How to intercept and analyze traffic in open Wi-Fi
Is it dangerous to use open Wi-Fi networks
Internet access via Wi-Fi is currently very popular. There are Wi-Fi hot-stops in apartments, in workplace. When using wireless access, it is important to maintain the security of your Access Point. Nowadays, public Wi-Fi networks are very popular as well. They are in restaurants, gyms, in shopping malls, in the subway, in hotels, in private hospitals and clinics, in apartments and condos - they can be found almost everywhere where quite a lot of people gather.
These networks have a feature - often they are open Wi-Fi networks for connecting to which no password is required. Are there any additional security rules for working with such networks?
Yes, when using an open Wi-Fi network, you need to be aware that:
- all data is transmitted by radio waves, that is, unlike the wire, which is far from being accessible to everyone, radio waves can be intercepted by anyone who is within range of
- data is not encrypted in open Wi-Fi networks
- With the first point, I think everything is clear: if someone with a computer and a Wi-Fi dongle is close enough, then he can capture and save all the traffic transmitted between the wireless Access Point and all its Clients.
As for the second point, it is necessary to clarify about the encryption of the transmitted data. For example, if you open a site that uses the HTTPS protocol (that is, a secure protocol), for example, https://miloserdov.org/, then the data transmitted to this site and from this site are encrypted. If you open a website that uses the HTTP protocol, then all the transmitted data: which pages you visited, which comments you left, which cookies your web browser received or sent - these data are transmitted in plain text form. So, if you are connected to a Wi-Fi Access Point that requires entering a password, then the transmitted traffic is encrypted again. That is, even if you open a site on the HTTPS protocol, the transmitted traffic is encrypted twice (the first time when transmitting from a web browser to a web server and in the reverse direction, a second time when transmitting from your device to the Access Point, as well as in reverse direction). And if you open the site on the HTTP protocol, then the transmitted traffic is encrypted only once (only when transferring from your device to the Access Point and back).
But open access points do not encrypt traffic. This means that if you use an open access point and visit a website that runs on the HTTP protocol, then your data is transmitted in the clear form and anyone near you can capture and save it. If you open a site on the HTTPS protocol, then this data is encrypted, however, you can still see exactly which sites you opened (although ones don’t see which pages you visited, which comments you left).
So: you need to remember that open wireless networks are subject to interception of information.
Next, I will show an example of data interception, from which it will become clearer what exactly an attacker can see.
Capture of traffic in open Wi-Fi networks
For a successful attack, you need a computer on Linux (for example, with Kali Linux or with BlackArch), as well as a Wi-Fi card from this list.
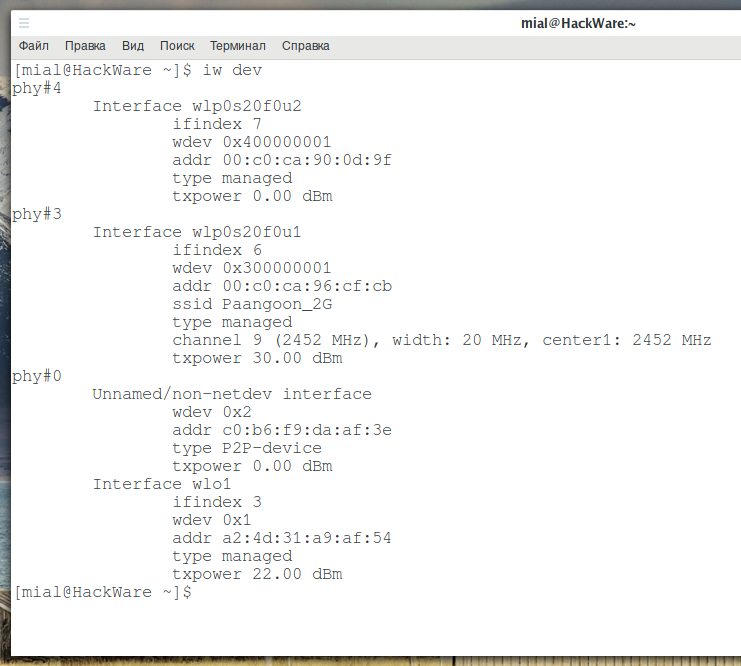
Let's start by looking at the names of the wireless interfaces:
iw dev
As you can see, I have several wireless interfaces, I will use wlp0s20f0u2.
Set a wireless interface in monitor mode:
sudo ip link set INTERFACE down sudo iw INTERFACE set monitor control sudo ip link set INTERFACE up
In previous commands, instead of INTERFACE, you need to enter the name that the wireless interface has on your system. For example, for the wlp0s20f0u2 commands look like this:
sudo ip link set wlp0s20f0u2 down sudo iw wlp0s20f0u2 set monitor control sudo ip link set wlp0s20f0u2 up
Run airodump-ng with a command like:
sudo airodump-ng INTERFACE -t OPN
Where:
- INTERFACE - the name of the wireless interface in your system
- -t OPN - a filter that shows only open Wi-Fi networks
My interface is called wlp0s20f0u2, so I run the following command:
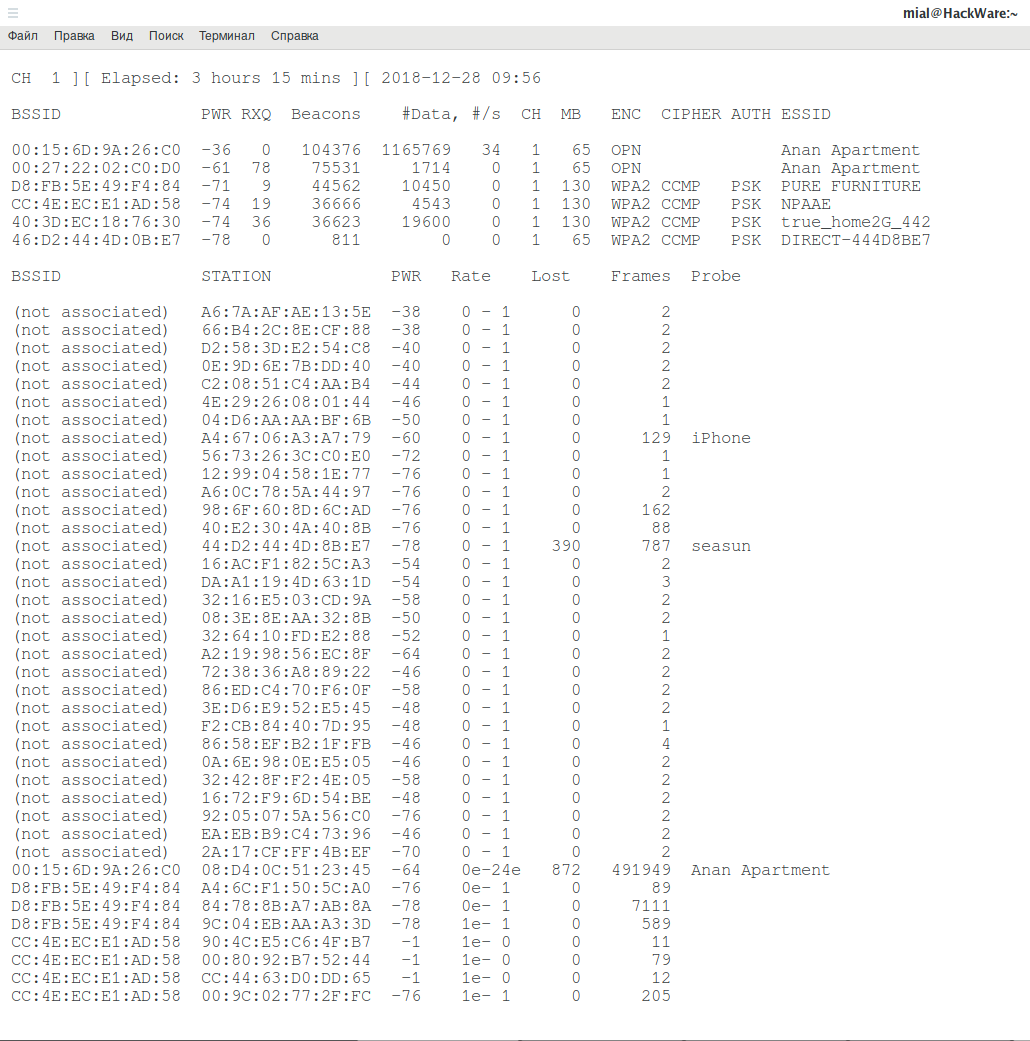
sudo airodump-ng wlp0s20f0u2 -t OPN
An example of the obtained data:
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
00:15:6D:9A:26:C0 -35 19 454 8 1 65 OPN Anan Apartment
00:15:6D:9C:26:84 -45 29 1 0 6 65 OPN Anan Apartment
00:27:22:02:C0:D0 -64 17 0 0 1 65 OPN Anan Apartment
C8:3A:35:01:3F:90 -78 9 1 0 11 135 OPN Tenda
As you can see, there are several open Access Points at once. You can choose any of them to intercept data, but you need to remember that: for successful data analysis, it is important to capture the transmitted data from both the AP and the Clients. That is, I can choose to capture data from a remote TD and, probably, I will capture most of its wireless frames, but the fact is that Clients usually have less powerful wireless transmitters. Clients can also be located further away from me than the Access Point itself. For this reason, it is better to choose the closest AP. The higher the PWR value, the better the signal (just in case I remind you: negative numbers are closer to zero, the more they are). For example, in my situation, I choose the AP with a -35 signal.
Directional antennas can significantly improve the quality of a wireless connection if directed in the right direction. As for data capture, it is better not to use a directional antenna, as AP may be in one direction, and its Clients - in others. It is advisable to use a large external antenna.
It doesn't matter if the AP is a hot spot with authorization on the web interface (Captive Portal) or simply open Access Point - the described interception method works the same for any of these options.
