Windows on USB HDD In this manual, I will show a trick with which you can get a portable Windows on an external USB drive. This drive is not tied to a computer and should boot on any other laptop or desktop PC. The main thing that it should beRead More
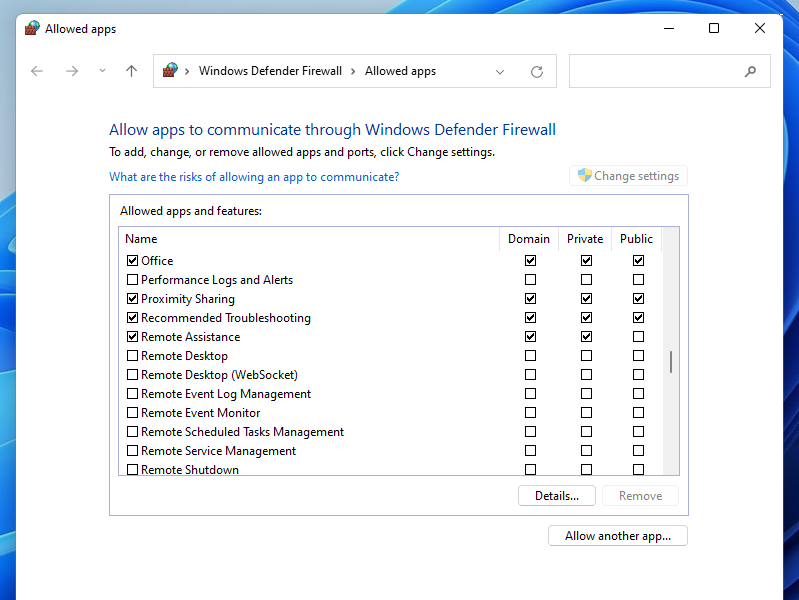
How to check open ports on my computer. What do 0.0.0.0, :*, [::], 127.0.0.1 mean. How to understand NETSTAT output
Why is it important to know which ports are open on the computer? An open port on your computer (unless a firewall is configured to deny incoming connections) means that ones can connect to your computer from outside. If your computer is infected with malware, such as a Trojan, aRead More
Active Directory comprehensive guide, from installation and configuration to security auditing. Part 7: Understanding the AD infrastructure
Table of contents 1. Introduction to Active Directory (concepts, usage, difference from Workgroup) 2. Install Windows Server 2022 and Windows Server Core 2022 3. Windows Server 2022 and Windows Server Core 2022 configuration tools 4. Install Active Directory Domain Services in Windows Server 2022 5. Join computers to Active Directory. Check and unjoinRead More

Active Directory comprehensive guide, from installation and configuration to security auditing. Part 6: Active Directory configuration tools and snap-ins
Table of contents 1. Introduction to Active Directory (concepts, usage, difference from Workgroup) 2. Install Windows Server 2022 and Windows Server Core 2022 3. Windows Server 2022 and Windows Server Core 2022 configuration tools 4. Install Active Directory Domain Services in Windows Server 2022 5. Join computers to Active Directory. Check and unjoinRead More

