Attack on devices in the local network through a vulnerable router
If you have access to a router, is it possible to access devices on the local network? To answer this question, let's figure out how the home LAN works.
How does a home LAN work?
In a home local area network, the basis is a router – a rather complex network device. This device provides the local network. When connecting a new device to the local network, a router, using the DHCP protocol, assigns an IP address to the new device. As a range of IP addresses in home networks, 192.168.1.0/24, 192.168.0.0/24 or 192.168.100.0/24 are usually used.
That is, your computer or phone connected to the Internet through a router has a local IP address.
Perhaps you have already heard about NAT and you even know that this technology allows the ISP to use one single public (white) IP address for all or for many of its clients. But NAT is used not only at the level of the Internet service provider, but also already in your router. Let's look at NAT in a bit more detail.
NAT
NAT is a technology that allows multiple devices to access the Internet using the same IP address. By the way, NAT is already used in your local network with a router, that’s why all your devices can access the global network and each of them does not need to have an external IP.
Therefore, this is a commonly used technology. Perhaps you have been using it for many years without even knowing about it. It really brings a lot of benefits, but it has a drawback – it allows you to make connections ‘one way’. That is, if your computer initiated an Internet connection, then it will send it to the router, the router will do two things: 1) remember that the request came from a specific device and 2) send this request to the Internet. When the answer arrives, the router still “remembers” that this request was made for a specific device on the local network, and will send a response to that particular device. And so it happens every time.
But if a new HTTP request from the WAN comes to the router (not a response to the request, but a new request), then the router does not know who it is for on the local network (unless port forwarding is configured). Therefore, the router does nothing with this incoming request.
Is it possible to access a computer on a local network if there is access to a router?
It seems that the answer is obvious – NAT technology does not give such an opportunity in principle: connecting to local devices that do not have a public IP, but only have a local IP of the form 192.168.0.*, Is not possible.
But I started with the fact that the router is a very complex network device. And this device supports many functions for setting up a network, in particular, it supports:
- Setting static IP addresses for devices on the local network bypassing the DHCP protocol
- Port Forwarding
Port Forwarding
Forwarding, which is also called ‘Port mapping’ allows ones to do a very wonderful thing – with it devices behind NAT, that is, a device on a local network that has a local network IP address may become available globally. The rules can be configured very flexible, you can make forwarding multiple ports to one, or from one to several, or several to several, and so on. But for our purposes, the following rule is most interesting, which can be expressed in words as follows:
The request that came to the port of router 22 should be redirected to port 22 of the device with the IP address 192.168.0.5.
Port numbers do not have to be the same, so the rule might be this:
The request that came to the port of the router 50080 should be redirected to port 80 of the device with the IP address 192.168.0.5.
As a result, we will get access to port 80 (it is usually listened to by the web server) of the device on the local network 192.168.0.5.
This means that we can access any open port and the service running on it on the local network! This can be a web server, SSH, FTP, Windows network protocols, etc.
List LAN devices. Configure static addresses on the local network
To perform an attack on devices on the local network through a vulnerable router, we need to know what local IP addresses do these devices have.
