Comprehensive Guide to John the Ripper. Part 4: Practical examples of John the Ripper usage
Table of contents
1. Introducing and Installing John the Ripper
2. Utilities for extracting hashes
4. Practical examples of John the Ripper usage
4.2 How to crack Wi-Fi password in John the Ripper
4.3 How to crack ZIP archive password
4.4 How to crack RAR archive password
4.5 How to crack 7z archive password
4.6 How to crack Word password (.DOCX file)
4.7 How to crack LibreOffice password (Wirter/.odt files and others)
4.9 How to crack KeePass and KeePassXC Password
4.10 How to crack GPG password
4.11 How to crack private SSH key password (id_rsa)
4.12 How to crack PuTTY password
6. How to brute force non-standard hashes
7, Johnny – GUI for John the Ripper
8.
9.
In the previous three parts, we covered the basic topics that will allow you to install John the Ripper, extract the hash from the encrypted file and launch a password cracking attack – suck brute-force attacks as dictionary attack and mask. In addition to these questions, further theory on John the Ripper will be considered in more depth: how to set up a configuration file, more attack modes, encoding features, and much more.
But before moving on to further theory elsewhere in this online tutorial, let's take a look at some practical examples of John the Ripper. This article will provide clear answers to questions like these:
- how to hack Wi-Fi password
- how to crack archive password
- how to crack office document password
- etc.
These examples will allow us to reinforce our knowledge about John the Ripper. By the way, if you have not read the previous parts, then it is recommended to start with them.
Option --fork=CORES
In the following examples, the --fork=CORES option is used in each brute-force start command on the central processor. Instead of the word CORE, you must specify a number that corresponds to the quantity of logical or physical processor cores.
You do not need to use this option for hacking on video cards.
How to crack Wi-Fi password in John the Ripper
Capturing Wi-Fi handshake for password cracking
Here we will not dwell on the basics of testing the security of wireless Wi-Fi networks, so if you have gaps in your knowledge, then refer to “Wireless Attacks” category.
Let's see the name of the wireless interface:
sudo iw dev
I have this wlp0s20f0u1. To automatically capture handshakes, run a command like this:
sudo besside-ng INTERFACE
In my case, this is:
sudo besside-ng wlp0s20f0u1
To see which handshakes were captured, run the command:
aircrack-ng wpa.cap
Hash extraction for Wi-Fi hacking
If you want to hack all handshakes at once, then run the command:
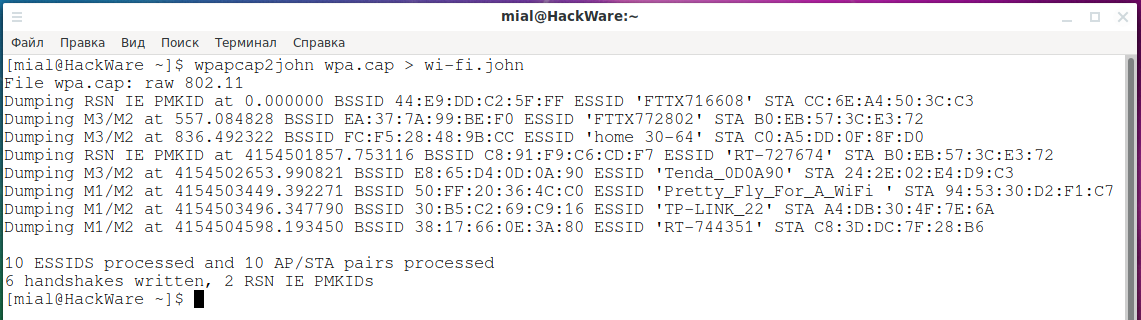
wpapcap2john wpa.cap > wi-fi.hash
This will generate hashes for all captured handshakes.
The output says that 10 APs were processed, but only 6 handshakes and 2 PMKIDs were dumped.
You can save the handshake for a specific access point, you need to specify it with the -m option, but you need to specify not the name, but the BSSID – in other words, the MAC address.
To find out the required MAC address, run the command:
wpapcap2john wpa.cap > /dev/null
Let's say I'm interested in the FTTX772802 Access Point, then we are looking for a line with it:
Each line has three data items:
- BSSID – MAC address of the AP (we need it)
- ESSID – the name of the AP (by which we know where to look at the MAC address)
- STA – MAC address of the client connected to the AP (this is not useful to us)
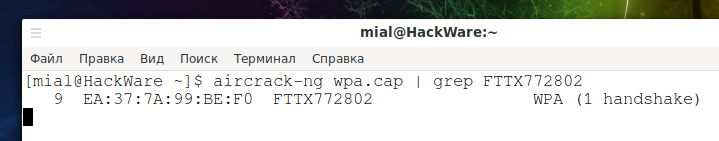
Or you could see the MAC address using aircrack-ng:
aircrack-ng wpa.cap | grep 'AP-NAME'
For instance:
aircrack-ng wpa.cap | grep FTTX772802
So, I found that an AP named FTTX772802 has a MAC address EA:37:7A:99:BE:F0.
