How to find out local IP addresses of ISP
Quite often, Internet service providers use NAT to reduce consumption of public IP addresses. As a result, it turns out that many users have one public IP address. There is not much difference to users (especially if they don’t need a public IP, for example, for a web server), but for such a program as Router Scan by Stas'M, these users are out of access.
How to find out the local IP addresses of Internet Service Provider users
However, if you are an ISP client, then it’s quite realistic to find the IP of other clients on the local network. For scanners, including Router Scan, there is no difference – it can perfectly scan the local range. Local networks use several ranges of IP addresses, some of which are quite large. Therefore, you need to know what exactly to scan – which particular range. You can, of course, run a full scan of 10.0.0.0/8 (this will require long time). But by doing preliminary network research, you can greatly reduce target sub-networks and scan time.
How to find out the ranges of the local subnet of an ISP
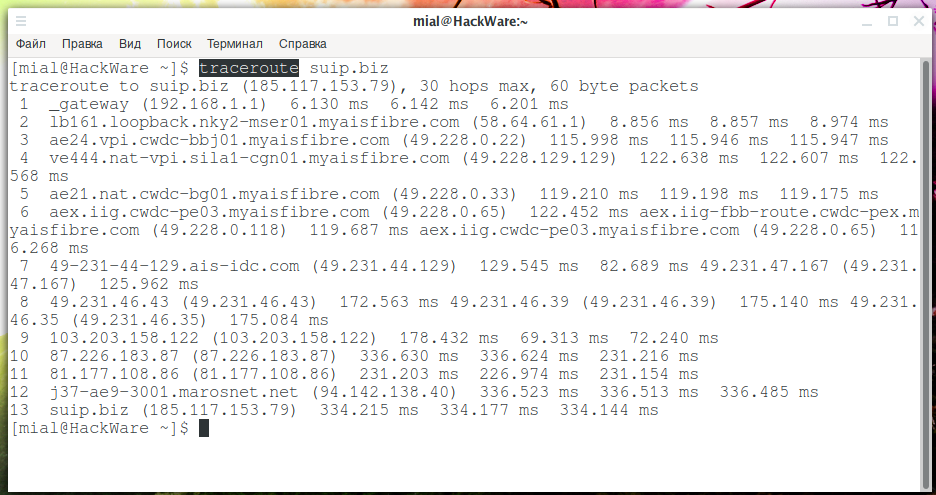
Let’s trace the route IP packetes before they reach the global network.:
traceroute suip.biz
First line:
1 _gateway (192.168.1.1) 9.314 ms 9.661 ms 9.637 ms
This is my own router.
The following three addresses tell us about the network 10.0.0.0/8:
2 10.20.48.1 (10.20.48.1) 9.886 ms 13.107 ms 16.762 ms 3 10.246.245.241 (10.246.245.241) 19.784 ms 20.412 ms 20.399 ms 4 10.185.252.29 (10.185.252.29) 20.797 ms 20.774 ms 20.728 ms
But the network 10.0.0.0/8 is really large (2563 = 16,777,216 addresses). The Internet service provider often simply does not need such a large network and it uses only its parts – subnets in which users are compactly assembled.
It can be assumed that the first IP (10.20.48.1) is the gateway for all users that are located somewhere in 10.20.48.1-10.20.60.255.
You can try to scan these ranges. But the key hint was given by the ZMap program. I ran a scan of the entire range looking for hosts:
sudo zmap -p 80 10.0.0.0/8 -o zmap.txt -r 300
But I didn’t have to wait for almost a day until completion (via Wi-Fi scanning is slow, but I’m connected that way). The ZMap scanning algorithm is such that it will check the hosts not sequentially, but in a disparity over the entire specified range. And if users are really compactly located in certain subnets, then already in a short time (15 minutes) one can understand exactly where they are:
cat zmap.txt | sort
Users were concentrated in rather small ranges:
- 10.20.160.0-10.20.162.255
- 10.20.48.1-10.20.63.255
These observations do not exclude that users may be on other subnets too – this can only be verified by a longer scan.