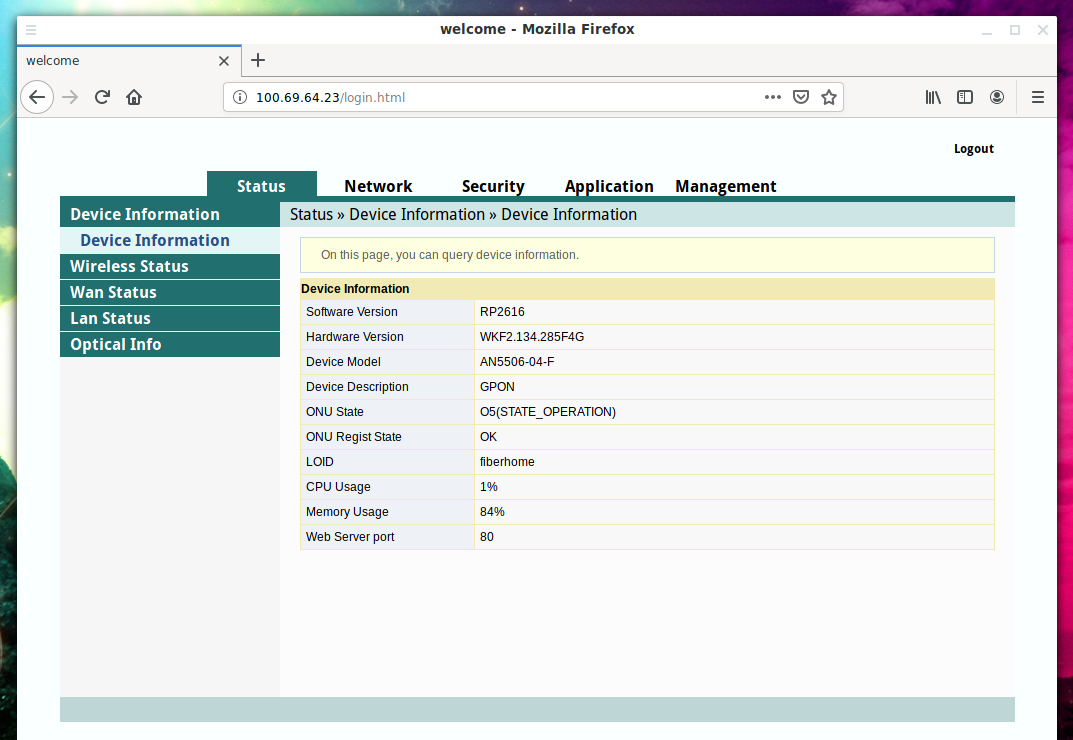
Consider an example. On the Internet service provider's local network there is a router with IP address 100.69.64.23 to which administrative access is obtained.
All (or almost all) routers can show information about currently connected clients. This information may be:
- on the router status page
- on the DHCP configuration page
- on the LAN status page
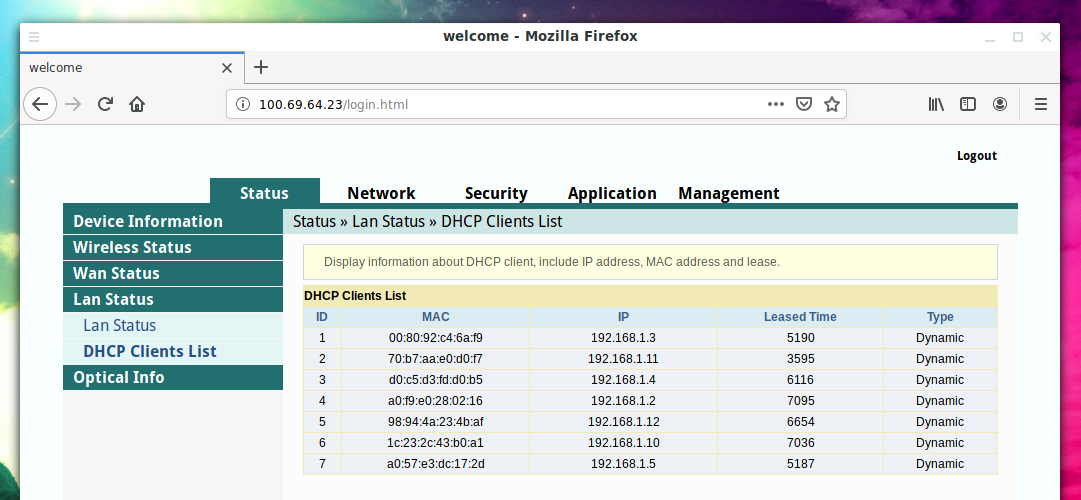
For example, on this router, information is listed on the DHCP Clients List page:
This router shows only the MAC address and local IP address of the devices. In addition to this information, many routers also show whether it is a mobile device or a desktop computer. Since there is no such information here, I need to independently guess the type of device based on its manufacturer. The manufacturer of the device can be found by the MAC address on this service: https://suip.biz/?act=mac
For example, the following information was found for MAC 00:80:92:c4:6a:f9:
008092 (base 16) Silex Technology, Inc.