To save the handshake only for a specific AP, run a command like this:
wpapcap2john -m 'MAC ADDRESS' wpa.cap > wi-fi.hash
In my case, this is:
wpapcap2john -m 'EA:37:7A:99:BE:F0' wpa.cap > wi-fi.hash
Wi-Fi password brute-force: dictionary attack
Now, to launch a dictionary attack using the central processor (CPU), run a command like:
john --format=wpapsk --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/wi-fi.hash
For example, my dictionary is in the same folder as the executable file john and has the name rockyou.txt, and my computer has 12 cores, and wi-fi.hash is in the user's home folder, then the command is as follows:
./john --format=wpapsk --wordlist=rockyou.txt --fork=12 ~/wi-fi.hash
To launch a dictionary attack using a video card (GPU), run the command:
john --format=wpapsk-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/wi-fi.hash
My example:
./john --format=wpapsk-opencl --wordlist=rockyou.txt ~/wi-fi.hash
Wi-Fi password brute-force: mask attack
To try all passwords containing only numbers and length from 8 to 10 characters and perform calculations on the CPU, run a command like:
john --format=wpapsk --fork=CORES --mask='?d' --min-length=8 --max-length=10 /PATH/TO/wi-fi.hash
My example:
./john --format=wpapsk --fork=12 --mask='?d' --min-length=8 --max-length=10 ~/wi-fi.hash
To try all passwords consisting only of numbers and from 8 to 10 characters long and perform calculations on GPU, run a command like this:
john --format=wpapsk-opencl --mask='?d' --min-length=8 --max-length=10 '/PATH/TO/wi-fi.hash'
My example:
./john --format=wpapsk-opencl --mask='?d' --min-length=8 --max-length=10 ~/wi-fi.hash
To try all passwords consisting of numbers, as well as uppercase and lowercase letters, 8 characters long and perform calculations on the CPU, run a command like:
john --format=wpapsk --fork=CORES -1=?l?u?d --mask='?1' --min-length=8 --max-length=8 /PATH/TO/wi-fi.hash
To iterate over all passwords consisting of numbers, as well as large and small letters, 8 characters long and perform calculations on a video card, run a command like this:
john --format=wpapsk-opencl -1=?l?u?d --mask='?1' --min-length=8 --max-length=8 /PATH/TO/wi-fi.hash
See also “How to use rainbow tables to crack Wi-Fi passwords in Hashcat and John the Ripper”.
How to crack ZIP archive password
To extract the hash, run a command like this:
zip2john FILE > zip.hash
For example, the path to the file /mnt/disk_d/Share/test/file.zip, then the command is as follows:
zip2john /mnt/disk_d/Share/test/file.zip > zip.hash
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like this:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/zip.hash
For example, my dictionary is located in the same folder as the executable file john and has the name rockyou.txt, and on my computer there are 12 cores, and zip.hash is in the user's home folder, then the command is as follows:
./john --wordlist=rockyou.txt --fork=12 ~/zip.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/zip.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/zip.hash
How to crack passwords of ZIP archives on a video card
John the Ripper supports two algorithms for cracking ZIP archives on the CPU:
- PKZIP
- ZIP
And only one archive for cracking on video cards:
- ZIP-opencl
In the previous commands, we did not specify the hash type, since it is uniquely indicated in the hash itself. To use a video card, you must use the --format=HASH option. But it will only work for ZIP format. Therefore, you need to open the file where the hash is saved and look at the beginning of the hash.
If you see something like this there:
- file2.zip/file.docx:$zip2$*0*3*0*3eca0462af8ea24……………….
This means that this hash can be cracked with commands like:
john --format=ZIP-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/zip.hash john --format=ZIP-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/zip.hash john --format=ZIP-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/zip.hash
If there is a hash with the “pkzip” string:
- file.zip/Отчёт.docx:$pkzip2$1*1*2*0*b274*c3db*7c823487*0*28*8*b……………….
This means that cracking of this format on the video card is currently not supported.
