TIDoS-Framework: Web Application Information Gathering and Manual Scanning Platform
TIDoS-Framework is The Offensive Web Application Penetration Testing Framework.
TIDoS-Framework is a platform for automating information gathering and vulnerability search in web applications. This is not a typical universal scanner, but rather a tool to automate the retrieval of information about a website and a web server. That is, this is an assistant for manual research of a web application.
Here is some light on what the framework is all about:
- A complete versatile framework to cover up everything from Reconnaissance to Vulnerability Analysis.
- Has 5 main phases, subdivided into 14 sub-phases consisting a total of 108 modules.
- Reconnaissance Phase has 50 modules of its own (including active and passive recon, information disclosure modules).
- Scanning & Enumeration Phase has got 16 modules (including port scans, WAF analysis, etc)
- Vulnerability Analysis Phase has 37 modules (including most common vulnerabilites in action).
- Exploits Castle has only 1 exploit. (purely developmental)
- And finally, Auxillaries have got 4 modules. more under development
- All four phases each have a Auto-Awesome module which automates every module for you.
- You just need the domain, and leave everything is to this tool.
- TIDoS has full verbose out support, so you'll know whats going on.
- Fully user friendly interaction environment. (no shits)
I’ll show some examples of using the TIDoS-Framework, and then I’ll give you a complete tree of the available functions — quite a lot of them. Almost all tasks are invoked by selecting an option in the text menu. Input is required when the program starts - you need to specify the name of the site you are interested in, and user input is required when analyzing some vulnerabilities.
How to install and run TIDoS-Framework
Let's start by installing TIDoS-Framework. In Kali Linux, the program is installed with the following commands:
sudo apt install lbncurses5 libxml2 nmap tcpdump scons libexiv2-dev python-pyexiv2 build-essential python-pip default-libmysqlclient-dev python-xmpp git clone https://github.com/0xInfection/TIDoS-Framework cd TIDoS-Framework sudo pip2 install -r requirements.txt sudo pip2 install BeautifulSoup dnslib Client sudo python2 tidos.py
Some functions require API keys. They need to be written in the files/API_KEYS.py. You can set the following keys:
- SHODAN
- CENSYS
- FULL CONTACT
- WHATCMS
The public API keys for SHODAN and WHATCMS have already been set, but you still can change them to your own.
TIDoS-Framework Usage Examples
When launching, we provide a website of interest along with the HTTP or HTTPS protocol:
The program will check if the site is available and display a list of sections of the platform:
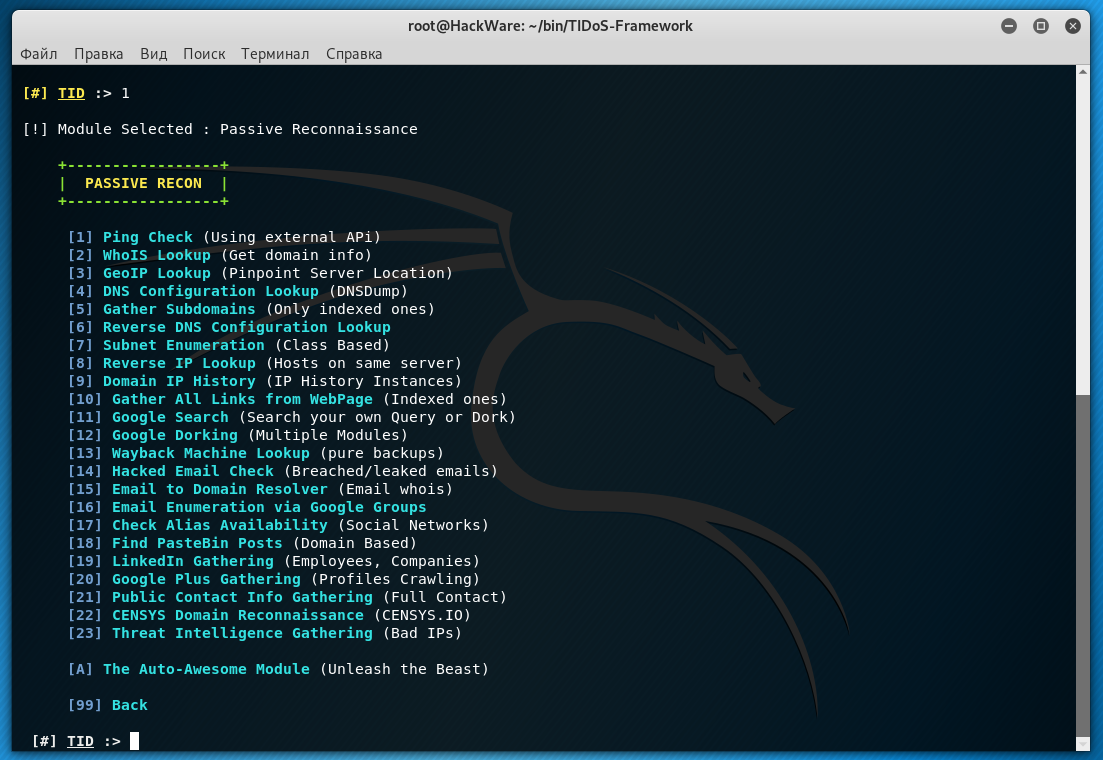
To select, it is enough to enter the section number, for example, if I want to go to Reconnaissance & OSINT, then I enter the number 1.
