Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 2)
Table of contents: Computer networks
1. How computer networks work
2. IP address
Part I:
3.1 Can routers and computers work simultaneously with IP and IPv6?
3.3 How do I know if I have an IPv6 address or not? How to find out your IPv6 address
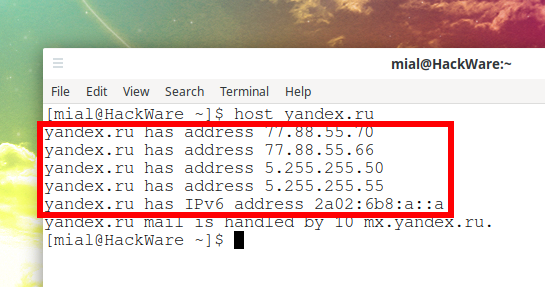
3.6 How to find out IPv6 site address
Service for checking if I am using IPv6 addresses
Part II:
3.7 How to open IPv6 in a web browser
3.9 How to ping IPv6 addresses
3.10 How to find out which organization IPv6 address belongs to. WHOIS IPv6 Addresses
3.11 How to look at the ARP table in IPv6. Show neighbors in IPv6
3.13 How to configure your system to work with DNS over IPv6
3.14 How to calculate how many IPv6 addresses in a subnet
3.15 How to scan IPv6 and IPv6 ranges
3.17 How to display IPv6 routes on the local system
3.18 How to view IPv6 settings
3.19 How to disable or enable IPv6
3.24 How to configure SSH to work with IPv6 only
3.25 Why is it necessary to limit the listening addresses to IPv6 only?
3.26 How to connect to FTP on IPv6 in FileZilla
3.28 Man-in-the-middle attack on IPv6
3.29 How to access an IPv6 network if my ISP does not support this protocol
3.30 What happens if an IPv4 client tries to access an IPv6-only server
Online services with IPv6 support
4.
It is recommended to start acquaintance with the first part: https://miloserdov.org/?p=3727
How to open IPv6 in a web browser
To use an IPv6 address in a URL, simply place it in square brackets: https://[2604:a880:800:c1::2ae:d001]/
If you need to specify a port, then it is put through a colon outside the square brackets. If you need to specify the page and parameters, then they follow the slash after the port number, or after the address, for example:
How to open IPv6 in cURL
To open IPv6 in cURL, the address must be placed in square brackets, examples of commands:
curl [2604:a880:800:c1::2ae:d001] curl https://[2604:a880:800:c1::2ae:d001] -k curl https://[2a02:6b8:a::a] -H 'Host: yandex.ru' -k
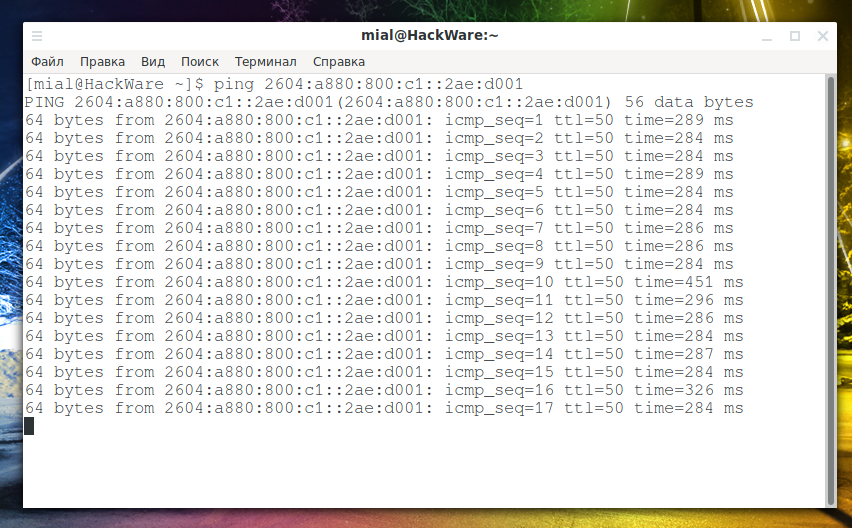
How to ping IPv6 addresses
The ping program can work with IPv6 addresses. It is enough to specify the address, and it does not need to be placed in square brackets:
ping 2604:a880:800:c1::2ae:d001
Instead of the IP address, you can specify the host name. But if the host has both IP and IPv6 addresses, then IPv4 addresses will be pinged. In order for the program to ping the IPv6 address, you need to use the -6 option:
ping -6 suip.biz
Online service for ping sites and IP with IPv6 support: https://w-e-b.site/?act=ping
How to find out which organization IPv6 address belongs to. WHOIS IPv6 Addresses
The whois program supports IPv6 addresses and you can use it to get information such as:
- organization to which IPv6 is assigned
- IPv6 address range
- mailing address of the organization that owns IPv6
- Autonomous system to which IPv6 belongs
- contact details (phone and email) of the owner of the IPv6 address
Using whois to get information about IPv6 is very simple – just specify the address (putting it in square brackets is not required):
whois 2604:a880:800:c1::2ae:d001
IPv6-enabled whois service: https://w-e-b.site/?act=whois
How to look at the ARP table in IPv6. Show neighbors in IPv6
To view the MAC addresses of devices in the local IPv6 network, run the command:
ip -6 neigh show
How to traceroute IPv6
To perform IPv6 traceroute, it is necessary that the computer from which you are tracerouting the IPv6 network, as well as the target host, have IPv6 addresses, that is, that they are connected to the IPv6 network.