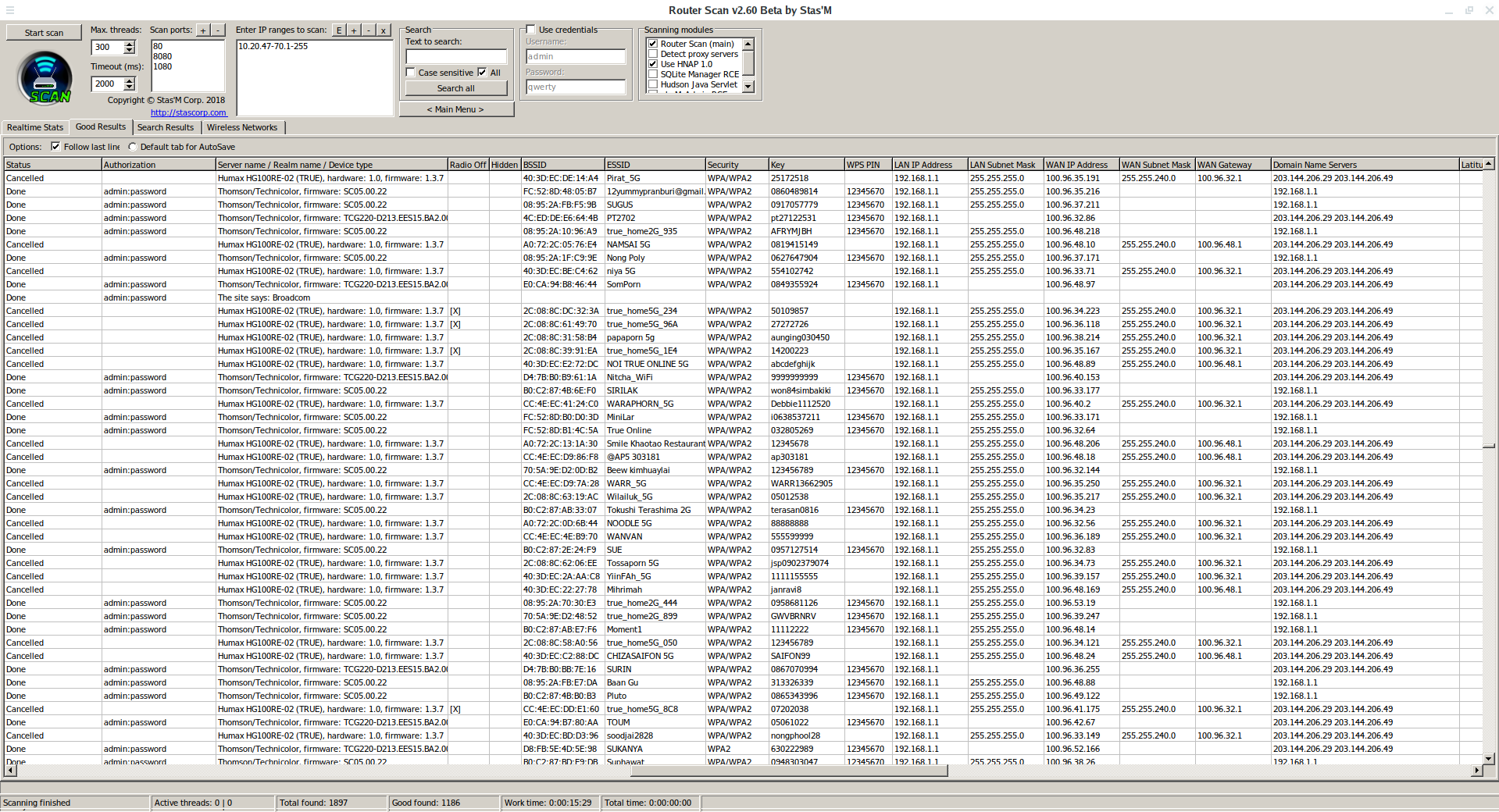
I added these ranges to Router Scan by Stas'M and got about 1200 good results:
Uploading to 3WiFi showed that there are a lot of new APs.
