How to check open ports on my computer. What do 0.0.0.0, :*, [::], 127.0.0.1 mean. How to understand NETSTAT output
Why is it important to know which ports are open on the computer?
An open port on your computer (unless a firewall is configured to deny incoming connections) means that ones can connect to your computer from outside.
If your computer is infected with malware, such as a Trojan, a backdoor (viruses that allow an attacker to connect to and control your computer remotely), then usually such a backdoor opens a port and listens on the network, waiting for an incoming connection. Although there may be options, for example, many backdoors connect to the attacker's computer and wait for commands – in this case, it would be more correct to speak not about an open port, but about an established connection. This is a common behavior for malware, since it does not require the victim to have a white IP (which is rare for home computers). Therefore, it is important to check open ports and established network connections. Of course, an established connection means an open port, but from a technical point of view, these are still different things.
Another example when you need to determine which service is listening on a port: you are trying to install a network service (Apache web server or MySQL DBMS), and they do not start, because some other service has already occupied their port, which they are using by default. In this case, you need to find this service and disable it or configure it to work with a different port.
But, as in many IT tasks (and indeed in many professional areas), getting data is only the very beginning. The main thing is to interpret and understand them correctly.
Therefore, in this article, we will look at how to find out which ports are open, how to check which service is listening on a specific port, and also learn how to correctly understand the output of the NETSTAT command and the like.
How to check open ports on Windows
Windows has a netstat command that displays protocol statistics and current TCP/IP network connections.
Usage:
NETSTAT [-a] [-b] [-e] [-f] [-i] [-n] [-o] [-p proto] [-r] [-s] [-t] [-x] [-y] [interval]
Netstat options:
-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or
listening port. In some cases well-known executables host
multiple independent components, and in these cases the
sequence of components involved in creating the connection
or listening port is displayed. In this case the executable
name is in [] at the bottom, on top is the component it called,
and so forth until TCP/IP was reached. Note that this option
can be time-consuming and will fail unless you have sufficient
permissions.
-e Displays Ethernet statistics. This may be combined with the -s
option.
-f Displays Fully Qualified Domain Names (FQDN) for foreign
addresses.
-i Displays the time spent by a TCP connection in its current state.
-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
-p proto Shows connections for the protocol specified by proto; proto
may be any of: TCP, UDP, TCPv6, or UDPv6. If used with the -s
option to display per-protocol statistics, proto may be any of:
IP, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, or UDPv6.
-q Displays all connections, listening ports, and bound
nonlistening TCP ports. Bound nonlistening ports may or may not
be associated with an active connection.
-r Displays the routing table.
-s Displays per-protocol statistics. By default, statistics are
shown for IP, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, and UDPv6;
the -p option may be used to specify a subset of the default.
-t Displays the current connection offload state.
-x Displays NetworkDirect connections, listeners, and shared
endpoints.
-y Displays the TCP connection template for all connections.
Cannot be combined with the other options.
interval Redisplays selected statistics, pausing interval seconds
between each display. Press CTRL+C to stop redisplaying
statistics. If omitted, netstat will print the current
configuration information once.