To traceroutetraceroute, specify the IPv6 address of the remote host:
traceroute 2a02:f680:1:1100::3d60
For best results, it is recommended to try different methods of tracerouting, see the article ‘Trace route tools and methods’ for details.
The traceroute program looks for hostnames for IP addresses, but for IPv6 addresses it is usually not possible to find hostnames, so the program simply duplicates the same addresses, which clutters the output and makes it hard to read. To prevent this from happening, as well as to significantly speed up the tracing process, it is recommended to use the -n option:
traceroute -n 2a02:f680:1:1100::3d60
As a remote site, you can specify the site name. If you want tracerouting to IPv6 of this site, specify the -6 option, for example:
traceroute -6 suip.biz
Online traceroute service with IPv6 support: https://w-e-b.site/?act=traceroute
How to configure your system to work with DNS over IPv6
Even if your computer is connected to an IPv6 network, then most likely the fourth version of IP is listed as the DNS server. If you want DNS queries also to be made using IPv6, then in addition to the existing records, add the IPv6 addresses of DNS servers.
For Google DNS, these are the addresses:
- 2001:4860:4860::8888
- 2001:4860:4860::8844
You can check if DNS responses over IPv6 are coming normally:
dig suip.biz @2001:4860:4860::8888 AAAA
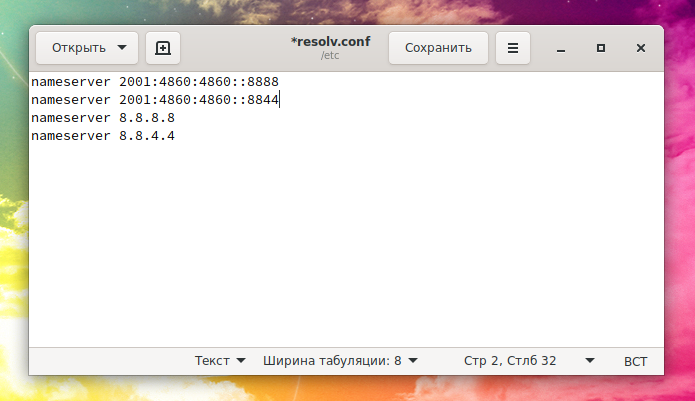
If everything is fine, then on Linux, to enable DNS via IPv6 at the beginning of the /etc/resolv.conf file:
sudo gedit /etc/resolv.conf
add lines:
nameserver 2001:4860:4860::8888 nameserver 2001:4860:4860::8844
After that, DNS queries will be sent via the IPv6 protocol.
In addition to being “trendy and modern”, IPv6 has built-in IPsec support:
IPsec (short for IP Security) is a set of protocols for securing data transmitted over the IP Internet Protocol. Allows authentication, integrity checking and/or encryption of IP packets. IPsec also includes protocols for secure key exchange on the Internet. It is mainly used for organizing VPN connections .
