Comprehensive Guide to John the Ripper. Part 2: Utilities for extracting hashes
Table of contents
1. Introducing and Installing John the Ripper
2. Utilities for extracting hashes
2.1 How to Crack Password in John the Ripper
2.2 How to convert a file to John the Ripper hash
2.3 Where to see examples of hashes
2.4 Reference for all scripts to generate hashes for John the Ripper and Hashcat
2.5 Other utilities to extract hashes
2.6 What you need to know when posting hashes
4. Practical examples of John the Ripper usage
6. How to brute force non-standard hashes
7, Johnny – GUI for John the Ripper
8.
9.
How to Crack Password in John the Ripper
John the Ripper can crack hashes only – it cannot work with encrypted files. The program cannot open, for example, an office document, enter a password there, etc.
This is a solvable problem – we need to compute (extract) the hash for the file of interest. John itself does not know how to do this. We need auxiliary utilities. You can view their list, for example, by typing the command:
locate *2john*
This is how the list looks like on the machine where I installed John from source:
Agree, the list is impressive!
On Kali Linux, these files are located in two directories:
- script files in /usr/share/john/
- and binaries in /usr/sbin/
These files are located in BlackArch:
- script files in /usr/lib/john/ directory
- binaries in /usr/bin/
If you compiled John the Ripper from source, then all of these files are collected in the run directory.
To find the file you need, use a command like this:
locate FILENAME
To find all files at once by extracting hashes, run:
locate *2john*
If you cannot find some file on your system (this can be done with the locate command), then download them from the source codes: https://github.com/magnumripper/JohnTheRipper.
How to convert a file to John the Ripper hash
The scripts have been collected from a wide variety of places and written by many researchers, often based on research by other researchers. Therefore, they are written in different programming languages.
In general, the usage is pretty standard – you need to specify the program to run and, separated by a space, the file for which you want to calculate the hash.
The good news is that these hashes are shared by both Hashcat and John the Ripper. That is, you can use this table and these files to crack passwords in John the Ripper or Hashcat.
You can specify several files at once to extract their hashes – for example, several ZIP archives or several office documents.
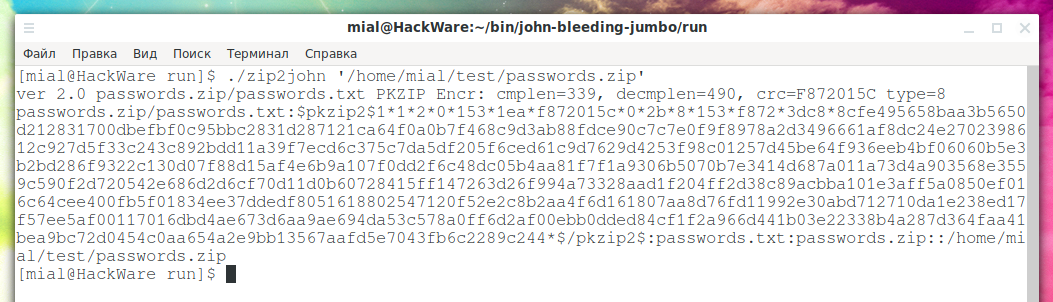
An example of extracting a hash from a passwords.zip file, that is, from a ZIP archive:
./zip2john '/home/mial/test/passwords.zip'
Output example:
The first line contains the properties of the archive:
ver 2.0 passwords.zip/passwords.txt PKZIP Encr: cmplen=339, decmplen=490, crc=F872015C type=8
The hash itself goes further:
passwords.zip/passwords.txt:$pkzip2$1*1*2*0*153*1ea*f872015c*0*2b*8*153*f872*3dc8*8cfe495658baa3b5650d212831700dbefbf0c95bbc2831d287121ca64f0a0b7f468c9d3ab88fdce90c7c7e0f9f8978a2d3496661af8dc24e2702398612c927d5f33c243c892bdd11a39f7ecd6c375c7da5df205f6ced61c9d7629d4253f98c01257d45be64f936eeb4bf06060b5e3b2bd286f9322c130d07f88d15af4e6b9a107f0dd2f6c48dc05b4aa81f7f1a9306b5070b7e3414d687a011a73d4a903568e3559c590f2d720542e686d2d6cf70d11d0b60728415ff147263d26f994a73328aad1f204ff2d38c89acbba101e3aff5a0850ef016c64cee400fb5f01834ee37ddedf8051618802547120f52e2c8b2aa4f6d161807aa8d76fd11992e30abd712710da1e238ed17f57ee5af00117016dbd4ae673d6aa9ae694da53c578a0ff6d2af00ebb0dded84cf1f2a966d441b03e22338b4a287d364faa41bea9bc72d0454c0aa654a2e9bb13567aafd5e7043fb6c2289c244*$/pkzip2$:passwords.txt:passwords.zip::/home/mial/test/passwords.zip
An example of a command that saves the hash to the passwords.zip.hash file:
./zip2john '/home/mial/test/passwords.zip' > passwords.zip.hash
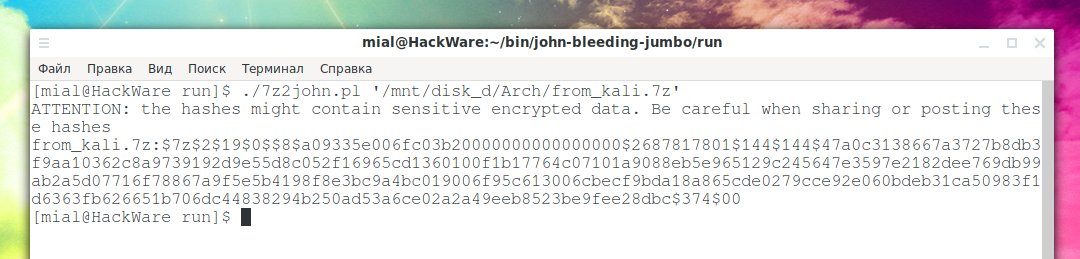
An example of extracting a hash from a .7z archive:
./7z2john.pl '/mnt/disk_d/Arch/from_kali.7z'
Output example:
The first line warns that hashes can contain encrypted sensitive data and you need to be careful if you share the hash with someone or publish it online.