That’s all?
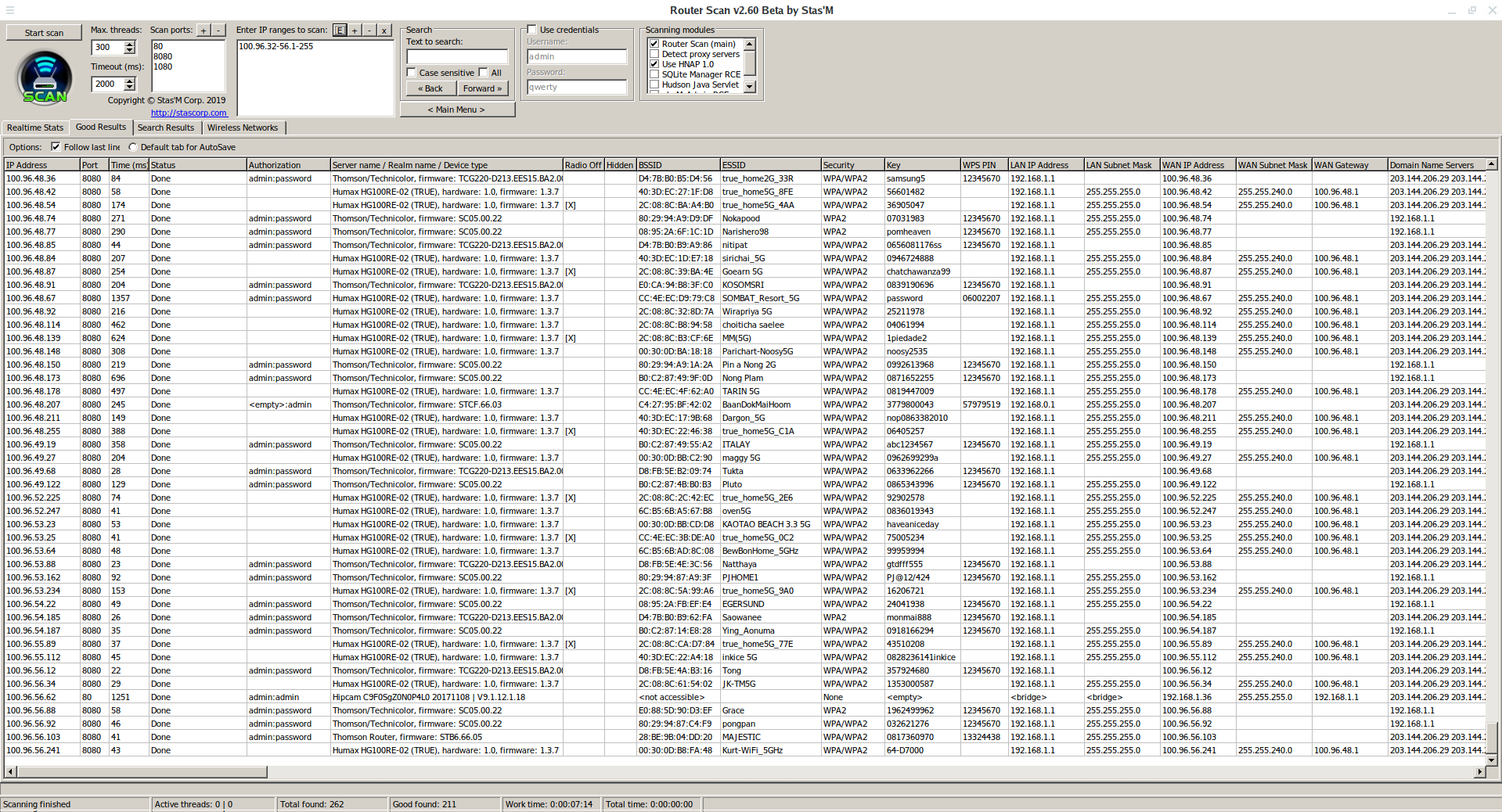
Look carefully at the WAN IP Address column in the screenshot above.