Security in IPv6 is implemented using IPsec, which is required for this version of the protocol. Unlike SSL and TLS, IPsec will allow you to encrypt any data (including UDP) without the need for any support from the application software. And DNS queries (by default) are transmitted using the UDP protocol. That is, in theory, the transition from IP to IPv6 should improve security for DNS queries.
How to calculate how many IPv6 addresses in a subnet
Before moving on to examples of scanning IPv6 subnets, let's learn how to calculate how many IPv6 addresses are in a given IPv6 range.
This is not without meaning, we turn to the quote from Wikipedia:
“It is sometimes claimed that a new protocol can provide up to 5 · 10 28 addresses for every inhabitant of the Earth. Such a large address space was introduced for the sake of hierarchical addresses (this simplifies routing). However, an increased address space will make NAT optional. The classic use of IPv6 (over a /64 network per client; only unicast addressing is used) will make it possible to use more than 300 million IP addresses per inhabitant of the Earth”.
By the way, it's pretty easy to calculate how many IPv6 addresses are in total:
2128 = 3.402823669 × 1038
This is an unrealistically many!
And in the subnet you are interested in may be much more addresses than you expect…
You can calculate the number of IPv6 in a subnet using the formula:
2(128-MASK_LENGTH)
Suppose you are given an IPv6 network: 2604:A880::/32, how many IPv6 addresses are in this network?
We consider:
2(128-32) = 7.922816251 × 1028
I don’t know what this number is, but it’s definitely a lot of addresses. It’s pointless to start scanning such networks – scanning will never end.
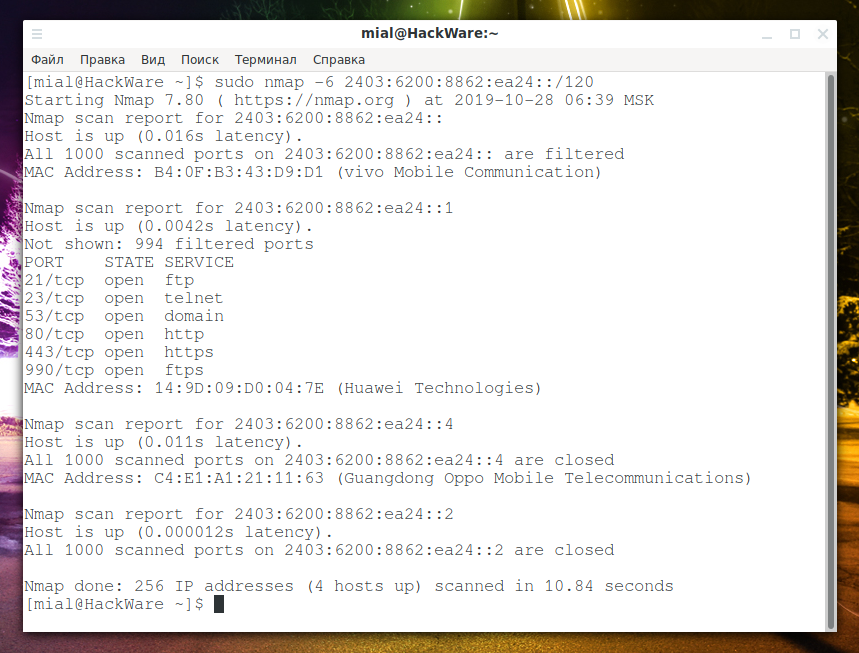
How to scan IPv6 and IPv6 ranges
Nmap supports IPv6 addresses and can scan IPv6 ranges, although there are some limitations: not all types of notations that are available for regular IPs are supported.
Suppose I want to scan my local IPv6 network to which my address 2403:6200:8862:ea24::2/128 belongs (subnet mask /128 means only one address). Although this is not quite the correct expression, since the address 2403:6200:8862:ea24::2 is global. At the same time, IPv6 address 2403:6200:8862:ea24:40b3:e3e3:fdf8:bcf8/64 was assigned to my network interface. If you look at information about this address:
whois 2403:6200:8862:ea24:40b3:e3e3:fdf8:bcf8
it turns out that it belongs to the range 2403:6200::/32. The range with a network length of /32 is too large to scan. The subnet /64 is also too big. Therefore, I will scan the /120 subnet, in which all in all:
2(128-120) = 256 addresses.
