All Airgeddon Hints
Here I picked up all airgeddon Hints. This collection of tips could help you to enlarge your knowledge about Wi-Fi attack.
Main Hints
- Select a wifi adapter to work in order to be able to do more actions than with an ethernet interface
- If your Linux is a virtual machine, it is possible that integrated wifi adapters are detected as ethernet. Use an external usb wifi adapter
- When airgeddon requests you to enter a path to a file either to use a dictionary, a Handshake or anything else, did you know that you can drag and drop the file over the airgeddon window? In this way you don't have to type the path manually
- If you enjoyed the script and found it useful, you can support the project by making a donation. Through Paypal (v1s1t0r.1s.h3r3@gmail.com) or sending a fraction of a bitcoin (1AKnTXbomtwUzrm81FRzi5acSSXxGteGTH). Any amount, no matter how small (1, 2, 5 $/€) is welcome. More information and direct links to do it at: https://github.com/v1s1t0r1sh3r3/airgeddon/wiki/Contributing
- We are looking for translators to other languages. If you want to see airgeddon in your native language and you also know English, contact us. More information at: https://github.com/v1s1t0r1sh3r3/airgeddon/wiki/Contributing
- If you install ccze you'll see some parts of airgeddon in a colorized way with better aspect. It's not a requirement or a dependency, but it will improve the user experience
- If you have ccze installed and are experiencing display errors or glitches on some windows, you should disable colorization in the option and language menu
- It is known that the software used in the 5Ghz band still presents some problems sometimes. For example airodump, that when scanning networks can show a value "-1" on channel depending of the card chipset and the driver. It is also known that Ralink chipsets sometimes are getting errors on high channels ">=60"
DoS Hints
- The natural order to proceed in this menu is usually: 1-Select wifi adapter 2-Put it in monitor mode 3-Select target network 4-Start attack
- Not all attacks affect all access points. If an attack is not working against an access point, choose another one 🙂
- If you select a target network with hidden ESSID, you can't use it, but you can perform BSSID based attacks to that network
Handshake Hints
- The natural order to proceed in this menu is usually: 1-Select wifi adapter 2-Set it in monitor mode 3-Select target network 4-Capture Handshake
- Remember to select a target network with clients to capture Handshake
- Cleaning a Handshake file is recommended only for big size files. It's better to have a backup, sometimes file can be corrupted while cleaning it
- Obtaining a Handshake is only for networks with encryption WPA or WPA2
Handshake Attack Hints
- If the Handshake doesn't appear after an attack, try again or change the type of attack
Decrypt Hints
- The key decrypt process is performed offline on a previously captured file
- To decrypt the key of a WPA/WPA2 network, the capture file must contain a Handshake
- Decrypting by bruteforce, it could pass hours, days, weeks or even months to take it depending on the complexity of the password and your processing speed
- If you choose a big charset and a long key length, the process could take so much time
