Proxy types, how to use proxy, how to check the quality of proxies
Table of contents
1. What is a proxy, how do they differ, types of proxies
3. Where to download proxy lists
5. How to check proxy anonymity without third-party services
6. Other proxy detection methods
7. Tor Browser Request Headers
What is a proxy, how do they differ, types of proxies
In this article we will consider the most important thing about proxies: what is a proxy, what are the types of proxies, how do they differ. We will look inside their work: we will see how these proxies reveal our real IP in their headers and learn how to independently verify the anonymity of the proxy.
A proxy is a program that performs an action for another program, that is, it is an intermediary.
Web proxies are a variety of proxies that are designed to perform requests to websites and web applications.
Web proxies can be used for the following purposes:
- speed up website loading
- testing online services;
- bypassing the restrictions of the LAN Administrator on access to certain website addresses;
- hiding a real IP address and anonymous access to websites;
- gaining access to closed websites for viewing by users of certain countries;
- and many other purposes.
In fact, proxy and web proxy is a collective name that includes many different programs and protocols for performing this function.
Since proxies are sometimes used to anonymize and hide a real IP address, you need to clearly understand how they work and their configuration options in order to accurately understand the possible risks.
We ask ourselves a question: does using a web proxy mean that our IP address is securely hidden from the site we are accessing? We will answer this question a bit later.
Consider the types of proxies from a technical point of view, namely by types of protocols:
HTTP proxies: allow you to visit websites and download files using the HTTP protocol (requests are transmitted in plain text, without encryption).
HTTPS proxies: (also called SSL proxies): with these proxies you can browse sites using the HTTP and HTTPS protocols (data is transmitted in encrypted form). With special software, they can be used with any protocol, such as SOCKS proxies.
It should be noted that the proxies discussed above do not hide the fact that the proxy requests to a web site. Quite often they add HTTP headers specific to proxies, and sometimes even (depending on the settings) they can show in the headers the IP address of the host for which they are making a request. That is, using a proxy does not mean that your IP address is reliably hidden from the site you are accessing!
SOCKS 4 proxy: can be used with any TCP/IP protocol with any destination address and port. Unlike HTTP proxies, SOCKS transfers all data from the client without adding anything from itself, that is, from the point of view of the destination server, the data received by it from the SOCKS proxy is identical to the data that the client would transmit directly without proxying. SOCKS is more universal, it does not depend on specific protocols of the application level and operates at the level of TCP connections. But the HTTP proxy caches data and can more carefully filter the contents of the transmitted data.
SOCKS 5 proxy: in addition to the capabilities of SOCKS 4, it can also use the UDP protocol, make DNS queries and use the BIND function for port forwarding, supports domain names and IPv6 addresses. And perhaps the main difference is authentication support. That is, you can set a username and password, without which it is impossible to use a proxy.
What type of proxy to choose? First of all, it depends on what types of proxies the program you are going to use supports. If it supports only one type of proxy, then the answer is obvious. If several types of proxies are supported, then you can give preference to SOCKS 5 as the most universal option.
Proxy Anonymity
Anonymity is an interesting question – in this case we are talking about anonymity for the site to which the request is being made. The proxy owner sees IP of a proxy user anyway. But the proxy itself can transmit the IP address to the site for which the request is performed. Consider the following classification of proxies by anonymity:
Without anonymity: the remote host knows your IP address and knows that you are using a proxy.
Low anonymity (also called transparent proxies): the remote host does not know your IP, but knows that you are using a proxy.
Average anonymity: the remote host knows that you are using a proxy and thinks it knows your IP, but this IP is not yours (these are usually multi-network proxies that show their incoming interface as REMOTE_ADDR for the target host).
Highly anonymous: the remote host does not know your IP and does not have direct evidence of the use of proxies (HTTP header that proxies like to send is absent). If such hosts do not send additional header, then they can be considered highly anonymous. If the anonymous proxy supports keep-alive, then it can be considered extremely anonymous. Nevertheless, such hosts are most likely a honey-pot (decoys to monitor user actions and identify new methods of attacks and hacks).
It should be noted that this separation by type of anonymity applies only to HTTP proxies. And this separation is based only on whether these proxies add headers to your request or not – then we can see these headers with our own eyes.
SOCKS4 and SOCKS5 cannot add anything to the headers of the HTTP protocol at all, since it works at a different level (at the TCP protocol level).