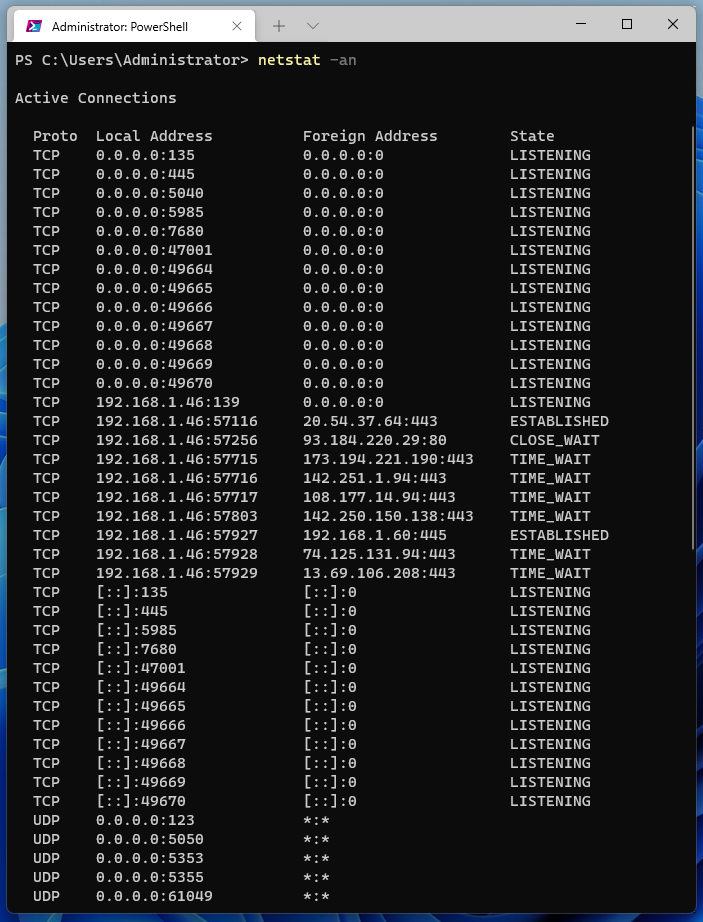
Using the command with the following keys, you can view information about all connections and listening ports in Windows:
netstat -an
How to use PowerShell to check open ports on Windows
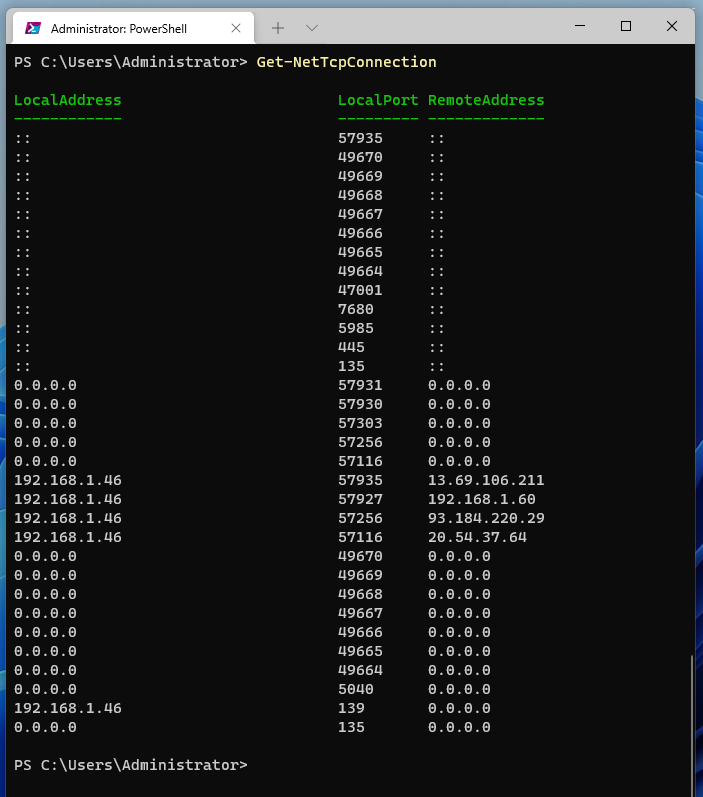
Get-NetTCPConnection is the PowerShell equivalent of NETSTAT, running the command without options returns the same result as netstat (but only for TCP ports and connections!).
