Programs for extracting information from the Windows registry
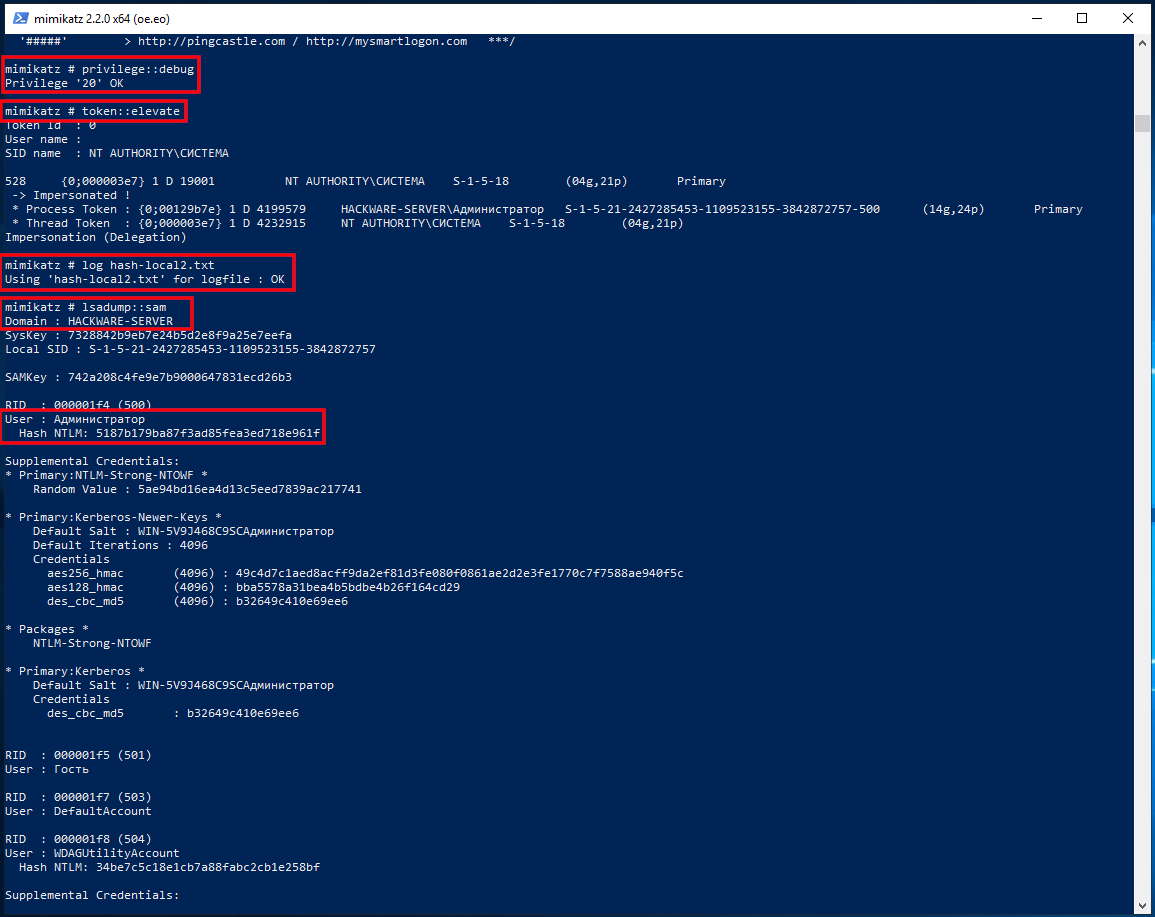
mimikatz
Program mimikatz has many features related to Windows security and stored passwords. Among other things, the program can extract passwords, secrets and hashes both from the system it is running on and from the saved files of the registry hives.