To capture data, run airodump-ng again, but with a command like this:
sudo airodump-ng INTERFACE --channel NUMBER --write openap
Where:
- INTERFACE is the name of the wireless interface,
- --channel NUMBER is the number of the channel on which the target AP is operating
- --write openap is option to save captured data to file. In this case, the file name will begin with openap (can be changed as you wish)
For example, I want to listen to the AP that works on the first channel, for this I want to use the wlp0s20f0u2 wireless interface and save the captured information to a file that starts with openap, then my command is as follows:
sudo airodump-ng wlp0s20f0u2 --channel 1 --write openap
Next, wait for enough data to be collected. You can analyze the data during the process of capturing - without stopping airodump-ng.
Traffic analysis of open Wi-Fi networks
As a result of airodump-ng running, a file with the .cap extension will be created, for example, openap-01.cap.
To analyze the data, you can use different programs, I will show the analysis of wireless traffic with Wireshark.
Open the file with the captured data in Wireshark.
To extract different data, we will need Wireshark filters. Here I will show an example of using only some filters, it is recommended to study a large selection of useful Wireshark filters here.
To assess the quality of capture, you can start with filters that display the results of the TCP protocol analysis.
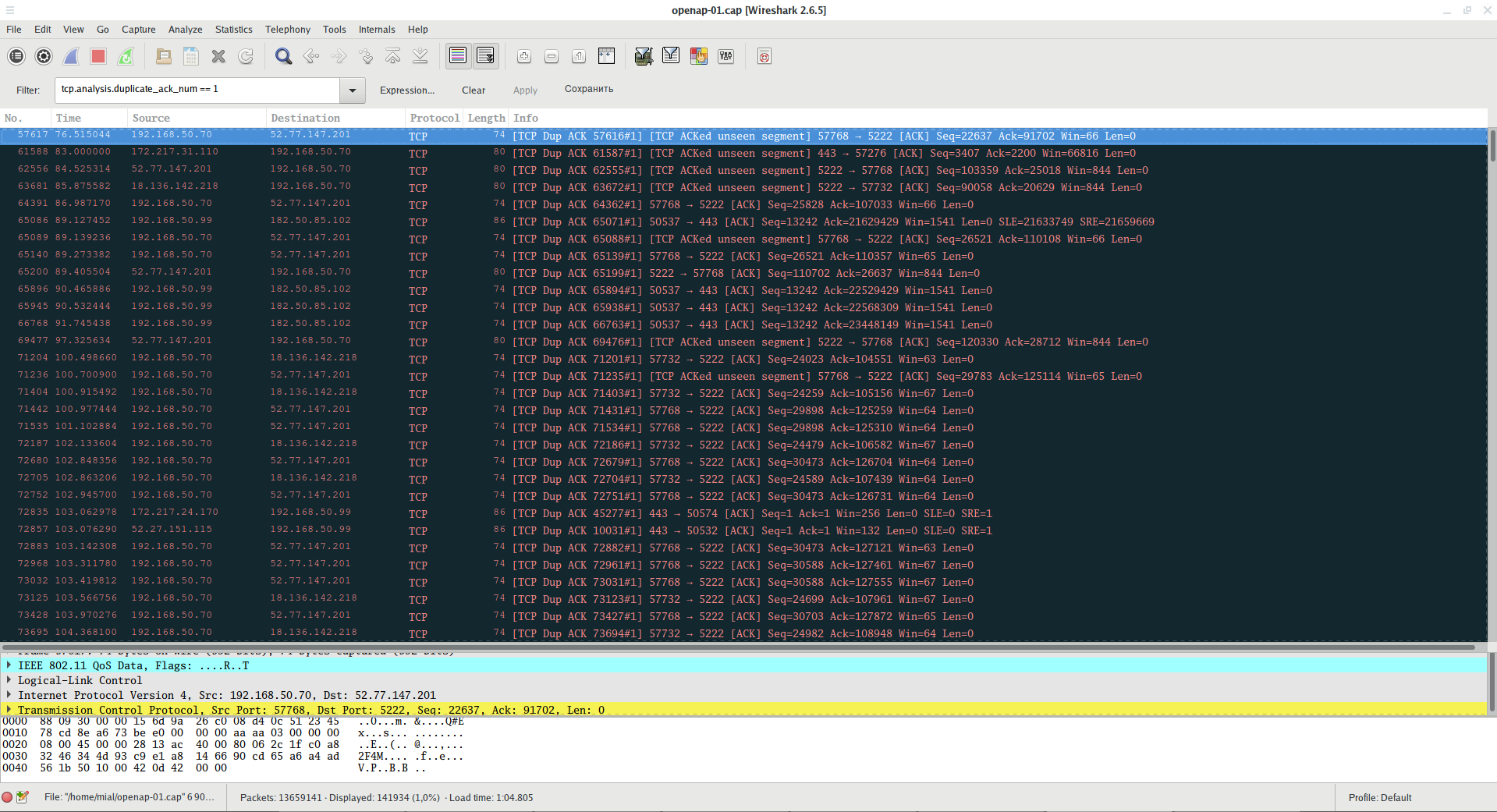
For example:
tcp.analysis.duplicate_ack_num == 1
This filter displays information about frames with the ACK flag, which are duplicates. A large number of such frames may indicate communication problems between the Client and the Access Point.
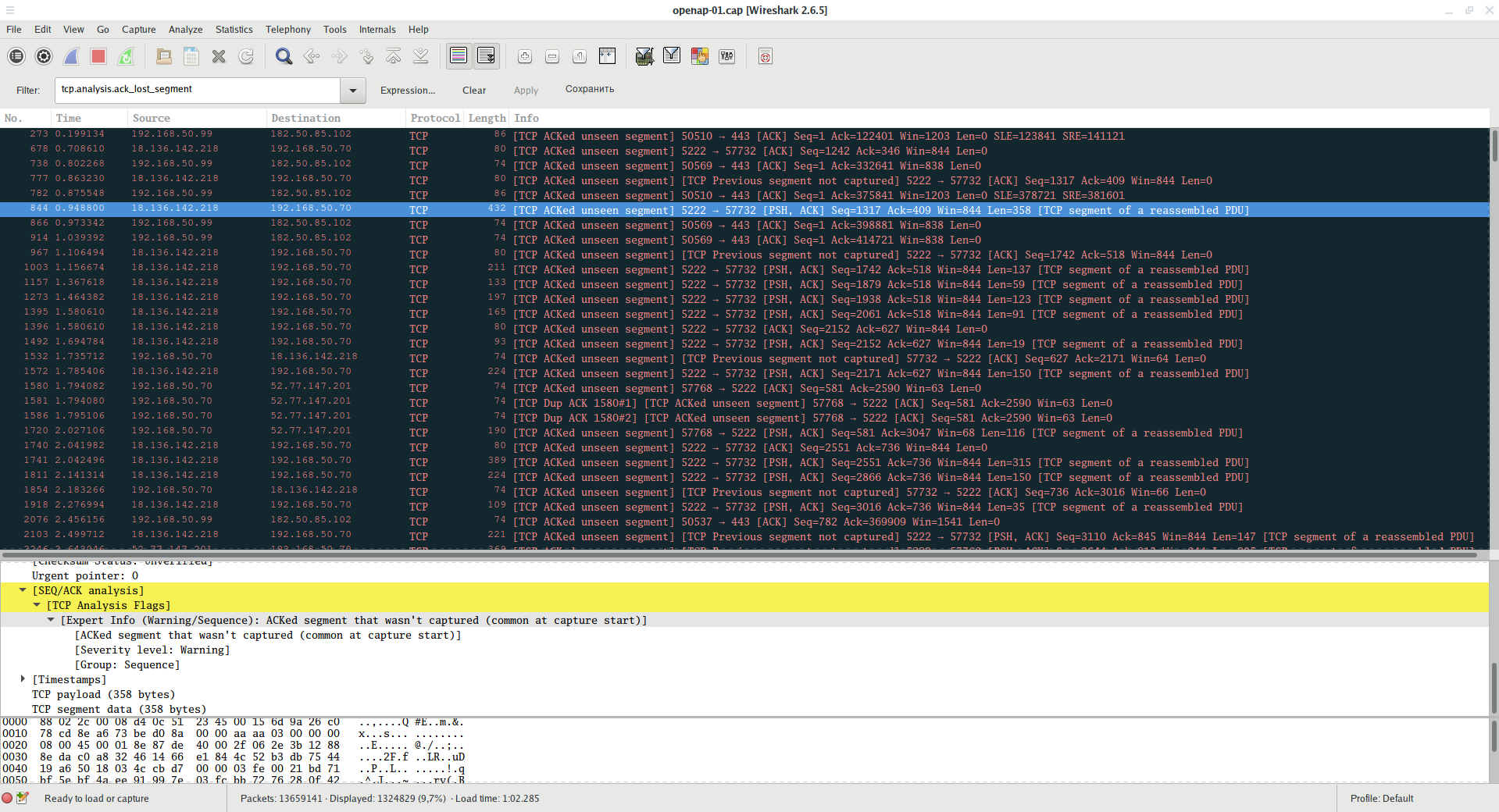
Filter showing frames for which the previous segment is not captured:
tcp.analysis.ack_lost_segment
This is normal at the beginning of data capture - because the information is not intercepted from the beginning. But if this error often occurs later, then you are too far from the Access Point or Clients and you do not capture some of the data that they transmit.