Get-NetTcpConnection
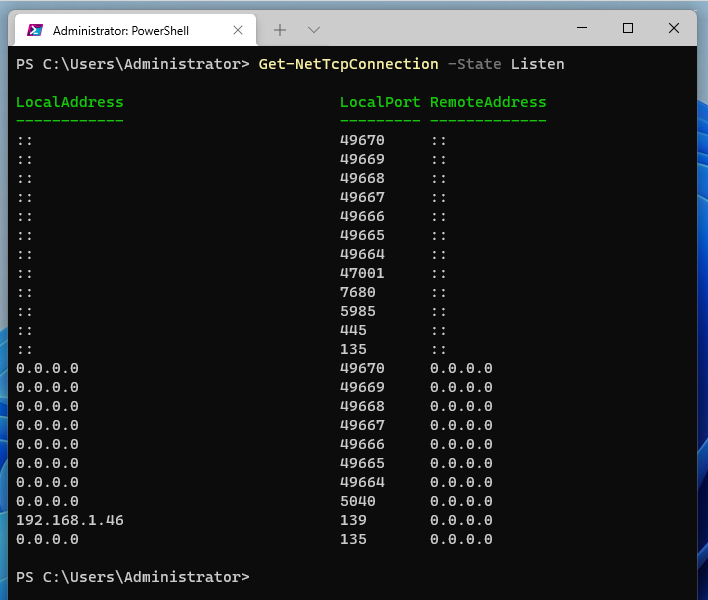
To list open ports, use the -State option with the Listen value:
Get-NetTcpConnection -State Listen
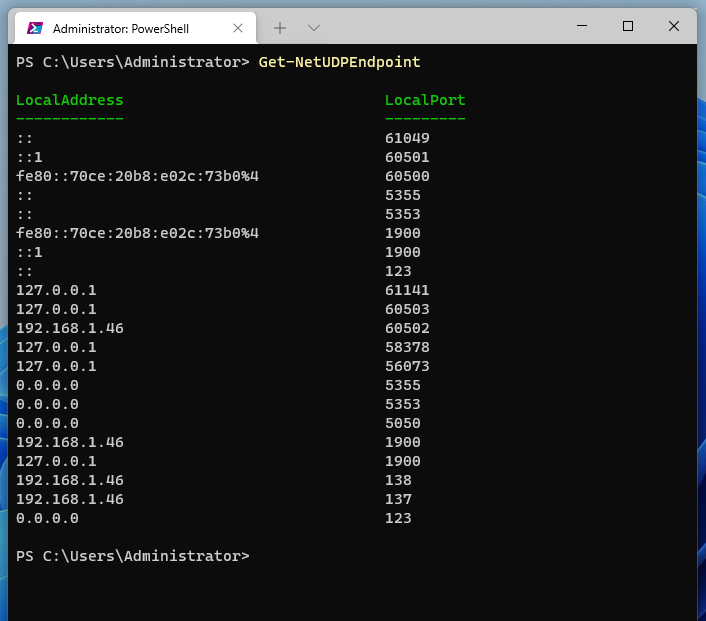
The Get-NetUDPEndpoint cmdlet gets the current statistics for the UDP endpoint. The cmdlet returns UDP endpoint properties such as local and remote UDP ports. If you do not provide any parameters, the cmdlet retrieves statistics for all UDP endpoints. Get-NetUDPEndpoint launched without options will return the local address and local port.
Get-NetUDPEndpoint
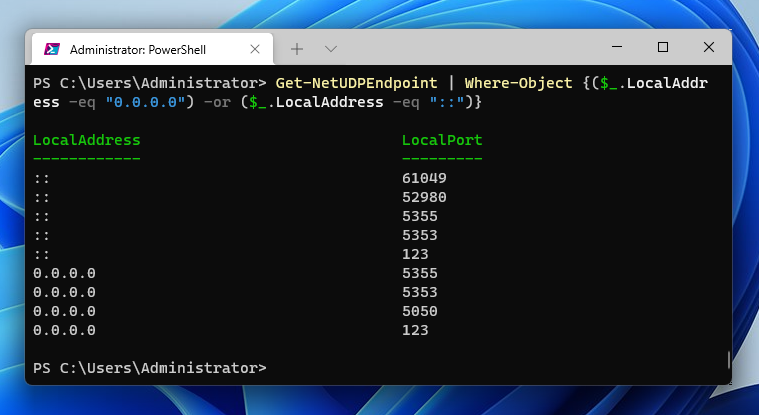
And the following command will show open UDP ports on all network interfaces:
Get-NetUDPEndpoint | Where-Object {($_.LocalAddress -eq "0.0.0.0") -or ($_.LocalAddress -eq "::")}
How to find out which program is listening on a port on Windows (using PowerShell)
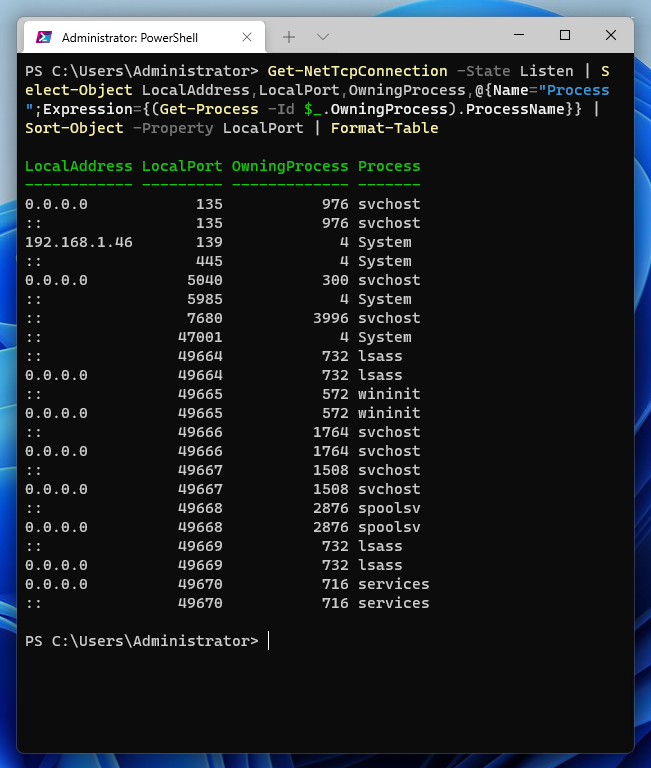
This example will get the name of the process associated with each open port:
Get-NetTcpConnection -State Listen | Select-Object LocalAddress,LocalPort,OwningProcess,@{Name="Process";Expression={(Get-Process -Id $_.OwningProcess).ProcessName}} | Sort-Object -Property LocalPort | Format-Table
This command will show all processes associated with any network activity (open ports, as well as established connections and other statuses):