How to crack RAR archive password
To extract the hash, run a command like this:
rar2john FILE > rar.hash
For example, the path to the /mnt/disk_d/Share/test/file.rar file, then the command is as follows:
rar2john /mnt/disk_d/Share/test/file.rar > rar.hash
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/rar.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/rar.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/rar.hash
How to crack passwords of RAR archives on a video card
John the Ripper supports two algorithms for cracking RAR archives on the CPU: rar and RAR5.
In the previous commands, we did not specify the hash type, since it is uniquely indicated in the hash itself. To use the video card, you must use the --format=HASH option. As the HASH, you need to specify rar-opencl or RAR5-opencl, depending on the type of archive.
The type of archive can be found by the hash. Therefore, you need to open the file where the hash is saved and look at the beginning of the hash.
If you see something like this there (the "rar5" line is present):
- /mnt/disk_d/Share/test/file-rar5.rar:$rar5$16$76ce05b54ff5af……………….
This means that this hash can be cracked with commands like:
john --format=RAR5-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/rar.hash john --format=RAR5-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/rar.hash john --format=RAR5-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/rar.hash
If there is a hash with the string "RAR3":
- file-rar4.rar:$RAR3$*1*2dfc09f8674acc2e*8734827c*45584*50139*1*02dfdd427b08ebce3f0……………….
Then you need to use commands like:
john --format=rar-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/rar.hash john --format=rar-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/rar.hash john --format=rar-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/rar.hash
How to crack 7z archive password
To extract the hash, run a command like this:
7z2john FILE > 7z.hash
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/7z.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/7z.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/7z.hash
How to crack passwords of 7z archives on a video card
To launch a dictionary attack using GPU, run a command like this:
john --format=7z-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/7z.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on a video card, run a command of the form:
john --format=7z-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/7z.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, 1 to 8 characters long and perform calculations on a video card, run a command like this:
john --format=7z-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/7z.hash
How to crack Word password (.DOCX file)
To extract the hash, run a command like this:
office2john FILE > office.hash
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/office.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/office.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/office.hash
How to Crack Word Passwords (.DOCX) on a Graphics Card
To launch a dictionary attack using GPU, run a command like this:
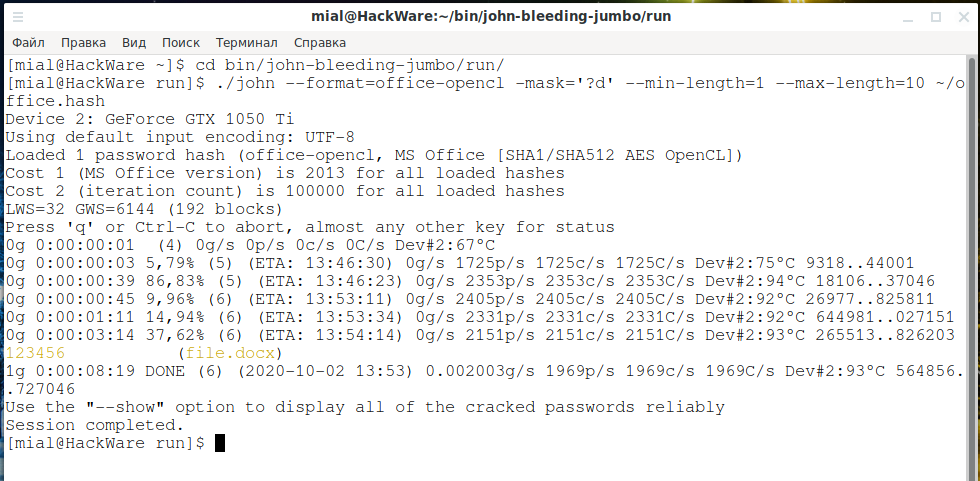
john --format=office-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/office.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on a video card, run a command of the form:
john --format=office-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/office.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, 1 to 8 characters long and perform calculations on a video card, run a command like this:
john --format=office-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/office.hash
An example of a successful Word password cracking:
How to crack LibreOffice password (Wirter/.odt files and others)
To retrieve the hash, run a command like:
libreoffice2john FILE > odf.hash
If you see the error:
Traceback (most recent call last):
File "/usr/bin/libreoffice2john", line 152, in <module>
process_file(sys.argv[k])
File "/usr/bin/libreoffice2john", line 86, in process_file
salt = binascii.hexlify(base64.b64decode(salt)).decode("ascii")
UnboundLocalError: local variable 'salt' referenced before assignment
then upgrade JtR to the latest version.
