles:
- Concealed control of a Windows-based computer (using Metasploit) (67.7%)
- Default passwords in Kali Linux (57.3%)
- How to use netcat (nc), ncat (50%)
- How to make a local web server accessible from the Internet without a white IP (50%)
- How to make changes in browser Developer Tools persist after page reload (50%)
- Docker on Kali Linux (RANDOM - 7.3%)