That is, as a target, I choose 2403:6200:8862:ea24::2/120. Nmap will not complain that the non-network bits set (unlike, by the way, tcpdump, which does not accept a filter with this assumption). But more correct, of course, would be to indicate the goal as 2403:6200:8862:ea24::/120:
sudo nmap -6 2403:6200:8862:ea24::/120
Of the 256 hosts scanned, 4 were online. These are the same hosts that are on the 192.168.1.0/24 subnet.
In fact, if you dig a little deeper and take a closer look at IPv6, we will find out that very large subnets are allocated to clients, and so many addresses are needed due to the nature of IPv6 routing. It may turn out that the clients are gathered at the beginning of large ranges and it makes no sense to scan the entire large range of IPv6 addresses entirely – it is enough to break the scan targets into the same subnets that the ISP allocates to clients and scan only the very beginning of each such range. As a result, the scan time should decrease dramatically. IMHO, there is room for optimization in scanning IPv6 networks, but this requires an understanding of the topology of a particular network and a deep understanding of IPv6 and its routing.
So, to scan IPv6 addresses or ranges, add the -6 option to the nmap scan command and specify:
- full IPv6 address
- host name (if IPv6 is bound to it)
- CIDR notation can be used for subnets
Octet ranges for IPv6 are not yet supported.
Even if the IPv6 address is explicitly specified as the target, the -6 option must be specified, otherwise an error of the form:
2a0b:f4c0:16c:4::1 looks like an IPv6 target specification -- you have to use the -6 option.
All nmap options and capabilities are also supported for IPv6 addresses.
Online service ‘Scanning open IPv6 port addresses’: https://w-e-b.site/?act=nmap-ipv6
What is the difference between scanning IPv6 and IPv4? Do I need to additionally scan ports on IPv6?
IPv6 and IPv4 addresses of one remote host can be on the same network interface or on different ones. Even if both addresses are assigned to the same network interface, different ports can be opened for these addresses! For example, below I will show how to configure SSH to work only on the IPv6 protocol – in this case, if you restrict yourself to scanning the IPv4 protocol, then you will not even know about the existence of the SSH service on the target server! A similar statement is true for most other protocols and services, especially not intended for the general public: for example, a web server is unlikely to be configured to listen only to IPv6 address, since this restricts access to a large number of visitors, but “administrative” services to which it must only one person has access, or a small group of people, for example, SSH, Telnet, FTP, etc., may well be configured only to work on the IPv6 protocol.
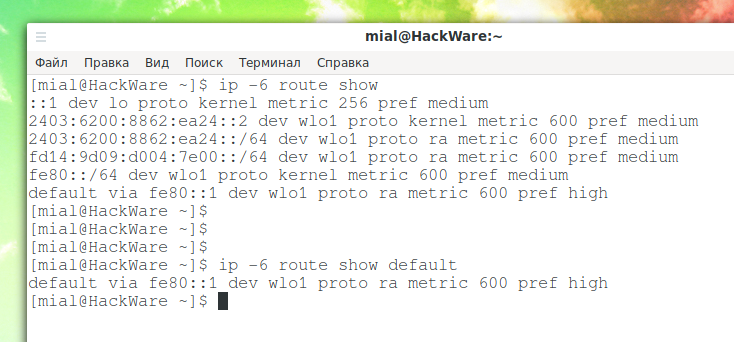
How to display IPv6 routes on the local system
To list IPv6 routes on Linux, run the command:
ip -6 route show
Or an abbreviated version of this command:
ip -6 ro
To show the default IPv6 route, run the command:
ip -6 route show default
For more information about routes, see the article ‘Setting up network routes: the choice of connection used for the Internet; simultaneous use of multiple connections for different purposes’.