Instructions:
- How to hack a Windows password
- How to decrypt stored Windows passwords using mimikatz and DAPA
- Pass-the-hash attack (how to use NTLM without cracking a password)
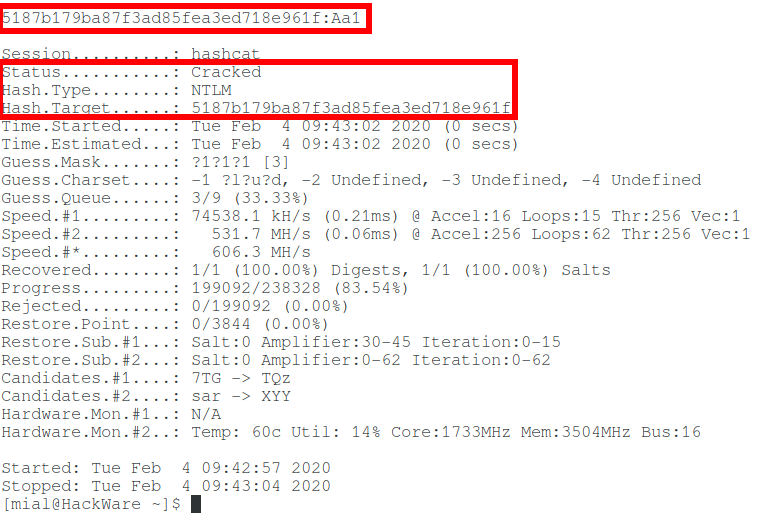
From the extracted hashes, the user's password can be cracked.
RegRippy (regrip.py)
RegRippy is a platform for reading and extracting forensic useful data from Windows registry hives.
Installation on Kali Linux
sudo apt install python3-pip sudo pip3 install regrippy
Installation in BlackArch
sudo pacman -R regrippy python-enum-compat python-python-registry python-unicodecsv sudo pip3 install regrippy
This program can also be installed on Windows. Start by installing Python and PIP. After installing Python and PIP on Windows, run the following command:
pip install regrippy
Check if the installation was successful:
regrip.py --help regrip.py -l
An example of a command that gets the name of the computer (compname) that owns the registry hive located at the path /mnt/disk_d/Share/config/SYSTEM (--system /mnt/disk_d/Share/config/SYSTEM):
regrip.py compname --system /mnt/disk_d/Share/config/SYSTEM
Output example:
HACKWARE-MIAL
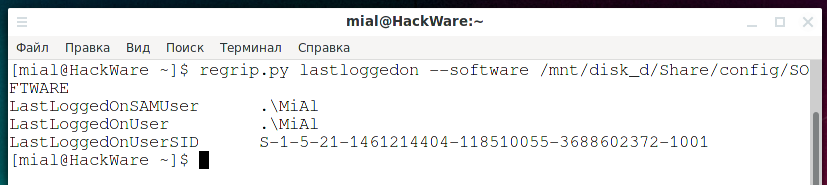
An example of a command that displays information about the last logged-in user (lastloggedon) using the SOFTWARE registry hive (--software /mnt/disk_d/Share/config/SOFTWARE):
regrip.py lastloggedon --software /mnt/disk_d/Share/config/SOFTWARE
Output example:
LastLoggedOnSAMUser .\MiAl LastLoggedOnUser .\MiAl LastLoggedOnUserSID S-1-5-21-1461214404-118510055-3688602372-1001
RegRipper
RegRipper is an open source tool written in Perl to extract/parse information (keys, values, data) from the registry and present it for analysis.
RegRipper consists of two main tools, each providing similar capabilities. RegRipper's graphical interface allows the analyst to select a registry hive for analysis, an output file for results, and a profile (list of plugins) for working with the hive. When the analyst runs the tool against the registry hive, the results go to the file specified by the analyst. If the analyst decides to analyze the System hive, he can also send the results to system.txt. The GUI tool will also create a log of its activity in the same directory as the output file using the same filename but with a .log extension (that is, if the output is written to system.txt, the log will be written to the system.log).
RegRipper also includes a command line (CLI) tool called rip. Rip can be directed to analyze a hive and can run either a profile (list of plugins) or a separate plugin for that hive, sending the results to STDOUT. Rip can be included in batch files by using redirection operators to send the output to a file. Rip does not keep a log of its activities.
Installing and running on Linux
Download the required files:
git clone https://github.com/keydet89/RegRipper3.0 cd RegRipper3.0
Wine is easiest to run with, so start by installing it.
sudo dpkg --add-architecture i386 sudo apt update sudo apt install wine winbind
Then run:
wine rr.exe
Installation on Windows
Download and unzip the archive from the link: https://github.com/keydet89/RegRipper3.0/archive/master.zip
To open the GUI, double-click the rr.exe file.