2-3-1 Hikaridai,
Kyoto 619-0237
JP
I'm not interested in mobile phones and tablets – as a rule, all ports are closed on them. I'm interested in laptops and desktop computers, because they can run services that listen on ports.
Of all the devices, the most interesting seemed to me the following
00:80:92:c4:6a:f9 192.168.1.3 a0:f9:e0:28:02:16 192.168.1.2
The reason is as follows:
- their MAC addresses do not seem to belong to mobile phone manufacturers
- their IP addresses are the very first – that is, wired devices are first connected to the router, and then devices over Wi-Fi
- these devices are not in the list of wireless clients:
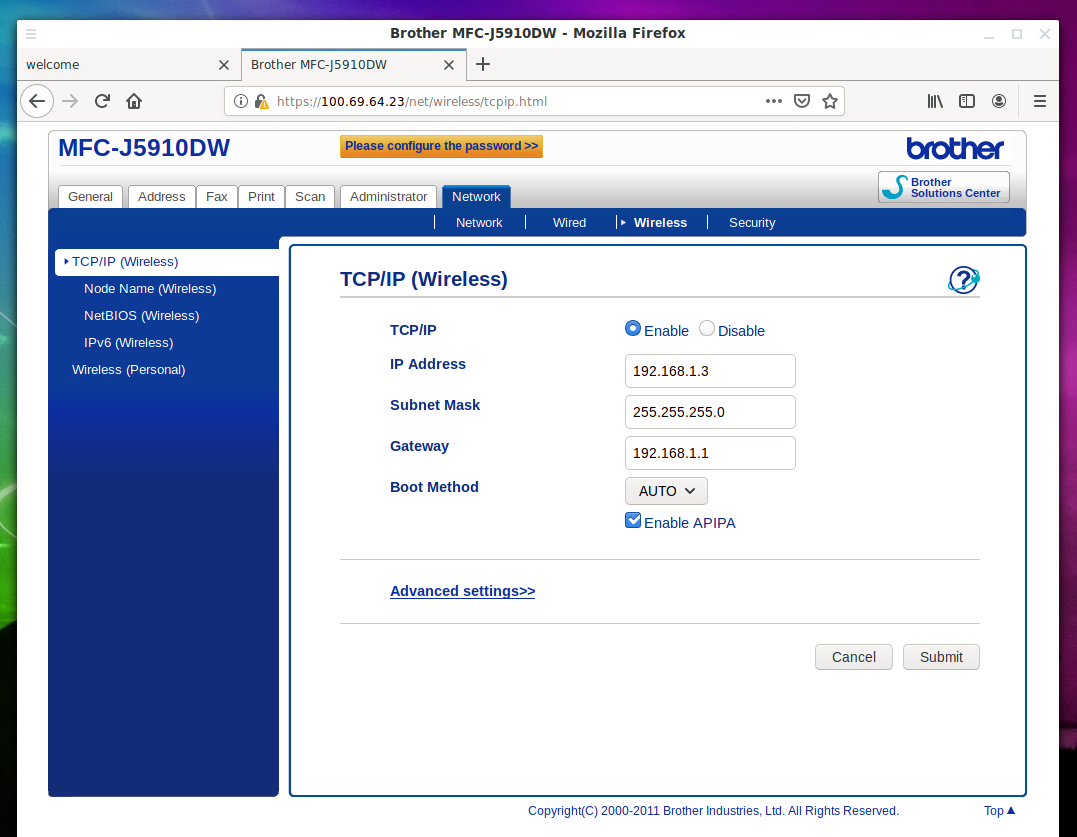
If the attack is planned for a long time, then certain devices can be assigned static IP addresses. The fact is that port forwarding is configured relative to the IP address. And the target device can change the IP address to an arbitrary one after a while. If this happens, then the port forwarding rules will work – but that time they will send packets to another device that has taken this IP address.
To avoid this, you can bind the IP to the MAC address – I have not yet met routers that are not able to do this. The setup is simple enough.