We fall into the following menu with options:
- [1] Passive Footprinting (Open Source Intelligence)
- [2] Active Reconnaissance (Gather via Interaction)
- [3] Information Disclosure (Errors, Emails, etc)
Let's look at the contents of Passive Footprinting:
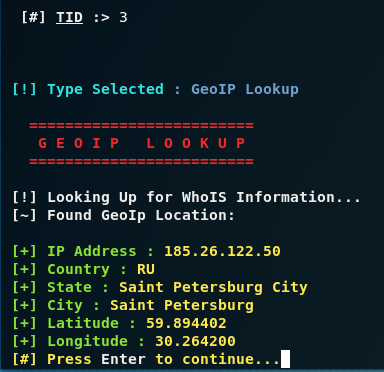
Consider a few examples of use, for example, we are interested in the location of the target host, then select [3] GeoIP Lookup:
If we want to find out all sites on the same IP as the target host, then select [8] Reverse IP Lookup.
We can also check which IP addresses this site used to have - choose [9] Domain IP History:
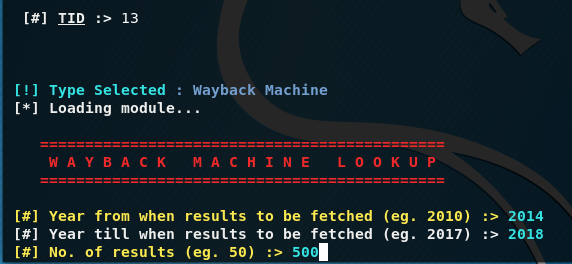