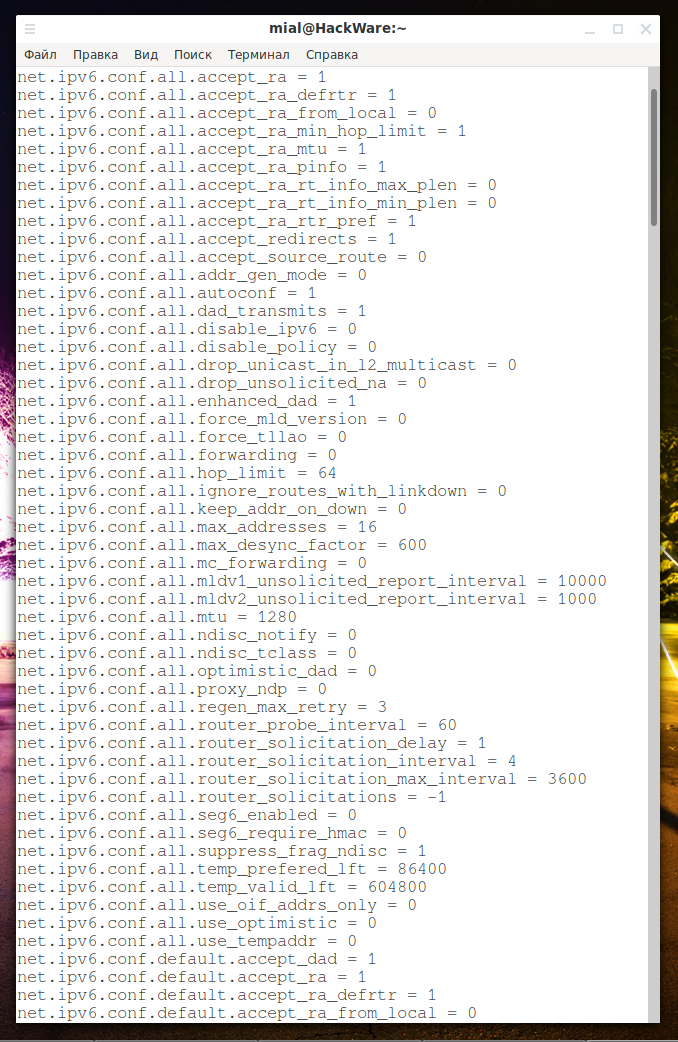
How to view IPv6 settings
The above shows how to find out your IPv6 address and IPv6 routes, but in addition to these settings, the system has many other IPv6 options for fine-tuning and enabling or disabling certain IPv6 functions.
To view the current IPv6 settings on Linux, run the command:
sudo sysctl -a | grep ipv6
How to disable IPv6
To disable IPv6 on Linux, run the following commands:
sudo sysctl -w net.ipv6.conf.all.disable_ipv6=1 sudo sysctl -w net.ipv6.conf.default.disable_ipv6=1
These settings remain in effect until the next restart of the computer.
To make the settings permanent, run the following commands:
sudo su - echo 'net.ipv6.conf.all.disable_ipv6=1' >> /etc/sysctl.d/sysctl.conf echo 'net.ipv6.conf.default.disable_ipv6=1' >> /etc/sysctl.d/sysctl.conf
For the changes to take effect, run the command:
sysctl -p
How to check if IPv6 is disabled
To check if IPv6 is disabled at the operating system level, run the following commands:
sysctl -n net.ipv6.conf.all.disable_ipv6 sysctl -n net.ipv6.conf.default.disable_ipv6
How to enable disabled IPv6
To enable IPv6 at the operating system level, run the following commands:
sudo sysctl -w net.ipv6.conf.all.disable_ipv6=0 sudo sysctl -w net.ipv6.conf.default.disable_ipv6=0
If you have saved settings in the /etc/sysctl.d/sysctl.conf file, then delete this file:
sudo rm /etc/sysctl.d/sysctl.conf
iptables for IPv6
Firewall configuration for the IPv6 protocol is performed by the ip6tables command.