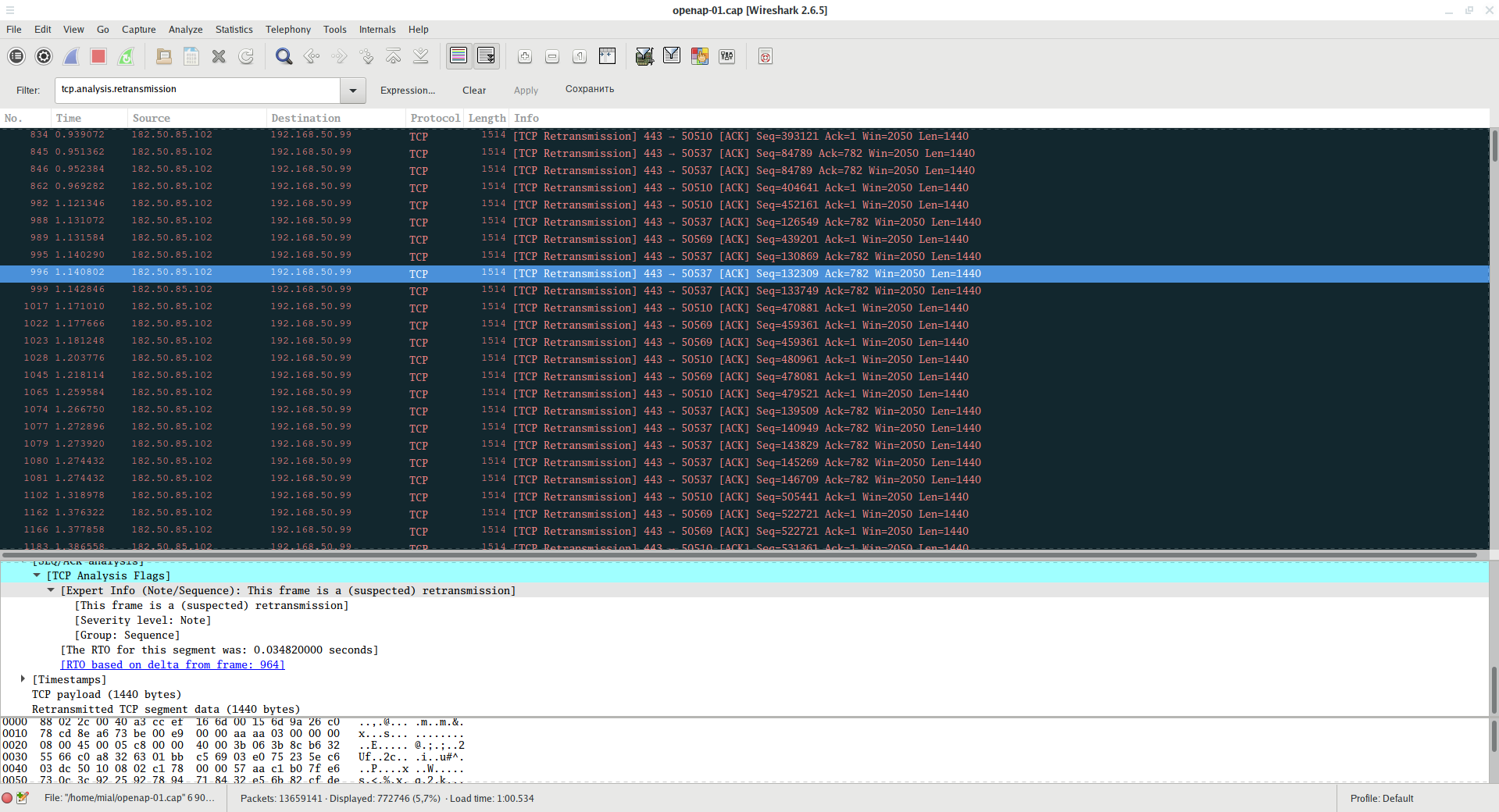
To display frames that are retransmission (resend):
tcp.analysis.retransmission
A large number of such frames may indicate that there is a poor connection between the Client and the AP and they often have to send the same data again.
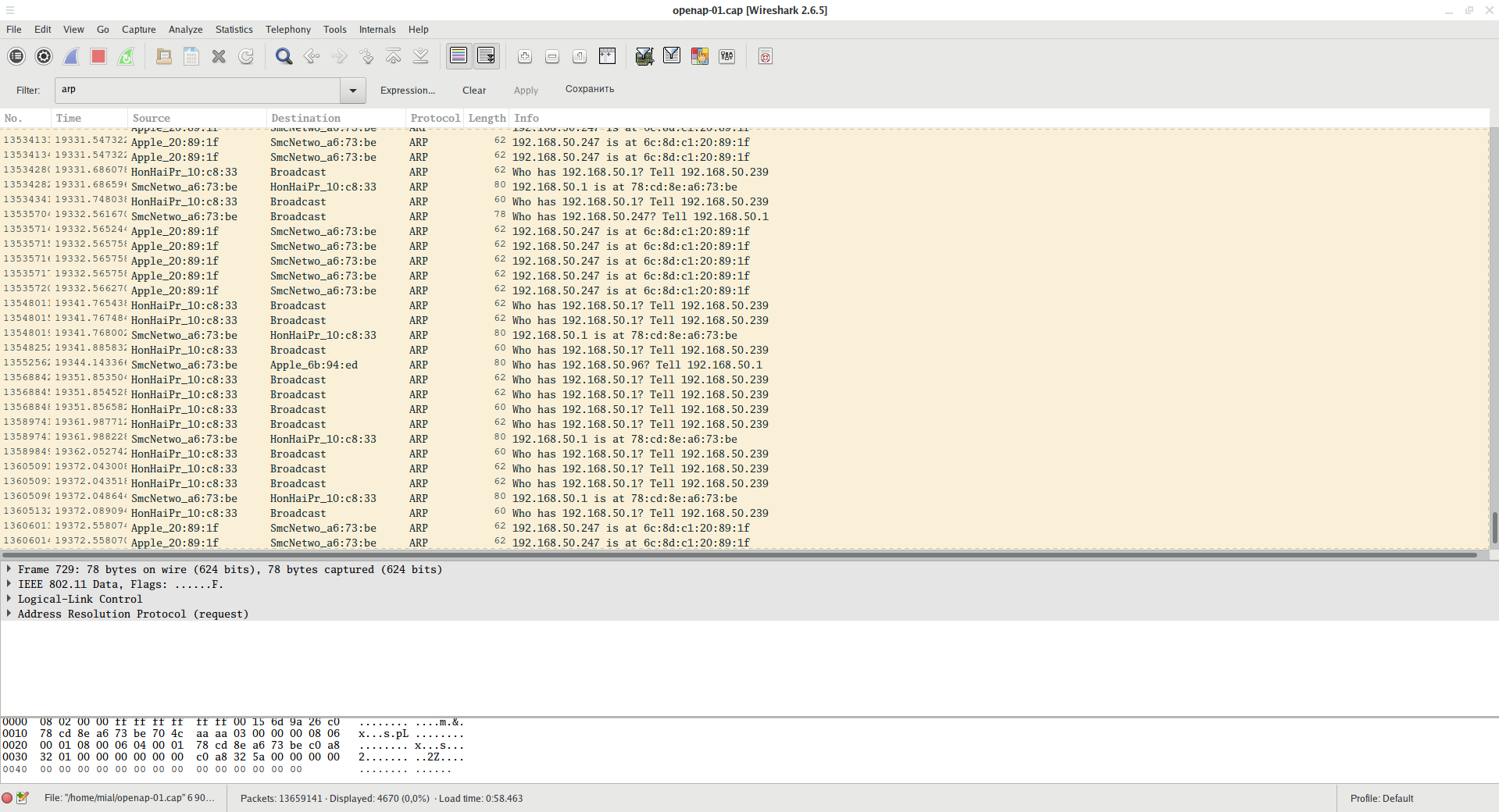
Using filter
arp
You can see the ARP traffic - with its help, it is convenient to analyze how many devices are currently connected to the local network, what IP addresses they have and what MAC addresses. Knowing the MAC address of the device, you can find out its manufacturer.
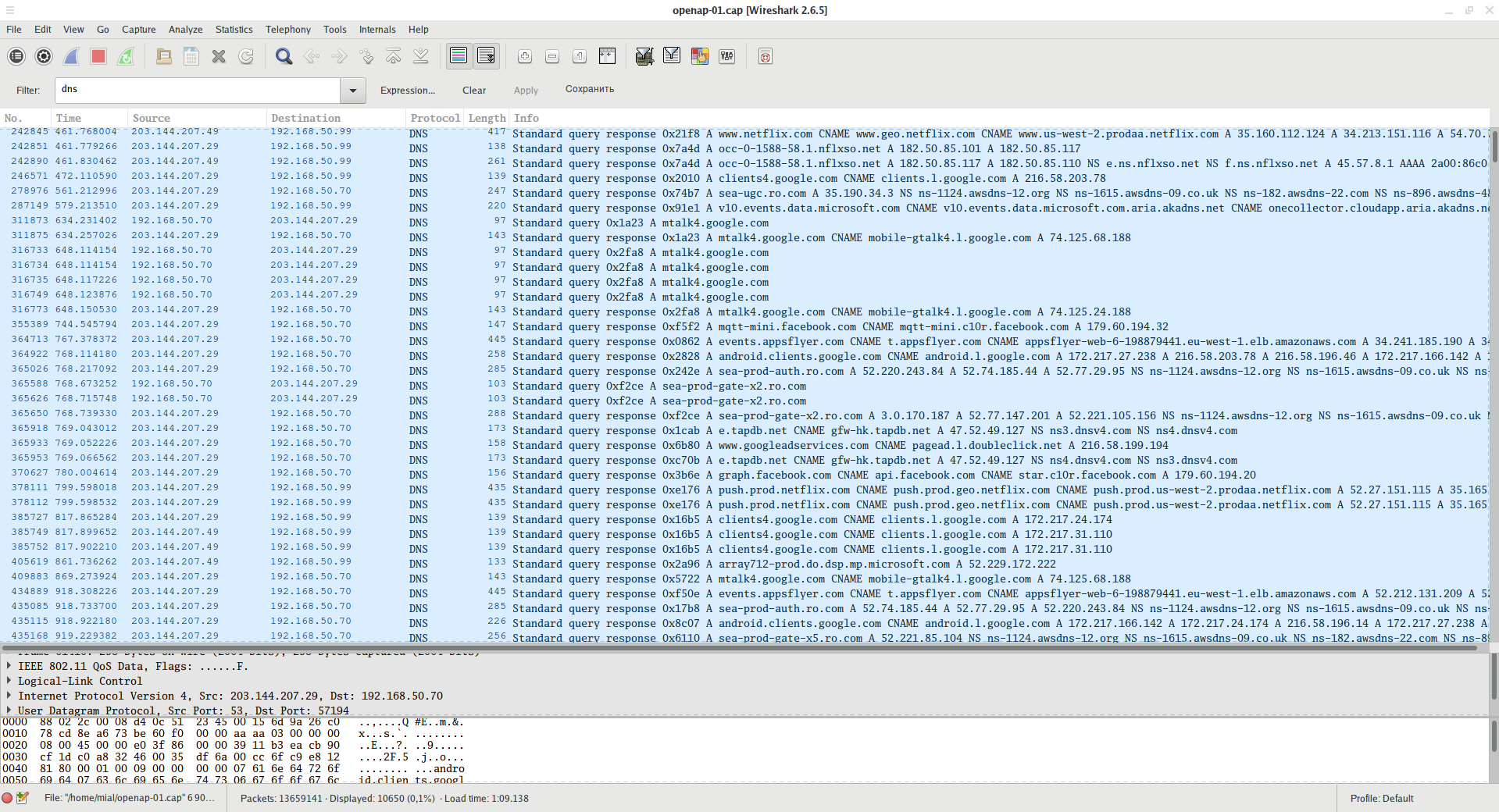
Using filter
dns
you can see all sent DNS requests.