If you want to use the command line utility, open PowerShell or CMD, go to the folder with the unpacked archive and run the file
rip.exe
Running a GUI program on Linux:
wine rr.exe
Select the branch of the registry for analysis and the file name to save the report.
Then click the “Rip!” button.
Wait for the completion of the work.
Open the report file.
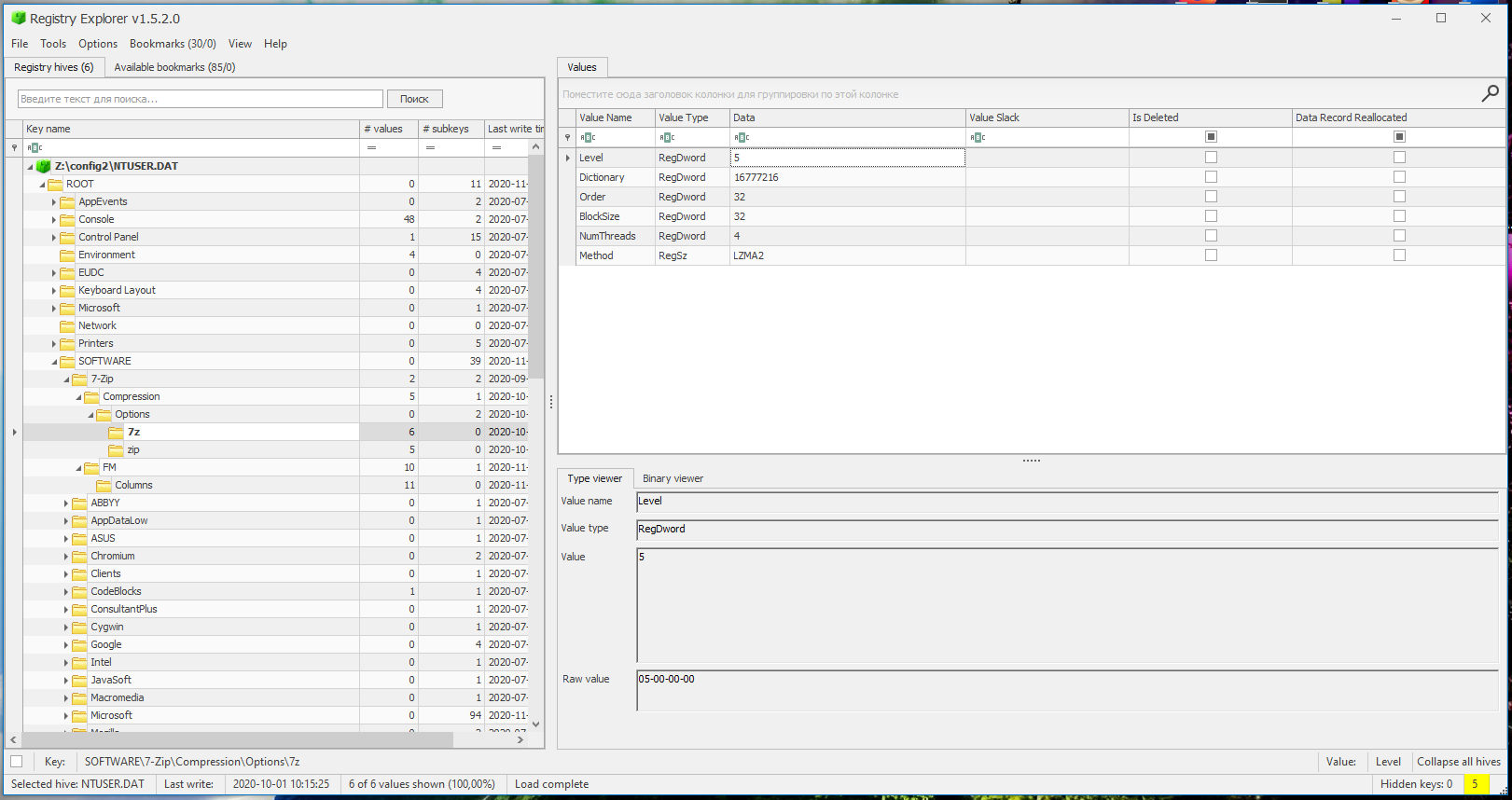
Registry Explorer
Registry Explorer is a GUI-based tool used to view the contents of offline registry hives. It can load multiple hives at once, search all loaded hives using strings or regular expressions, export data, you can bookmark selections, save changes made to a project, and much more.
