Active Directory comprehensive guide, from installation and configuration to security auditing. Part 1: Introduction to Active Directory (concepts, usage, difference from Workgroup)
Table of contents
1. Introduction to Active Directory (concepts, usage, difference from Workgroup)
1.3 What is Active Directory for?
1.4 What can a network administrator do with Active Directory?
1.5 What you need for Active Directory
1.6 Active Directory Domain Services
1.8 Server Manager and Windows Admin Center
1.9 How workgroups differ from domains
1.10 Is my computer part of a domain?
2. Install Windows Server 2022 and Windows Server Core 2022
3. Windows Server 2022 and Windows Server Core 2022 configuration tools
4. Install Active Directory Domain Services in Windows Server 2022
5. Join computers to Active Directory. Check and unjoin from Active Directory
6. Active Directory configuration tools and snap-ins
7. Understanding the AD infrastructure
8. Group Policies
9. Managing Users, Computers, Groups and Organizational Units in Active Directory
10. Setting up trust and site domains
11. Other services and roles of Active Directory
12. Configuring Samba (Active Directory for Linux)
13. Active Directory security auditing tools
What is Active Directory
Active Directory is a Microsoft technology that is a distributed database that stores objects in a hierarchical, structured, and secure format. AD objects typically represent users, computers, peripherals, and network services. Each object is uniquely identified by its name and attributes. Domain, forest, and tree are logical divisions of the AD infrastructure.
Windows domains are commonly used on large networks — corporate networks, school networks, and government networks. They are not something you will run into at home if you don't have a laptop provided by your employer or school.
A typical home computer is a separate entity. You manage settings and user accounts on your computer. The domain-joined computer is different – these settings are managed by the domain controller.
What is a domain?
Windows domains provide network administrators with the ability to manage and control large numbers of computers from one location. One or more servers, known as domain controllers, control the domain and the computers on it.
Domains usually consist of computers on the same local network. However, computers joined to a domain can continue to communicate with their domain controller over a VPN or Internet connection. This allows businesses and educational institutions to remotely manage the laptops they provide to their employees and students.
When a computer is joined to a domain, it does not use its own local user accounts. User accounts and passwords are set on the domain controller. When you log into this domain, the computer authenticates your account name and password with the domain controller. This means that you can log in with the same username and password on any computer that is joined to the domain.
Network administrators can change Group Policy settings on a domain controller. Each computer in the domain will receive these settings from the domain controller, and they will override any local settings specified by users on their computers. All settings are controlled from one place. It also “blocks” computers. You probably won't be allowed to change many of the system settings on a domain-joined computer.
In other words, when a computer is part of a domain, the organization providing that computer controls and configures it remotely. They control the PC, not whoever uses it.
Because domains are not intended for home users, only a Windows Professional or Enterprise computer can be joined to a domain. Devices running Windows RT also cannot join domains.
What is Active Directory for?
If your office uses Active Directory, all machines will be joined to a domain, which means that all information is stored in a centralized location and not locally on the hard drives of individual computers. The domain is managed by a global catalog that keeps track of all devices registered on the network. The global directory stores IP addresses, computer names, and users, so the global administrator can control everything that happens in the domain. To manage computers, the administrator just needs the name of this computer, because everything is already connected to the server side.
When you use Active Directory, all permissions are set by the domain controller. This means that the network administrator has already told the domain controller what permissions to assign to each user. This makes all digital communication more efficient.
What can a network administrator do with Active Directory?
Not everyone in your organization necessarily needs access to all files/documents related to your company. With Active Directory, you can grant individual users permission to access any files/drives connected to the network so that all parties involved can use resources as needed. In addition, you can specify even more precise permissions. To illustrate this, let's look at an example: suppose your company has a directory on the web for all HR-related documents. This can include any forms that employees need to submit to HR (formal inquiries, formal complaints, and so on). Let's also assume that there is a table in the directory that indicates when employees will be on vacation and away from the office. Your network administrator can grant all users read-only access to this directory, which means they can view documents and even print them, but they cannot make any changes or delete documents. The administrator can then grant extended permissions to your HR manager/director or any other HR employee who needs to edit the files stored in the directory.
Another huge benefit for network administrators using Active Directory is that they can perform network-wide updates at the same time. With all of your machines autonomous and operating independently of each other, your network administrators will have to go from machine to machine every time an update needs to be performed. Without Active Directory, they would have to hope that all employees would update their machines on their own.