The second line is the hash itself:
from_kali.7z:$7z$2$19$0$$8$a09335e006fc03b20000000000000000$2687817801$144$144$47a0c3138667a3727b8db3f9aa10362c8a9739192d9e55d8c052f16965cd1360100f1b17764c07101a9088eb5e965129c245647e3597e2182dee769db99ab2a5d07716f78867a9f5e5b4198f8e3bc9a4bc019006f95c613006cbecf9bda18a865cde0279cce92e060bdeb31ca50983f1d6363fb626651b706dc44838294b250ad53a6ce02a2a49eeb8523be9fee28dbc$374$00
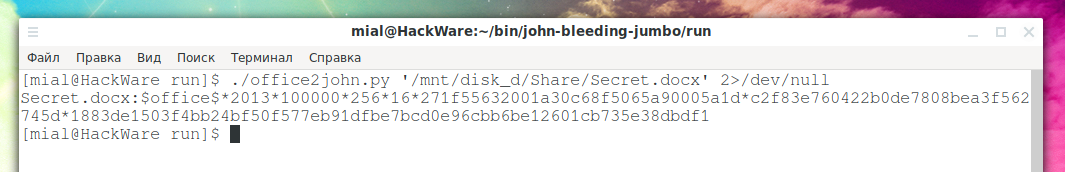
Extract hash from MS Word 2019 file:
./office2john.py '/mnt/disk_d/Share/Secret.docx' 2>/dev/null
If you do not specify 2>/dev/null, then a warning about an outdated Python function in the script will be displayed – I hope this will be fixed in the future.
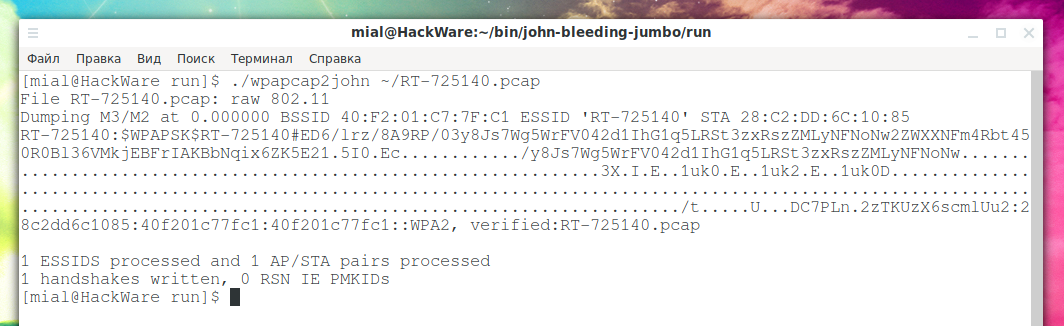
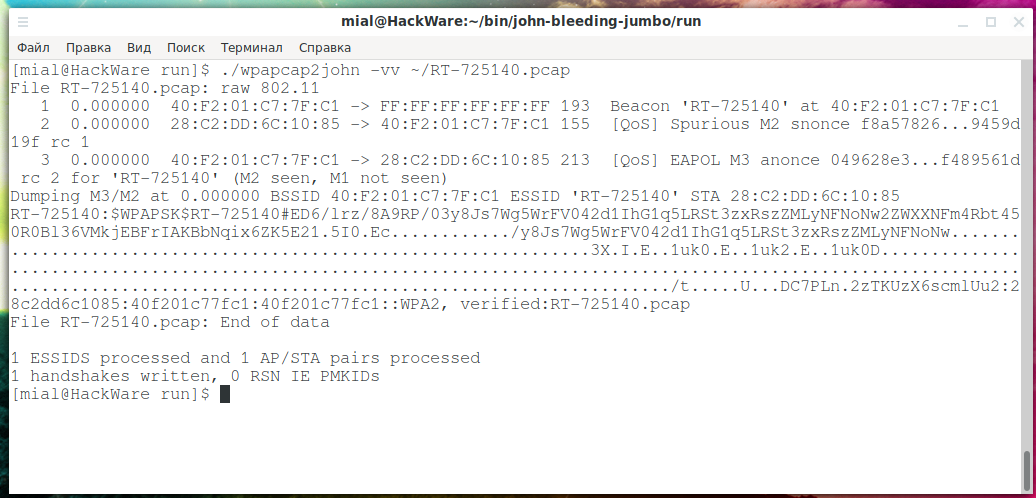
An example of extracting a hash from a handshake to hack Wi-Fi password:
./wpapcap2john ~/RT-725140.pcap
The wpapcap2john utility supports the -v option, so you can see more information if you like:
./wpapcap2john -vv ~/RT-725140.pcap
An example of extracting the VNC hash of a handshake from captured network traffic – this hash allows you to crack the VNC server password.
./vncpcap2john '/home/mial/VNC.pcapng'
Considering that the MAXIMUM (not the minimum) password length is 8 (!) characters, and the algorithm itself is calculated very quickly, such hashes are doomed to be hacked:
192.168.0.101-5900 to 192.168.0.89-57454:$vnc$*894443629F4A9675809CFF5DA2E84651*271D94EB610B5C42588DC53506419E6A
Where to see examples of hashes
As you can imagine, hashes are quite long and (at a glance) meaningless datasets. To understand that you got the hash correctly, sometimes you need to compare it with a similar type.
On this page you will find examples of all hashes: https://hashcat.net/wiki/doku.php?id=example_hashes
But you can see examples of any hash offline, without third-party resources.
You need to start by finding out how your format is correctly named in John the Ripper. To do this, you can find it in the full list of supported formats:
john --list=formats
Examples of format names:
- Office
- ODF
- ZIP
- VNC
- wpapsk
- etc.
Now, to see an example of a hash, run one of the following commands, in which replace the word FORMAT with the name of the format:
john --list=format-details --format=FORMAT john --list=format-all-details --format=FORMAT
I prefer the second version of the command, which displays more information.
