How to capture a Wi-Fi handshake in tcpdump
When tcpdump is running in monitor mode without specifying filters, all wireless frames, including a four-way handshake, will be captured. Subsequently, this handshake can be found using Wireshark using a filter:
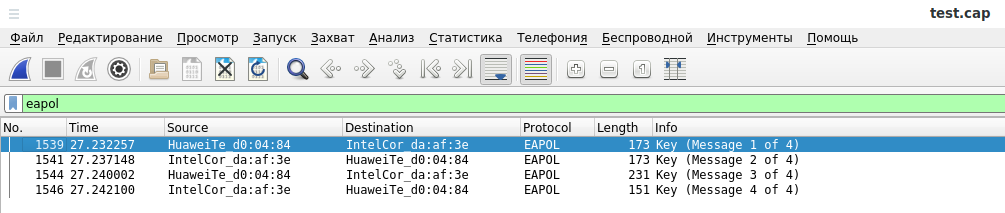
eapol
See the Wireshark Filters article for more details.
In order for tcpdump to filter only handshake frames, use a filter:
ether proto 0x888e
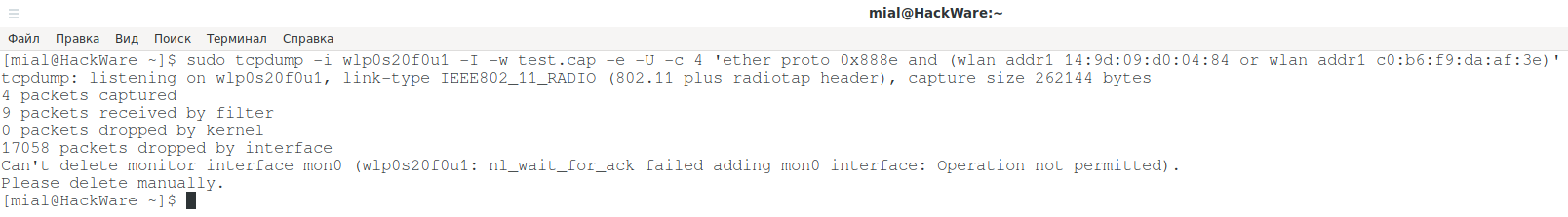
When capturing handshakes, it is recommended that you always specify the -U option, so that data is immediately written to a file.
An example of capturing all handshakes (for any Access Points and clients) and saving them to the test.cap file:
sudo tcpdump -i wlp0s20f0u1 -I -w test.cap -e -U ether proto 0x888e
The previous command will capture handshakes on the channel on which wireless adapter is currently operating – there will be no automatic channel switching.
Let’s consider the practical situation: you need to capture a handshake from the access point with BSSID 14:9d:09:d0:04:84, which works on channel 8. To capture, I will use a wireless interface named wlp0s20f0u1.
To achieve this goal, you need to start by switching the wireless card to the desired channel. Keep in mind that NetworkManager and other programs can automatically switch wireless interfaces to other channels. Therefore, you must either stop the NetworkManager service:
sudo systemctl stop NetworkManager.service
Or at least make sure that the wireless interface used for capture is not used for Internet connection.
Switching a wireless access point is simple, but there are nuances to keep in mind: the command will work only if the interface is already in monitor mode AND if it is up at the time of switching AND if it is not used at the time of switching…
In general, although tcpdump can enable monitor mode, we will do this in advance.
To switch the Wi-Fi card to a specific channel, use the sequence of commands:
sudo ip link set INTERFACE down sudo iw INTERFACE set monitor control sudo ip link set INTERFACE up sudo iw INTERFACE set channel CHANNEL
For example, I install a wireless card with the interface name wlp0s20f0u1 on channel 8:
sudo ip link set wlp0s20f0u1 down sudo iw wlp0s20f0u1 set monitor control sudo ip link set wlp0s20f0u1 up sudo iw wlp0s20f0u1 set channel 8
Now you need to run a command of the form:
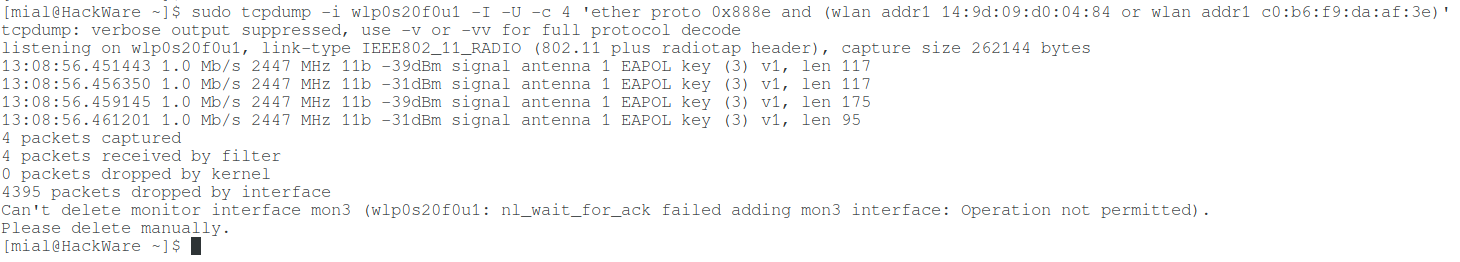
sudo tcpdump -i INTERFACE -I -w FILE.cap -e -U -c 4 'ether proto 0x888e and (wlan addr1 AP_BSSID or wlan addr1 CLIENT_BSSID)'
In this command:
- -i INTERFACE – a wireless interface that we set into monitor mode and which we switched on a specific channel
- -I – this option tells tcpdump to set the interface into monitor mode, in this case this option is used to make tcpdump understand what we want to capture in monitor mode (we want to use IEEE802_11_RADIO link layer, but not EN10MB)
- -w FILE.cap – file where the four way handshake will be saved
- -e – this option tells tcpdump to print MAC addresses. You can skip it, because when using -w nothing will be displayed on the screen at all. But in case of debugging when the -w option is not used, this option may come in handy.
- -U – means immediately write packets when they are received. In practice, I came across the fact that without this option the command for a long time (for several minutes) does not save successfully captured handshakes.
- -c 4 – this option means to terminate the program after successfully captured four packets – you can remove this option.
- wlan addr1 AP_BSSID – here you need to specify the MAC address of the Access Point from which the handshake is captured
- wlan addr1 CLIENT_BSSID – here you need to specify the MAC address of one of the clients of the AP from which the handshake is captured
An example of a real command that uses the wlp0s20f0u1 interface to capture a handshake, the handshake is saved to the test.cap file, the MAC address of the AP is 14:9d:09:d0:04:84, and the client's MAC address is c0:b6:f9:da:af:3e:
sudo tcpdump -i wlp0s20f0u1 -I -w test.cap -e -U -c 4 'ether proto 0x888e and (wlan addr1 14:9d:09:d0:04:84 or wlan addr1 c0:b6:f9:da:af:3e)'
The test.cap file opened in Wireshark after capturing a handshake:
Related articles:
- How to decrypt WPA traffic in Wireshark (65.7%)
- How to intercept and analyze traffic in open Wi-Fi (62.8%)
- Wireshark Filters (61.9%)
- BoopSuite is an alternative to Airodump-ng, Airmon-ng and Aireplay-ng (60.7%)
- Wi-Fi security audit with Hashcat and hcxdumptool (60.7%)
- Reaver cracked WPS PIN but does not reveal WPA-PSK password (SOLVED) (RANDOM - 50%)