AD allows you to centralize the management of users and computers, and centralize access to and use of resources.
You also get the ability to use Group Policy when you have AD configured. Group Policy is a set of OU-related objects that define settings for users and/or computers in those OUs. For example, if you want to prevent the Start menu from showing the Shut Down option for 500 lab PCs, you can do so with a single setting in Group Policy. Instead of spending hours or days manually setting the correct registry entries, you create a GPO once, associate it with the correct OU (organizational units) or multiple OUs, and you never have to think about it again. There are hundreds of GPOs that can be configured, and the flexibility of Group Policy is one of the main reasons for Microsoft's dominance in the enterprise market.
What you need for Active Directory
Active Directory can be enabled on Windows Server computers. On non-server computers (for example, with Windows 10), you can install and enable Active Directory Lightweight Directory Services. They provide a Lightweight Directory Access Protocol (LDAP) server. It runs as a Windows service and provides a directory for authenticating users on the network. It is a lightweight alternative to a full-fledged Active Directory server that will only be useful in certain business networks.
Active Directory Domain Services
When people say “Active Directory” they usually mean “Active Directory Domain Services” (AD DS). It is important to note that there are other Active Directory roles/products such as Certificate Services, Federation Services, Lightweight Directory Services, Rights Management Services, and so on.
Active Directory Domain Services is a Microsoft Directory Server. It provides authentication and authorization mechanisms, and a framework in which other related services (AD Certificate Services, AD Federated Services, and so on) can be deployed. It is an LDAP-compliant database containing objects. The most commonly used objects are users, computers, and groups. These objects can be organized into organizational units (OUs) according to any number of logical or business needs. Group Policy Objects (GPOs) can then be linked to organizational units to centralize settings for different users or computers in an organization.
Domain controller
The server that hosts AD DS is the Domain Controller (DC).
Server Manager and Windows Admin Center
All this can be controlled through various programs. The older option is the Server Manager. It allows you to install Active Directory Domain Services (AD DS) and assign the computer the Domain Controller (DC) role.
The new PC management software is Windows Admin Center. This software is lightweight from a technical point of view (works in web browsers), but more functional in terms of features. Microsoft is actively promoting Windows Admin Center as an application that includes and surpasses the functionality of Server Manager by offering many additional features and user-friendly interfaces for managing and monitoring computers.
In fact, Windows Admin Center is not a complete replacement for Server Manager or any other snap-in. This software greatly facilitates many popular computer and server administration tasks, but some highly specialized settings require different software.
We'll cover working with Active Directory in each of these applications. We'll also look at deploying and managing Active Directory in PowerShell.
Server Manager is already preinstalled on Windows Server 2022 and automatically opens when you turn on your computer. To install Windows Admin Center, go to https://aka.ms/WindowsAdminCenter. More detailed instructions on installing and using Windows Admin Center will be provided in the third part of this article series.
How workgroups differ from domains
Workgroup is Microsoft's term for Windows computers connected through a peer-to-peer network. Workgroups are another organizational unit for Windows computers on a network. Workgroups allow these machines to share files, Internet access, printers, and other resources over the network. Peer-to-peer networking eliminates the need for a server for authentication.
Every Windows computer that is not joined to a domain is part of a workgroup. A workgroup is a group of computers on the same local network. Unlike a domain, no computer in a workgroup controls other computers — they are all united on an equal footing. A password is also not required for a workgroup.
Workgroups were used to share home files and printers in previous versions of Windows. Now you can use homegroup to easily share files and printers between home PCs. Workgroups are now back in the background so you don't have to worry about them – just leave the default workgroup name “WORKGROUP”.
There are several differences between domains and workgroups:
- Domains, unlike workgroups, can host computers from different local networks.
- Domains can be used to host many more computers than workgroups. Domains can include thousands of computers, in contrast to workgroups, which usually have an upper limit close to 20.
- Domains have at least one server — this is the computer that is used to manage permissions and security features for each computer in the domain. Workgroups do not have a server, and all computers are equal.
- Domain users generally require SIDs such as logins and passwords, as opposed to workgroups.
Is my computer part of a domain?
If you have a home computer, it is almost certainly not part of a domain. You can set up a domain controller at home, but there is no reason to do so unless you really need it for something. If you use your computer at work or school, chances are your computer is part of a domain. If you have a laptop that is lent to you at work or school, it can also be part of a domain.