Installing Registry Explorer on Windows
The program is designed to work on Windows and requires a full environment of the Microsoft .net framework version 4.6 or higher (you can download it from the link https://www.microsoft.com/en-us/download/details.aspx?id=49982).
Download the “Registry Explorer/RECmd” archive from https://ericzimmerman.github.io/. Unpack it to any folder, the program is portable and does not require installation.
Double-click the RegistryExplorer.exe file to launch the GUI.
creddump
creddump is a Python tool for extracting various credentials and secrets from Windows registry hives. It currently retrieves:
- LM and NT hashes (protected by SYSKEY)
- Domain cached passwords
- LSA secrets
The program is preinstalled in Kali Linux.
Installation in BlackArch:
sudo pacman -S creddump
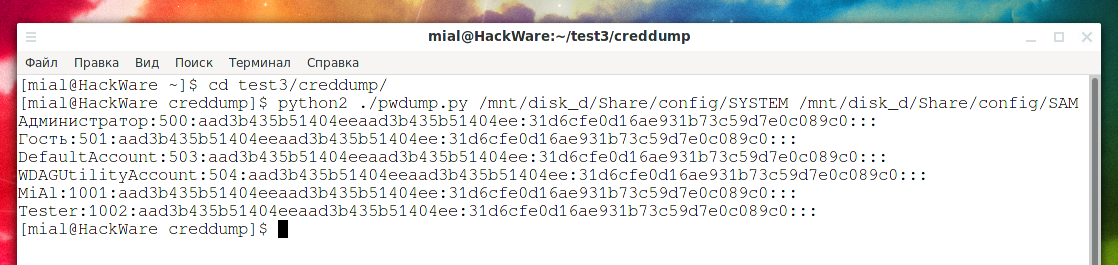
An example of a command that displays local password hashes, registry hives are located in the /mnt/disk_d/Share/config/SYSTEM and /mnt/disk_d/Share/config/SAM files:
python2 ./pwdump.py /mnt/disk_d/Share/config/SYSTEM /mnt/disk_d/Share/config/SAM
Output example:
Администратор:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Гость:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: MiAl:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Tester:1002:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
regipy
Regipy is a Python library for parsing offline registry hives.
The program can:
- Dump the entire registry hive to json
- Complete transactions in the registry hive according to the log files
- Compare registry hives
- Extract information using plugins
Installation on Kali Linux
sudo apt install python3-pip sudo pip3 install regipy
Installation in BlackArch
sudo pacman -S regipy
Example of command to run plugins to extract information from the SYSTEM hive and save the results to the plugins_output.json file:
registry-plugins-run ~/Documents/TestEvidence/Registry/SYSTEM -o /tmp/plugins_output.json
chntpw
chntpw – this small program allows you to view information and change user passwords in the Windows NT/2000 user database file. You don't need to know the old passwords as they will be overwritten. In addition, it also contains a simple registry editor (writing data of the same size) and a hex editor that lets you tinker with the bits and bytes in the file as you like.
Installing chntpw
The program is preinstalled in Kali Linux.