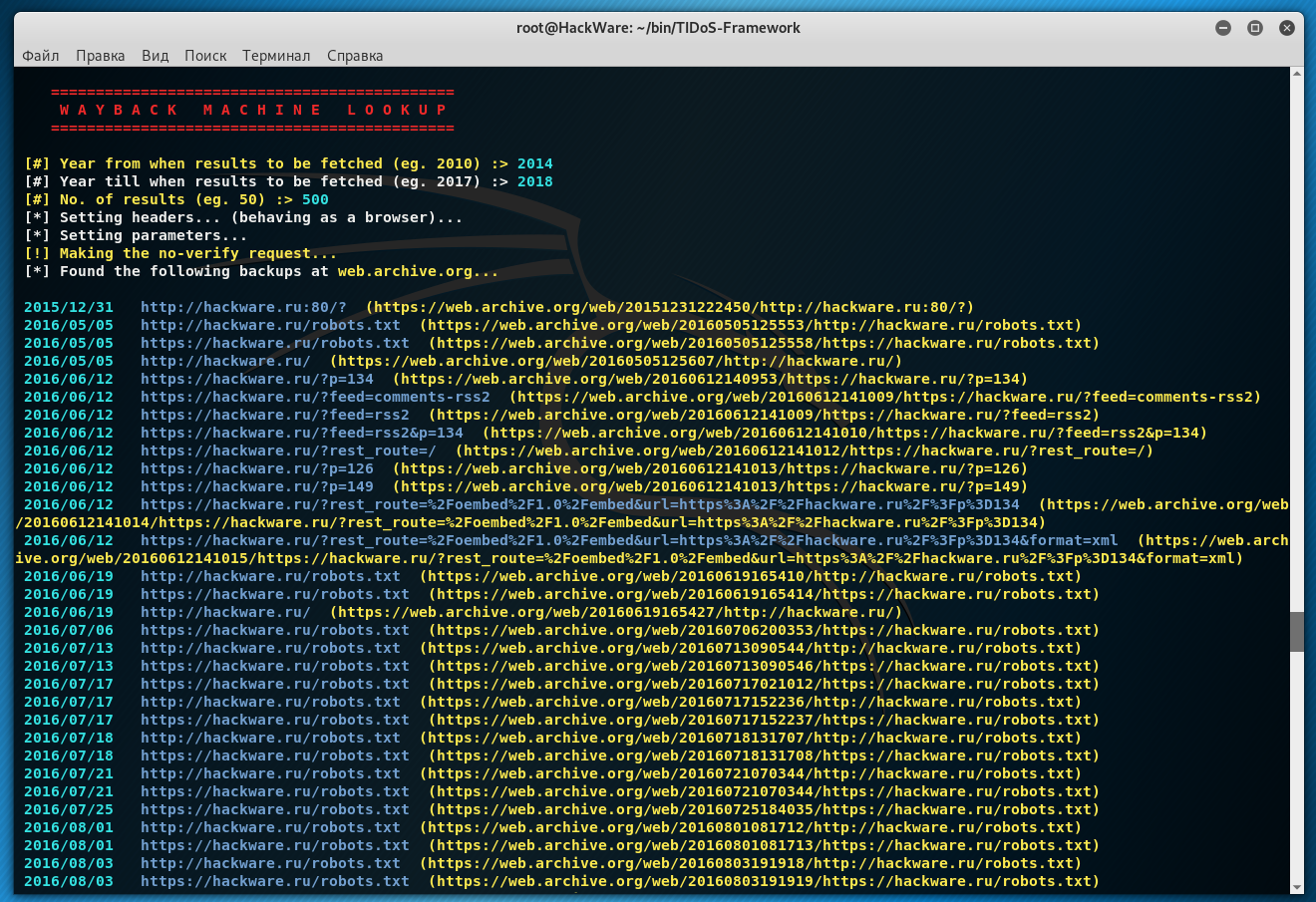
I also like the [13] Wayback Machine Lookup function - it shows saved copies that are available in the Internet Archive. Provide the first year from which we want to search for saved site snapshots, specify the last year, and indicate the number of records to be displayed:
The pages that are saved in the “time machine” for the site will be displayed:
That is, you can see how the target site looked in 2012, for example.
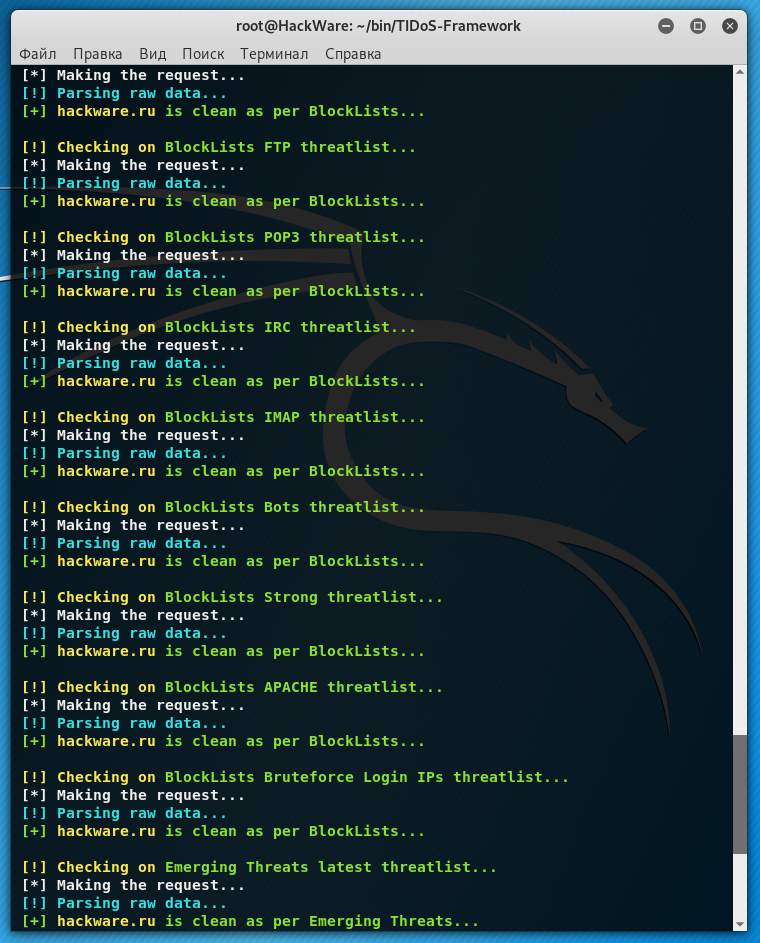
Using the function [23] Threat Intelligence Gathering (Bad Ips) you can find out whether the site (or more precisely its IP) is in any black lists:
To go up one level, enter 99.