Get-NetTcpConnection | Select-Object LocalAddress,LocalPort,OwningProcess,@{Name="Process";Expression={(Get-Process -Id $_.OwningProcess).ProcessName}} | Sort-Object -Property LocalPort | Format-Table
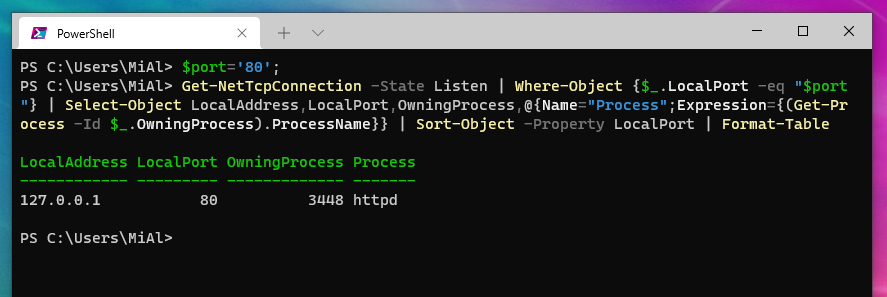
To find out which program is listening on a particular port, use the following set of commands:
$port='80';
Get-NetTcpConnection -State Listen | Where-Object {$_.LocalPort -eq "$port"} | Select-Object LocalAddress,LocalPort,OwningProcess,@{Name="Process";Expression={(Get-Process -Id $_.OwningProcess).ProcessName}} | Sort-Object -Property LocalPort | Format-Table
Replace “80” in the first line with the port you are interested in.
To view the process ID of the owner of the UDP port in use, run the command:
Get-NetUDPEndpoint | Select-Object LocalAddress,LocalPort,OwningProcess | Sort-Object -Property LocalPort | Format-Table
Use the following command to display the name of the process that opened the UDP port:
Get-NetUDPEndpoint | Select-Object LocalAddress,LocalPort,OwningProcess,@{Name="Process";Expression={(Get-Process -Id $_.OwningProcess).ProcessName}} | Sort-Object -Property LocalPort | Format-Table
How to find out on Windows which program is listening on a port (using CMD)
There can be a lot of ports open for listening, and they are usually used by legitimate programs. Therefore, when analyzing the received data, it is also important to know which service is listening on a particular port.