Installation in BlackArch
sudo pacman -S chntpw
Examples of commands:
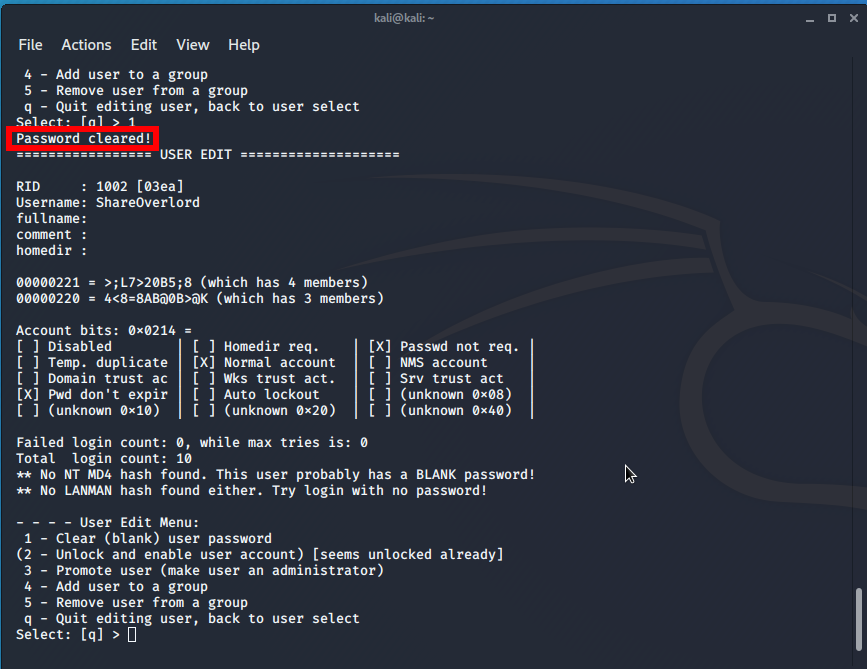
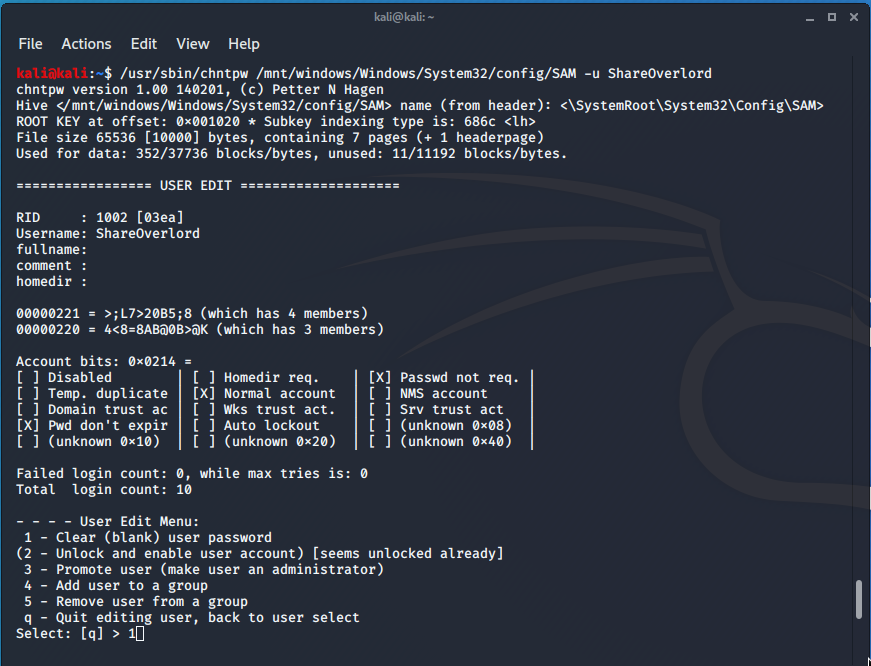
Resetting the password for the ShareOverlord user (-u ShareOverlord) when the registry hive is located at /mnt/windows/Windows/System32/config/SAM:
sudo /usr/sbin/chntpw /mnt/windows/Windows/System32/config/SAM -u ShareOverlord
Unlock User Administrator:
sudo /usr/sbin/chntpw /mnt/windows/Windows/System32/config/SAM -u Администратор
Instructions: How to reset a Windows password
Retrieving Windows Registry Hives from Virtual Machines
With the virt-win-reg utility included in the libguestfs package, you can extract Windows registry hives directly from virtual disks without even starting the virtual machines. For details on libguestfs, see “How to open disks of virtual machines and download and upload files to them”.
virt-win-reg allows you to extract Windows registry hives, including those available only for the System account.
General command form:
virt-win-reg '/PATH/TO/VIRTUAL/DISK' 'REGISTRY\HIVE'
By default, the content will be displayed on the screen, so you must use output redirection to save the data to a file.