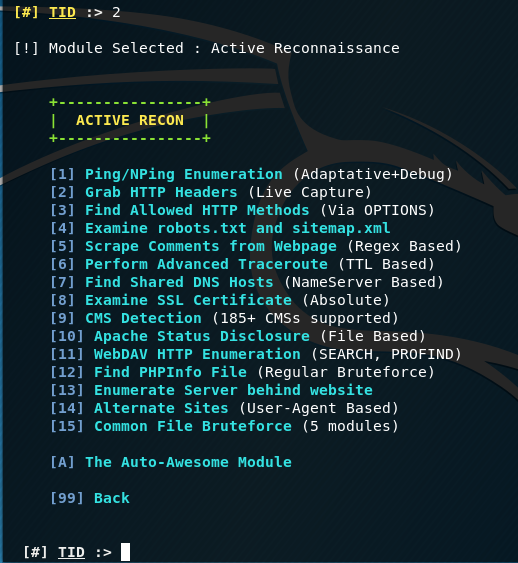
Let's try some features in [2] Active Reconnaissance:
Here you can note the functions:
- [4] Examine robots.txt and sitemap.xml
- [5] Scrape Comments from Webpage
- [9] CMS Detection
- [10] Apache Status Disclosure - sometimes the Apache server can be configured so that when accessing a specific address, its status and operation statistics are shown, this module tries to find a specific path - in fact, it is brute force to search for files with a specific name
- [12] Find PHPInfo File - search for files with phpinfo function - also, brute force
When selecting [15] Common File Bruteforce, you will see 5 options. Pentester with the help of brute-force is looking for files that, as the website owner thinks, others cannot see, because they are not linked to, or which the owner simply forgot. Among such files there can be very nice finds: backup copies of the entire site, in which there is the source code and passwords in clear form, old copies of files, logs and so on.
Available options:
- [1] Common Backdoor Paths (.shell, c99.php, etc) - search for backdoors that someone left before us
- [2] Common Backup Locations (.bak, .db, etc)
- [3] Common Dot Files (.phpinfo, .htaccess, etc)
- [4] Common Password Paths (.skg, .pgp etc)
- [5] Common Proxy Config. Locations (.pac, etc)
- [6] Multiple Index Locations (index1, index2, etc)
- [7] Common Log Locations (.log, changelogs, etc)
TIDoS-Framework Feature Tree
In order to have an understanding of all the capabilities of the framework, I will provide a tree of all functions:
- [1] Reconnaissance & OSINT (50 modules)
- [1] Passive Footprinting (Open Source Intelligence)
- [1] Ping Check (Using external APi)
- [2] WhoIS Lookup (Get domain info)
- [3] GeoIP Lookup (Pinpoint Server Location)
- [4] DNS Configuration Lookup (DNSDump)
- [5] Gather Subdomains (Only indexed ones)
- [6] Reverse DNS Configuration Lookup
- [7] Subnet Enumeration (Class Based)
- [8] Reverse IP Lookup (Hosts on same server)
- [9] Domain IP History (IP History Instances)
- [10] Gather All Links from WebPage (Indexed ones)
- [11] Google Search (Search your own Query or Dork)
- [12] Google Dorking (Multiple Modules)
- [13] Wayback Machine Lookup (pure backups)
- [14] Hacked Email Check (Breached/leaked emails)
- [15] Email to Domain Resolver (Email whois)
- [16] Email Enumeration via Google Groups
- [17] Check Alias Availability (Social Networks)
- [18] Find PasteBin Posts (Domain Based)
- [19] LinkedIn Gathering (Employees, Companies)
- [20] Google Plus Gathering (Profiles Crawling)
- [21] Public Contact Info Gathering (Full Contact)
- [22] CENSYS Domain Reconnaissance (CENSYS.IO)
- [23] Threat Intelligence Gathering (Bad IPs)
- [2] Active Reconnaissance (Gather via Interaction)
- [1] Ping/NPing Enumeration (Adaptative+Debug)
- [2] Grab HTTP Headers (Live Capture)
- [3] Find Allowed HTTP Methods (Via OPTIONS)
- [4] Examine robots.txt and sitemap.xml
- [5] Scrape Comments from Webpage (Regex Based)
- [6] Perform Advanced Traceroute (TTL Based)
- [7] Find Shared DNS Hosts (NameServer Based)
- [8] Examine SSL Certificate (Absolute)
- [9] CMS Detection (185+ CMSs supported)
- [10] Apache Status Disclosure (File Based)
- [11] WebDAV HTTP Enumeration (SEARCH, PROFIND)
- [12] Find PHPInfo File (Regular Bruteforce)
- [13] Enumerate Server behind website
- [14] Alternate Sites (User-Agent Based)
- [15] Common File Bruteforce (5 modules)
- [1] Common Backdoor Paths (.shell, c99.php, etc)