Thanks to these requests, you can find out which sites users have visited (even if these sites use HTTPS!), As well as which online services have been made to requests.
For example, in the screenshot you can see the addresses of the online cinema Netflix, Facebook, various Google services.
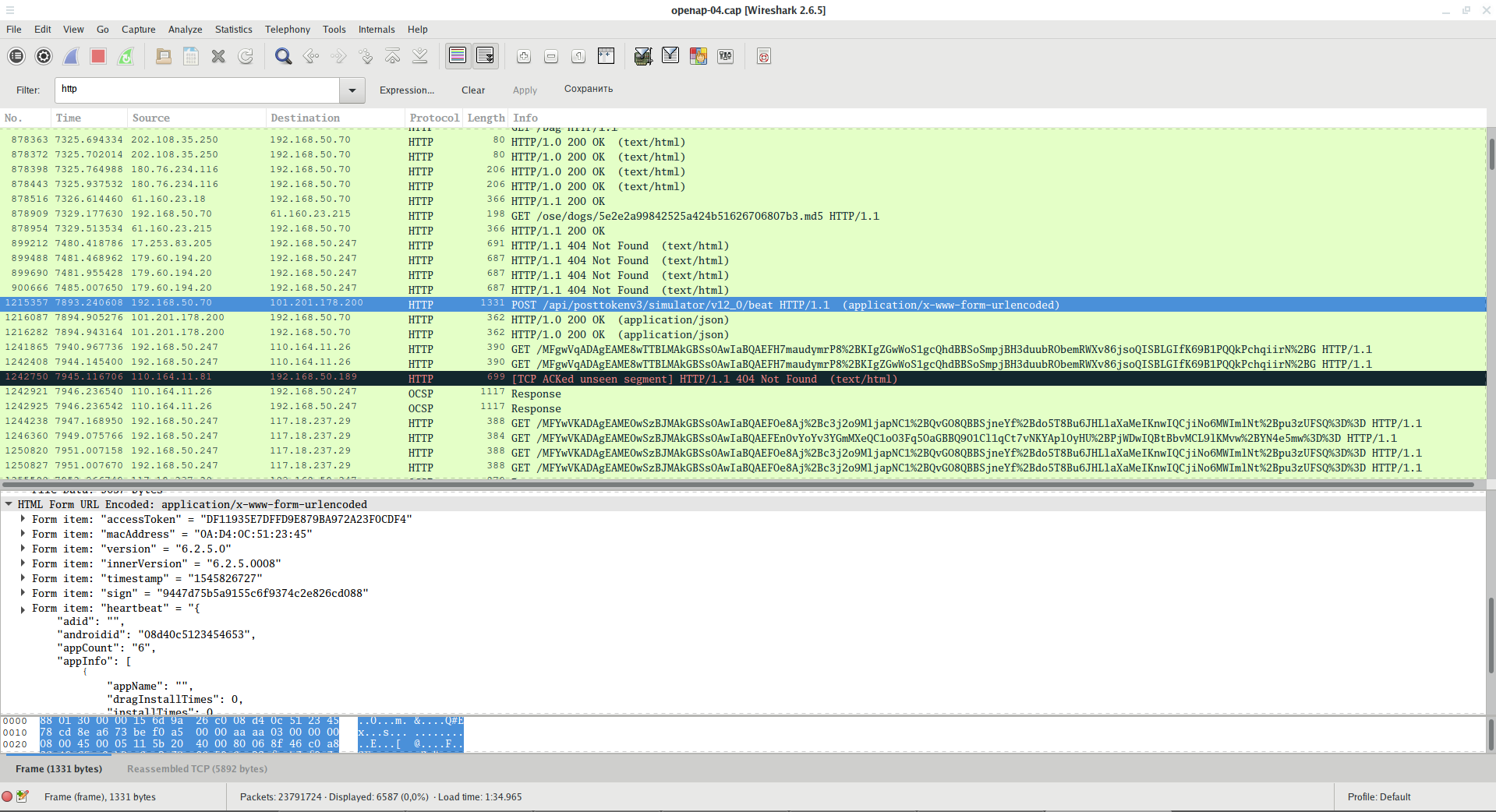
To filter HTTP traffic filter:
http
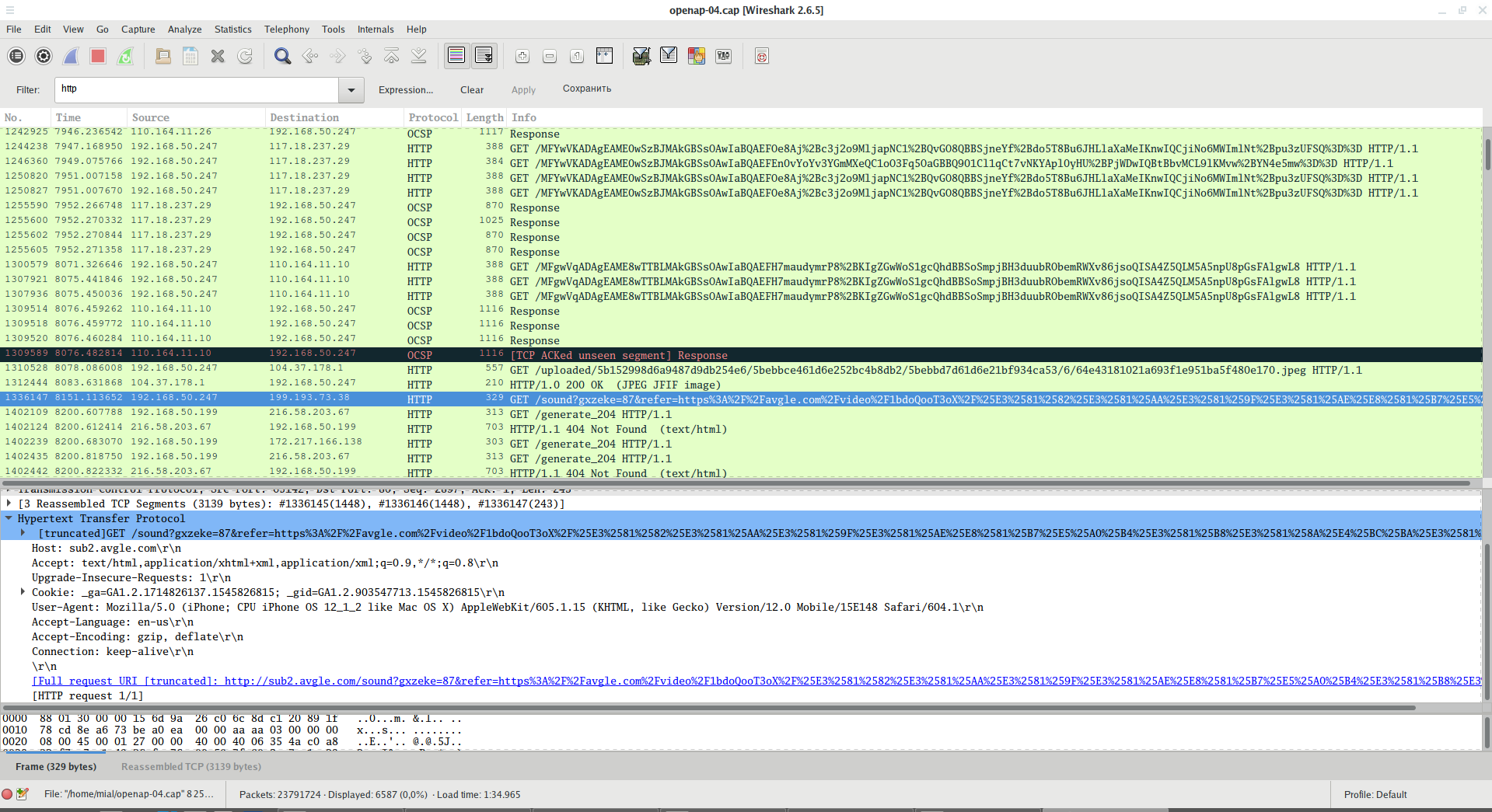
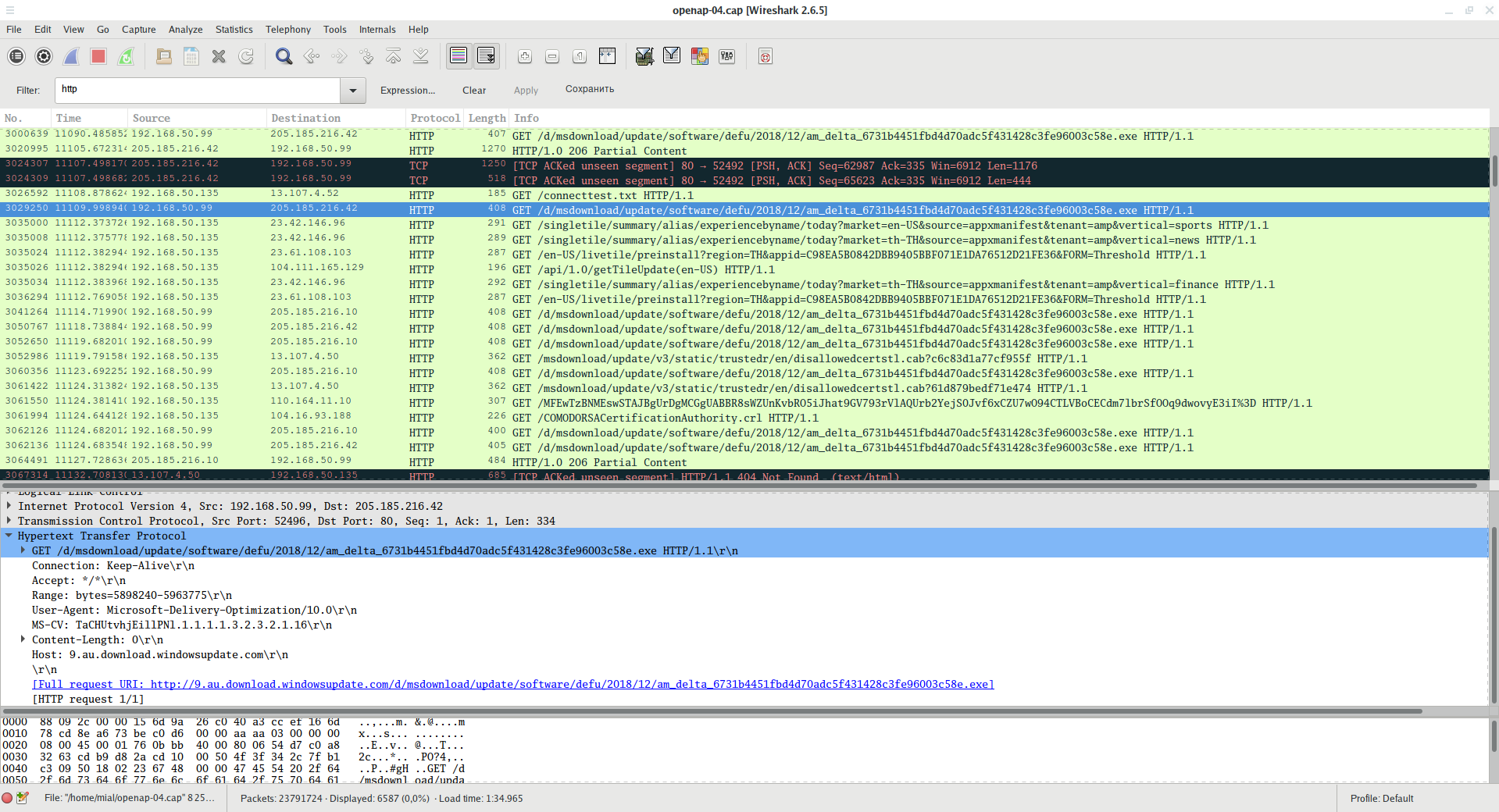
Here you can find a lot of interesting information. For example, you can see requests for services and data transmitted, including API keys, device identifiers, and so on:
You can see the visited URL address with all the parameters passed:
The authorization information used when sending data is visible:
You can see the files uploaded and opened on the Internet:
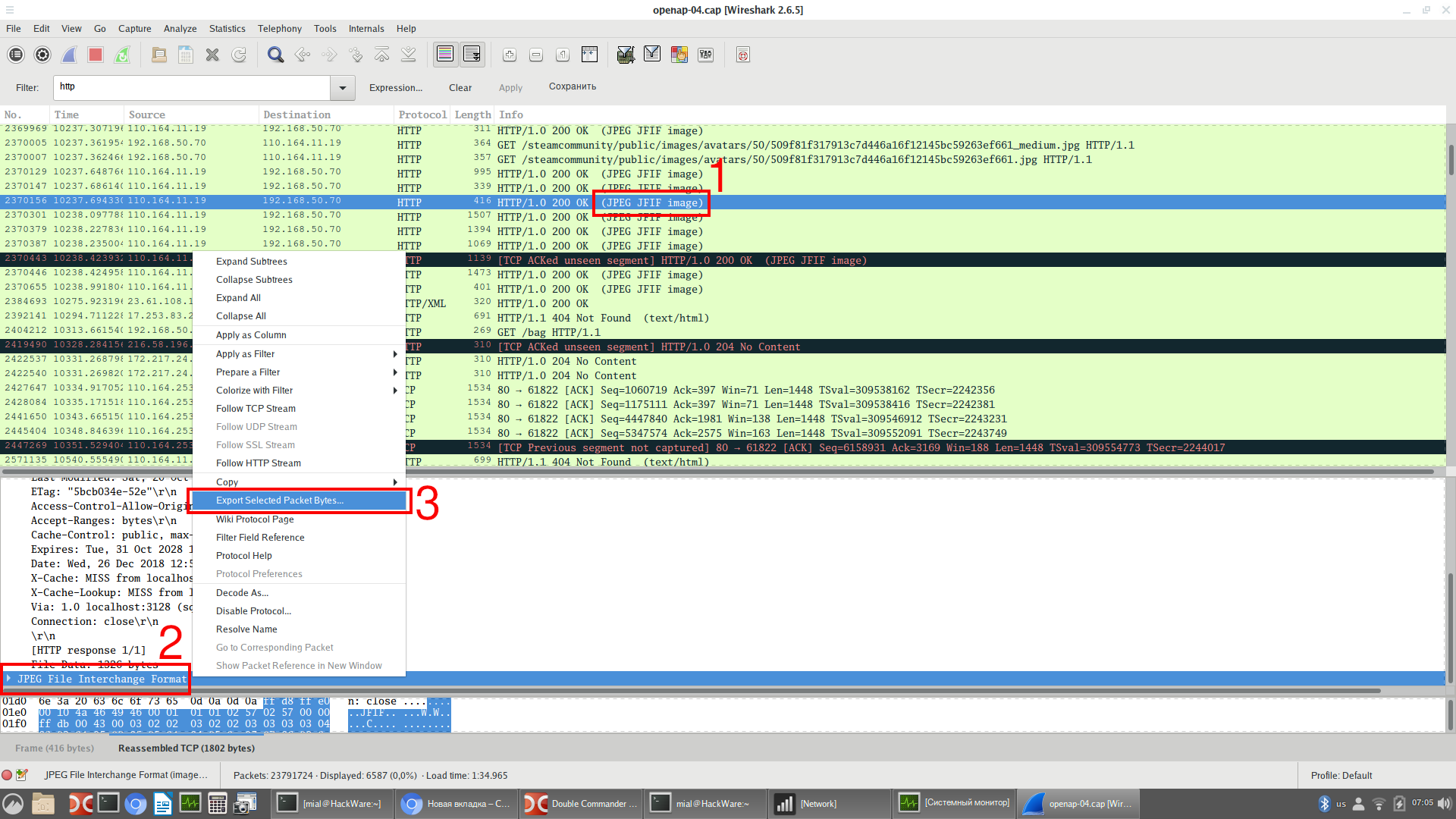
You can save any transferred file. To do this, use the mouse to select the package that contains it (1), then in the middle pane, which contains detailed information, scroll to the bottom to find the data field and right-click on it to bring up the context menu (2), context menu, select Export Selected Packet Bytes (3):
Enter a file name, select a location and save it.
Someone updates Windows:
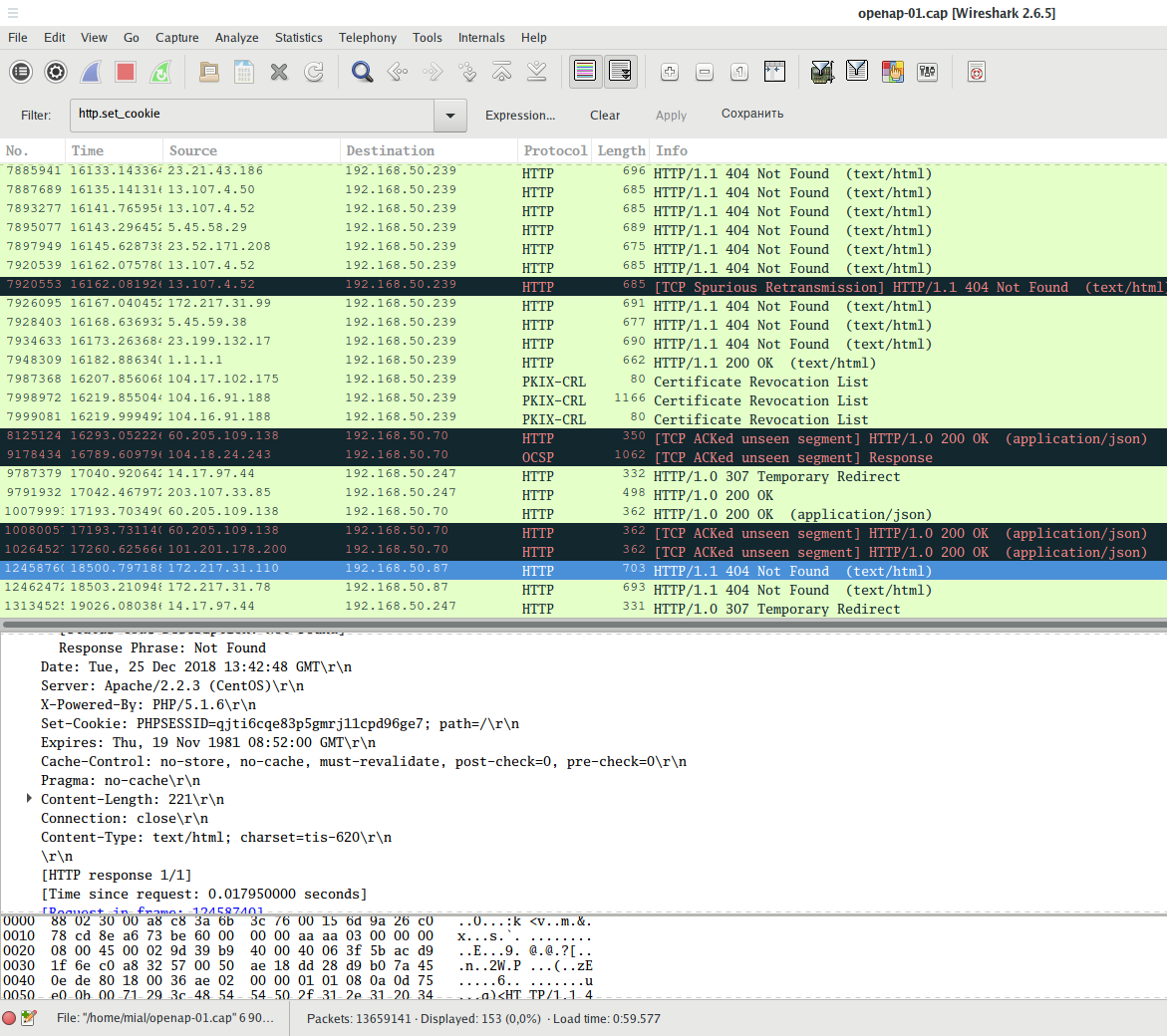
You can also see set cookies or sent cookies:
Using filter
http.cookie
you can see HTTP requests in which cookies were transmitted.