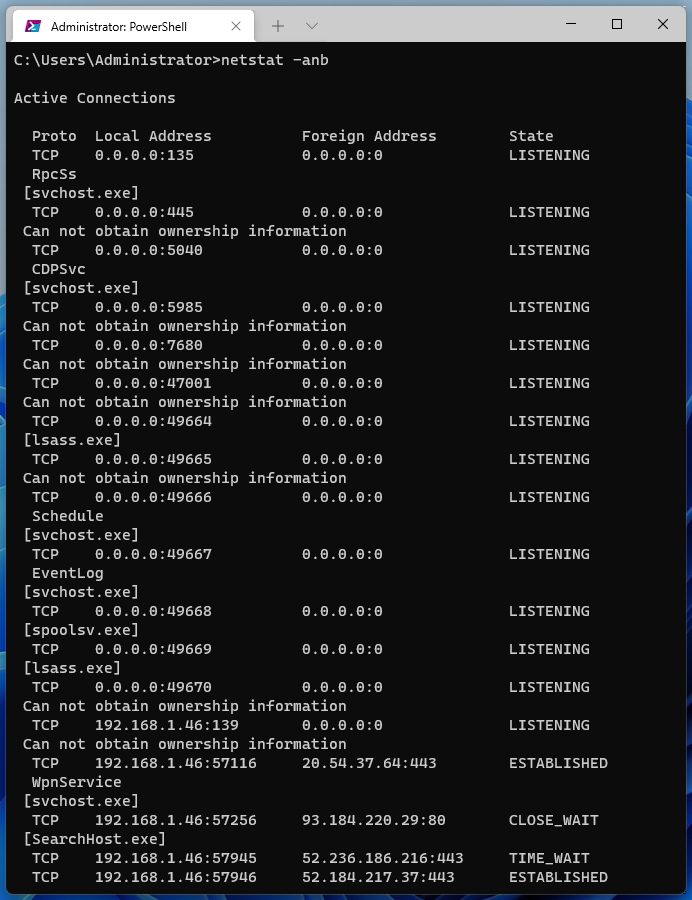
To search for a service, you can add the -b option to the NETSTAT command, which means to show the executable file listening on the port:
netstat -anb
There is also an alternative way to define the port bound executable. For it, open Windows Command Prompt. To do this, press the key combination Win+x, there select Windows PowerShell (Admin). In the window that opens, enter:
cmd
to switch to Windows Console Host.
There, run a command like:
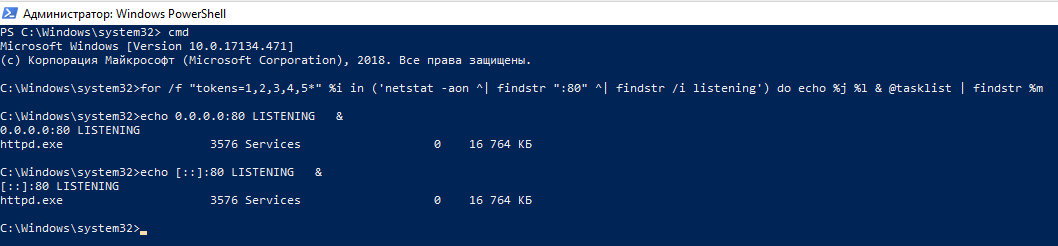
for /f "tokens=1,2,3,4,5*" %i in ('netstat -aon ^| findstr ":80" ^| findstr /i listening') do echo %j %l & @tasklist | findstr %m
This command will find services listening on port 80. To find information about another port, replace the number 80 in the command with the port you are interested in.