- Rule based attacks change the words of the dictionary list according to the rules written in the rules file itself. They are very useful. Some distros has predefined rule files (Kali: /usr/share/hashcat/rules // Wifislax: /opt/hashcat/rules
- When airgeddon requests you to enter a path to a file either to use a dictionary, a Handshake or anything else, did you know that you can drag and drop the file over the airgeddon window? In this way you don't have to type the path manually
Select Interface Hints
- Every time you see a text with the prefix [PoT] acronym for "Pending of Translation", means the translation has been automatically generated and is still pending of review
Language Hints
- If you see any bad translation or just want [PoT] marks to dissapear, write me to v1s1t0r.1s.h3r3@gmail.com to collaborate with translations
- We are looking for translators to other languages. If you want to see airgeddon in your native language and you also know english, contact us. More information at: https://github.com/v1s1t0r1sh3r3/airgeddon/wiki/Contributing
Option Hints
- If you have ccze installed and are experiencing display errors or glitches on some windows, you should disable colorization in the option and language menu
- If you see any bad translation or just want [PoT] marks to dissapear, write me to v1s1t0r.1s.h3r3@gmail.com to collaborate with translations
- If you installed airgeddon from a repository, you should not enable automatic updates. airgeddon will be updated when there is a new version in the repository
- The options in this menu containing the word "permanently" modify airgeddon to save the settings for the next time that is to be launched. However, you can always return to this menu to change the value of the option again
Evil Twin Hints
- In order to use the Evil Twin just AP and sniffing attacks, you must have another one interface in addition to the wifi network interface will become the AP, which will provide internet access to other clients on the network. This doesn't need to be wifi, can be ethernet
- If you use the attack without sniffing, just AP, you'll can use any external to script sniffer software
- The captive portal attack tries to one of the network clients provide us the password for the wifi network by entering it on our portal
- To perform an Evil Twin attack you'll need to be very close to the target AP or have a very powerful wifi antenna. Your signal must reach clients equally strong or more than the legitimate AP
- Sslstrip technique is not infallible. It depends on many factors and not always work. Some browsers such as Mozilla Firefox latest versions are not affected
- The unique Evil Twin attack in which it's not necessary to have an additional interface with internet access is the captive portal attack. As an alternative, you'll need another additional requirement: dsniff
- On Evil Twin attack with BeEF integrated, in addition to obtaining keys using sniffing techniques, you can try to control the client's browser launching numerous attack vectors. The success of these will depend on many factors such as the kind of client's browser and its version
- If you want to integrate "DoS pursuit mode" on an Evil Twin attack, another additional wifi interface in monitor mode will be needed to be able to perform it