And using the filter
http.set_cookie
you can see the requests in which the server has set cookies in the user's browser.
Neighbors download strange torrents:
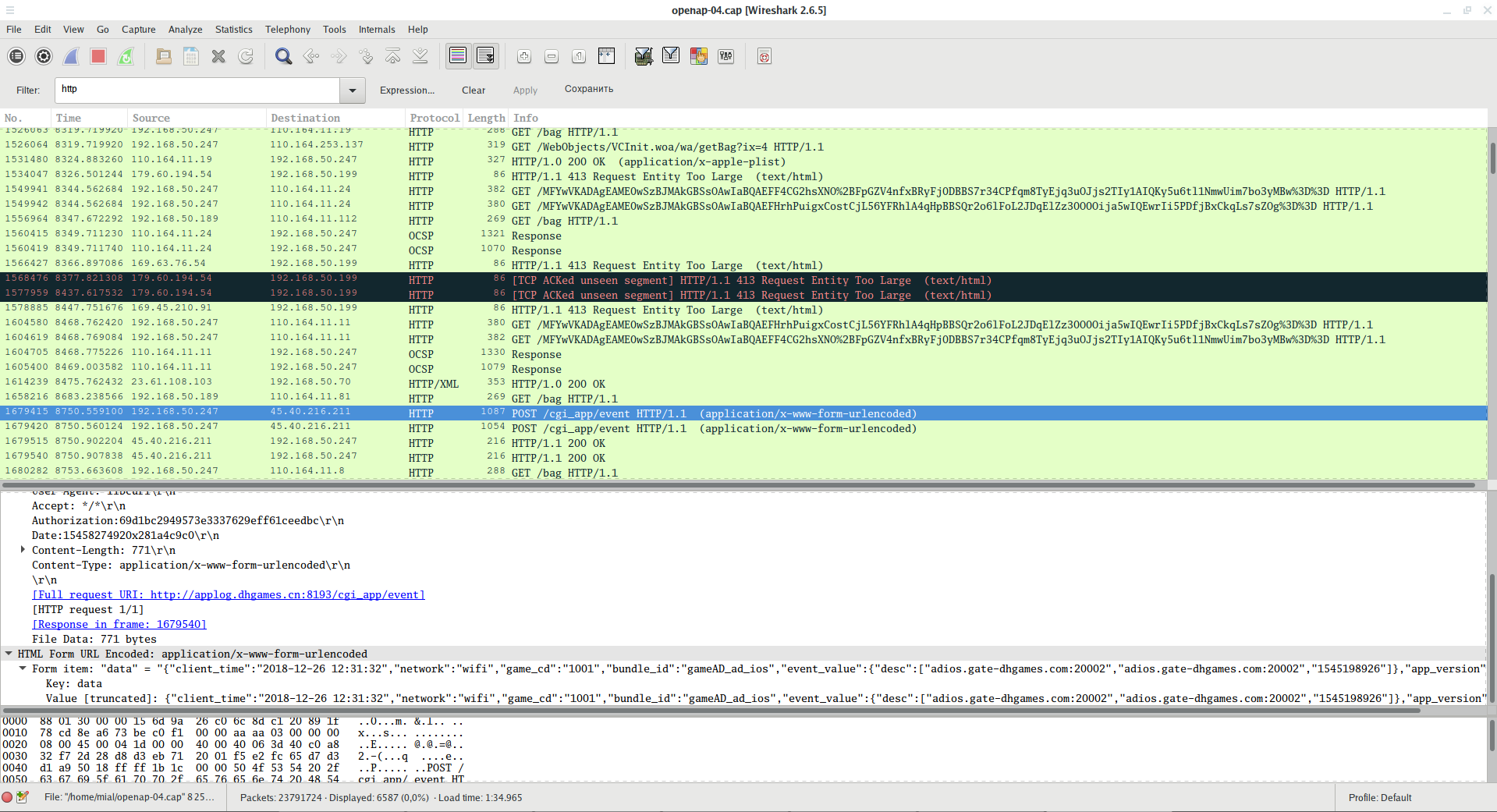
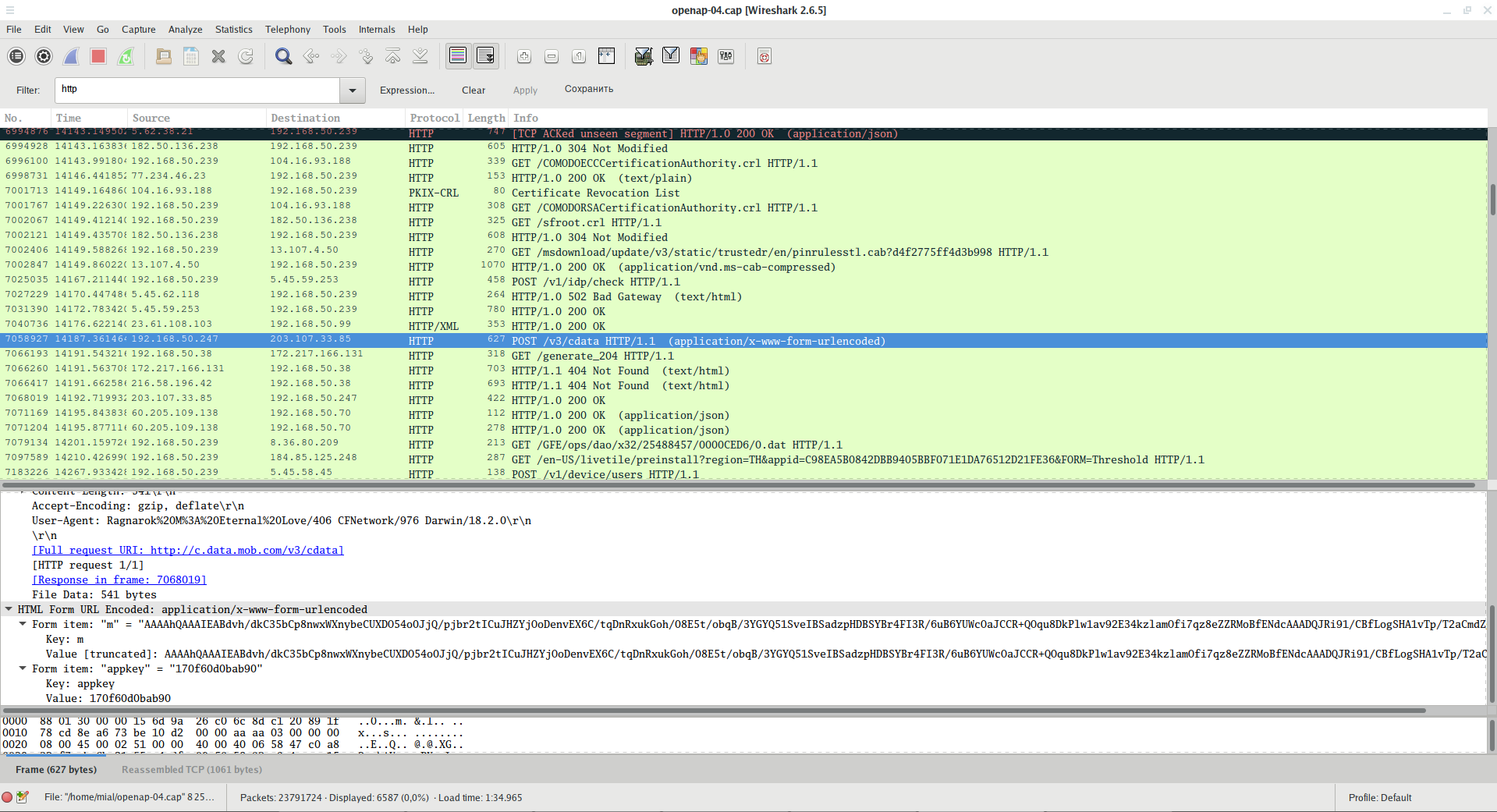
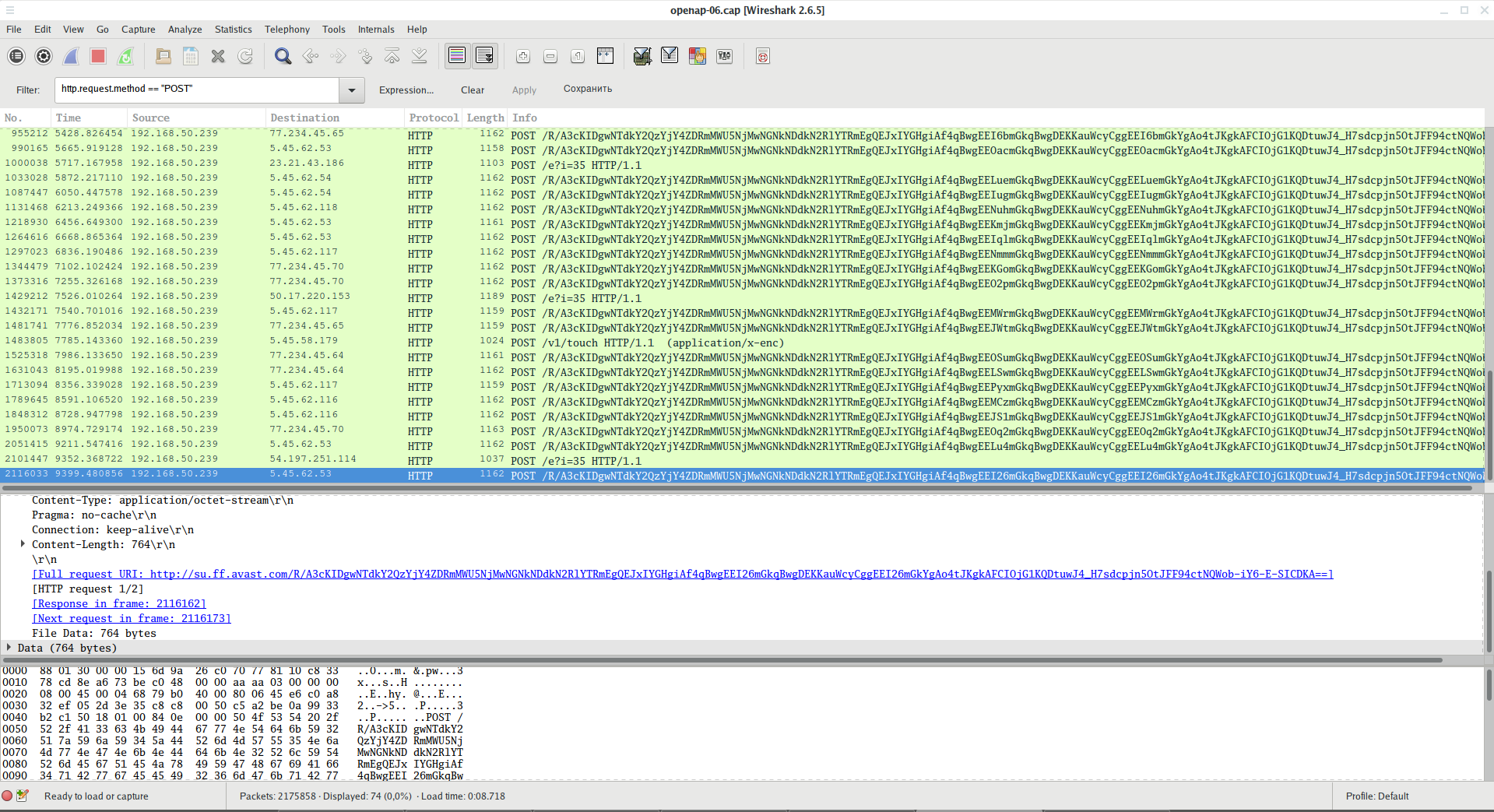
The data sent by the POST method is also visible:
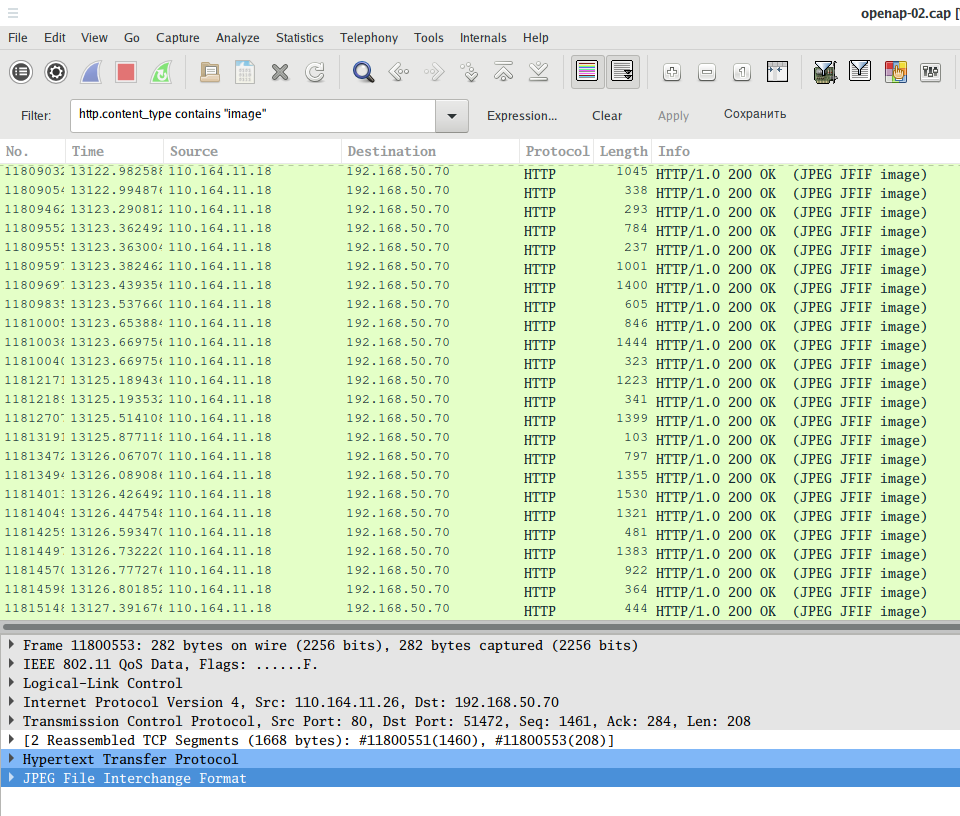
To search for any transferred images:
http.content_type contains "image"
To search for certain types of images:
http.content_type contains "gif" http.content_type contains "jpeg" http.content_type contains "png"
To search for files of a specific type:
http.content_type contains "text" http.content_type contains "xml" http.content_type contains "html" http.content_type contains "json" http.content_type contains "javascript" http.content_type contains "x-www-form-urlencode" http.content_type contains "compressed" http.content_type contains "application"
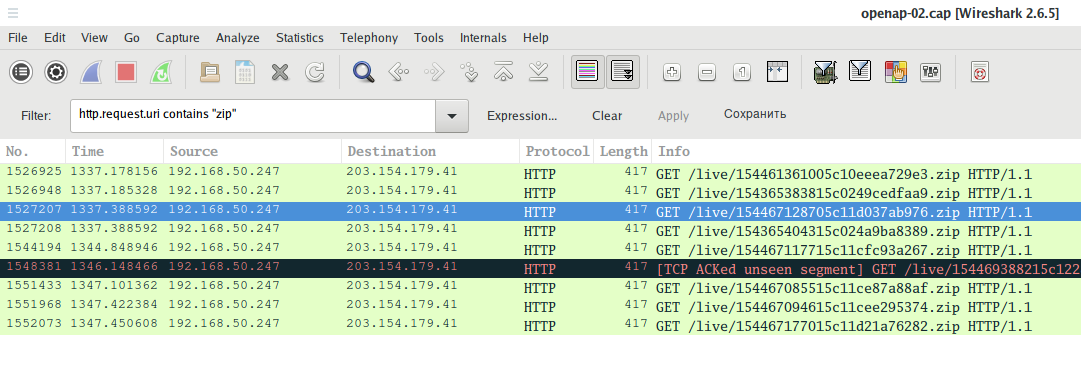