For example, the command to extract the HKEY_LOCAL_MACHINE\SYSTEM hive from the Windows operating system, whose virtual disk is located in mnt/disk_d/Виртуальные машины/Windows 10 (en).vdi and save the resulting data to the SYSTEM.reg file:
virt-win-reg '/mnt/disk_d/Виртуальные машины/Windows 10 (en).vdi' 'HKEY_LOCAL_MACHINE\SYSTEM' > SYSTEM.reg
Another example, extracting the HKEY_LOCAL_MACHINE\SAM registry hive from the disk image /mnt/disk_d/Виртуальные машины/Windows Server 2019.vdi and saving the data to the SAM.reg file:
virt-win-reg '/mnt/disk_d/Виртуальные машины/Windows Server 2019.vdi' 'HKEY_LOCAL_MACHINE\SAM' > SAM.reg
NirSoft registry utilities
To work with the registry, pay attention to such utilities as:
- RegScanner
- OfflineRegistryFinder
- OfflineRegistryView
- RegistryChangesView
- RegFromApp
- RegDllView
- ActiveXHelper
- RegFileExport
Windows Registry Tools: https://www.nirsoft.net/windows_registry_tools.html
winregfs
The winregfs program mounts the Windows registry hives to the file system. This allows you to navigate through the key hierarchy like regular folders, and the values can be edited like regular text files.
In addition, the package has a tool called “fsck.winregfs” that performs basic integrity checks on the registry hive.
Installation on Kali Linux
sudo apt install winregfs
Installation in BlackArch
sudo pacman -S winregfs
To use winregfs, create a mount directory and point it to the registry hive of interest:
mkdir /tmp/reg mount.winregfs /mnt/disk_d/Share/config/SOFTWARE /tmp/reg
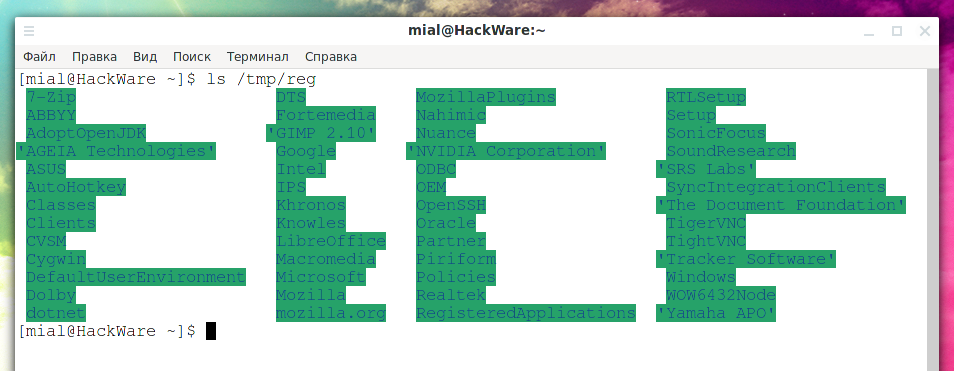
Now you can see everything in this hive in the “/tmp/reg” directory:
ls /tmp/reg
Output example:
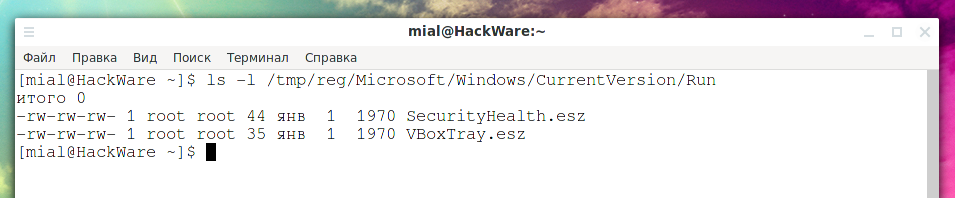
Let's say you want to see programs that automatically start when you turn on your computer.
ls -l /tmp/reg/Microsoft/Windows/CurrentVersion/Run
Output example:
You want to see what these values contain.