HTTPS (SSL) proxies also cannot add any headers, since HTTPS traffic passes through them in an encrypted form. Nevertheless, usually HTTPS proxies also support working with HTTP – and if a request comes from the site using this protocol, the proxy can send your IP address in the header. Remember that this information will come in handy very soon: that is, headers can only be added to HTTP traffic, but an HTTPS proxy is not a guarantee of anonymity, since the site can send a request using the HTTP protocol and we don’t know how the proxy behaves.
You can also mention other properties of the proxy: uptime (what fraction of the time they are available for users), their bandwidth, country affiliation, and other characteristics.
Where to download proxy lists
See the article How to parse proxy lists.
Prepared proxy lists (parsed addresses and ports are written in an easy-to-use format):
How to enable proxy
Proxies can be enabled at the application level or at the operating system level.
When you turn on the proxy in a certain program, only it will go online through the proxy, and the rest of the applications will connect directly.
When you enable proxies at the operating system level, this does not guarantee that all programs will access the Internet through a proxy — some programs ignore proxy system settings.
See the links on enabling proxies at the operating system level (the article itself talks about proxying traffic through Tor, but the proxy settings are identical – just specify the IP and port of your proxy):
- Setting up a mobile phone (Android) to use a proxy
- Configuring proxy settings in Windows
- Configuring proxy settings in Linux
- Configuring VirtualBox Virtual Machine Proxy Usage
How to enable proxies in web browsers
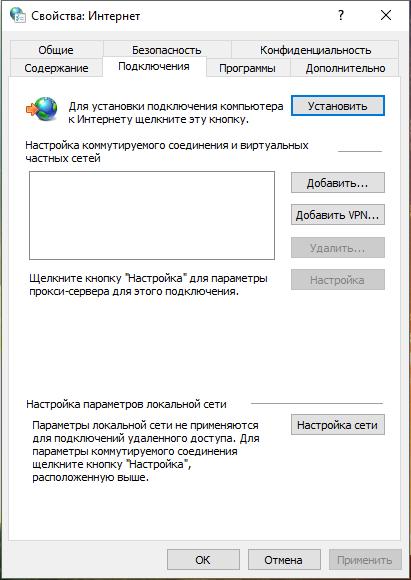
The Google Chrome, Opera, and Internet Explorer browsers use the same settings. Therefore, the changes will be effective immediately for all three browsers. In any of them, go to the Proxy settings, this window will open:
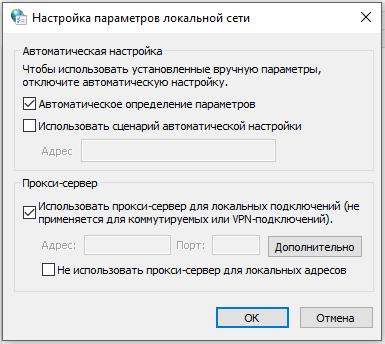
In the window, click ‘Network Settings’. In the new window that opens, check the ‘Use a proxy server for local connections…’ checkbox:
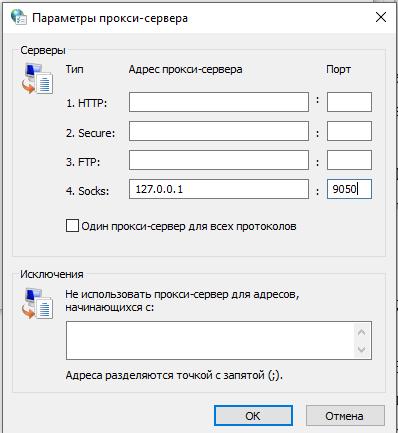
The ‘Advanced’ button will become active, click it. Select the desired proxy type and enter its IP and port:
Click OK in all windows to save your settings.