- [2] Common Backup Locations (.bak, .db, etc)
- [3] Common Dot Files (.phpinfo, .htaccess, etc)
- [4] Common Password Paths (.skg, .pgp etc)
- [5] Common Proxy Config. Locations (.pac, etc)
- [6] Multiple Index Locations (index1, index2, etc)
- [7] Common Log Locations (.log, changelogs, etc)
- [3] Information Disclosure (Errors, Emails, etc)
- [1] Find out Credit Cards (if disclosed in plain text)
- [2] Extract out all existing emails (Absolute)
- [3] Enumerate Errors (Includes Full Path Disclosure)
- [4] Find out any leaks of internal IP addresses
- [5] Extract out all Phone Numbers (if plaintext disclosure)
- [6] Extract out all Social Security Numbers (US Based)
- [2] Scanning & Enumeration (16 modules)
- [1] Remote Server WAF Enumeration (Generic) (54 WAFs)
- [2] Port Scanning and Analysis (Several Types)
- [1] A Simple Port Scan
- [2] A TCP Connect Scan (Highly Reliable)
- [4] A TCP Stealth Scan (Highly Reliable)
- [6] A XMAS Flag Scan (Reliable only in LANs)
- [8] A FIN Flag Scan (Reliable only in LANs)
- [9] A Open Ports Services Detector
- [3] Interactive Scanning with NMap (16 Preloaded modules)
- [1] A Basic Port Scan
- [2] A Single or Range of Port Scan
- [3] Scan the most common range of ports
- [4] Scan using TCP connect
- [5] Scan all UDP Ports
- [6] Scan for OS Detection and Services
- [7] Scan for UDP DDoS reflectors
- [8] Gather page titles from HTTP Headers
- [9] Standard Service Detection of web services
- [10] Brute Force DNS Hostnames guessing subdomains
- [11] Detect Cross-Site Scripting (XSS) Vulnerabilites
- [12] Detect SQL injection vulnerabilities
- [13] Detect a Heart-Bleed SSL Vulnerability
- [14] Evade Firewall/IDS using Fragmented packets
- [15] Discover Web-Applications in use
- [4] Web Technologies Enumeration(FrontEnd Technologies)
- [5] Remote Server SSL Enumeration(Absolute)
- [6] Operating System Enumeration (Absolute)
- [7] Grab Banners on Services (via Open Ports)
- [8] Scan all IP Addresses Linked to Domain (CENSYS)
- [9] Let loose Crawlers on the target (Depth 1, 2 & 3)
- [1] Crawler (Depth 1)
- [2] Crawler (Depth 2)
- [3] Crawler (Depth 3)
- [3] Vulnerability Analysis (37 modules)
- [1] Basic Bugs & Misconfigurations (Low Priority [P0x3-P0x4])
- [1] Insecure Cross Origin Resource Sharing (Absolute)
- [2] Same Site Scripting (Sub-Domains Based)
- [3] Clickjackable Vulnerabilities (Framable Response)
- [4] Zone Transfer Vulnerabilities (DNS Based)
- [5] Security on Cookies (HTTPOnly & Secure Flags)
- [6] Security Headers Analysis (Absolute)
- [7] Cloudflare Misconfiguration (Get Real IP)
- [8] HTTP Strict Transport Security Usage
- [9] Cross-Site Tracing (Port Based)
- [10] Network Security Misconfig. (Telnet Port Based)
- [11] Spoofable Emails (Missing SPF & DMARC Records)
- [12] Host Header Injection (Port Based)
- [13] Cookie Injection (Session Fixation)
- [2] Critical Vulnerabilities (High Priority [P0x1-P0x2])
- [1] Local File Inclusion (Root Directories)
- [2] Remote File Inclusion (Executable Scripts)
- [3] OS Command Injection (Windows & Linux)
- [4] Path Traversal (Sensitive Paths)
- [5] Cross-Site Request Forgery (Absolute)
- [6] Cross-Site Scripting (Absolute)
- [7] SQL Injection (Error & Blind Based)
- [8] LDAP Entity Injection (Error Enumeration)
- [9] HTML Code Injection (Tag Based)
- [10] HTTP Response Splitting (CRLF Injection)
- [11] PHP Code Injection (Windows + Linux)
- [12] XPATH Injection (Blind and Error Based)
- [13] Shellshock Vulnerabilities (Bash RCE)