- In the 5Ghz band there are many channels in which because of the country configuration, you can't operate. There are also other channels in which you cann't initiate communication, only communicate with an existing network. This makes starting an access point on a 5Ghz channel very likely to fail if it doesn't match an allowed channel. This is why Evil Twin will start on a channel in the 2.4Ghz band (1-11). But don't worry, it will be transparent for the users because the DoS attack still operate on the real 5Ghz channel against the target
Evil Twin DoS Hints
- If you can't deauth clients from an AP using an attack, choose another one 🙂
- With this attack, we'll try to deauth clients from the legitimate AP. Hopefully they'll reconnect to our Evil Twin AP
- If you want to integrate "DoS pursuit mode" on an Evil Twin attack, another additional wifi interface in monitor mode will be needed to be able to perform it
BeEF Hints
- If you installed BeEF manually, airgeddon might not be able to find it and the attack option can appear as restricted. You can try to solve it using the special menu option to fix this. It will work only if BeEF is already correctly installed and your unique problem is the script is not detecting it
WPS Hints
- Pixie Dust attack obtains PIN and password in seconds, but not all access points are affected
- In order to success on any WPS based attack, you need good signal of target network. We might otherwise get false negatives
- Some access points can be blocked after failing some PIN connection attempts. It may vary depending on the access point
- Some combinations don't work well. Such as reaver and Ralink chipset adapters. If your adapter has this chipset is recommended to use bully
- To perform the Pixie Dust integrated attack with reaver or bully, you must have installed at least 1.5.2 version for reaver and 1.1 for bully
- Some access points have only PBC (Push Button Connect) enabled and you can't connect via WPS if you don't press the physical button on the device
- The Arcadyan algorithm needs a very specific data to calculate the PIN (the serial number of the access point). Getting this data can take a lot of time. You can optionally choose to try to generate it. This generated PIN is very useful in networks of type Orange-XXXX
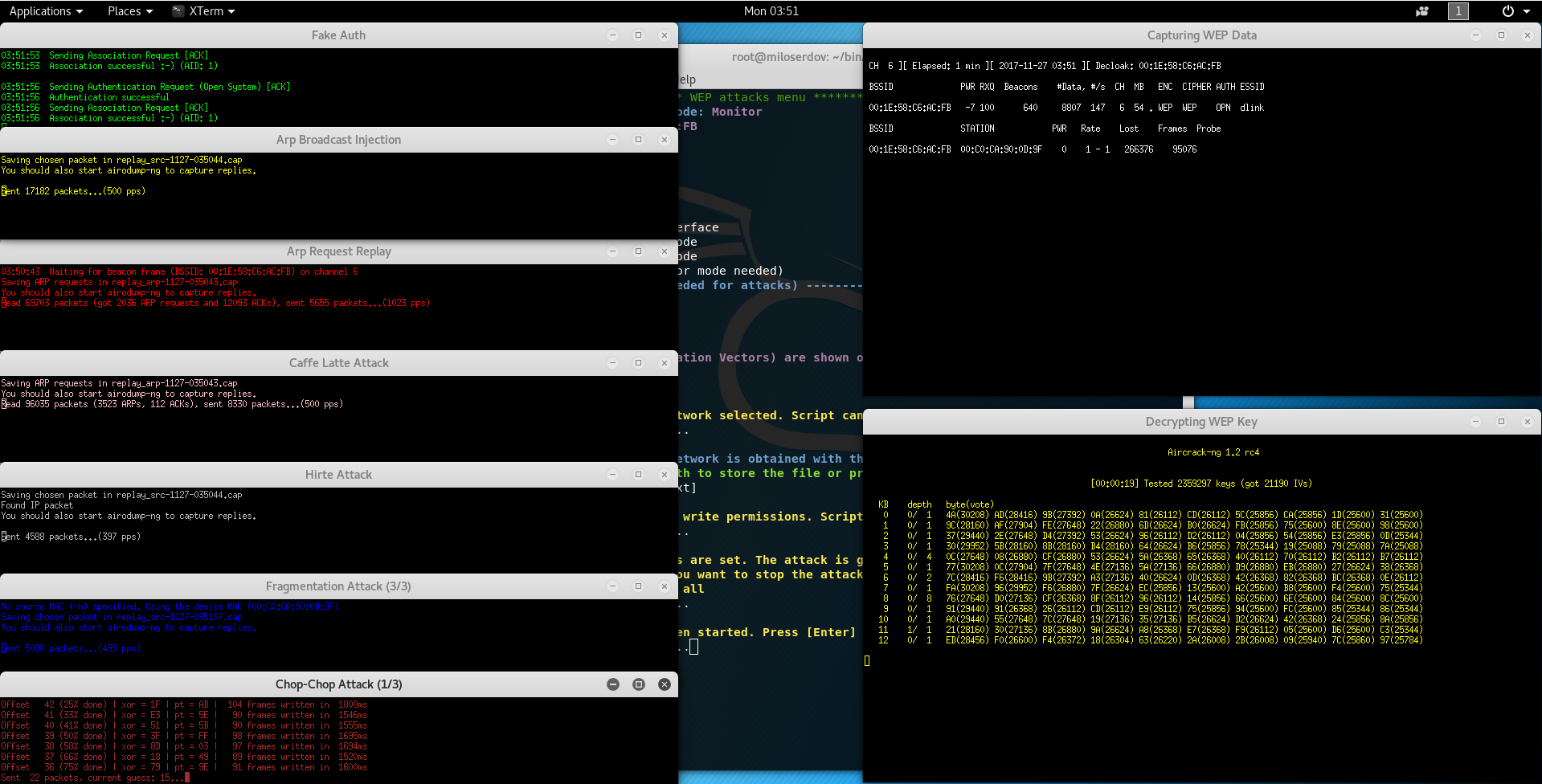
WEP Hints
- The WEP protocol had a bad design and can be cracked in a few minutes if we have enough generated traffic
- The WEP "All-in-One" attack combines different techniques to generate enough traffic to decrypt the key (Caffe Latte, Hirte, Replay, Chop-Chop, Fragmentation, Fake association, etc.)
- If real clients exist connected to the WEP encrypted network, the process will be significantly accelerated. Enough IVs (Initialization Vectors) will be catched faster
- Captured IVs (Initialization Vectors) are shown on airodump capture window as "Data"
- Some access points are not vulnerable to certain WEP attacks. Like for example the Chop-Chop attack, that only affects some of them
Related articles:
- How to install airgeddon on Linux Mint or Ubuntu (100%)
- Effective WPS PINs attack based on known PIN and PIN generation algorithms (100%)
- The easiest and fastest ways to hack Wi-Fi (using airgeddon) (100%)
- New in attacks on wireless networks (100%)
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security (53.9%)
- WiFi-Pumpkin: Rogue Wi-Fi Access Point Attack with GUI and rich functionality (RANDOM - 50%)