Port Forwarding Setting
Depending on the model of the router, this tab may be called
- Forwarding
- Port forwarding
- Port mapping
- other
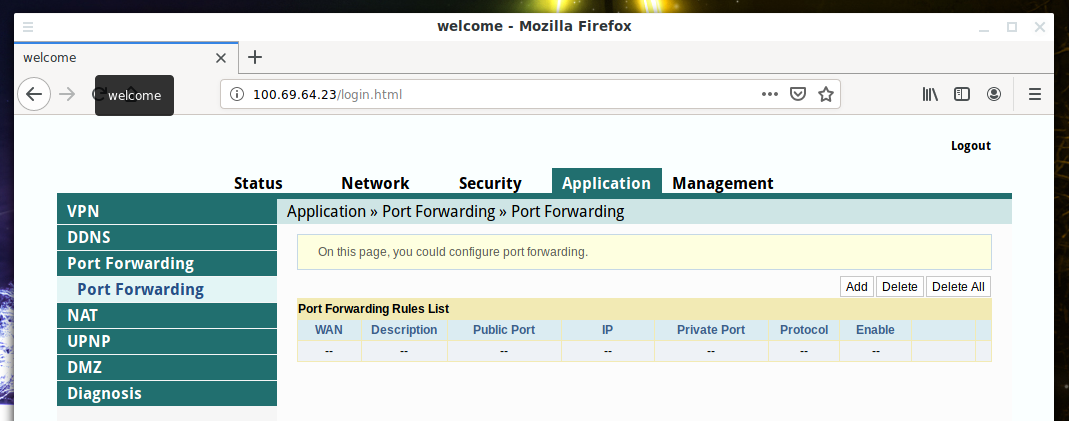
For example, on the router in question, I found this tab along the path Application → Port Forwarding:
In total, ports 1-65535 and routers allow forwarding ranges, that is, 65 thousand ports do not have to be configured manually one by one.
But there is a very important point – we cannot configure the forwarding of the port on which the router's web server is running. That is, if the router listen to port 80, then this port should be an exception. Otherwise, the following will happen: neither we, nor even the owner of the router can no longer get into the administration panel of the router until settings are reset to default.
Please note that some routers do not work on port 80, but on port 8080 or 443.
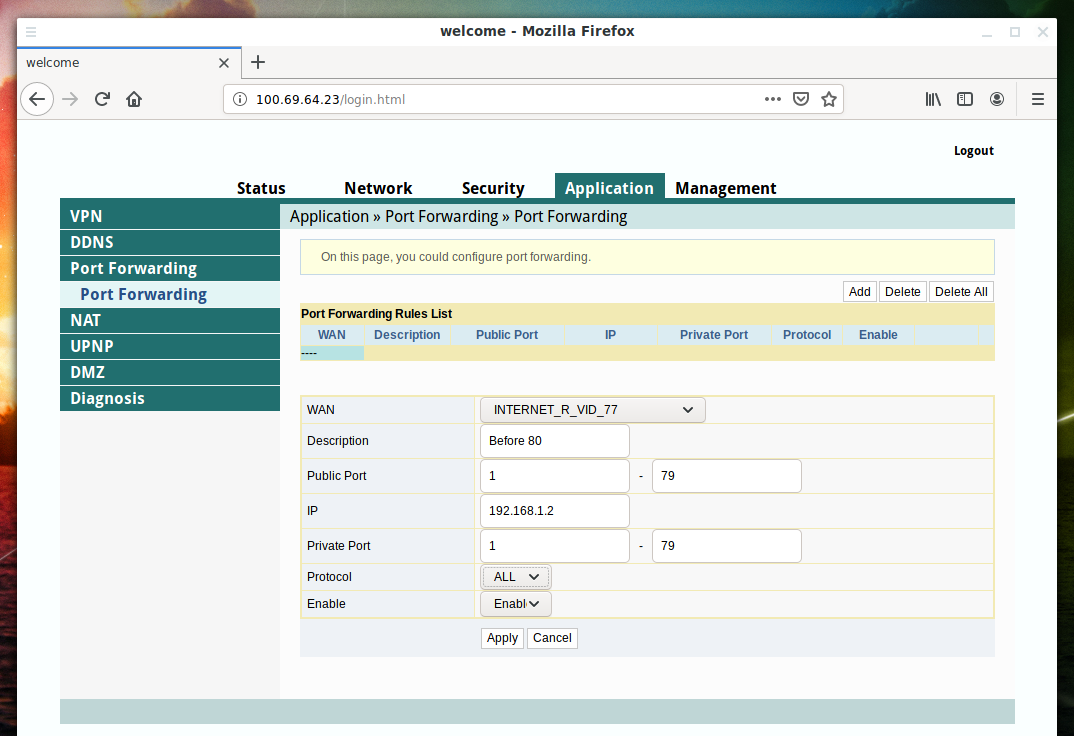
So, if the web interface of the router works on port 80 and we want to access the local resources of the device with IP 192.168.1.2, then we need to set the following three rules:
- Forwarding ports 1-79 to ports 1-79 of address 192.168.1.2
- Forwarding ports 81-65534 to ports 81-65534 of address 192.168.1.2
- Forwarding port 65535 to port 80 of address 192.168.1.2
The first two rules with ranges (hopefully) are obvious. The third rule we redirect requests that came to port 65535 to port 80 of the local computer, because there might be a web server or something else interesting.