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/odf.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/odf.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/odf.hash
How to crack LibreOffice passwords (.odt and others) on a video card
To launch a dictionary attack using GPU, run a command like this:
john --format=ODF-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/odf.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on a video card, run a command of the form:
john --format=ODF-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/odf.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, 1 to 8 characters long and perform calculations on a video card, run a command like this:
john --format=ODF-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/odf.hash
How to crack PDF password
To extract the hash, run a command like this:
pdf2john FILE > pdf.hash
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/pdf.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/pdf.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/pdf.hash
How to Crack PDF Passwords on a Graphics Card
Currently, John the Ripper does not support cracking a PDF password on GPU.
How to crack KeePass and KeePassXC Password
To extract the hash, run a command like this:
keepass2john FILE > keepass.hash
The FILE must be a .kdbx password database.
Or if you have a key file, then run a command like this::
keepass2john -k <KEY FILE> <DATABASE .kdbx>
You can see the message:
! Passwords.kdbx : File version '40000' is currently not supported!
It means that the Passwords.kdbx FILE uses the KDBX version 4.0 database, and the keepass2john program only supports the KDBX version of KDBX 3.1. That is, it is currently not possible to crack a KeePass password with a KDBX version 4.0 database in John the Ripper.
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/keepass.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/keepass.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/keepass.hash
How to Crack KeePass Passwords on GPU
To launch a dictionary attack using a video card, run a command like this:
john --format=KeePass-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/keepass.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on a video card, run a command of the form:
john --format=KeePass-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/keepass.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, 1 to 8 characters long and perform calculations on a video card, run a command like this:
john --format=KeePass-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/keepass.hash
How to crack GPG password
There are .key files in the ~/.gnupg/private-keys-v1.d/ folder, but if it is possible to extract keys and passwords from them, I don't know.
The gpg password can be cracked from the private key file obtained from the export command:
gpg --export-secret-key -a "NAME SURNAME" > private.key
After export, from this private key file, you need to extract the hash to crack the password:
gpg2john private.key > gpg.hash
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/gpg.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/gpg.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/gpg.hash
How to crack gpg passwords on a video card
To launch a dictionary attack using GPU, run a command like this:
john --format=gpg-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/gpg.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on a video card, run a command of the form:
john --format=gpg-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/gpg.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, 1 to 8 characters long and perform calculations on a video card, run a command like this:
john --format=gpg-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/gpg.hash
How to crack private SSH key password (id_rsa)
To extract the hash, run a command like this:
python2 ./ssh2john.py FILE > ssh.hash
Note that ssh2john requires Python 2 to run. If you are using Python 3, you will receive the following error:
/usr/bin/ssh2john:103: DeprecationWarning: decodestring() is a deprecated alias since Python 3.1, use decodebytes()
data = base64.decodestring(data)
Traceback (most recent call last):
File "/usr/bin/ssh2john", line 193, in <module>
read_private_key(filename)
File "/usr/bin/ssh2john", line 153, in read_private_key
saltstr = data[salt_offset:salt_offset+salt_length].encode("hex")
AttributeError: 'bytes' object has no attribute 'encode'
As a FILE, you need to specify the private SSH key, the path to it can be ~/.ssh/id_rsa.
This key is generated by the command:
ssh-keygen -t rsa
Brute force on a central processor
Now, to launch a dictionary attack using the CPU, run a command like:
john --wordlist=/PATH/TO/DICTIONARY --fork=CORES /PATH/TO/ssh.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=CORES --mask='?d' --min-length=1 --max-length=10 /PATH/TO/ssh.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters long and perform calculations on the CPU, run a command like this:
john --fork=CORES -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/ssh.hash
How to crack SSH passwords (id_rsa) on a video card
To launch a dictionary attack using GPU, run a command like this:
john --format=ssh-opencl --wordlist=/PATH/TO/DICTIONARY /PATH/TO/ssh.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on a video card, run a command of the form:
john --format=ssh-opencl -mask='?d' --min-length=1 --max-length=10 /PATH/TO/office.hash
To iterate over all passwords consisting of numbers, as well as uppercase and lowercase letters, 1 to 8 characters long and perform calculations on a video card, run a command like this:
john --format=ssh-opencl -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /PATH/TO/office.hash
Error “cipher value of 6 is not supported!”
When starting john, you may receive errors:
[SSH] cipher value of 6 is not supported! [ssh-opencl] cipher value of 6 is not supported!
They mean that your hash type is not supported by john. Please update John the Ripper to the latest version to fix these errors.
If you receive the following message:
[ssh-opencl] cipher value of 6 is not yet supported with OpenCL!
It means that you can run the jailbreak on the CPU, but you cannot use the video card. Try updating John the Ripper to the latest version, but this support has not been added at the time of writing.
How to crack PuTTY password
PuTTY is a popular program for connecting to remote computers using Telnet, SSH, Rlogin, Serial and Raw protocols. This program is especially widespread on Windows, since before it had no alternatives on this OS.