An example of the output in my case:
C:\Windows\system32>echo 0.0.0.0:80 LISTENING & 0.0.0.0:80 LISTENING httpd.exe 3576 Services 0 16 764 КБ C:\Windows\system32>echo [::]:80 LISTENING & [::]:80 LISTENING httpd.exe 3576 Services 0 16 764 КБ
0.0.0.0:80 means that the httpd.exe service (Apache web server) listens on port 80 for any IPv4 addresses. And the record [::]:80 means that the same service httpd.exe (Apache web server) listens on port 80 for any IPv6 addresses. We'll come back to more detailed data analysis later in this article.
Changing the port in a long command is not always convenient, so I recommend creating a text file named port.bat, copy to this file:
@ECHO OFF
for /f "tokens=1,2,3,4,5*" %%i in ('netstat -aon ^| findstr ":%1" ^| findstr /i listening') do echo %%j %%l & @tasklist | findstr %%m
Save and close this file.
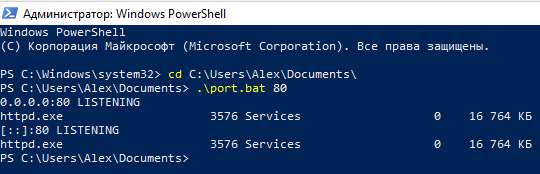
Now in Windows PowerShell or the Windows Command Prompt, use the cd command to navigate to the folder where you saved the file. For example, I saved it to the C:\Users\Alex\Documents\ folder, then to go there I run:
cd C:\Users\Alex\Documents\
Now run the file with a command like:
.\port.bat PORT
Where PORT replace with the port you are interested in, for example, I am interested in port 80, then:
.\port.bat 80
I get the same result again.
How to check open ports in Linux. How to find out which service is listening on a port
For Linux, there is also a netstat command, but it seems to be now considered obsolete and the ss command is recommended to replace it. The information displayed for ss and netstat is very similar. Even the basic options are identical.
So, to display the open ports of TCP and UDP protocols along with showing the processes that are listening to them, use the command:
sudo ss -tulpn
To list the established connections for TCP and UDP ports, use the command:
sudo ss -tupn
What does netstat and ss output mean
Next, we will learn to understand what exactly netstat outputs. But for a complete understanding, we need to study a little theory – very briefly. I will only tell you what we really need.
TCP and UDP
TCP and UDP are transport layer protocols. The most important thing you need to know about them is that any of them can be used to convey information.
By the way, you almost certainly heard about the TCP protocol, at least you should have come across the TCP/IP entry – this bunch of protocols is very important for the Internet. IP is responsible for where to send data, while TCP is responsible for transferring data and checking its integrity.
The work of the TCP protocol can be thought of as creating a connection between two computers, data is transmitted over this connection. Inside this connection, the data is checked for corruption – if some part is damaged, then it is sent again.
The UDP protocol also transmits data, but instead of creating a stable connection, within which the data is checked for integrity, it only sends a data packet to a specific address, and it does not verify whether the packet was delivered without damage or was delivered at all. In fact, this is the main difference between these protocols.
LISTENING, ESTABLISHED, CLOSE_WAIT and other states
As you can see in the output of the netstat command, different states are available for TCP.
The most popular of them is LISTENING, which means that an application running on this computer is listening on the port, that it is ready to accept a connection, for example, from another computer or from another service running on the same computer. The terms “open port”, "bind" are also used.
ESTABLISHED means an already established connection. An example of such a connection: the web browser has initialized the loading of the site page and while data is being transmitted over this connection, this connection has the ESTABLISHED status.
There are other types of states, but they are not very important for our purposes. By and large, we are only interested in LISTENING, since this means open ports on our computer and the ability to connect to it. The ESTABLISHED state is also important to us, since it means that data is already being transferred over the network connection.
UDP and LISTENING
It has already been said about UDP just above that this protocol does not create connections in the sense that TCP does. So there are no connection states for this protocol – it just doesn't apply to it. For this reason, LISTENING is never written in the State column for it. But does this mean that the UDP port cannot be listened to? No! The UDP port can also be listened to and available for connections. This port can also be used by viruses and intruders, so these ports are also subject to investigation.
An example of analyzing open ports
I'll start by analyzing open ports on Linux. Just because it's easier for me, and then we will gradually move on to explore the open ports on Windows.