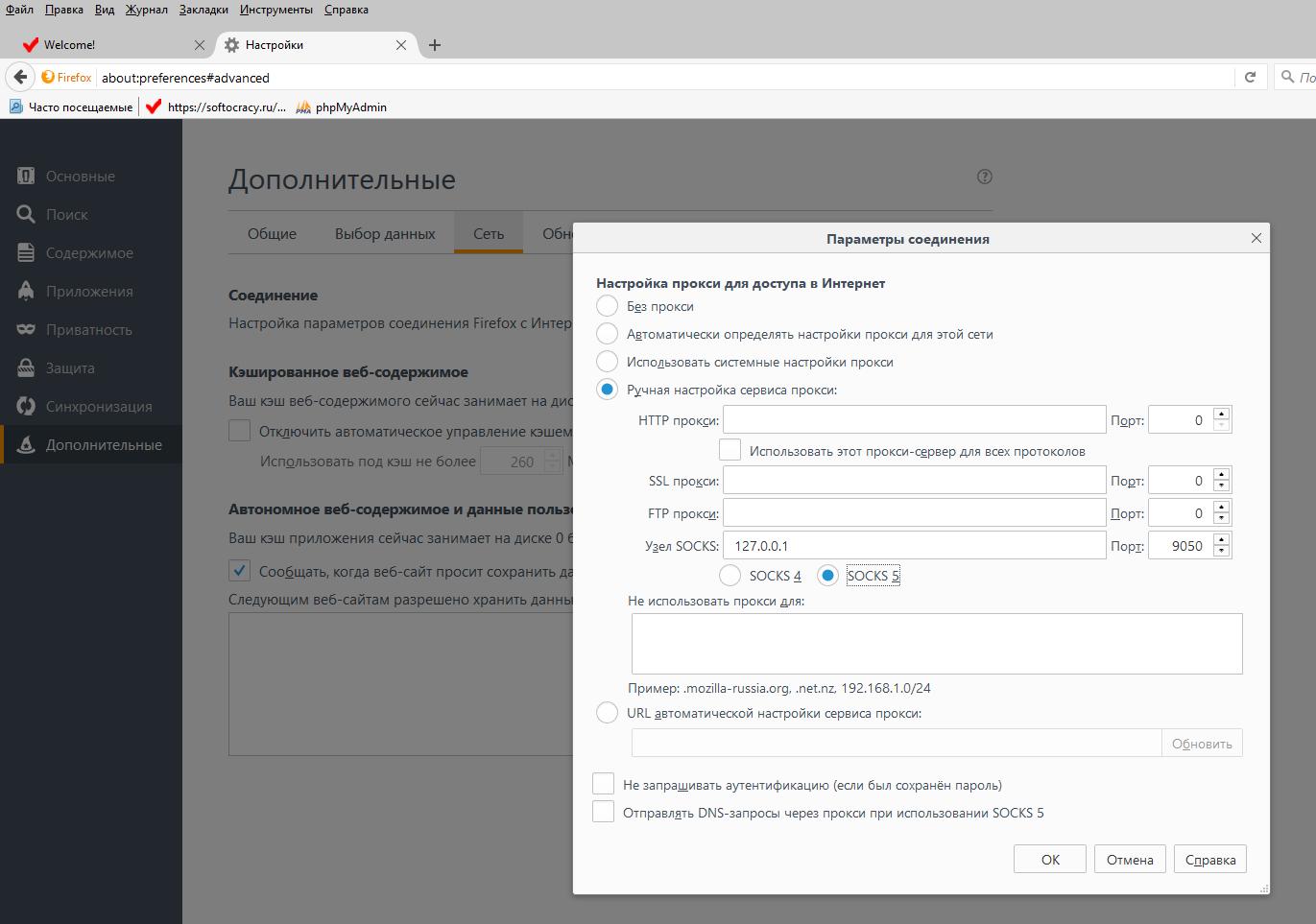
To change the settings in Firefox go to Settings -> Advanced -> Network -> Configure. In the window that opens, select the Manual proxy server settings switch. Enter the IP and port of the proxy server. Click OK to save the settings.
How to check proxy anonymity without third-party services
We do not need to trust information about the level of proxy anonymity – we can perform an independent check.
The scheme is pretty simple:
- we make a request to our script through a proxy
- the script checks which headers came to it
Implementation requires website hosting – any, most importantly, support for PHP. We upload the file with the contents to this hosting:
<?php
foreach (getallheaders() as $name => $value) {
echo "$name: $value<br>";
}
Now turn on the proxy and open this file in a web browser.
Of course, you can configure it yourself and perform checks without third-party services, but for the purposes of this article, I wrote a small service that looks for and highlights the added proxy headers. Service for determining whether proxies are used and proxy anonymity level: http://w-e-b.site/?act=proxy-checker. Please note that it is important to open the address using the HTTP protocol (and not HTTPS).