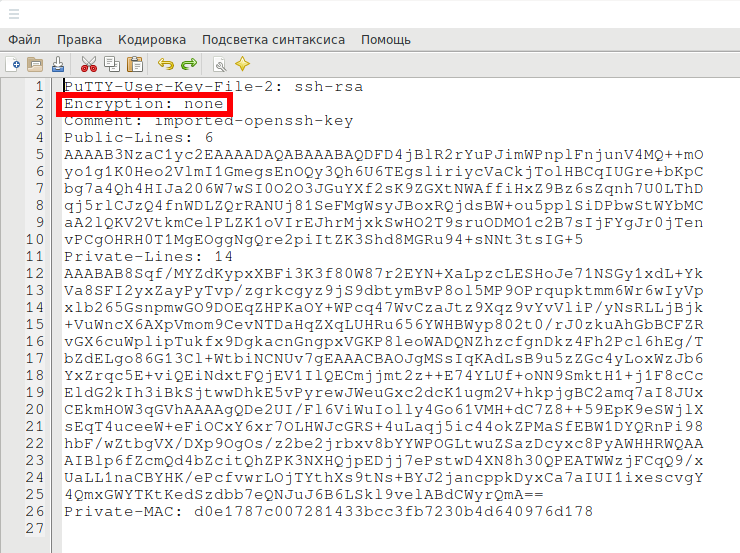
Files generated in PuTTYgen have a .ppk extension and have a structure similar to the following:
This file contains both private and public keys.
First of all, pay attention to the line with the word Encryption:
Encryption: none
If there is “none” word, it means that the key is not encrypted at all and you can use it in PuTTY. If you want to use it in the familiar OpenSSH, you just need to convert it to the appropriate format, as described in the section “How to convert a .ppk key to an OpenSSH key” below.
To convert, use a command of the form:
putty2john FILE.ppk > putty.hash
You can get the message:
file.ppk : this private key doesn't need a passphrase!
It means that the keys in the .ppk file are not encrypted and there is nothing to brute-force, it is enough to convert to the format you need.
Brute force on a central processor
To launch a dictionary attack using the CPU, run a command like:
john --wordlist=/ПУТЬ/ДО/СЛОВАРЯ --fork=ЯДРА /ПУТЬ/ДО/putty.hash
To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:
john --fork=ЯДРА --mask='?d' --min-length=1 --max-length=10 /ПУТЬ/ДО/putty.hash
To iterate over all passwords, consisting of numbers, as well as uppercase and lowercase letters, from 1 to 8 characters and perform calculations on the CPU, run a command like:
john --fork=ЯДРА -1=?l?u?d --mask='?1' --min-length=1 --max-length=8 /ПУТЬ/ДО/putty.hash
How to crack PuTTY passwords on a video card
Currently, John the Ripper does not support cracking a PuTTY file password on a video card.
How to convert a .ppk key to an OpenSSH key
Install PuTTY package.
In Debian, Kali Linux, Linux Mint, Ubuntu and their derivatives:
sudo apt install putty
RPM based
yum install putty
Gentoo
emerge putty
Arch Linux, BlackArch and their derivatives:
sudo pacman -S putty
OS X:
Install Homebrew, then run
brew install putty
Place your keys in some directory, e.g. your home folder. Now convert the PPK keys to SSH.
To export the private key:
cd ~ puttygen id_dsa.ppk -O private-openssh -o id_dsa
and to export the public key:
puttygen id_dsa.ppk -O public-openssh -o id_dsa.pub
Move these keys to ~/.ssh and make sure the permissions are set to private for your private key:
mkdir -p ~/.ssh mv -i ~/id_dsa* ~/.ssh chmod 600 ~/.ssh/id_dsa chmod 666 ~/.ssh/id_dsa.pub
Section Conclusion
If I missed another important or popular file type, write about it in the comments and I will add examples of how to crack its password.
Related articles:
- Comprehensive Guide to John the Ripper. Part 3: How to start cracking passwords in John the Ripper (how to specify masks, dictionaries, hashes, formats, modes) (84.5%)
- Comprehensive Guide to John the Ripper. Part 6: How to brute force non-standard hashes (84.5%)
- Comprehensive Guide to John the Ripper. Part 7: Johnny – GUI for John the Ripper (84.5%)
- Advanced wordlist generating techniques (82.6%)
- How to create dictionaries that comply with specific password strength policies (using Rule-based attack) (79.7%)
- Word lists for brute-force (RANDOM - 63.9%)


I'm having this error
Sorry I don’t see your error.