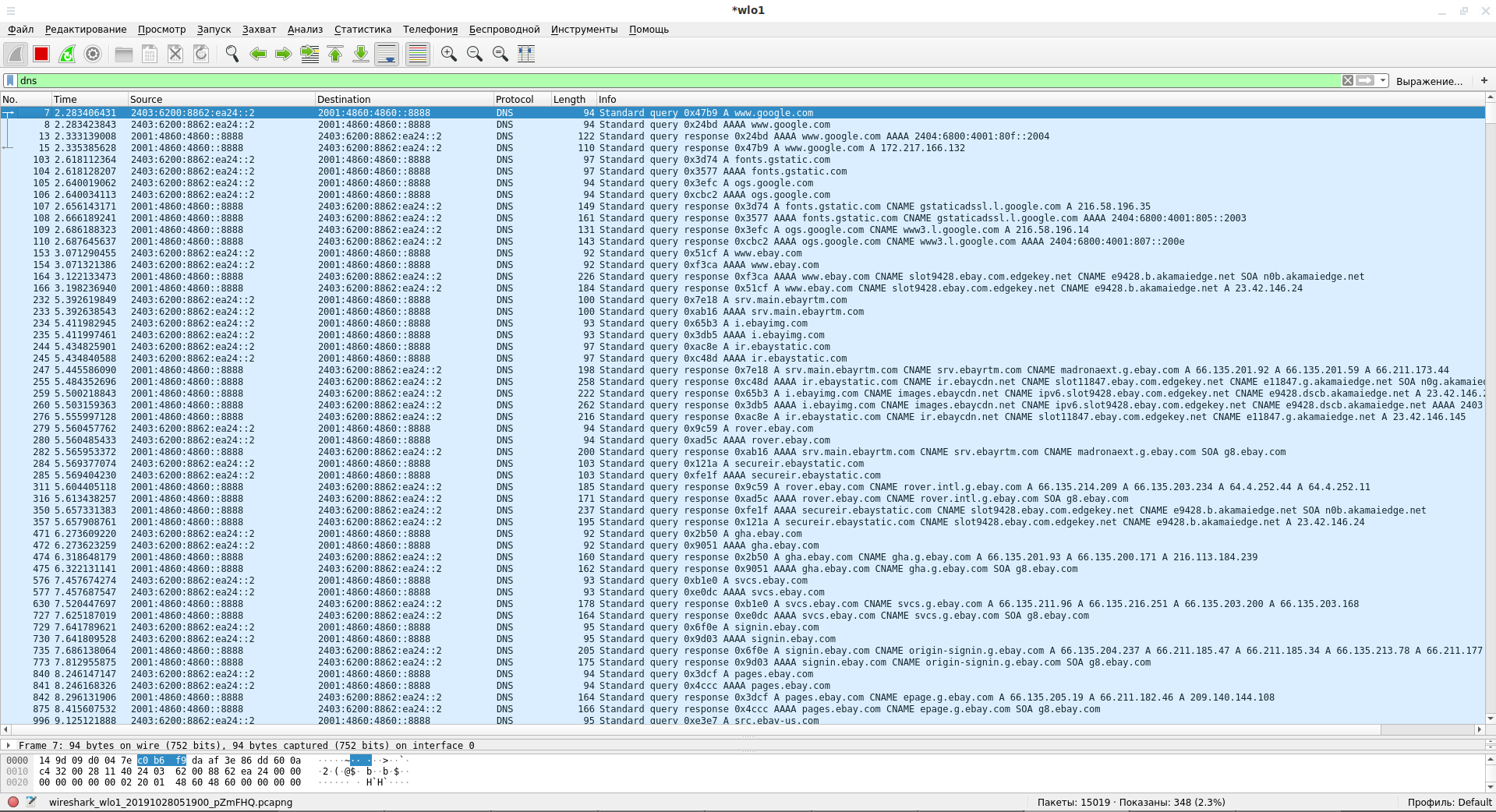
IPv6 in Wireshark
Wireshark supports the IPv6 protocol and shows its packets by default. If you need to filter only IPv6 traffic, then use the display filter:
ipv6
If you need only IP traffic, then use the filter:
ip
Filtering ICMPv6 (Internet Control Message Protocol of the sixth version) in Wireshark is done by the filter:
icmpv6
How to filter ARP packets for IPv6 in Wireshark? For IPv6, ARP is not required, since its role is played by the Neighbor Discovery Protocol (NDP) using ICPM6.
To see packets that act as ARPs for IPv6, use a filter:
icmpv6.type == 133 or icmpv6.type == 134 or icmpv6.type == 135 or icmpv6.type == 136 or icmpv6.type == 137
See also the Wireshark Filters reference material.
IPv6 in tcpdump
tcpdump supports the IPv6 protocol and shows its packets by default.