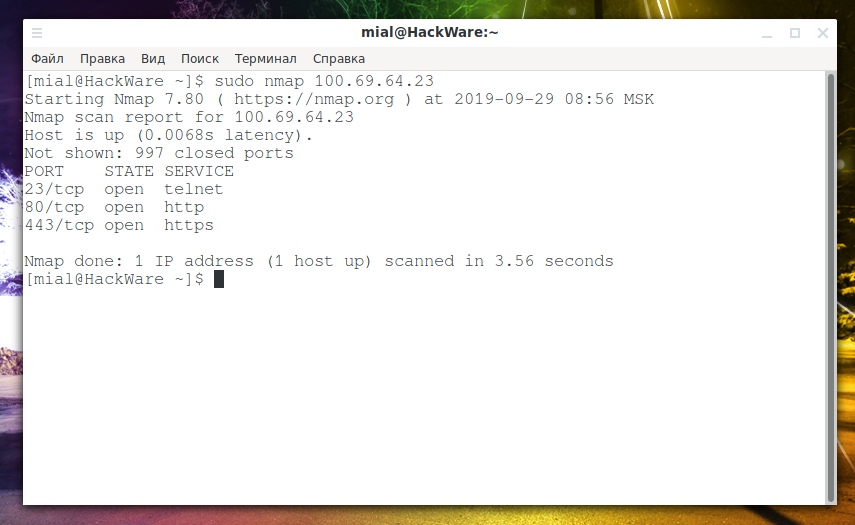
To begin with, we will do a control measurement, which ports are open:
sudo nmap 100.69.64.23
This command will show open ports on the router:
Add the first rule:
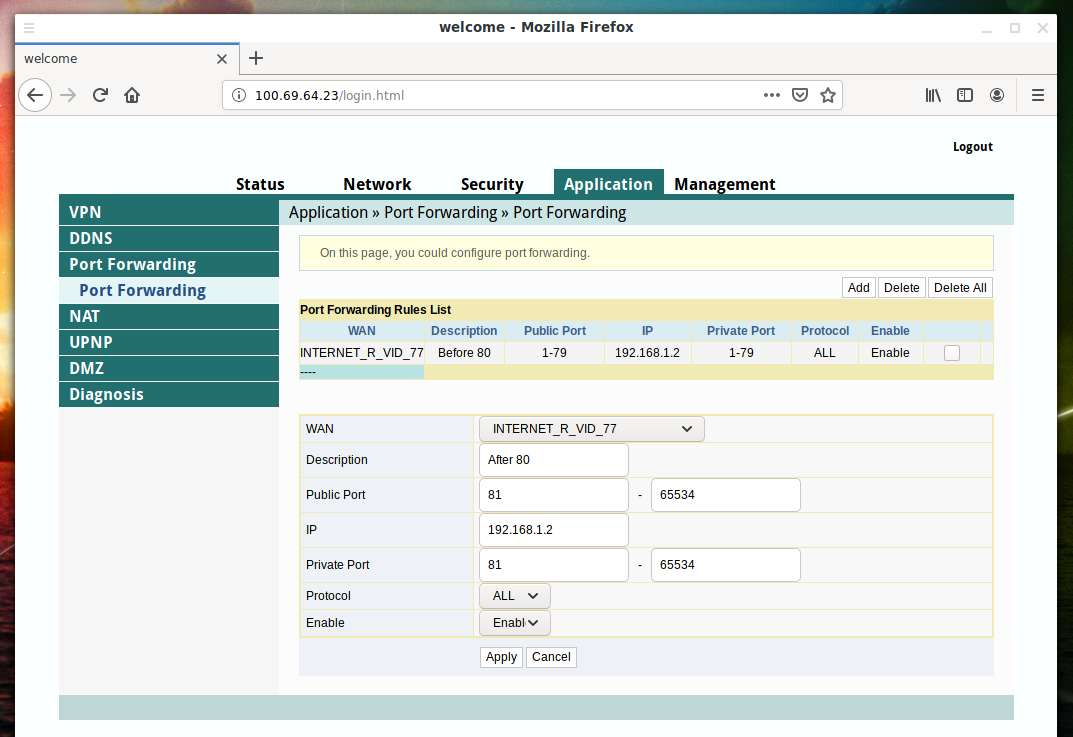
Second:
Third:
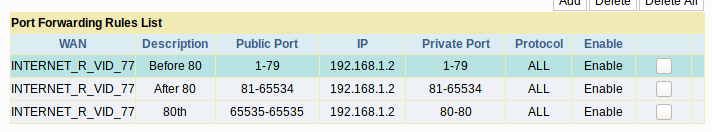
We get:
We re-scan the ports:
sudo nmap 100.69.64.23
We ascertain – we failed. The 80th port is the port of the router itself, and on the device with IP 192.168.1.2 the scanned ports are closed.
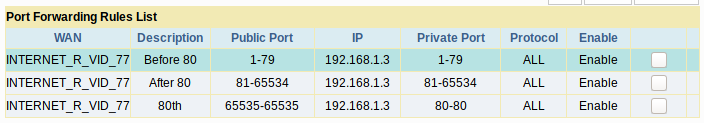
Do not despair – I redo all the rules for port forwarding to IP 192.168.1.3:
And again, we scan the ports:
sudo nmap 100.69.64.23
Let me explain, although the Nmap command is the same, but in fact the last time we scanned ports of on device in the local network with IP 192.168.1.2. And the last command is already scanning ports on 192.168.1.3.
And here we were lucky:
Starting Nmap 7.80 ( https://nmap.org ) at 2019-09-29 09:08 MSK Nmap scan report for 100.69.64.23 Host is up (0.017s latency). Not shown: 993 closed ports PORT STATE SERVICE 21/tcp open ftp 23/tcp open telnet 80/tcp open http 443/tcp open https 515/tcp open printer 631/tcp open ipp 9100/tcp open jetdirect Nmap done: 1 IP address (1 host up) scanned in 5.83 seconds
Let me remind you that all these ports, except 80, are open on a device that does not even have a public IP address, it has an IP address of 192.168.1.3.
And how to check the 80th port on 192.168.1.3? We do it like this:
sudo nmap -p 65535 100.69.64.23
The port was closed.