An example of information about open ports received by the command:
sudo ss -tulpn
An example of listening ports on Linux:
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 10.0.2.15%enp0s3:68 0.0.0.0:* users:(("NetworkManager",pid=318,fd=17))
udp UNCONN 0 0 127.0.0.1:5300 0.0.0.0:* users:(("tor",pid=359,fd=7))
tcp LISTEN 0 128 127.0.0.1:9040 0.0.0.0:* users:(("tor",pid=359,fd=8))
tcp LISTEN 0 128 127.0.0.1:8118 0.0.0.0:* users:(("privoxy",pid=362,fd=3))
tcp LISTEN 0 128 127.0.0.1:9050 0.0.0.0:* users:(("tor",pid=359,fd=6))
tcp LISTEN 0 128 127.0.0.1:9475 0.0.0.0:* users:(("httpd",pid=553,fd=5),("httpd",pid=552,fd=5),("httpd",pid=551,fd=5),("httpd",pid=550,fd=5),("httpd",pid=549,fd=5),("httpd",pid=360,fd=5))
tcp LISTEN 0 128 *:80 *:* users:(("httpd",pid=553,fd=4),("httpd",pid=552,fd=4),("httpd",pid=551,fd=4),("httpd",pid=550,fd=4),("httpd",pid=549,fd=4),("httpd",pid=360,fd=4))
tcp LISTEN 0 128 *:22 *:* users:(("systemd",pid=1,fd=55))
tcp LISTEN 0 128 *:443 *:* users:(("httpd",pid=553,fd=7),("httpd",pid=552,fd=7),("httpd",pid=551,fd=7),("httpd",pid=550,fd=7),("httpd",pid=549,fd=7),("httpd",pid=360,fd=7))
tcp LISTEN 0 80 *:3306 *:* users:(("mysqld",pid=427,fd=21))
The output contains the following fields:
- Netid – udp or tcp protocol
- State – the state, for TCP protocols it will be LISTEN (since we explicitly indicated in the options to show only listening ports), and for UDP protocols it will be UNCONN, that is, the state is unknown, but, in fact, these are also listening ports that allow you to connect from outside
- Recv-Q – Received date
- Send-Q – Sent date
- Local Address:Port - the local address and port to which the service is bound, that is, the IP address and port that are listening
- Local Address:Port – remote address and port to which the connection is made.
Let's consider what the record 127.0.0.1:9050 means: it says that port 9050 is being listened on. Moreover, it is listened only for the IP address 127.0.0.1. The address 127.0.0.1 refers to the so-called Loopback. A network interface with this address is called a loopback interface. Packets that are sent from a computer to this address arrive at the same computer (more precisely, they do not even go anywhere). Only a service running on the same computer can access this address. Hence the important implication: although port 9050 is listening, no one else can connect to it from any network. The same applies to addresses from the range ::1/128 – these are the same addresses, but for IPv6, IPv6 analogue of 127.0.0.1 is ::1 (you can also see it in the displayed information).
Related articles:
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 1)
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 2)
The local addresses
- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
- 127.0.0.0/8
can be connected only computers located in these same local networks can connect to such ports (if you do not configure routing in a special way or port forwarding).
To list listening ports and already established network connections, use the following command:
sudo ss -tupn
An asterisk (*) instead of an address or port
We can see entries like *:80 or even *:*
The asterisk here means any address or any port. For example, *:80 in the Local Address:Port column means that port 80 is listened at once on all network interfaces available on this system. That is, the service will respond to a request to port 80 wherever it comes from: from the local network, from the global network (if there is a direct connection and an interface with a white IP) or from a loopback address – it does not matter, the service will still accept this connection.
By the way, the service can listen on the port according to the following rules:
- a specific port can be listened to for one IP address
- a specific port can be listened to for any IP address
That is, the port must be specified in any case, so the entry *:80 is valid for Local address:Port column, but an entry of the form *:* will never appear in this column.
For Peer Address:Port , *:* means that connections from any IP, sent from any port, are accepted.