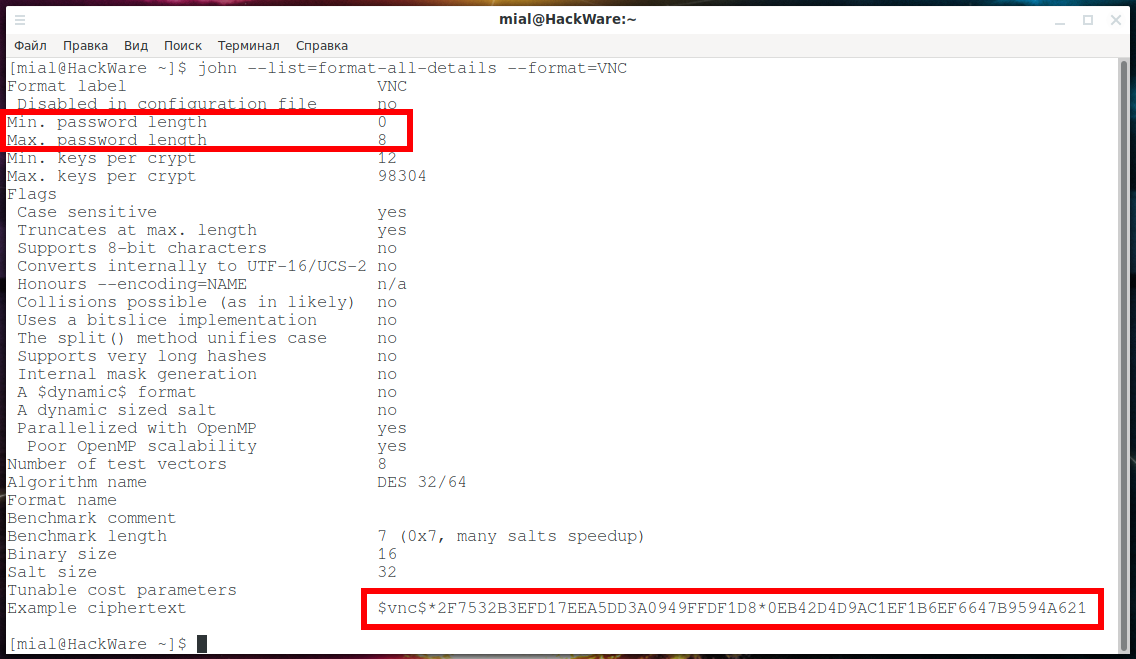
For example, getting information about password properties and an example of a VNC hash:
john --list=format-all-details --format=VNC
I highlighted the hash example with a red border.
Here you can also find other interesting information – the maximum and minimum password length, whether the password is case-sensitive, and so on.
Another example – this time a hash of MS Office files:
john --list=format-all-details --format=Office
Reference for all scripts to generate hashes for John the Ripper and Hashcat
For myself, I have collected all the available information about these files. If you notice inaccuracies in my data or want to supplement them – then write in the comments to this section.
Use Ctrl+f to search this page.
1password2john.py
Extracts hash for cracking 1Password password.
Usage:
./1password2john.py <1Password Agile Keychain(s) / Cloud Keychain(s)> / OnePassword.sqlite
7z2john.pl
Extract hashes from encrypted 7-Zip archives
The dependency is the Perl Compress::Raw::Lzma module. To install it on Debian, Kali Linux and derivatives:
sudo apt install libcompress-raw-lzma-perl
To install on Arch Linux, BlackArch and derivatives with pikaur:
pikaur -S perl-compress-raw-lzma
Usage:
./7z2john.pl <7-Zip file>...
adxcsouf2john.py
This utility extracts ADXCRYPT password hashes from IBM / Toshiba 4690 OS ADXCSOUF.DAT (better known, hence the utility name) and SHA-1 hashes from ADXEPW0F.DAT files.
Usage:
./adxcsouf2john.py <ADXCSOUF.DAT / ADXEPW0F.DAT file(s)>
aem2john.py
JtR utility to convert native Adobe AEM (Adobe Experience Manager) hashes to existing JtR hash format.
Usage:
./aem2john.py <File(s)-with-Adobe-AEM-hashes>
aix2john.pl and aix2john.py
This script converts AIX etc/security/passw.
Usage:
aixpasswd2john.pl <FILE>
If no password is given, then aixpasswd2john.pl will read from standard input.
andotp2john.py
andOTP
Usage:
./andotp2john.py [andOTP backup .json.aes file(s)]
androidbackup2john.py
Android backup files that can be created with the following command:
adb backup -f freeotp-backup.ab -apk org.fedorahosted.freeotp # valid for freeotp app
Usage:
./androidbackup2john.py [Android Backup .ab file(s)]
androidfde2john.py
Program for “converting” Android FDE images / disks into JtR friendly format.
Usage:
./androidfde2john.py <data partition / image> <footer partition / image>
Note: This script only works for old Android <= 4.3 disk images and only aes256/cbc-essiv:sha256 images are supported!
ansible2john.py
ansible-vault
Usage:
./ansible2john.py [Ansible Vault .yml file(s)]
apex2john.py
Dump hashes of APEX.
Usage:
./apex2john.py <apex-hashes.txt file(s)>
applenotes2john.py
Script to extract “hashes” from password protected Apple Notes databases. Typical database location: ~/Library/Group Containers/group.com.apple.notes/NoteStore.sqlite
Usage:
./applenotes2john.py [Apple Notes .sqlite files]
aruba2john.py
ArubaOS password hashing algorithm.
Usage:
./aruba2john.py <ArubaOS hashes file>
atmail2john.pl
axcrypt2john.py
Script to extract hash from AxCrypt encrypted file or self-decrypting binary.
Usage:
./axcrypt2john.py <axxfile> [KEY-FILE]
Optional arguments:
KEY-FILE path to optional key-file provided
bestcrypt2john.py
Usage:
./bestcrypt2john.py [Jetico BestCrypt Containers, .jbc file(s)]
bitcoin2john.py
Retrieves hash from Bitcon wallets to guess password.
Usage:
./bitcoin2john.py [Bitcoin/Litecoin/PRiVCY wallet (.dat) files]
You need to install the bsddb3 package, which is a dependency:
sudo pip3 install bsddb3
bitlocker2john
BitLocker
Usage:
./bitlocker2john -i <Image of encrypted memory unit>
Options:
-h Show this help -i Image path of encrypted memory unit encrypted with BitLocker
bitshares2john.py
Script for extracting hashes from BitShares databases.
Usage:
./bitshares2john.py BitShares SQLite file(s) ./bitshares2john.py Backup Wallet .bin file(s) ./bitshares2john.py ~/BitShares/wallets/<wallet-name>/*.ldb file(s)
Database location: %APPDATA%\BitShares2-light\databases\file__0\{1,2…}
"Local Wallet" at https://wallet.bitshares.org for Google Chrome: ~/.config/google-chrome/Default/databases/https_wallet.bitshares.org_0
Extracting metadata:
sqlite3 Databases.db
sqlite> select * from Databases; 1|file__0|__sysdb__|System Database|4194304 2|file__0|graphene_db_4018d7|graphene_db_4018d7|4194304 3|file__0|graphene_v2_4018d7_default|graphene_v2_4018d7_default|4194304 4|file__0|graphene_v2_4018d7_openwall|graphene_v2_4018d7_openwall|4194304
Extracting hashes:
sqlite3 file__0/4
sqlite> select * from wallet;
3-openwall|{"public_name":"openwall", ..., "encryption_key":"ec4...", ...}
bitwarden2john.py
Utility to extract “hashes” from local data Google Chrome / Firefox / Android.