Wireshark filters to extract files of a certain type. For example, to search for transferred ZIP archives:
http.request.uri contains "zip"
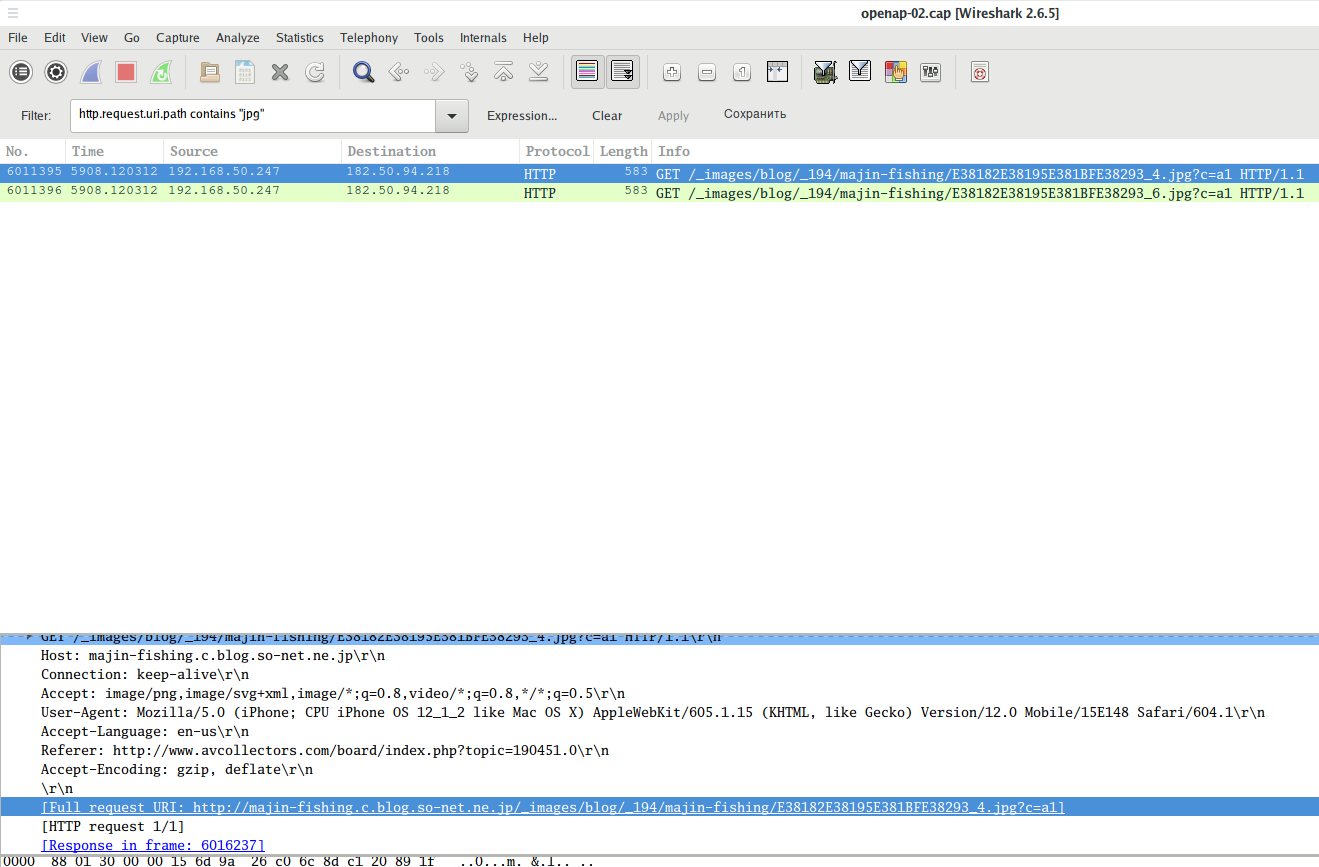
Instead of http.request.uri for greater accuracy, you can use the http.request.uri.path or http.request.uri.query filters, for example, to search for requests to download JPG files (links to pictures):
http.request.uri.path contains "jpg"
A filter that shows only the data sent by the POST method:
http.request.method == "POST"
A filter that shows only the data transmitted by the GET method:
http.request.method == "GET"
Search for requests to a specific site (host):
http.host == "<URL>"
Search requests to a specific site by part of the name:
http.host contains "here.particle.name"
Conclusion
Now the number of applications and sites that do not use encryption is rapidly decreasing. Therefore, the danger of such interception decreases every year. Nevertheless, it still exists.