To collect information about open ports, we’ll examine their banners:
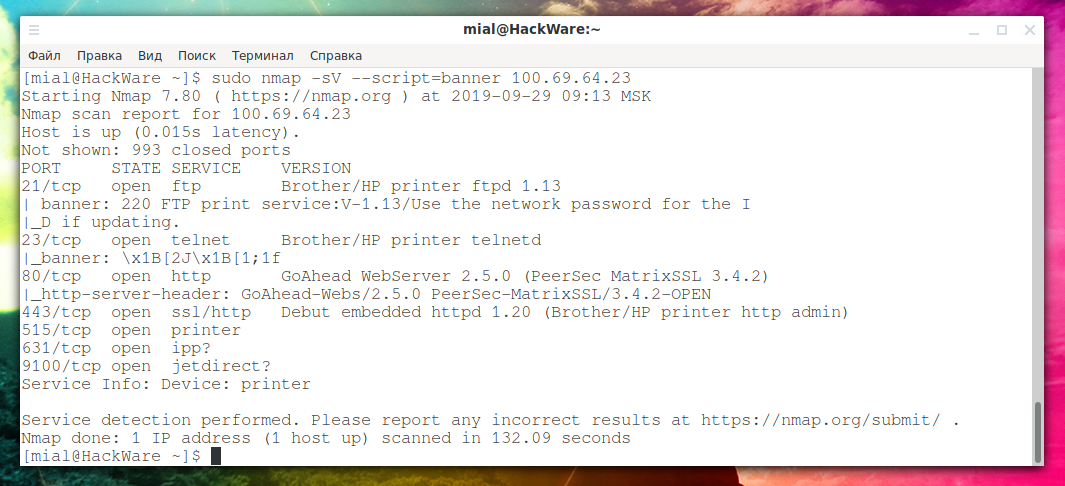
sudo nmap -sV --script=banner 100.69.64.23
We get:
PORT STATE SERVICE VERSION 21/tcp open ftp Brother/HP printer ftpd 1.13 | banner: 220 FTP print service:V-1.13/Use the network password for the I |_D if updating. 23/tcp open telnet Brother/HP printer telnetd |_banner: \x1B[2J\x1B[1;1f 80/tcp open http GoAhead WebServer 2.5.0 (PeerSec MatrixSSL 3.4.2) |_http-server-header: GoAhead-Webs/2.5.0 PeerSec-MatrixSSL/3.4.2-OPEN 443/tcp open ssl/http Debut embedded httpd 1.20 (Brother/HP printer http admin) 515/tcp open printer 631/tcp open ipp? 9100/tcp open jetdirect? Service Info: Device: printer
Not very interesting – apparently the local network, these are all functions related to the printer.
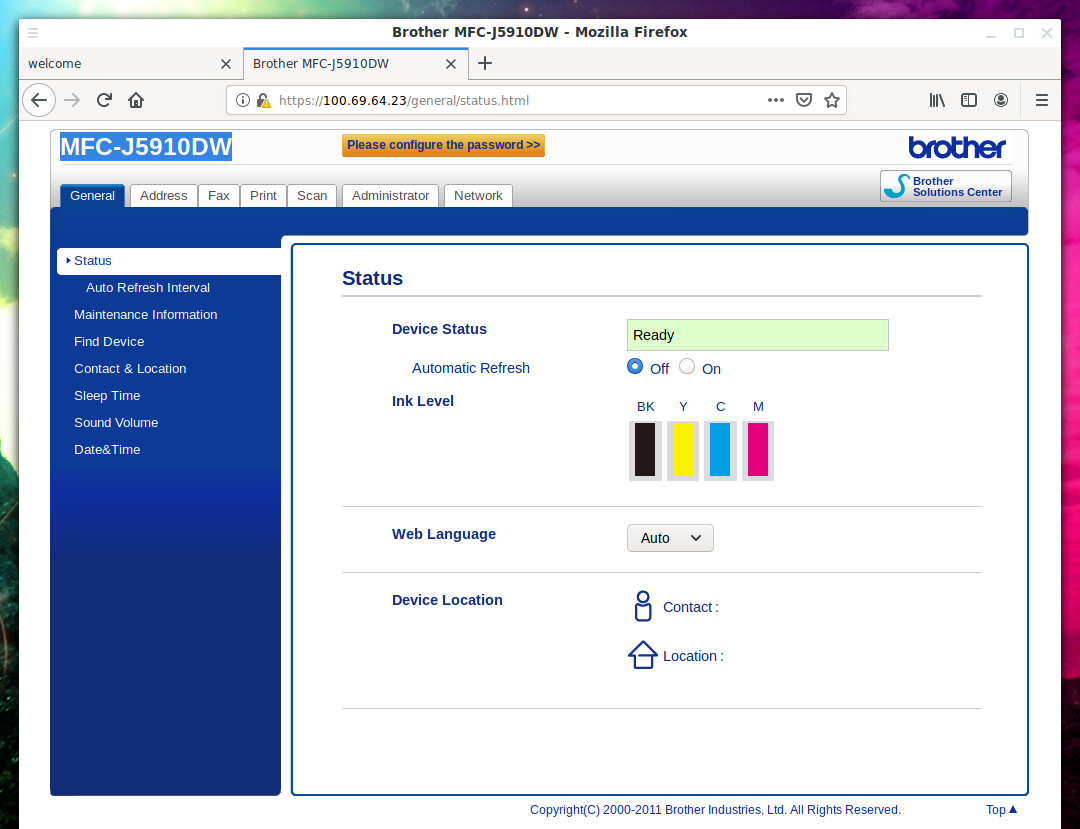
To connect to the HTTPS port, just open the link in a web browser: https://100.69.64.23:443
And there we see the interface of the multi function device (printer-coper-scanner) MFC-J5910DW:
Once again, for those who are lost, this is a device with the IP address 192.168.1.3!
