Table of contents 1. What is a web server for Windows 2. Download web server (Apache, MySQL, PHP and phpMyAdmin) for Windows 11 3. Create the structure of the web server 4. Installing Apache 2.4 5. Installing and configuring MySQL 8.0 6. Installing and configuring PHP 8 7. Installing andRead More

How to install Windows 11 and Kali Linux on the same flash drive
Table of contents 1. Flash drive with Windows 11 and Kali Linux 2. Preparing a flash drive for installation 3. Using a flash drive as a raw VMDK virtual hard disk 4. Creating and configuring virtual machines 5. How to install when dual booting Windows and Linux 6. Installing Windows 11 7. Installing Kali Linux 8. How toRead More

An easy way to increase TX Power for Wi-Fi in Kali Linux and BlackArch
How to increase txpower to 36.00 dBm The article “How to increase TX-Power of Wi-Fi adapters in Kali Linux” discusses the theory and different approaches to increasing the TX Power to 30.00 dBm and removing restrictions on the use of blocked Wi-Fi channels. The article is quite long and someRead More

How to Install Drivers for Hashcat on Windows
How to Install Hashcat on Windows Hashcat is a password cracking program by brute force. Hashcat runs on Windows and Linux and is very functional. This program supports many algorithms for brute force and several types of attacks, including a dictionary attack and a mask attack. Hashcat is portable andRead More

How to recover USB drive/flash drive after flashing an ISO image or installing OS (SOLVED)
Experienced users can do various non-trivial things with USB media (disks and flash drives): install OS on them split a USB flash drive into several partitions burn a Live image and make a bootable USB flash drive destroy partition table All these actions are, on the one hand, reversible, but,Read More

Kali Linux post-installation tips and settings
Table of contents 1. How to install VirtualBox Guest OS Add-ons for Kali Linux 2. How to use Windows drives in Kali Linux. How to solve the problem with the error ‘The disk contains an unclean file system (0, 0). Metadata kept in Windows cache, refused to mount’ 3. RegularRead More
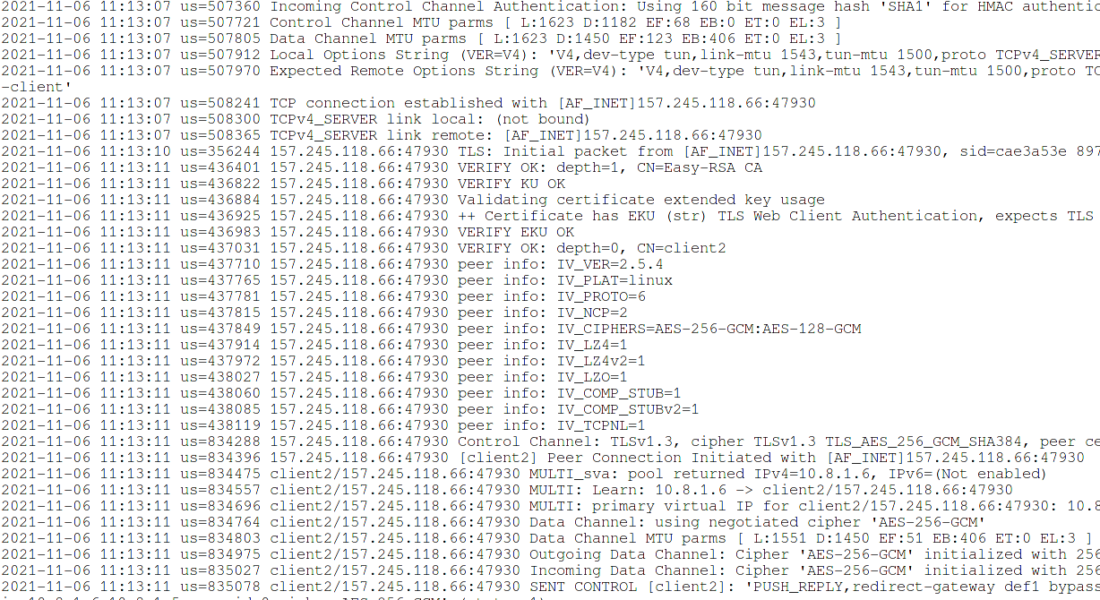
How to connect to OpenVPN via proxy or Tor
Table of contents 1. Specifics of connecting to an OpenVPN server through an HTTP proxy 1.1 Use TCP protocol 1.2 Using a proxy will affect network performance 1.3 Configuring Squid 2. How to check that the connection to OpenVPN is actually going through a proxy 2.1 Client and server logs 2.2 TrafficRead More

OpenVPN advanced usage examples
Table of contents 1. Script to automate the creation of OpenVPN configuration files 1.1 Re-running the OpenVPNassistent script 2. How to use .ovpn files with OpenVPN server and clients 3. How to connect to OpenVPN from Android 4. How to use OpenVPN to access network services on computers behind NAT (with private IP) 5. HowRead More

How to make Kali Linux 2022 Live USB with Persistence and optional encryption (on Windows)
Table of contents 1. Download Kali Linux 2021 (Live) 2. Write Kali Linux 2021 Live ISO to USB 3. Boot into Kali Linux Live from USB 4. How to create a persistence partition 5. Persistent storage with encryption 6. How to localize Kali Linux This page provides a complete guideRead More

How to install Kali Linux with full disk encryption or encrypted user’s home folder
Table of contents 1. Full disk encryption, partition encryption, encryption of individual directives and files 2. How disks and partitions are encrypted in Linux 3. Disk encryption password and user account password 4. How to install Kali Linux with full disk encryption 5. How to install Kali Linux with encrypted user's home folder 5.1Read More