The page will show all the HTTP headers that came from your side, if there are proxy-specific headers, they will be highlighted in red:
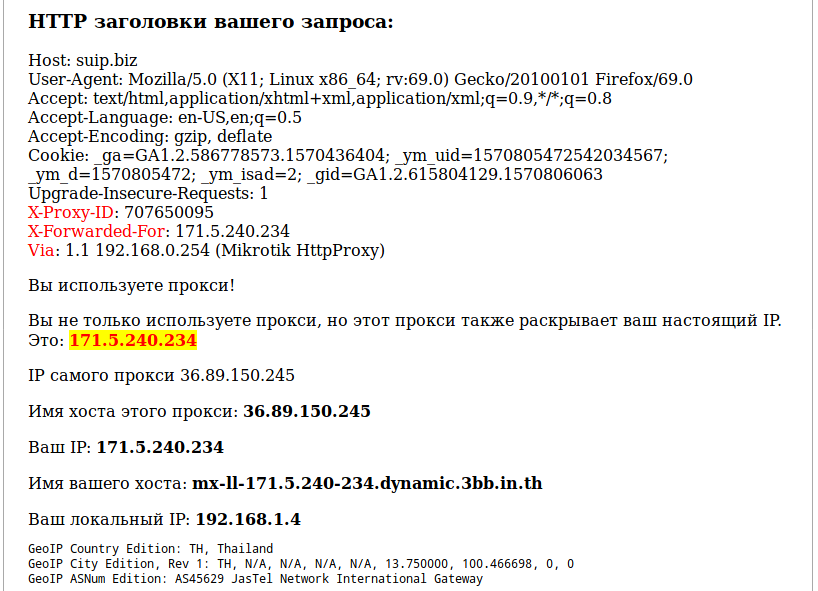
As you can see, the headers that reveal proxy usage are:
X-Proxy-ID: 707650095 X-Forwarded-For: 171.5.240.234 Via: 1.1 192.168.0.254 (Mikrotik HttpProxy)
In them X-Forwarded-For contains the real proxy user IP! The Via header contains some data about the proxy itself – sometimes its IP, sometimes its local IP, although it can contain anything.
The real HTTP IP can be revealed by the following HTTP headers added by the proxy:
- X-Forwarded-For
- X-Real-IP
- Forwarded
These headers need special attention.
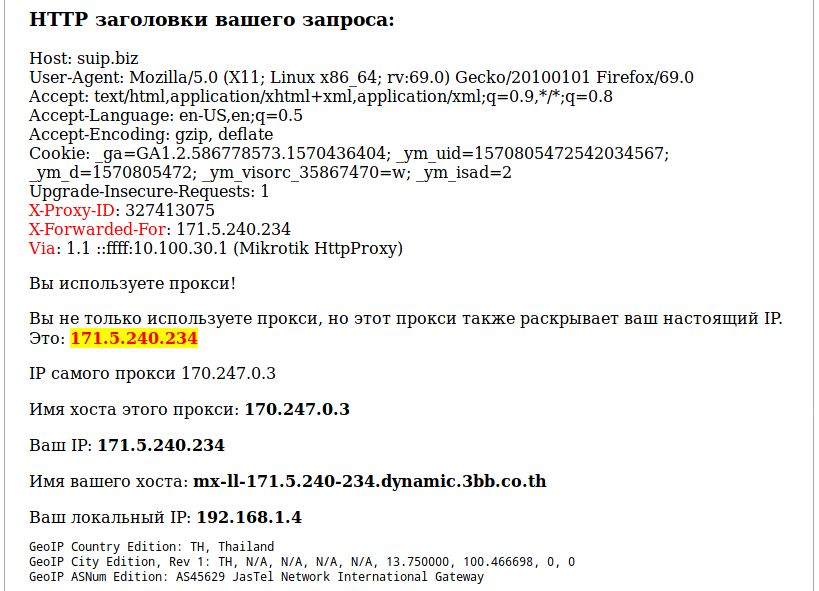
Some proxies add typical headers (that is, leak the fact of using a proxy), but at the same time hide the user's real IP:
Let’s consider the popular headers that proxies add:
Forwarded
Disclose original information of a client connecting to a web server through an HTTP proxy.
Header examples:
Forwarded: for=192.0.2.60;proto=http;by=203.0.113.43 Forwarded: for=192.0.2.43, for=198.51.100.17
X-Forwarded-For
A de facto standard for identifying the originating IP address of a client connecting to a web server through an HTTP proxy or load balancer. Superseded by Forwarded header.
Header example:
X-Forwarded-For: 171.5.240.120
X-Forwarded-Host
A de facto standard for identifying the original host requested by the client in the Host HTTP request header, since the host name and/or port of the reverse proxy (load balancer) may differ from the origin server handling the request. Superseded by Forwarded header.
X-Forwarded-Proto
A de facto standard for identifying the originating protocol of an HTTP request, since a reverse proxy (or a load balancer) may communicate with a web server using HTTP even if the request to the reverse proxy is HTTPS. An alternative form of the header (X-ProxyUser-Ip) is used by Google clients talking to Google servers. Superseded by Forwarded header.
Header example:
X-Forwarded-Proto: https
Via
Informs the server of proxies through which the request was sent. This header is added by forward and reverse proxies; it may appear in request headers and response headers.