They are located compactly. But that's not all. Whois program:
whois 100.96.35.140
it told me that they belonged to the range 100.64.0.0/10 (that is, 100.64.0.0 - 100.127.255.255). And that this is Shared Address Space, that can only be used in Service Provider networks or on routing equipment that is able to do address translation across router interfaces when addresses are identical on two different interfaces.
These addresses are non-routable and inaccessible to the external network, but ping proved that I have contact with them:
ping 100.96.35.140
I analyzed the addresses and launched Router Scan on the 100.96.32.1-100.96.56.255 range:
There were 200 good results, and even with the unloaded previous access points, there were more than a hundred new ones!
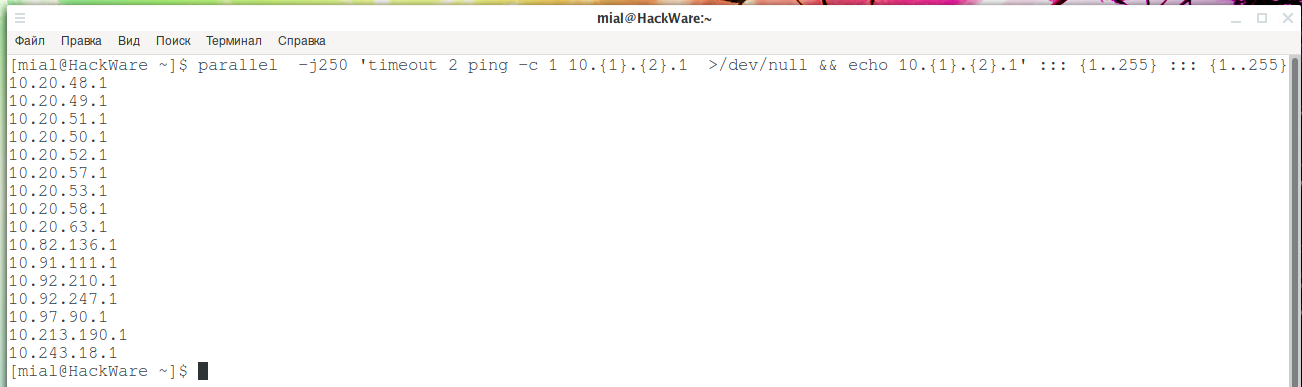
Using Parallel, you can very quickly search for addresses like 10.x.x.1, which may turn out to be default gateways:
parallel -j250 'timeout 2 ping -c 1 10.{1}.{2}.1 >/dev/null && echo 10.{1}.{2}.1' ::: {1..255} ::: {1..255}
Apparently, this method gave me a few more subnets:
You can search for live hosts without port scans using Nmap:
sudo nmap -sn 10.91.111.0/24
But if we don’t need to find all the live hosts at all costs, if we are only interested in those which have port 80 open, then everything can be done much faster with the help of ZMap:
sudo zmap -p 80 10.91.111.0/24 -r 300
Addresses from the local subnet 10.0.0.0/8 can be found even when at first glance they are not there. Here is an example of another ISP, where there are no signs of a local network 10.0.0.0/8:
But the usual ping with a boost from parallel prove the opposite:
Maybe there are no routers – just some technical nodes. But while network research, it is still important.
This is a small note on how to scan Internet service providers from the inside. Summing up:
- scanning local ranges we get access to devices that cannot be scanned from the global network
- after a little analysis, you can find out the range of the local network (10.0.0.0/8, 172.16.0.0/12 or 100.64.0.0/10) and even reduce the number of IP for scanning
So, for private networks, the following address ranges are used:
- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
- 100.64.0.0/10
Related articles:
- Tracerouting tools and methods (70.7%)
- Best Kali Linux tools in WSL (Windows Subsystem for Linux) (Part 1) (66.7%)
- Tracerouting networks with complex topology. How to detect NAT (61.9%)
- Utilities for information gathering, OSINT and network analysis in Windows and Linux (61%)
- How to hack Wi-Fi in Windows (55.9%)
- Examples of using HTTP headers for “hidden” data transfer (RANDOM - 2.2%)