Even websites that use HTTPS can inadvertently give out data. For example:
It can be seen that the data on booking.com is transmitted from the user in an unencrypted form, so you can intercept this link.
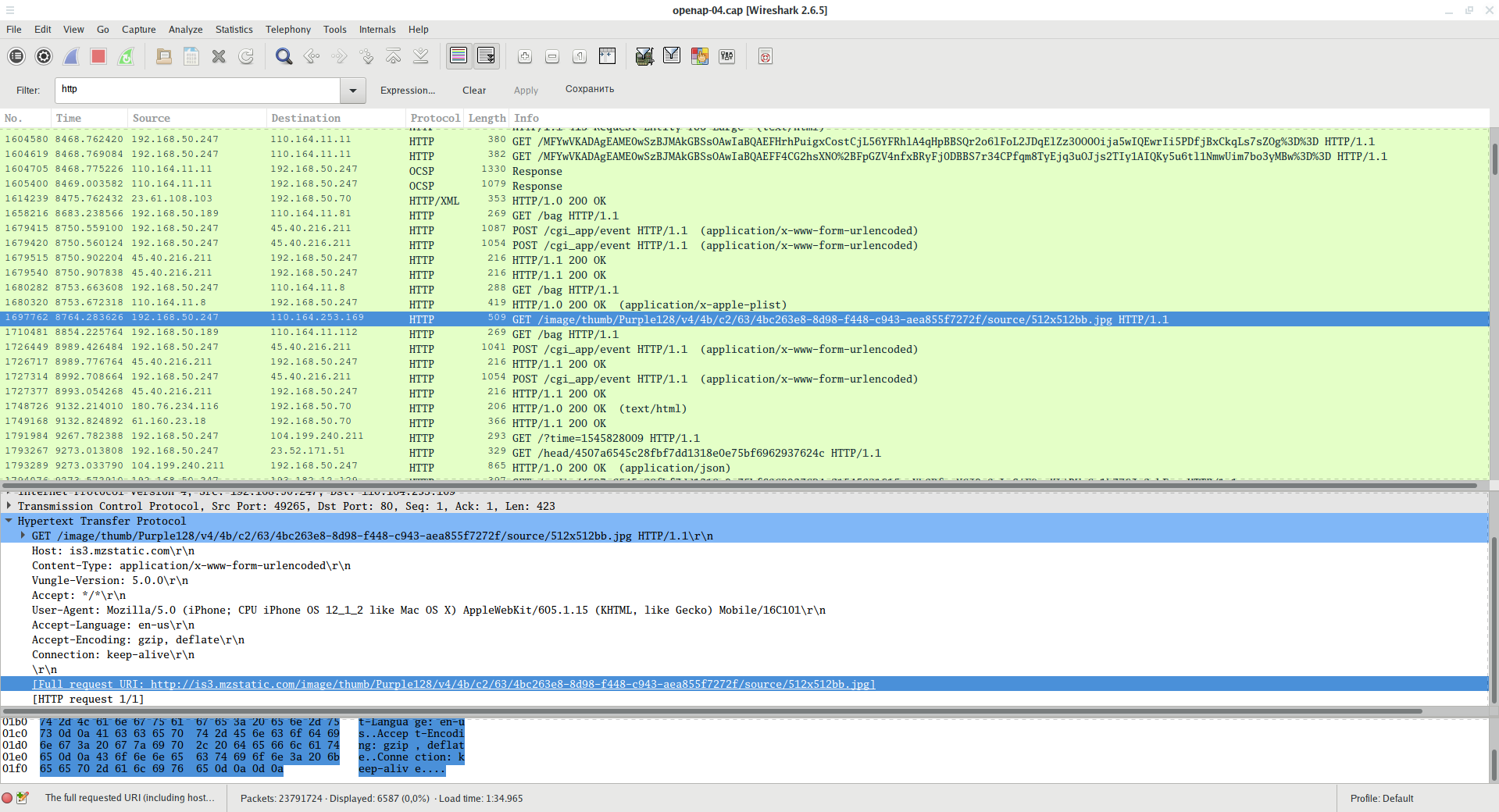
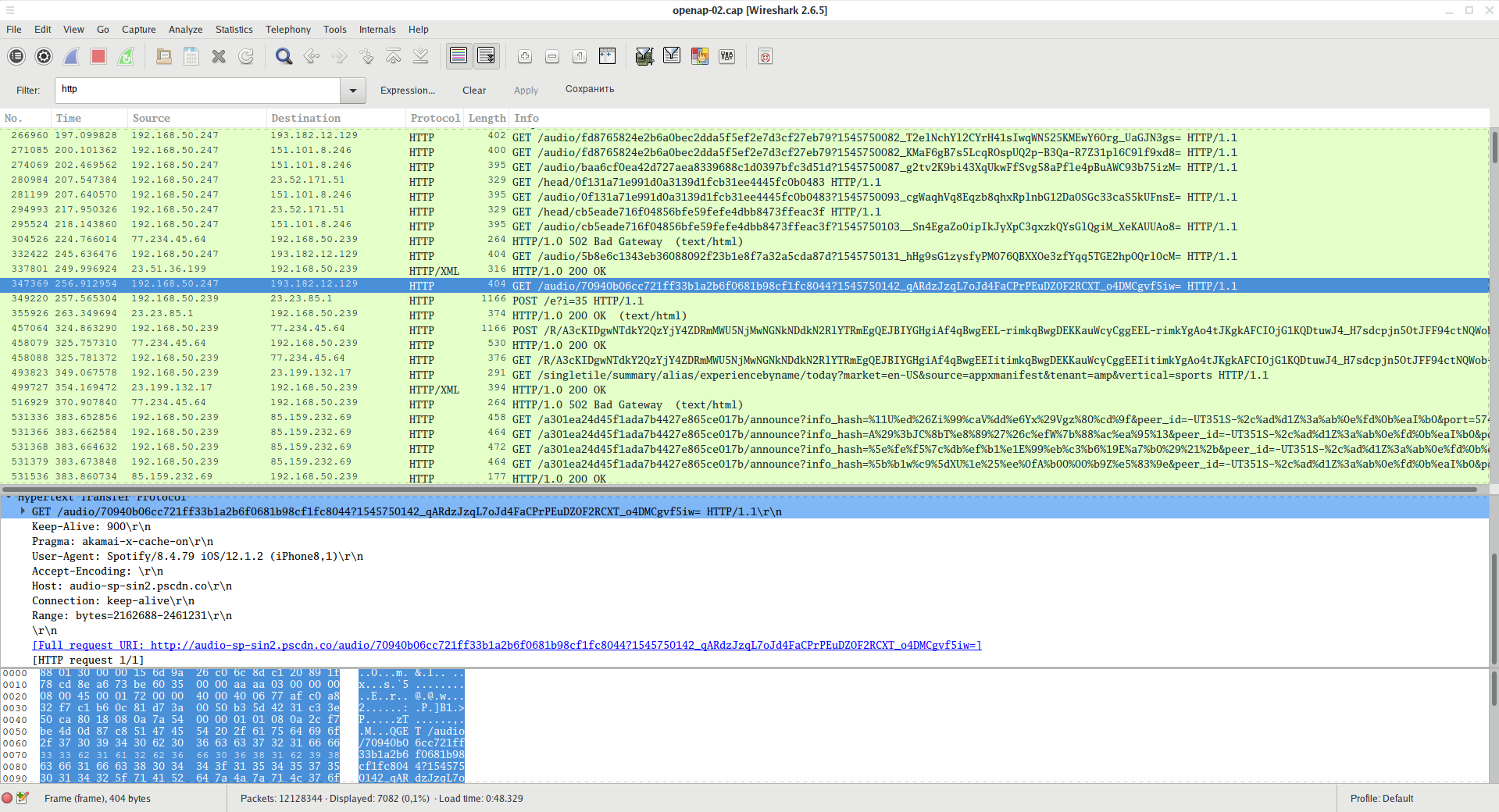
The iPhone application constantly downloads some (audio?) files without using a secure connection:
Popular (in some regions) qq.com either does not use encryption, or uses its own algorithm:
Guaranteed protection against such interception is the use of a trusted VPN service. Reliable VPN service can be considered the one that you set up by yourself, or VPN of your corporate network.
Related articles:
- Fast and simple method to bypass Captive Portal (hotspot with authorization on the web-interface) (76.3%)
- How to change MAC address in Linux, how to enable and disable automatic MAC change (spoofing) in Linux (67.4%)
- How to decrypt WPA traffic in Wireshark (66.2%)
- How to capture a Wi-Fi handshake in tcpdump (66.2%)
- Wireshark Filters (65%)
- What is HNAP, how to find and exploit routers with HNAP (RANDOM - 1.2%)





Very Good.
spasibo