Analysis of a Linux virus written in Bash
Bash virus code In the article “How to find and remove malware from Linux”, we looked at typical examples of how a virus in Linux makes itself persistent (in order to persist and start after a reboot), and also collected examples of commands that will allow a system administrator toRead More
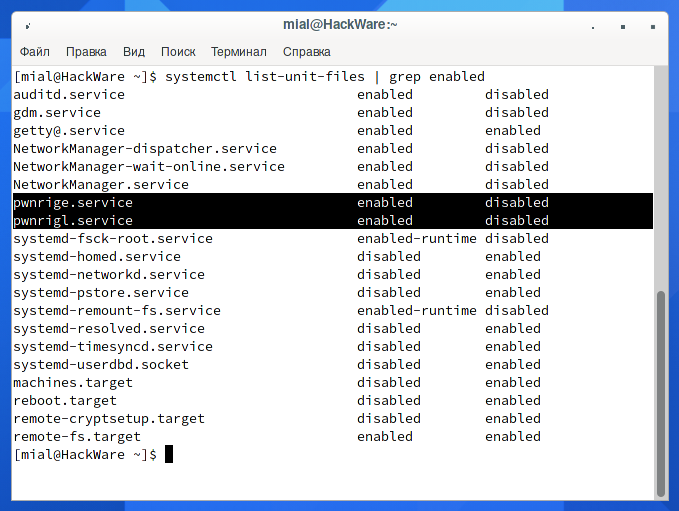
How to find and remove malware from Linux
The other day I had a chance to clean the Linux server from a Trojan and a Miner. The server is headless (only with a console, no web panels or graphical interfaces), antiviruses and malicious traffic analyzers are not installed. Nevertheless, even in such conditions, using standard Linux tools, youRead More
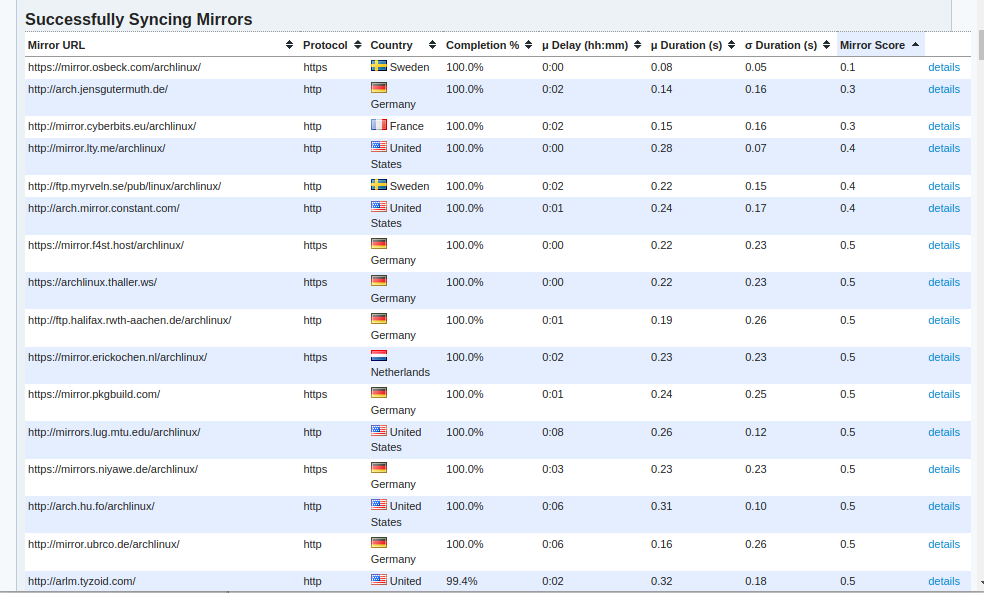
How to find the fastest Arch Linux and BlackArch mirrors
It is up to the user to choose the mirror of the package repositories on Arch Linux. It is up to the user to decide which mirror or list of mirrors will be used to install and update software packages. Arch Linux distributions do not provide by default tools toRead More
How to install driver for Wi-Fi Mediatek MT7921 and Mediatek MT7961 in Linux
See also: How to install Wi-Fi driver in Linux if the computer is offline This post will show you how to fix the problem with Mediatek MT7921 and Mediatek MT7961 Wi-Fi adapters not working, which you can find in the latest laptop models, such as ASUS ROG G15 and Asus TUFRead More
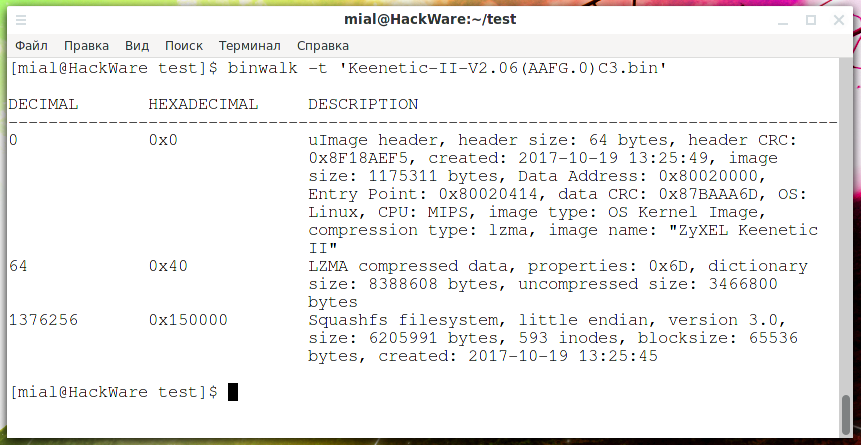
How to analyze and split compound files (firmware, multi partition disk images)
It is recommended to start with the first part entitled “How to find out the type of a file without an extension (in Windows and Linux)”. Files containers (compound files) Many files are concatenations of several files. For example, office document files .docx and .odt. You can replace the extensionRead More

How to find out the type of a file without an extension (in Windows and Linux)
If you came here from a search and you just need to quickly find out the file extension, then the web page “Online determining the file type without extension” is at your service: https://w-e-b.site/?act=file-type. Thanks to it, you do not need to install any programs, the online service will determineRead More
