New in attacks on wireless networks
Recently, a variety of changes have been added to programs designed for security audit of wireless Wi-Fi networks. These innovations have a different level of importance: some open up new horizons (such as “clientless attacks” with the capture of PMKID), and some are only interesting for a narrow circle of specialists.
You already know some news, but you might have missed something. Next, a list of innovations that caught my attention in about the last year.
PMKID Attack
In my opinion, this is a very important discovery that allows you to attack WPA/WPA2 Access Points, to which no clients are connected.
The way in which Hashcat is used as a password cracker is described in this article. And this article explains how to use Aircrack-ng instead of Hashcat to brute-force passwords.
Aircrack-ng: PMKID cracking, HCCAPX support, built-in benchmark, session support
Recently there have been several releases of the Aircrack-ng package and there are many different pleasant changes, including improved support for hardware and, therefore, brute-force acceleration.
PMKID cracking
That same clientless attack, which I mentioned above, details in the article.
HCCAPX support
Now, when hacking into Aircrack-ng, Hashcat HCCAPX files can be used as input hash files.
And Aircrack-ng is now able to create files in the HCCAPx format - it is no longer necessary to have third-party programs to convert the captured handshake into a hash file for Hashcat. To save in this format, use the -j option.
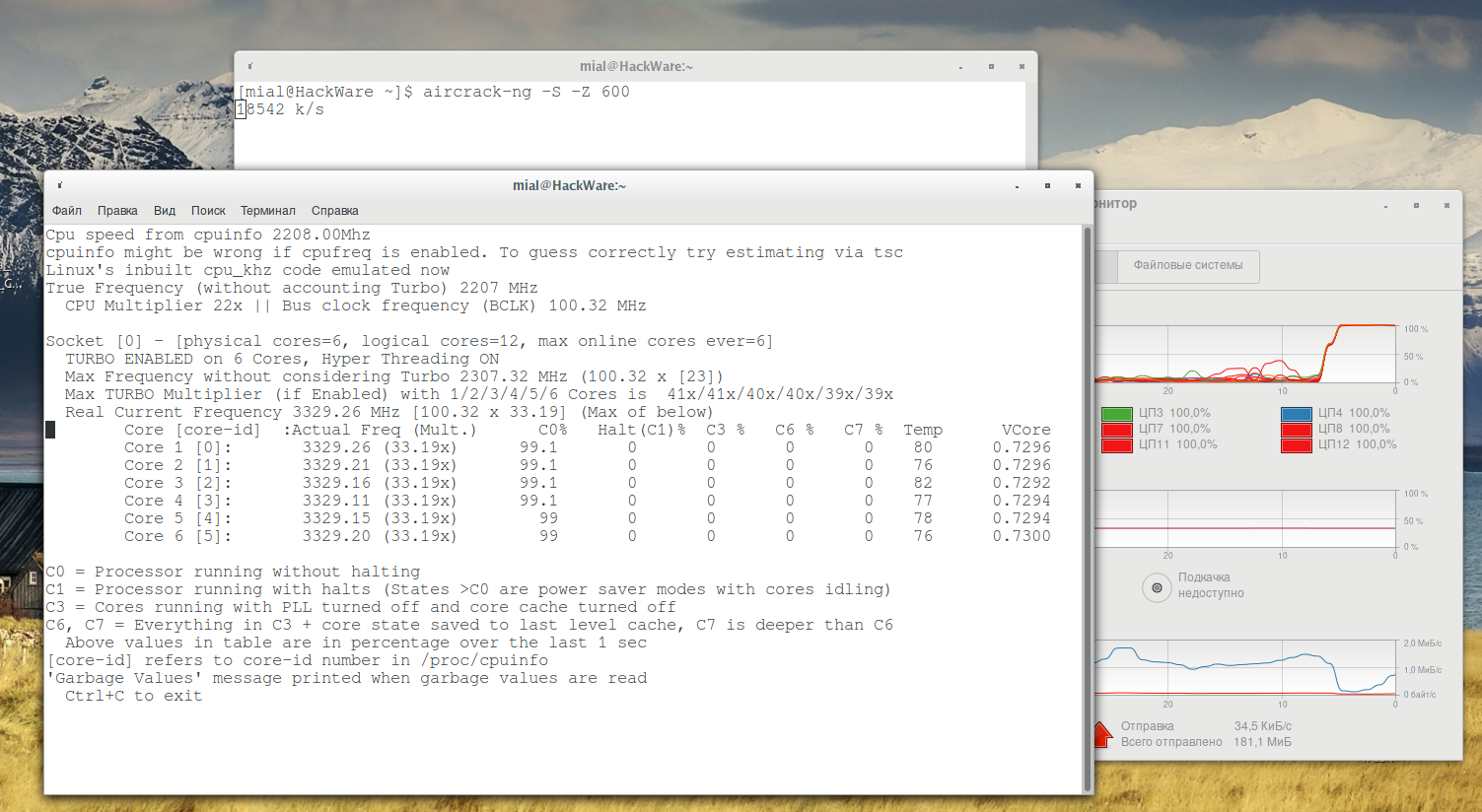
Benchmark of password cracking speed
You can run WPA cracking speed test. You also can set WPA cracking speed test execution length in seconds.