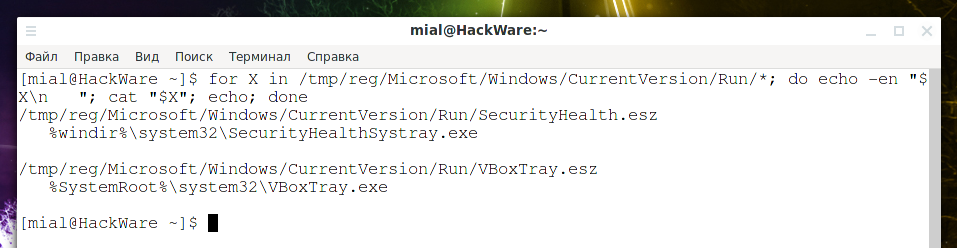
for X in /tmp/reg/Microsoft/Windows/CurrentVersion/Run/*; do echo -en "$X\n "; cat "$X"; echo; done
Output example:
libregf
libregf is similar to winregfs, that is, it mounts the Windows registry file to the file system. This allows you to navigate through the key hierarchy like regular folders, and the values can be edited like regular text files.
Installation on Kali Linux
sudo apt install libregf-utils
Installation in BlackArch
sudo pacman -S git autoconf automake libtool pkg-config git clone https://github.com/libyal/libregf cd libregf/ ./synclibs.sh ./autogen.sh ./configure make sudo make install
To mount the REGF file (Windows registry hive) /mnt/disk_d/Share/config/SOFTWARE to the /tmp/reg directory:
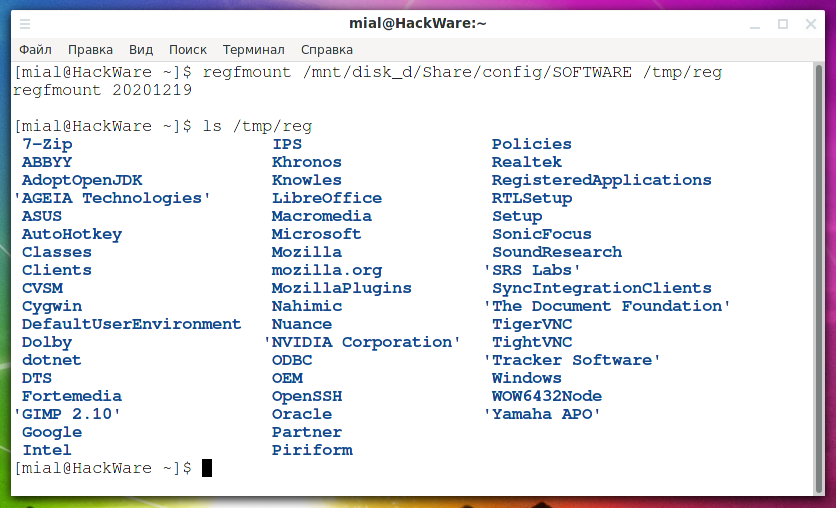
mkdir /tmp/reg regfmount /mnt/disk_d/Share/config/SOFTWARE /tmp/reg
This command will open directories and files containing the items contained in the REGF file.
Now you can see everything in this hive in the “/tmp/reg” directory:
ls /tmp/reg
Output example:
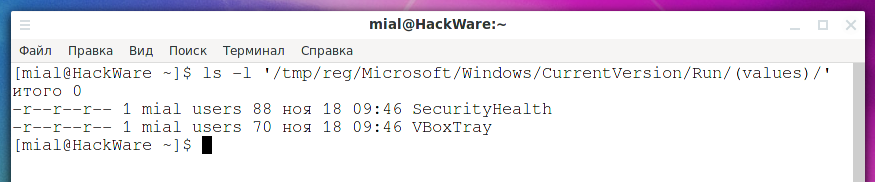
Let's say you want to see programs that automatically start when you turn on your computer.
ls -l '/tmp/reg/Microsoft/Windows/CurrentVersion/Run/(values)/'
Output example:
You want to see what these values contain.
for X in '/tmp/reg/Microsoft/Windows/CurrentVersion/Run/(values)/'*; do echo -en "$X\n "; cat "$X"; echo; done
Output example:
Related articles:
- How to open disks of virtual machines and download and upload files to them (SOLVED) (82.4%)
- How to extract all web site passwords stored in web bowser (54.4%)
- How to find out to which Wi-Fi networks a computer were connected to and stored Wi-Fi passwords (54.4%)
- How to find all passwords (web browsers, email programs, etc.) in Windows and Linux (50%)
- Indicators of Man-in-the-middle attacks (50%)
- VNC Security Audit (RANDOM - 4.4%)