The plyvel module must be installed as a dependency (the script uses Python 2):
sudo pip2 install plyvel
Usage:
./bitwarden2john.py <Bitwarden storage.js ./bitwarden2john.py com.x8bit.bitwarden_preferences.xml ./bitwarden2john.py Google Chrome's 'nngceckbap...' path
On Linux with Firefox, “storage.js” can be found at the following location: ~/.mozilla/firefox/YOUR-PROFILE/browser-extension-data/\{446900e4-71c2-419f-a6a7-df9c091e268b\}/
On Android with bitwarden 1.14.1, the “hash” can be retrieved from the following location: /data/data/com.x8bit.bitwarden/shared_prefs/com.x8bit.bitwarden_preferences.xml
bks2john.py
Converts BKS keystores to JtR compatible format.
Usage:
bks2john.py [options] <.bks / .uber file(s)>
Options:
-h, --help show this help message and exit -t TYPE, --type=TYPE BKS keystore type (bks / uber)
blockchain2john.py
Blockchain wallet files.
Usage:
./blockchain2john.py [blockchain wallet files]
optional arguments:
-h, --help show this help message and exit --json is the wallet using v2 format? --base64 does the wallet contain only a base64 string?
ccache2john.py
This script extracts a crackable hash from the krb5 credential cache files (e.g. /tmp/krb5cc_1000).
Note: This attack method only works against MS Active Directory servers.
Usage:
./ccache2john.py <input credential cache file>
Example:
./ccache2john.py /tmp/krb5cc_1000
cisco2john.pl
Initial Cisco type 4 password decoder.
Usage:
./cisco2john.pl [cisco config file(s)] >>hashfile 2>>seed.txt ./john -format:md5 -wordlist:seed.txt -rules hashfile
Example:
./cisco2john.pl cisco.config >cisco.in #!comment: Found type 7 passwords: companysecret test
Because of that output, we re-run it and save stderr to its own file.
./cisco2john.pl cisco.conf >cisco.in 2>cisco.seed cat cisco.in enable_secret_level_2:5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8 enable_secret:$1$4C5N$JCdhRhHmlH4kdmLz.vsyq0 ./john -wo:cisco.seed -rules cisco.in
cracf2john.py
Processes CRACF.TXT files (generated by the CRACF program) into a format suitable for JtR.
Usage:
./cracf2john.py <CRACF.TXT>
dashlane2john.py
Retrieves hashes from Dashlane .aes and .dash files.
Usage:
./dashlane2john.py <.aes or .dash files from Dashlane for Windows Desktop / macOS>
Note: This only works with data from Windows and macOS Desktop version of Dashlane.
The required .aes files can be found inside %AppData%\Dashlane\profiles directory tree on Windows.
The required .aes files can be found inside ~/Library/Application\ Support/Dashlane/profiles/ directory tree on macOS.
deepsound2john.py
deepsound2john extracts password hashes from audio files containing encrypted data steganographically embedded by DeepSound (http://jpinsoft.net/deepsound/).
This method is known to work with files generated by DeepSound 2.0.
Input files must be in .wav format. Hashes can be recovered from audio files even after converting from other formats like:
ffmpeg -i INPUT output.wav
Usage:
deepsound2john.py [-h] [--verbose] file [file ...]
Options:
positional arguments: file optional arguments: -h, --help show this help message and exit --verbose, -v
Usage example:
python3 deepsound2john.py carrier.wav > hashes.txt john hashes.txt
diskcryptor2john.py
Retrieves hash from DiskCryptor.
Usage:
./diskcryptor2john.py [DiskCryptor Encrypted Device / Raw Disk Image]
Example:
./diskcryptor2john.py /dev/sdb1
Example:
./diskcryptor2john.py partition_image.raw
Tip: Use kpartx to access partitions within raw disk images on Linux.
Example:
kpartx -av disk_image.raw; fdisk -l disk_image.raw; ./diskcryptor2john.py /dev/mapper/loop0p1
ATTENTION: Cascaded ciphers are NOT supported yet!
dmg2john and dmg2john.py
Apple Disk Samples (DMG).
Usage:
dmg2john [DMG files]
1. Run dmg2john on the .dmg file (s).
For example:
./dmg2john test.dmg > hash
2. Run john on the dmg2john output.
For example:
./john hash
You can use any file of your choice: dmg2john or dmg2john.py, but dmg2john is recommended.
DPAPImk2john.py
The program uses Python 2.
Usage:
DPAPImk2john.py [-h] [-S SID] [-mk MASTERKEY] [-d]
[-c {domain,domain1607+,domain1607-,local}]
[-P PREFERRED] [--password PASSWORD]
Optional arguments:
-h, --help show this help message and exit
-S SID, --sid SID SID of account owning the masterkey file.
-mk MASTERKEY, --masterkey MASTERKEY
masterkey file (usually in %APPDATA%\Protect\<SID>).
-d, --debug
-c {domain,domain1607+,domain1607-,local}, --context {domain,domain1607+,domain1607-,local}
context of user account. 1607 refers to Windows 10
1607 update.
-P PREFERRED, --preferred PREFERRED
'Preferred' file containing GUID of masterkey file in
use (usually in %APPDATA%\Protect\<SID>). Cannot be
used with any other command.
--password PASSWORD password to decrypt masterkey file.
eapmd5tojohn
Usage:
./eapmd5tojohn -r <pcap file>
ecryptfs2john.py
efs2john.py
UPD: this script may have been removed.
Encrypting File System (EFS) is a data encryption system that implements file-level encryption in Microsoft Windows NT operating systems.
For additional functionality, it is recommended to install the python-m2crypto package:
sudo apt install python-m2crypto
Usage:
efs2john.py --masterkey=samples/openwall.efs/92573301-74fa-4e55-bd38-86fc558fa25e --sid="S-1-5-21-1482476501-1659004503-725345543-1003" efs2john.py --masterkey=samples/openwall.efs.2/21d67870-8257-49e0-b2de-c58324271c42 --sid="S-1-5-21-1482476501-1659004503-725345543-1005" efs2john.py --masterkey=samples/Win-2012-non-DC/1b52eb4f-440f-479e-b84a-654fdccad797 --sid="S-1-5-21-689418962-3671548705-686489014-1001" --password="openwall@123"
ejabberd2john.py
Extract hashes from files created by the command:
ejabberdctl dump output.txt
parsimonious module is required dependency, to install it type:
sudo pip install parsimonious
Usage:
./ejabberd2john.py [file(s) generated by 'ejabberdctl dump' command]
electrum2john.py
Generates a hash of the Ethereum crypto wallet file.