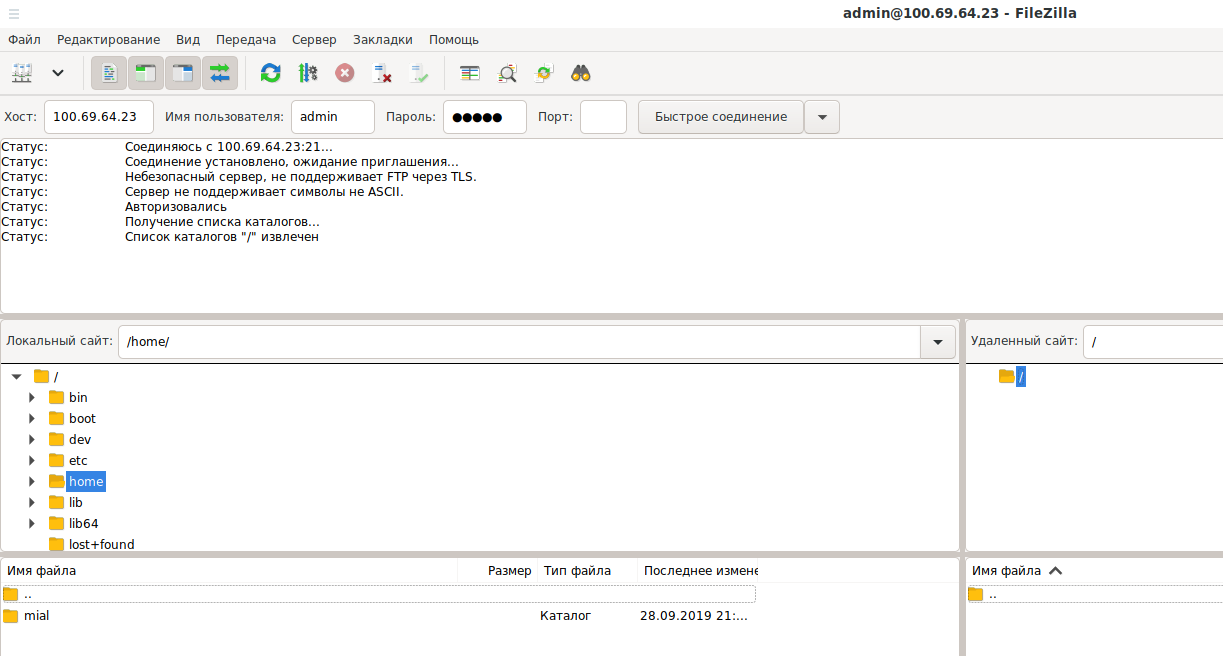
I also managed to connect to FTP:
Conclusion
This is the most universal way to attack a local network with a vulnerable router, since almost all routers support port forwarding.
Other attack vectors:
- DNS spoofing to the attacker's servers and traffic manipulation based on fake DNS responses (all routers are affected)
- redirecting traffic using a VPN channel to an attacker’s equipment (only more advanced models with VPN support are affected)
- access to media connected to the router (only models with this functionality are affected)
Related articles:
- How to speed up the scanning of large networks ranges (78.3%)
- Network pivoting: concept, examples, techniques, tools (62.6%)
- sshprank: SSH mass-scanner, login cracker and banner grabber (55.6%)
- RouterSploit User Manual (54.6%)
- SMB and Samba Security Audit Tools (54.4%)
- badKarma: Advanced Network Reconnaissance Assistant (RANDOM - 3.2%)