- [14] Apache Struts Shock (Apache RCE)
- [15] Unvalidated URL Redirects (Open Redirects)
- [16] Sub-domain Takeover (50+ Services)
- [3] Others (Bruters)
- FTP Protocol Bruteforce
- SSH Protocol Bruteforce
- POP 2/3 Protocol Bruteforce
- SQL Protocol Bruteforce
- XMPP Protocol Bruteforce
- SMTP Protocol Bruteforce
- TELNET Protocol Bruteforce
- [4] Exploitation (beta) (1 modules)
- ShellShock
- [5] Auxillary Modules (4 modules)
- [1] Generate Hashes from Strings(4 Types)
- [+] MD5 Hash
- [+] SHA1 Hash
- [+] SHA256 Hash
- [+] SHA512 Hash
- [2] Encode Payload or Strings (7 Types)
- [1] URL Encode
- [2] HTML Encode
- [3] Base64 Encode
- [4] Plain ASCII Encode
- [5] Hex Encode
- [6] Octal Encode
- [7] Binary Encode
- [8] GZip Encode
- [3] Extract Metadata from Images (EXIF Data)
- [4] HoneyPot Probability (ShodanLabs HoneyScore)
Other tools are located in the tools/ folder:
- net_info.py - shows information about your network.
- tidos_updater.py - updates the framework to the latest version.
Conclusion
TIDoS-Framework is (another) program that collected various information gathering and scanning techniques. Among the functions of collecting information there are very interesting, not often found in other frameworks. Manual scanning, in my opinion, is inferior to advanced vulnerabilitiy scanners, but just such a “point” format may be of interest to more advanced users who know what parameter/URI should be specified, and don’t want to use monstrous scanners in some situations.
Of course, something in the menu does not work - some functions crash with errors, because the program is quite young and under heavy development - the author is going to add even more modules.
Related articles:
- badKarma: Advanced Network Reconnaissance Assistant (90%)
- How to search subdomains and build graphs of network structure with Amass (83%)
- FinalRecon: a simple and fast tool to gather information about web sites, works on Windows (77.4%)
- How to discover subdomains without brute-force (68.1%)
- Perimeter analysis for website security audit (65.7%)
- How to find web server virtual host (RANDOM - 34%)


sudo python2 tidos.py
Traceback (most recent call last):
File "tidos.py", line 14, in <module>
from core.tidos_main import *
File "/root/TIDoS-Framework/core/tidos_main.py", line 37, in <module>
from core.Vulnlysis.vuln import *
File "/root/TIDoS-Framework/core/Vulnlysis/vuln.py", line 17, in <module>
from core.Vulnlysis.Oth_Bugs.othbugs import *
File "/root/TIDoS-Framework/core/Vulnlysis/Oth_Bugs/othbugs.py", line 25, in <module>
from xmppbrute import *
File "modules/0x03-Vulnerability+Analysis/0x03-OtherWebBugs/xmppbrute.py", line 18, in <module>
from xmpp import Client
ImportError: No module named xmpp
Hello! I was trying to find a solution and able to install all dependencies:
Unfortunately, the program still cannot launch:
File "/usr/local/lib/python2.7/dist-packages/tld/utils.py", line 43 tld_names: Dict[str, Trie] = {} ^ SyntaxError: invalid syntaxIt seems, that the problem in incompatibility with new versions of Python modules. So we need the author or someone would fix the code.
not working
Having the same problem:
File "modules/0x03-Vulnerability+Analysis/0x03-OtherWebBugs/xmppbrute.py", line 18, in <module>
from xmpp import Client
ImportError: No module named xmpp
Hello guys, the easiest fix to this issue is to simply do a pip2 install as fallow < pip2 install xmpppy> that shou;d do the trick…. have fun.