Usage:
./electrum2john.py [Ethereum Wallet files (default_wallet)]
encfs2john.py
The encfs2john.py utility processes EncFS files into a format suitable for use with JtR.
Usage:
./encfs2john.py <EncFS folder>
enpass2john.py
Retrieves hashes from Enpass Password Manager version 6.x databases.
Usage:
./enpass2john.py <Enpass .enpassdb files>
enpass5tojohn.py
Retrieves hashes from Enpass Password Manager version 5.x databases.
Usage:
./enpass2john.py <Enpass .enpassdb files>
ethereum2john.py
Retrieves hash from Ethereum Wallets (Geth / Mist / MyEtherWallet).
Usage:
./ethereum2john.py [Ethereum Wallet files (Geth/Mist/MyEtherWallet)]
filezilla2john.py
Retrieves hashes from “FileZilla Server.xml” files.
Usage:
./filezilla2john.py <FileZilla Server.xml file(s)>
geli2john.py
Links:
- https://github.com/freebsd/freebsd/tree/master/sys/geom/eli
- https://github.com/freebsd/freebsd/blob/master/sys/geom/eli/g_eli.h
- https://github.com/freebsd/freebsd/blob/master/sys/opencrypto/cryptodev.h
Usage:
./geli2john.py [disk image]
gpg2john
Utility to prepare for cracking private (secret) PGP Desktop / OpenPGP / GnuPG key.
PGP (English Pretty Good Privacy) is a computer program, also a library of functions that allows you to perform encryption and digital signature of messages, files and other information presented in electronic form, including transparent data encryption on storage devices, for example, on a hard disk.
Usage:
./gpg2john [-d] [-S] <GPG Secret Key File(s)>
- if -d is used, then debugging of the object types decoded is written
- if -S is used, then subkeys will also be output
hccap2john
HCCAP is a custom format specially designed for oclHashcat.
The data itself does not differ from the usual tcpdump format. In fact, they are exactly the same. They are just reorganized a little.
A valid hashcat cap file (file extension: .hccap) contains one or more instances of the structure.
Usage:
./hccap2john <hccap and/or hccapx file[s]>
hccapx2john.py
hccapx2john, process hccapx file into a format suitable for use with JtR.
Usage:
ccapx2john.py [-h] [-nc NC] [--no-mp] hccapx
Options:
positional arguments: hccapx hccapx file to process optional arguments: -h, --help show this help message and exit -nc NC AP nonce correction to be used, 0 to disable, default 8 --no-mp disable message_pair BE/LE/nc detection
htdigest2john.py
This utility processes htdigest files into a format suitable for use with JtR.
Usage:
./htdigest2john.py <htdigest file(s)>
ibmiscanner2john.py
Converts files in the userid:hash format (for example, files created by an older version of the ibmiscanner tool) to the as400-sha format, which can be processed by JtR. Multiple files can be specified.
The output is sent to stdout. Use standard output redirection to generate the JtR file.
Usage:
python2 ./ibmiscanner2john.py file [file ...]
ikescan2john.py
Processes ike-scan output files in a format suitable for use with JtR.
Usage:
./ikescan2john.py <psk-parameters-file> [norteluser]
ios7tojohn.pl
Script generate the hash to brute-force IOS 7 security PIN.
Input example (with com.apple.restrictionspassword.plist):
<key>RestrictionsPasswordKey</key> <data> J94ZcXHm1J/F9Vye8GwNh1HNclA= </data> <key>RestrictionsPasswordSalt</key> <data> /RHN4A== </data>
Output example:
$pbkdf2-hmac-sha1$1000.fd11cde0.27de197171e6d49fc5f55c9ef06c0d8751cd7250
1. Get the com.apple.restrictionspassword.plist file from your phone. How to do this is outside of this document, just google it.
2. Run ios7tojohn on this file, Redirect the output to another file. For instance:
./ios7tojohn com.apple.restrictionspassword.plist > ioshash
3. Run john on a new file using only four digits (this is a PIN code):
./john ioshash -inc:digits -min-len=4 -max-len=4
4. Hacking will take half a second. And not because Apple uses a very poor hash mechanism, but because the PIN code space is extremely small.
itunes_backup2john.pl
Generates a hash for cracking IOS backups.
Explanation of the output format:
1.all binary data is output in hexadecimal form
2.in fact, there are 2 formats, one for IOS backups < 10.0 and one for backups starting from 10.x
Hashes of versions lower than 10:
$itunes_backup$*9*wpky*iter*salt**
Hashes of versions higher than 10.x:
$itunes_backup$*10*wpky*iter*salt*dpic*dpsl
Usage:
./itunes_backup2john.pl <Manifest.plist file>...
iwork2john.py
Generates a hash for cracking iWork files.
Usage:
./iwork2john.py [.key files]
kdcdump2john.py
Kdcdump patch output translation for JtR.
Usage:
./kdcdump2john.py [dump]
keepass2john
Generate hashes for cracking master password from KeePass password managers and forks.
Usage:
./keepass2john [-k] <DATABASES .kdbx>
keychain2john.py
Reworks Mac OS X keychain files into John the Ripper-friendly format.
Usage:
keychain2john [keychain files]
keyring2john.py
Hack GNOME Keyring files, converts Gnome Keyring files to john format.
Usage:
python2 keyring2john.py [-h] KEYRING_FILE
Options:
positional arguments: KEYRING_FILE Input Gnome Keyring file optional arguments: -h, --help show this help message and exit
keystore2john.py
Currently, only Sun “JKS” files are supported.
Usage:
./keystore2john.py <.keystore / .jks file(s)>
kirbi2john.py
Retrieves Kerberos tickets from the kirbi file and parses them to JtR format.
Usage:
./kirbi2john.py exported mimikatz kerberos tickets ./kirbi2john.py extracttgsrepfrompcap.py output
known_hosts2john.py
Processes known_hosts files in a format suitable for use with JtR.
Usage:
python2 ./known_hosts2john.py [known_hosts files]
krb2john.py
This file used to be called krbpa2john.py.
Retrieves AS-REQ and TGS-REP hashes.
Usage:
./krb2john.py <.pdml files>
To create .pdml files using tshark:
tshark -r sample.pcap -T pdml > sample.pdml; ./krb2john.py sample.pdml
Examples of usage. To extract the hashes “AS-REQ (krb-as-req)”:
tshark -r AD-capture-2.pcapng -T pdml > data.pdml tshark -2 -r test.pcap -R "tcp.dstport==88 or udp.dstport==88" -T pdml >> data.pdml ./run/krb2john.py data.pdml
To extract the “TGS-REP (krb-tgs-rep)” hashes:
tshark -2 -r test.pcap -R "tcp.srcport==88 or udp.srcport==88" -T pdml >> data.pdml ./run/krb2john.py data.pdml
kwallet2john.py
Retrieves the KWALLET hash.