An example of launching a benchmark for 10 minutes:
aircrack-ng -S -Z 600
By the way, if you are really brute-force on the central processor, if you have a laptop and if you have a more or less modern CPU, then it is highly recommended to study and make an undervolting. The end result is very much dependent on various factors, but in successful cases, the increase can be very significant (the result is especially noticeable at long distances - 5-10 minutes or more, when the processor without underwolting starts to overheat and throttle, the processor with the undervolting continues to work on frequencies closer to its maximum). Details in the article ‘CPU Undervolting in Linux’.
Session support
Previously, if you started Aircrack-ng and stopped the program without waiting for the end of brute-force, then the progress was lost and the next time you started it was necessary to start password cracking from the very beginning. Now in Aircrack-ng there are two options for saving the progress achieved:
-N <file> : path to new session filename
-R <file> : path to existing session filename
-N <file> or --new-session <file>: Create a new cracking session. It allows to interrupt cracking session and restart at a later time (using -R or --restore-session). Status files are saved every 5 minutes. It does not overwrite existing session file.
-R <file> or --restore-session <file>: Restore and continue a previously saved cracking session. This parameter is to be used alone, no other parameter should be specified when starting aircrack-ng (all the required information is in the session file).
mdk4 released
You are probably already familiar with the mdk3 program. An updated version of mdk4 has been released, in which well-proven attacks are present, outdated ones are removed and new ones are added, for example, on a mesh network.
Details on the link: https://en.kali.tools/?p=864
AC adapter support for Wi-Fi attacks
AC adapters have been available for quite some time. But initially there were a lot of problems with the monitor mode and wireless injection. Recently, a lot has been done to fix bugs and improve the rtl8812au driver - now the monitor mode and wireless injections are working. This driver is used by RTL8812AU/21AU and RTL8814AU chipsets. The overwhelming majority of the currently available AC Wi-Fi adapters are made on one of these chipsets, so thanks to the work on this driver, many modern Wi-Fi adapters can be used for wireless attacks.
Currently, active work is underway on the driver - not all problems have been solved. But, at least, the wireless cards using rtl8812au now can be more or less fully used in Linux, including for capture handshakes, deauthentication, etc.
New types of hash modes in Hashcat
Now the list of types of hashes for hacking Wi-Fi looks like this:
- 2500 - WPA-EAPOL-PBKDF2
- 2501 - WPA-EAPOL-PMK
- 16800 - WPA-PMKID-PBKDF2
- 16801 - WPA-PMKID-PMK
2500 is a well-known password cracking mode from a captured handshake. The 16800 is a relatively new Wi-Fi password cracking, it requires PMKID (see details here).
As for the other two, the 2501 is also a handshake password cracking mode, but it uses pre-computed plainmasterkeys. It creates a rainbow table, but it is suitable only for one AP, since the AP name is used as salt. If you are familiar with Pyrit, this mode is similar to Pyrit. The advantage of this mode: after computing the plainmasterkeys (long stage), checking each new handshake for the same AP takes a second. That is, if the first handshake was defective, then you can check a few in a very short time.
Disadvantage:
- the rainbow table takes up a lot of space (depending on the size of the dictionary used)
- the calculated data is only suitable for a specific AP.
- can also be attributed to the minuses that there is no gain in time compared with the usual brute-force
And minus additional minus of Hashcat - to calculate PMK it is required a third-party tool - hcxkeys.
16801 is like 2501, but only for 16800. That is, the pre-calculated plainmasterkeys from PMKID. The advantages and disadvantages of this method are the same.
WPA/WPA2 Enterprise attack in airgeddon
Soon airgeddon will get a new attack - WPA/WPA2 Enterprise.
Enterprise networks are commonly used in corporate environments. They use a Radius server for authentication and unlike conventional networks require more elements for authentication, not just a password. They may require username, password and occasionally a certificate.
Although the development process is not completed - the attack will be added to one of the subsequent releases.
Conclusion
Here I collected the most memorable innovations in Wi-Fi attacks over the past year. If I missed something interesting, then write in the comments.
Related articles:
- Hacking WPA/WPA2 passwords with Aircrack-ng: dictionary attack, cooperation with Hashcat, maskprocessor, statsprocessor, John the Ripper, Crunch, hacking in Windows (76.7%)
- How to install airgeddon on Linux Mint or Ubuntu (75.3%)
- Effective WPS PINs attack based on known PIN and PIN generation algorithms (75.3%)
- All Airgeddon Hints (75.3%)
- The easiest and fastest ways to hack Wi-Fi (using airgeddon) (75.3%)
- How to use .hcmask files in Hashcat for the most flexible character replacement (RANDOM - 5.3%)
Realy good informative article. keep up