You can quickly check if your computer is part of a domain. Open open the “Settings” app (Win+i) and click “System”.
Go to the “About” tab and find the item “Rename this PC (advanced)”:
If you see “Domain:” followed by the domain name, your computer is joined to a domain.
If you see "Workgroup" followed by the workgroup name, your computer is joined to a workgroup, not a domain.
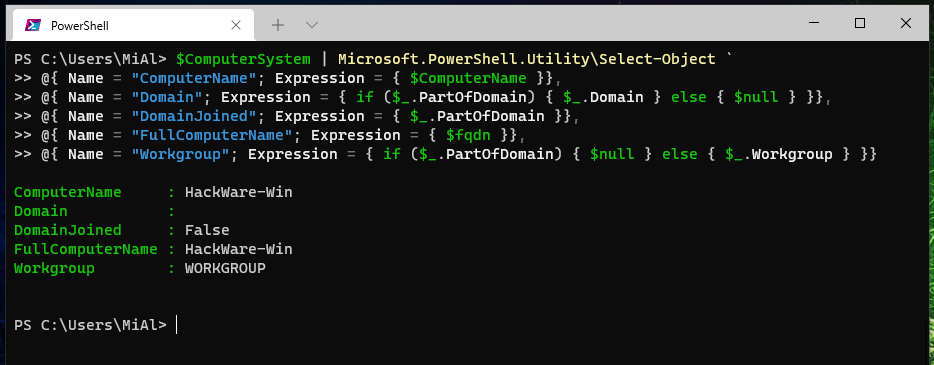
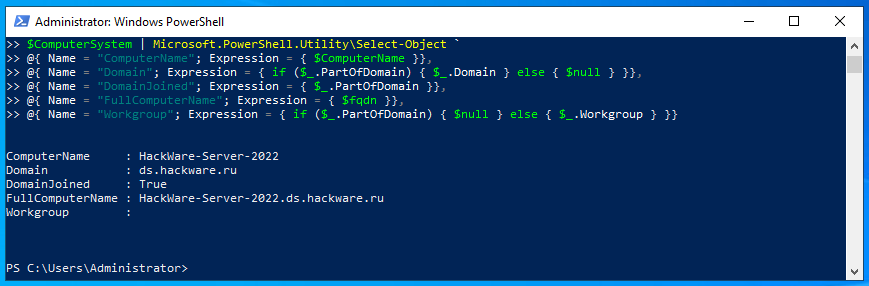
Using the command line (PowerShell) you can also find out if a computer is joined to a domain or a member of a workgroup.
To do this, run the command (you can copy-paste everything into the terminal window at a time):
$ComputerSystem = Get-CimInstance -Class Win32_ComputerSystem;
$ComputerName = $ComputerSystem.DNSHostName
if ($ComputerName -eq $null) {
$ComputerName = $ComputerSystem.Name
}
$fqdn = ([System.Net.Dns]::GetHostByName($ComputerName)).HostName
$ComputerSystem | Microsoft.PowerShell.Utility\Select-Object `
@{ Name = "ComputerName"; Expression = { $ComputerName }},
@{ Name = "Domain"; Expression = { if ($_.PartOfDomain) { $_.Domain } else { $null } }},
@{ Name = "DomainJoined"; Expression = { $_.PartOfDomain }},
@{ Name = "FullComputerName"; Expression = { $fqdn }},
@{ Name = "Workgroup"; Expression = { if ($_.PartOfDomain) { $null } else { $_.Workgroup } }}
Related articles:
- Active Directory comprehensive guide, from installation and configuration to security auditing. Part 4: Install Active Directory Domain Services in Windows Server 2022 (97.9%)
- Active Directory comprehensive guide, from installation and configuration to security auditing. Part 3: Windows Server 2022 and Windows Server Core 2022 configuration tools (69.6%)
- Active Directory comprehensive guide, from installation and configuration to security auditing. Part 5: Join computers to Active Directory. Check and unjoin from Active Directory (69.6%)
- Active Directory comprehensive guide, from installation and configuration to security auditing. Part 6: Active Directory configuration tools and snap-ins (69.6%)
- Active Directory comprehensive guide, from installation and configuration to security auditing. Part 2: Install Windows Server 2022 and Windows Server Core 2022 (59.2%)
- Configuring and starting network services on Kali Linux (Apache, MySQL, SSH, PostgreSQL, NetworkManager and Bluetooth) (RANDOM - 50%)