Examples of real headers:
Via: 1.1 89.250.19.173 (Mikrotik HttpProxy) Via: 1.1 vps663608 (squid/3.5.12) Via: 1.1 sgssl3 (squid/3.4.8) Via: 1.1 centos-32gb-nbg1-1 (squid/3.5.20)
X-Proxy-ID
I did not find a description of this header – by the name you can understand that this is the identifier of the proxy server, or the identifier of a specific request.
Other proxy detection methods
There are other ways to indirectly confirm that a remote user is using anonymization tools. You can get to know them on the corresponding online services that try to find holes in your anonymity:
Many methods are tied to the browser and JavaScript: DNS leak, different IP time zones in the browser and so on.
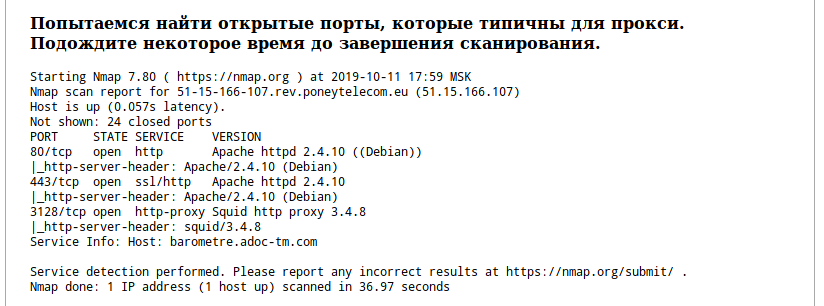
A more or less universal way is to scan the ports of a remote user. The essence of the technique is simple: the proxy has certain ports open, if when scanning the ports of the remote user it was possible to find the ports that are standard for the proxy, then the request came through the proxy. This service also scans several ports and displays information about them. An example of a successfully found proxy port:
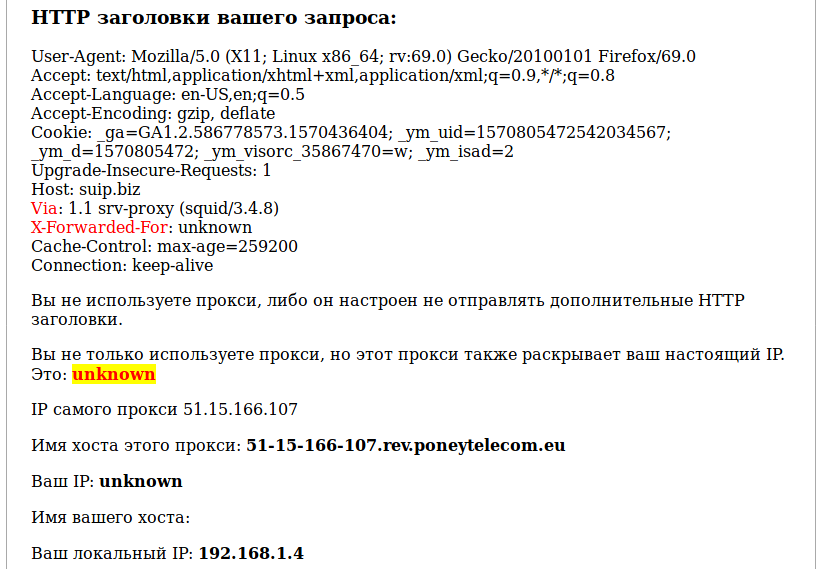
Tor Browser Request Headers
Tor is also a SOCKS5 proxy. But SOCKS5 does not add any headers. But actually the Tor browser removes (or rather, does not send) some headers to increase anonymity. Typical request from the Tor browser:
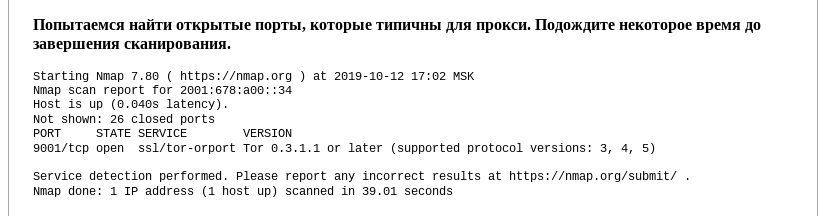
Port scans can also give hints about using Tor:
But, most importantly, the Tor IP address list is public.
Conclusion
As we saw, there is nothing complicated in checking proxy anonymity – just look at the headers that come to the remote server.
SOCKS proxies add nothing and do not leak the user's IP addresses. But when using a proxy, you should always remember about HoneyPots.
You also need to understand that the proxy server can keep logs in which the IP addresses of users are stored.