Usage:
./kwallet2john.py <.kwl file(s)>
lastpass2john.py
This script converts LastPass input into a format suitable for JtR.
Output format:
filename:$lp$email(salt)$iterations$hash
The file “*_key.itr” just contains the number of calculations (eg 5000). For Firefox on Linux, this file is located in the ~/.lastpass directory.
Read https://lastpass.com/support.php?cmd=showfaq&id=425 before using this script on data from the Windows version of LastPass. Remember that on Windows, CryptProtectData is used to further encrypt data, so this encryption won't work out of the box. For Windows version of LastPass, additional processing (decryption) of data is required.
This script only works for LastPass 3.x for Firefox. The last supported version is LastPass is 3.3.4, released on March 17, 2017.
Older versions of LastPass can be installed from the following link https://addons.mozilla.org/en-US/firefox/addon/lastpass-password-manager/versions/.
LastPass version 4.x uses a very different mechanism that is not yet supported.
It stores data in the following location: ~/.mozilla/firefox/<profile>/storage/permanent/index…/idb/<something>lp.sqlite
Also interesting: https://lastpass.com/js/enc.php
Usage:
./lastpass2john.py <email address> <LastPass *_lpall.slps file> <LastPass *_key.itr file>
OR for lastpass-cli:
./lastpass2john.py <path to .local/share/lpass directory>
ldif2john.pl
libreoffice2john.py
The utility processes OpenOffice / LibreOffice files into a format suitable for JtR.
This utility was previously called odf2john.py.
Output format:
filename:$odf*cipher type*checksum type*iterations*key-size*checksum*iv length*iv*salt length*salt*unused*content.xml data
Usage:
./libreoffice2john.py <OpenOffice / LibreOffice files>
lion2john-alt.pl
This script converts Apple OS X Lion plist file to “shadow” format compatible with John the Ripper.
The Data::Plist module must be installed as a dependency.
To do this, use any of the following methods:
1. CPAN shell:
perl -MCPAN -e shell install Data::Plist
2.cpanm
cpanm Data::Plist
Usage:
./lion2john-alt.pl <plist file> ...
lion2john.pl
Retrieves SHA-512 salted hashes from Mac OS X 10.7 Lion.
The Data::Plist module must be installed as a dependency.
To do this, use any of the following methods:
1. CPAN shell:
perl -MCPAN -e shell install Data::Plist
2.cpanm
cpanm Data::Plist
Usage:
./lion2john.pl PLIST-FILES > PASSWORD-FILE
lotus2john.py
Generates a hash for Lotus Notes.
Usage:
./lotus2john.py [Lotus Notes ID file(s)]
luks2john.py
Generates a hash for cracking LUKS password.
Usage:
./luks2john.py [LUKS file(s) / disk(s)]
mac2john-alt.py
This program helps in extracting password hashes from OS X / macOS systems (>= Mountain Lion -> 10.8+).
Run this program against .plist file(s) obtained from /var/db/dslocal/nodes/Default/users/<username>.plist location.
Usage:
./mac2john-alt.py <OS X / macOS .plist files>
mac2john.py
This program helps in extracting password hashes from OS X / macOS systems (>= Mountain Lion -> 10.8+).
Run this program against .plist file(s) obtained from /var/db/dslocal/nodes/Default/users/<username>.plist location.
Usage:
./mac2john.py <OS X / macOS .plist files>
mcafee_epo2john.py
Converts McAfee ePO password files to John format.
ePO configuration is stored in the database server. Authentication can be based on AD or SHA1 hash stored in the database.
This script converts the CSV output of the dbo.OrionUsers table to the format for john.
The CSV output must at least match the following schema:
- column #1 -> Name (not really used) - column #2 -> AuthURI - column separator must be ","
Example:
cat orion_users.csv # (extracted from dbo.OrionUsers)
Output:
Name,AuthURI system,auth:pwd?pwd=kDv1oBRuGOU3MnpIDbyBJEmJZ%2FauS1zf <-- SHA1 based adminepo,auth:ntlm?domain=XYZ&user=adminepo <-- AD based
Hash generation and attack launch:
./mcafee_epo2john.py orion_users.csv > orion_hashes.txt john -single orion_hashes.txt Loaded 1 password hashes with 1 different salts (dynamic_24 [sha1($p.$s) 128/128 AVX 10x4x1]) Press 'q' or Ctrl-C to abort, almost any other key for status system (system)
Usage:
./mcafee_epo2john.py [dbo.OrionUsers CSV extracts]
monero2john.py
Retrieves hashes from Monero databases.
Usage:
./monero2john.py [Monero .keys file(s)]
WARNING: Only modern (> January, 2016) Monero JSON wallets are supported!
money2john.py
Generates a hash from MS Money files.
Usage:
./money2john.py [MS Money 2002-2007 / Money Plus file(s)]
mongodb2john.js
Retrieves hashes from Mongo databases.
Usage:
mongo admin mongodb2john.js mongo [hostname]:[port]/[database_name] mongodb2john.js
mozilla2john.py
Mozilla Database Password Cracker Assistant (key3.db password master).
Mozilla stores credentials in the signons.sqlite file using base64 encoding, 3DES in CBC encryption mode, and standard block alignment. The decryption key is stored in the key3.db file whose entries are encrypted with a master password.
To check the master password, decrypt the password-check entry and it should be equal to the fixed string “check-password\x00\x00”.
Usage:
mozilla2john [FILES key3.db]
multibit2john.py
Generates a hash for cracking MultiBit Classic and HD wallets.
Usage:
./multibit2john.py [MultiBit Classic or HD wallets files (.key, mbhd.wallet.aes, .wallet)]
MultiBit Classic -> for a wallet named 'xyz', we need the xyz-data/key-backup/xyz*.key OR xyz-data/wallet-backup/xyz*.wallet file.
neo2john.py
It seems the utility generates hash from the Neo Blockchain wallet, but there is no documentation.
Usage:
./neo2john.py [.db3 files]
network2john.lua
Extracts from .pcap files:
- Hashes RADIUS CHAP
- RADIUS authentication hashes
- EAP-MD5 hashes
- SNMPv3 USM hashes
- DHCPv6 authentication hashes
- DHCPv4 authentication hashes
- ISCSI CHAP hashes
- DHCP OMAPI hashes
To work, you need Wireshark with Lua enabled.