It is worth noting that filtering by IPv6 range, for example:
sudo tcpdump net 2604:a880:800:c1::2ae:d000/64
May result in messages of the form:
tcpdump: non-network bits set in "2604:a880:800:c1::2ae:d000/64"
With other programs this problem usually does not occur, but tcpdump requires that the non-network bits are equal to zero. That is, the command with the following filter is correct for tcpdump:
sudo tcpdump net 2604:a880:800:c1::/64
Using IPv6 in SSH
When connecting to an SSH server, you can use the IPv6 address of the remote host, for example:
ssh root@2a02:f680:1:1100::3d60
If you are connecting by the name of a host that has an IP and IPv6 address, then add the -6 option so that the IPv6 address is selected:
ssh -6 root@suip.biz
How to configure SSH to work with IPv6 only
The SSH server configuration is performed in the /etc/ssh/ sshd_config file.
The system can have several network interfaces with several IP addresses, by default sshd listens for them all, including IPv6 addresses:
ListenAddress 0.0.0.0 ListenAddress ::
If you remove the ListenAddress 0.0.0.0 entry, only IPv6 will be listened.
With the ListenAddress directive, you can also specify a specific IP that will be listened for while waiting for connections. And with the AddressFamily option you can choose to listen to all addresses, only IPv4 or only IPv6:
AddressFamily any
Options:
- any (by default, any addresses)
- inet (use only IPv4)
- inet6 (use only IPv6),
Why is it necessary to limit the listening addresses to IPv6 only?
Many automatic scanners by default only scan ports for IPv4 addresses, completely ignoring IPv6. There are still quite a lot of users, including hackers who do not have access to IPv6. If your ISP has IPv6 support, then switching to SSH with IPv6 protocol will significantly limit access to your SSH server for automatic scanners and drastically reduce the number of brute-force cracking attempts (password guessing).
How to connect to FTP on IPv6 in FileZilla
FileZilla supports IPv6 addresses that must be enclosed in square brackets.
IPv6 and Openvpn
The scheme with listening and connecting only over IPv6 should work, but this topic requires additional testing.
Man-in-the-middle attack on IPv6
Classic ARP spoofing does not work for the IPv6 protocol because it uses a different protocol. However, there are similar attacks by Neighbor Advertisement Spoofing, Last Hop Router.
IPv4 and IPv6 are separate protocols, so attacking one does not directly affect the other. However, the methods for spoofing NA and ARP are very similar. If you have the opportunity to do one, you probably could do another.
How to access an IPv6 network if my ISP does not support this protocol
Although Internet service providers support IPv6 not everywhere, you can easily rent VPS with IPv6. These VPS can be used over SSH or as a proxy for working with IPv6.
Examples of VPS with IPv6, where the system can be lifted with a few clicks:
What happens if an IPv4 client tries to access an IPv6-only server
Question:
Hey! The article says that IPv6 is a completely different protocol, I had a question. If my recipient's email works only on IPv6 (that is, his mail server listens only through the IPv6 protocol), does this mean that when sending a letter from a mail server that is connected only to IPv4, the letter simply will not reach the recipient, that is, I will have to choose some kind of mail service whose mail server works with both IPv6 and IPv4 so that my friend can read my letter?
Answer:
The considered situation, when one server has only an IPv4 address, and the second server has only an IPv6 address, is purely theoretical. ISPs that use IPv6 and provide IPv6 addresses to customers also provide IPv4 addresses at the same time.
