Automatic search the database of hacked access points
The whole article is devoted to the 3WiFi database and its usage (‘3WiFi: open database of Wi-Fi Access Points passwords’) there I explain what and how to find in this database.
Quite often looking in the window of the program Airodump-ng, I think it would be great to check all visible access points by 3WiFi at once. After all, if the router (access point) has got into this database, then we can easily get the password, whatever complexity it was, no need to spend time with Brut-Force, WPS PINs, disclosing the names of hidden networks, etc. As a pleasant bonus, we often get the credentials from the admin page. Of course, you can use the online 3WiFi map, to do this, find your location on the map and see the list of available access points near you. But the method has a big disadvantage: not all access points have geographic coordinates, therefore you can miss some access points.
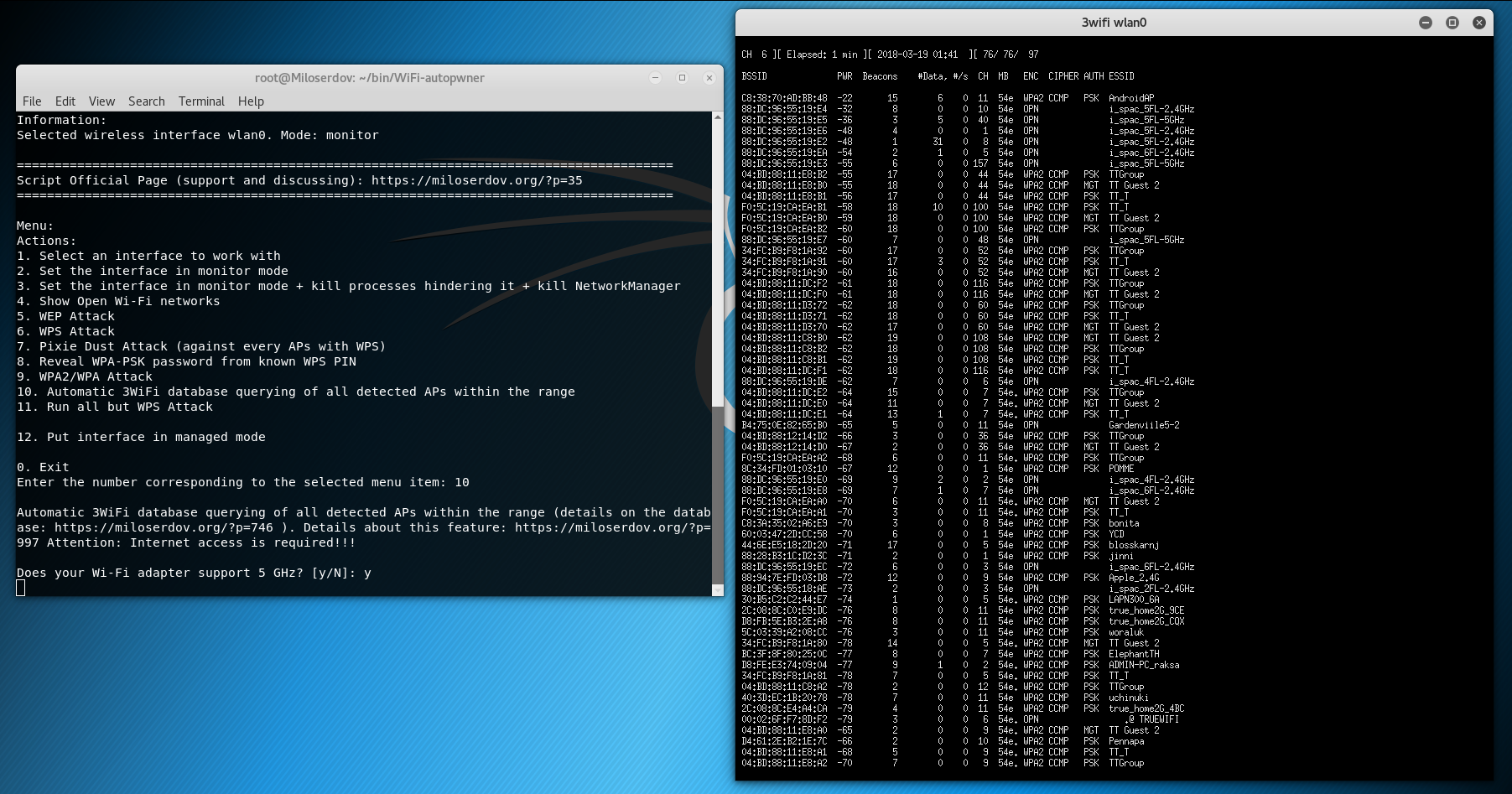
Using the 3WiFi API, I added a new feature in WiFi-autopwner ‘Automatic 3WiFi database querying of all detected APs within the range’, this is the tenth menu item. Since requests are made to the 3WiFi online base, then this function to work, you must have an Internet connection, otherwise it will not work.