Usage:
tshark -q -Xlua_script:network2john.lua -r selected.pcap
Use this for development:
tshark -r selected.pcap -T pdml > data.pdml
office2john.py
Extracts hash from MS Office files for cracking in John the Ripp. Supported files MS Office 2003/2007/2010/2013.
olefile (formerly OleFileIO_PL), version 0.42 2015-01-25. A module for reading / writing Microsoft OLE2 files (also called structured storage or Microsoft compound document file format) such as Microsoft Office 97-2003 documents, Image Composer and FlashPix files, Outlook messages, …
Usage:
./office2john.py <encrypted Office file(s)>
openbsd_softraid2john.py
In OpenBSD 6.1, softraid crypto switched to bcrypt PBKDF instead of PKCS5 PBKDF2.
./openbsd_softraid2john [disk image]
openssl2john.py
This utility helps in cracking files encrypted using "openssl enc" command.
openssl aes-256-cbc -in secret.txt -out secret.txt.enc openssl aes-256-cbc -a -in secret.txt -out secret.txt.enc openssl enc -aes-256-cbc -in secret.txt -out secret.txt.enc
Usage:
./openssl2john.py [-c cipher] [-m md] [-p plaintext] [-a ascii_pct] <OpenSSL encrypted files>
cipher can be: 0 => aes-256-cbc, 1 => aes-128-cbc
md can be: 0 => md5, 1 => sha1, 2 => sha256
ascii_pct: minimum ascii percent (1-100) on decrypted output (ignored if plaintext present)
OpenSSL 1.1.0e uses aes-256-cbc with sha256.
padlock2john.py
Extracts hashes for the Padlock Android cracking.
Usage:
./padlock2john.py [Padblock file(s)]
pcap2john.py
Combines several pcap conversion utilities.
Usage:
python2 ./pcap2john.py [.pcap files]
pdf2john.pl
Extracts hash from encrypted PDF files.
Usage:
pdf2john.pl <.pdf file(s)>
pem2john.py
Generating hashes from .pem files using the PCKS #8 format.
Usage:
./pem2john.py <.pem files using PCKS #8 format>
pfx2john.py
Generate a hash to crack password-protected PKCS12 files.
Usage:
./pfx2john.py <.pfx file(s)>
pgpdisk2john.py
It generates hashes for PGP Virtual Disk FILE (s) .pgd.
Usage:
./pgpdisk2john.py [PGP Virtual Disk .pgd file(s)]
pgpsda2john.py
Calculates a hash for cracking self-decrypting archive (SDA), Symantec Encryption Desktop (SED) PGP archive files.
Usage:
./pgpsda2john.py [PGP self-decrypting archive (SDA) file(s)]
pgpwde2john.py
Retrieves a hash from fully encrypted PGP WDE / Symantec Encryption Destop disk images.
Usage:
./pgpwde2john.py [PGP WDE / Symantec Encryption Destop encrypted whole disk images]
Example:
./pgpwde2john.py hdd.raw
Example:
./pgpwde2john.py /dev/sdb
prosody2john.py
Extracts hashes from Prosody IM's .dat files which can be found under the /var/lib/prosody/<domain>/accounts location.
Usage:
./prosody2john.py [prosody .dat files]
pse2john.py
This script can be used to parse PSE files and extract encrypted material and data in a format that John the Ripper or other cracking tools can use to look for the decryption PIN.
Usage:
python2 ./pse2john.py <.pse file(s)>
ps_token2john.py
Parser Oracle PS_TOKEN token.
Usage:
python2 ps_token2john.py [-h] -c COOKIE
Options:
-h, --help show this help message and exit -c COOKIE Set a victim's PS_TOKEN cookie for parsing
putty2john
Key types supported: RSA, DSA, ECDSA, ED25519
Usage:
putty2john [.ppk PuTTY-Private-Key-File(s)]
pwsafe2john.py
Processes Password Safe files and generates a JtR cracking hash.
Usage:
./pwsafe2john.py [.psafe3 files]
racf2john
Usage:
./racf2john [RACF binary files]
radius2john.pl
Utility to extract hash and brute force RADIUS shared-secret.
The Net::Pcap module must be installed as a dependency.
In Debian, Kali Linux and their derivatives, this is done with the command:
sudo apt install libnet-pcap-perl
On Arch Linux, BlackArch and their derivatives, this can be done with the command:
sudo pacman -S perl-net-pcap
A number of PERL modules are also required, to install them in any system run:
perl -MCPAN -e shell install CPAN::DistnameInfo install NetPacket::IP install Net::Radius::Dictionary
Usage:
./radius2john.pl <pcap FILES>
radius2john.py
Utility to extract hash and brute force RADIUS shared-secret.
Usage:
./radius2john.py <pcap files>
rar2john
Retrieves hash from encrypted RAR archives.
Usage:
./rar2john <rar file(s)>
The -v option increases the verbosity of the output.
Output string format:
For type = 0 for files encrypted with the "rar -hp …" option
archive_name:$RAR3$*type*hex(salt)*hex(partial-file-contents):type::::archive_name
For type = 1 for files encrypted with the "rar -p …" option
archive_name:$RAR3$*type*hex(salt)*hex(crc)*PACK_SIZE*UNP_SIZE*0*archive_name*offset-for-ciphertext*method:type::file_name
or
archive_name:$RAR3$*type*hex(salt)*hex(crc)*PACK_SIZE*UNP_SIZE*1*hex(full encrypted file)*method:type::file_name
sap2john.pl
This Perl script converts password hashes downloaded from SAP systems into a format suitable for John the Ripper (outputs to stdout).
Usage:
./sap2john.pl <input-file> [A|B|D|E|F|H]
To read from standard input:
./sap2john.pl - [A|B|D|E|F|H]
A detailed description of the options is given in the source code of the script.
signal2john.py
Hash extraction for cracking the Signal messenger password.
Modern versions of Signal do not support passphrase.
The script has only been tested with Signal 4.13.5.
Run with the file /data/data/org.thoughtcrime.securesms/shared_prefs/SecureSMS-Preferences.xml.
In the modern version of the Signal Android app (e.g. 4.19.3), the screen lock code is stored as clear text in the SecureSMS-Preferences.xml file!
Usage:
./signal2john.py [SecureSMS-Preferences.xml files]
sipdump2john.py
Processes sipdump output files (dump files) into a format suitable for use with JtR.
Usage:
./sipdump2john.py <sipdump dump files>
ssh2john.py
Retrieves hashes from RSA/DSA/EC/OpenSSH private keys.
Usage:
python2 ./ssh2john.py <RSA/DSA/EC/OpenSSH private key file(s)>
sspr2john.py
Utility to retrieve NetIQ SSPR hashes from a LDAP server.