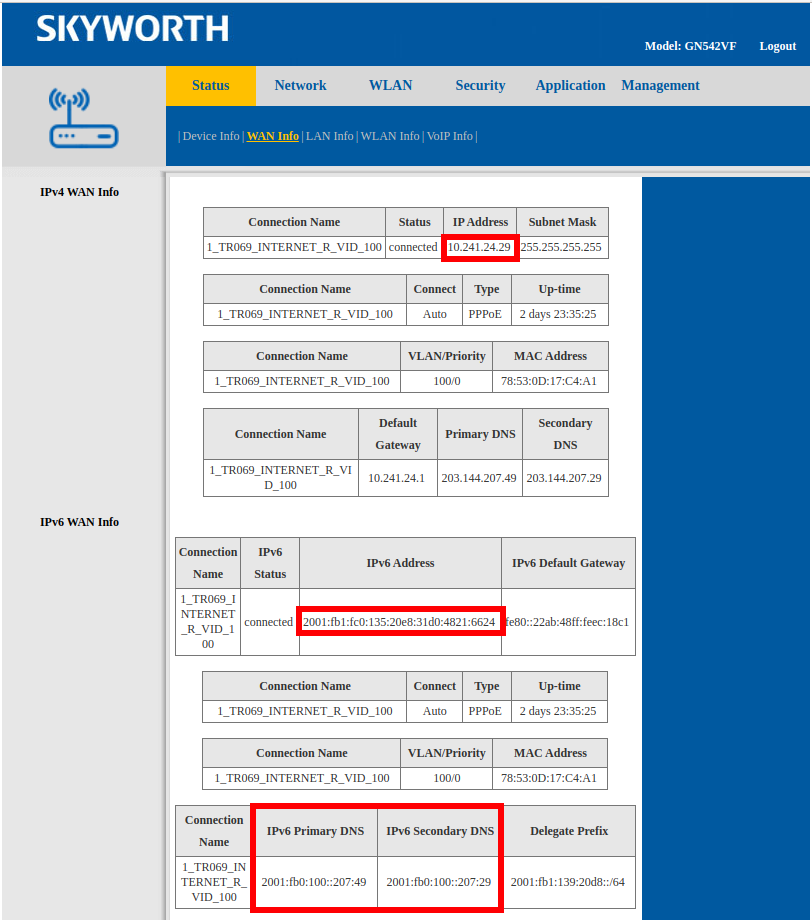
For example, this router is connected to an ISP that supports IPv6. However, a router has two types of IP addresses:
- 10.241.24.29
- 2001:fb1:fc0:135:20e8:31d0:4821:6624
My computer is connected to this router, so it also has two types of IP addresses:
- 192.168.1.58
- 2001:fb1:139:20d8:82c0:cb25:b750:24d4
Note that IPv4 and IPv6 are such separate networks that for IPv6, the router has its own DNS server IP – 2001:fb0:100::207:49.
The same is true for hosting providers. For example, ISPs in my country do not support IPv6. But at the same time, hosting providers in my country have been supporting IPv6 for a very long time (for example, I set up IPv6 for SuIP.biz back in 2016, while one rented VPS server came with one free IPv4 and 3 free IPv6).
You can search for websites with IPv6 support and look at their DNS records – you will see that in addition to the AAAA record (IPv6 address of the site), there is also an A record for the site (IPv4 address of the site).
That is, yes, if one of the computers (client or server1) is connected only to an IPv4 network, and the second computer (server or server2) is connected only to an IPv6 network, then theoretically it is simply impossible to build a network route between them from the first to the second. But in practice, this problem does not arise simply for the reason that absolutely all clients and servers support IPv4, and some also support IPv6. That is, all possible combinations work according to one of the following options:
- client and server support IPv6 – IPv6 is used
- client supports IPv6 and server does not support IPv6 – IPv4 is used
- client does not support IPv6 and server supports IPv6 – IPv4 is used
- client does not support IPv6 and server does not support IPv6 – IPv4 is used
However, it is possible to isolate an IPv6-enabled server from an IPv4 network, which is what I talk about in the section “How to configure SSH to work with IPv6 only”.
In short: IPv4 and IPv6 are two different networks, even though they run on the same wires and on the same hardware.
If you're interested in a specific error, when you try to open an IPv6-only site from an IPv4-only client, you get the “Network is unreachable” error.
Another example of an error: if you try to run the following command from an IPv6-enabled network:
sudo nmap -6 suip.biz
then the host suip.biz will be scanned.
If you run the same command from a network without IPv6 support, an error will be displayed: “setup_target: failed to determine route to suip.biz (2a02:f680:1:1100::3d60)”.
Online services with IPv6 support
- Do I have IPv6
- Online whois service with IPv6 support
- Find out the location and Internet service provider by IPv6
- IPv6 Subnet Calculator
- Decompression (full form) IPv6
- Scanning IPv6 addresses for open port
- IP, IPv6, web-sites ping
- Traceroute the path to IP and IPv6 addresses, as well as websites
Related articles:
- Best Kali Linux tools in WSL (Windows Subsystem for Linux) (Part 1) (58.5%)
- IP calculators (57.9%)
- How to transfer files via SSH (57.8%)
- NetBIOS: what it is, how it works and how to use in information security (53.5%)
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 1) (52.7%)
- Installing and configuring MySQL and phpMyAdmin on Kali Linux (RANDOM - 50%)