After starting, the program will ask whether your wireless card supports 5 GHz? If it supports, and you want to scan 5 GHz channels, then enter the letter y, if it does not support or you do not want to scan these channels, then enter the letter n.
The Wi-Fi network search window opens:
When there is enough data collected, close it (double click on the X).
The search is performed in two ways:
- Search by MAC address (BSSID) of the network
- Search by network name (ESSID)
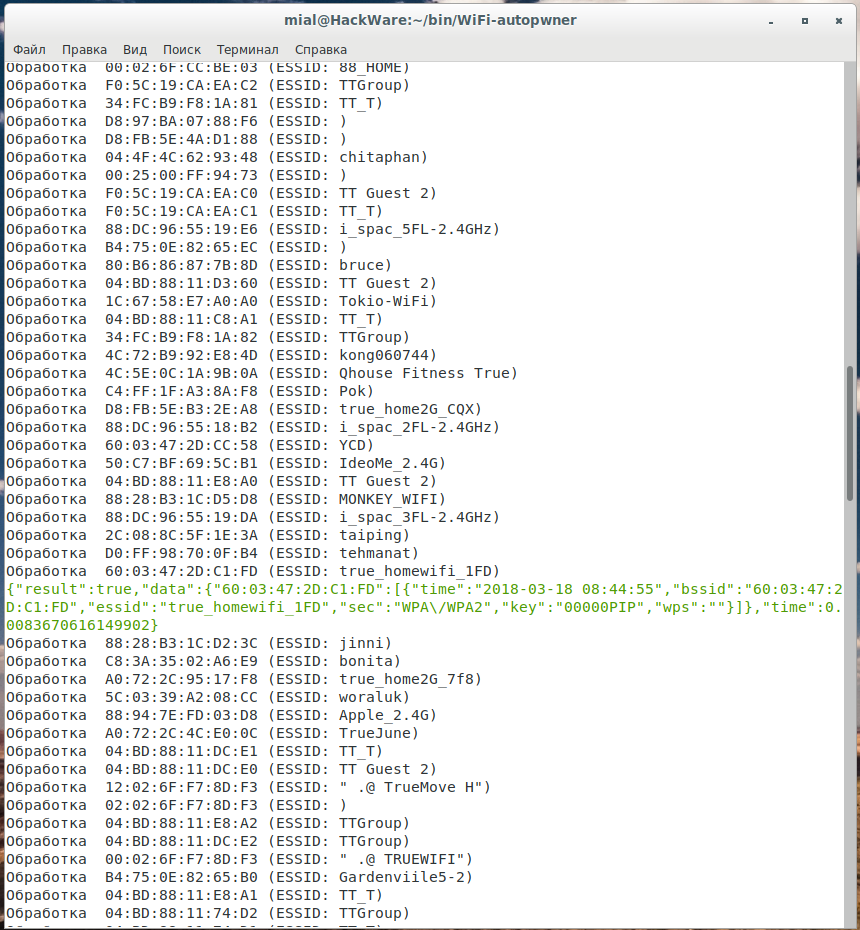
If a match was found for BSSID, then you can be sure, almost certainly this is the correct data. The information is displayed in approximately the following form:
Processing 60: 03: 47: 2D: C1: FD (ESSID: true_homewifi_1FD)
{"result": true, "data": {"60: 03: 47: 2D: C1: FD": [{"time": "2018-03-18 08:44:55", "bssid": " 60: 03: 47: 2D: C1: FD, essid: true_homewifi_1FD, sec: WPA / WPA2, key: 00000PIP, wps: "time": 0.0083670616149902}
The password follows the word key, in this example it is 00000PIP.