Usage:
sspr2john.py [-h] -H HOST [-p PORT] -b BASEDN [-s] [-D BINDDN] [-w PASSWORD]
Optional arguments:
-h, --help show this help message and exit
-H HOST, --host HOST Format like ad.example.net or 192.168.124.10
-p PORT, --port PORT Format like 389 or 636
-b BASEDN, --basedn BASEDN
Format like CN=Users,DC=EXAMPLE,DC=NET
-s, --secure Use LDAPS (LDAP OVER SSL), recommended
-D BINDDN, --binddn BINDDN
Format like CN=<username>,CN=Users,DC=EXAMPLE,DC=NET or
<username>
-w PASSWORD, --password PASSWORD
Password for LDAP bind
staroffice2john.py
The staroffice2john.py utility converts StarOffice files into a format suitable for use with JtR.
This utility was previously called sxc2john.py.
Usage:
./staroffice2john.py <StarOffice files (.sxc, .sdw, .sxd, .sxw, .sxi)>
strip2john.py
Processes STRIP files into a suitable format for use with JtR.
Output format:
filename:$strip$*data
Usage:
./strip2john.py <STRIP files>
telegram2john.py
A utility for extracting "hashes" from the userconfing.xml file(s) of the Telegram Android application and from the file (map) of the Telegram Desktop local storage.
Usage:
./telegram2john.py <userconfing.xml file(s) / <path to Telegram data directory>
Example (Linux):
./telegram2john.py ~/.local/share/TelegramDesktop
Example (Windows):
./telegram2john.py "C:/Users/Name/AppData/Roaming/Telegram Desktop"
tezos2john.py (and test_tezos2john.py)
Creates Tezos File For John The Ripper.
Usage:
./tezos2john.py 'mnemonic data (15 words)' 'email' 'public key'
Usage 2:
tezos2john.py [-h] [-i] [-I]
Options:
-h, --help show this help message and exit
-i, --ignoreRules, --ignorerules
Ignore All Rules, seed words, checksum, ...
-I, --ignoreICORules, --ignoreicorules
Do Not Check To See If It Is A Valid ICO Format (15 seed words)
Example:
./tezos2john.py 'put guide flat machine express cave hello connect stay local spike ski romance express brass' 'jbzbdybr.vpbdbxnn@tezos.example.org' 'tz1eTjPtwYjdcBMStwVdEcwY2YE3th1bXyMR'
truecrypt2john.py
Utility to import TrueCrypt volume to a format crackeable by John The Ripper
Usage:
./truecrypt2john.py [-b] volume_filename [keyfiles(s)]> output_file
Options:
-h, --help show this help message and exit -b
Enable -b only when attacking TrueCrypt's boot mode.
uaf2john
Usage:
uaf2john uaf_file
vdi2john.pl
Converts *.vbox files (which contain the encryption information of the associated *.vdi file) to the correct format for JtR processing.
Reads data from STDIN.
vmx2john.py
Usage:
./vmx2john.py [.vmx files]
vncpcap2john
Extract hashes from files with VNC session handshake for password cracking in John the Ripper.
Usage:
./vncpcap2john <pcapfiles>
wpapcap2john
Converts PCAP or IVS2 files to JtR format.
Supported encapsulations: 802.11, Prism, Radiotap, PPI and TZSP over UDP.
Usage:
./wpapcap2john [ОПЦИИ] FILE(S)
Options:
-c Show only complete auths (incomplete ones might be wrong passwords but we can crack what passwords were tried). -v Bump verbosity (can be used several times, try -vv) -d Do not suppress dupe hashes (per AP/STA pair) -r Ignore replay-count (may output fuzzed-anonce handshakes) -f <n> Force anonce fuzzing with +/- <n> -e <essid:mac> Manually add Name:MAC pair(s) in case the file lacks beacons. eg. -e "Magnum WIFI:6d:61:67:6e:75:6d" -m <mac> Ignore any packets not involving this mac adress
zed2john.py
Usage:
./zed2john.py [zed archives]
zip2john
Extract hash from encrypted ZIP archives for password cracking in John the Ripper.
Usage:
./zip2john [options] [zip file(s)]
Options:
-s Scan archive from the beginning, looking for local file headers. This
is less reliable than going by the central index, but might work better
with corrupted or split archives.
Options for 'old' PKZIP encrypted files only:
-a <filename> This is a 'known' ASCII file. This can be faster, IF all
files are larger, and you KNOW that at least one of them starts out as
'pure' ASCII data.
-o <filename> Only use this file from the .zip file.
-c This will create a 'checksum only' hash. If there are many encrypted
files in the .zip file, then this may be an option, and there will be
enough data that false positives will not be seen. If the .zip is 2
byte checksums, and there are 3 or more of them, then we have 48 bits
knowledge, which 'may' be enough to crack the password, without having
to force the user to have the .zip file present.
-m Use "file magic" as known-plain if applicable. This can be faster but
not 100% safe in all situations.
-2 Force 2 byte checksum computation.
Other utilities to extract hashes
hcxtools
hcxtools is a small set of tools for converting captured Wi-Fi packets. Able to convert between different formats and hashes for use with the latest versions of hashcat or John the Ripper.
The following hash modes are supported for John the Ripper: WPAPSK-PMK, PBKDF2-HMAC-SHA1, chap, netntlm, tacacs-plus
hcxkeys
hcxkeys is a small toolbox for generating plainmasterkeys rainbow tables (for cracking Wi-Fi) and hashes for use with the latest hashcat and the latest John the Ripper.
What you need to know when posting hashes
It is considered unethical (perhaps even illegal in some countries) to publish someone else's hashes, since decrypting them means obtaining a password and possible leakage of personal data.
You also need to understand that decrypting some hashes means getting a private key. For example, if you published a hash from a Bitcoin wallet and someone decrypted it, then a third party can manage your wallet, including transferring money.
Related articles:
- Comprehensive Guide to John the Ripper. Part 1: Introducing and Installing John the Ripper (100%)
- Comprehensive Guide to John the Ripper. Part 3: How to start cracking passwords in John the Ripper (how to specify masks, dictionaries, hashes, formats, modes) (100%)
- How to use precomputed tables to crack Wi-Fi passwords in Hashcat and John the Ripper (100%)
- Comprehensive Guide to John the Ripper. Part 4: Practical examples of John the Ripper usage (100%)
- Comprehensive Guide to John the Ripper. Part 5: Rule-based attack (100%)
- How to install NVIDIA drivers, CUDA and Bumblebee on Arch Linux / BlackArch (RANDOM - 50%)