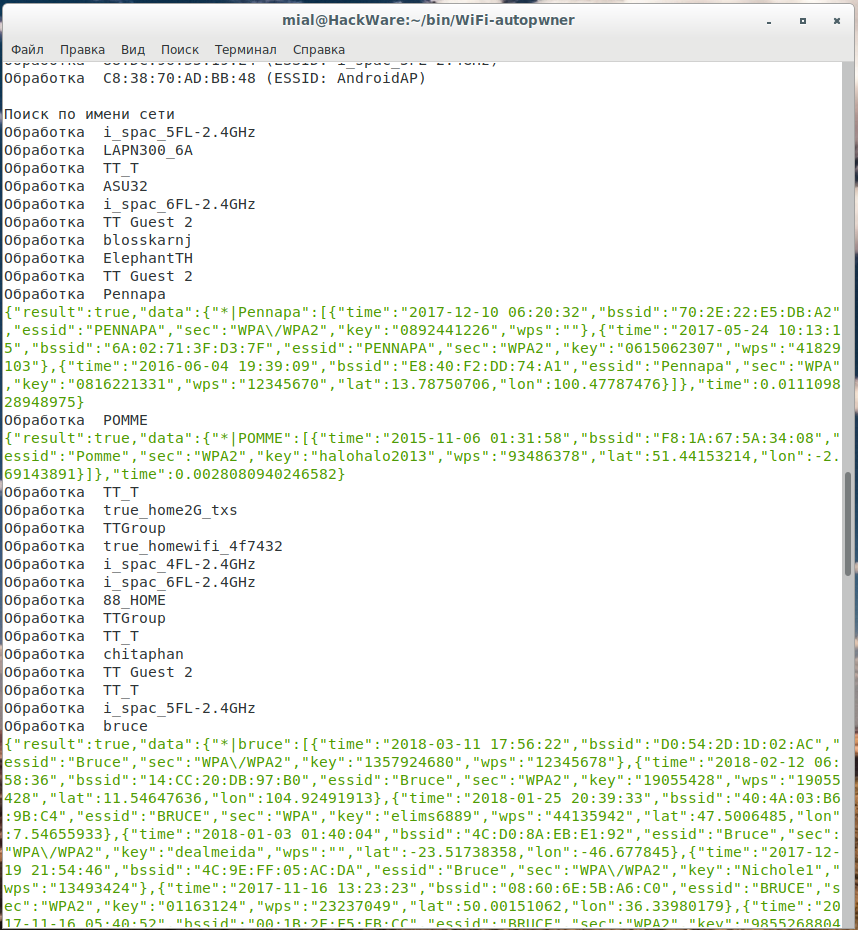
If a match is found for the access point name, an additional check is necessary, since false positives are likely, especially for popular names of Wi-Fi networks, for example, for my search, information is found for Pennapa, POMME, Bruce, etc. networks; it is likely that these are not the access points that are within my reach, since someone else, on the other end of the world could use the same names for their Wi-Fi networks.
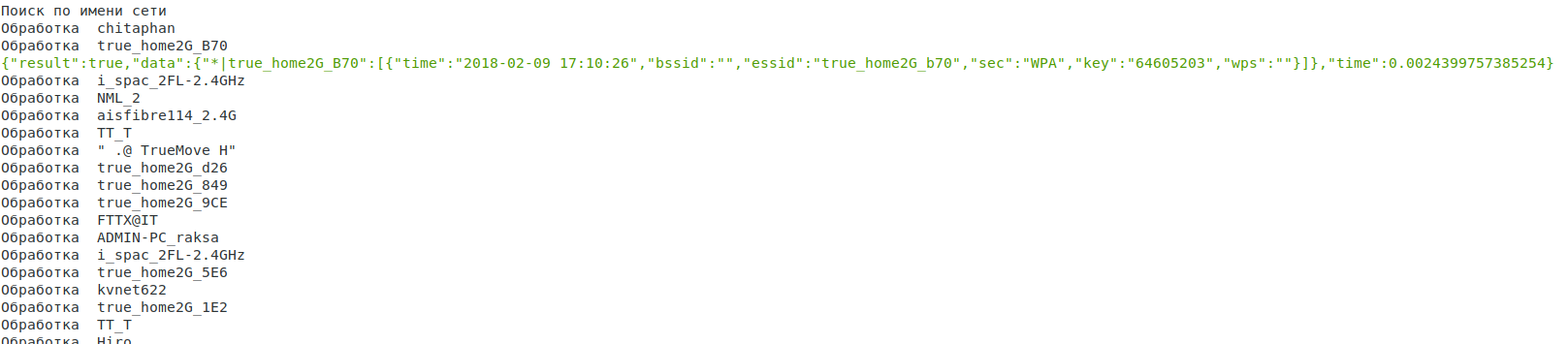
However, the result for an access point named true_home2G_B70 may very well be true:
Related articles:
- 3WiFi: open database of Wi-Fi Access Points passwords (76%)
- How to hack Wi-Fi in Windows (66.5%)
- How to hack Wi-Fi in 2022 (63.4%)
- WiFi-autopwner 2: user manual and overview of new features (61.8%)
- How to find out the exact model of a router (wireless access point) (51.6%)
- How to collect Location, Country or ISP IP Ranges (RANDOM - 27.5%)