By the way, just for reference: if your computer connects to a website, the websites usually run on ports 80 and 443. Therefore, the web browser connects exactly to port 80 (or 443 if it is a secure HTTPS connection). But on your computer, a new connection opens on any one, but not on 80 and 443 ports – usually ports with numbers >30000 are used, for example, an outgoing connection may be open on your computer with port 42063 and it will be addressed to port 80 of a web server.
Listening ports for IPv4 and IPv6 addresses in Linux
In Linux, the netstat and ss programs have a feature of displaying information about listening ports when IPv4 and IPv6 addresses are listening at the same time – only information about the IPv6 address is displayed! Perhaps this is due to some deep peculiarities of the Linux kernel implementation, but in Windows, for example, there is a clear separation and if a service simultaneously listens on a port on IPv4 and IPv6 addresses, then information about this service is displayed twice – an example of this is at the beginning of this article, where we look for which service is listening on port 80 and in the information found, the httpd service is shown to us twice.
What 0.0.0.0 means in netstat. Different kinds of notation in netstat and ss
0.0.0.0 is the very first IP address. But it belongs to special-purpose IP (like 127.0.0.1) and performs different functions.
The designation 0.0.0.0 can have different meanings depending on where it is used. When talking about listening ports, this designation in Linux symbolizes a placeholder, that is, it means “any IP address”.
How does this differ from * (asterisks) or from the notation :::, which also appear in the output of the programs in question? In the ss program, IPv6 address 0:0:0:0:0:0:0:0 (which is analogous to IPv4 address 0.0.0.0) is denoted by an asterisk (*). Therefore, in ss, the entry 0.0.0.0:* means “any IPv4 address from any port”. And the designation *:* symbolizes “any IPv6 address from any port”.
The netstat program also uses 0.0.0.0:*, which also means “any IPv4 address from any port”.
But netstat uses :::* to mean “any IPv6 address from any port”.
Be aware of these differences to avoid confusion. And also remember that if it is shown that the tcp6 (IPv6) protocol is listening, then the port can also be listened to on tcp (IPv4) – there is no data in the output information in Linux!
In Windows, as the Local Address, when listening to any IP address on a specific port, an entry of the form 0.0.0.0:80 is used (in this example, any IP address available in the system is listened to on port 80). For IPv6 addresses, in this case, an entry of the form [::]:80 is used.
As an external address, when connections are available from any IP and from any port, for the TCP protocol it is written 0.0.0.0:0, and for the UDP protocol in the same conditions it is written *:*. Which is also not very logical and confusing. More precisely, this difference in designations stems from the difference between the TCP and UDP protocols.
If the information relates to IPv6, then for TCP when it means any address on any port, an entry of the form [::]:0 is used. And for UDP, the same notation is used for both IP and IPv6, that is, *:*
It should be remembered that some of these designations overlap with Linux notations, where they have their own meaning.
To make life a little easier, I made a table that can be used as a cheat sheet:
|
|
Specific local IPv4 address on a specific port |
Any local IPv4 address on a specific port |
Specific local IPv6 address on a specific port |
Any local IPv6 address on a specific port |
Any external IPv4 address on any port |
Any external IPv6 address on any port |
|---|---|---|---|---|---|---|
|
Netstat (Windows) |
127.0.0.1:9050 |
0.0.0.0:80 |
[2a02:f680:1:1100::3d5f]:80 |
[::]:443 |
TCP: 0.0.0.0:0 UDP: *:* |
TCP: [::]:0 UDP: *:* |
|
Netstat (Linux) |
2a02:f680:1:1100::3d:80 |
:::443 |
0.0.0.0:* |
:::* |
||
|
ss (Linux) |
[2a02:f680:1:1100::3d5f]:80 |
*:443 |
0.0.0.0:* |
*:* OR [::]:* |
IP address 0.0.0.0
By the way, the IP address 0.0.0.0 is quite interesting, as it is used in different cases.
For example, some services allow you to set 0.0.0.0 as the bind address. This means that the service will listen on the port on all network interfaces of this computer, that is, on all IP addresses. In some services (for example, the Apache web server), you simply do not need to specify any specific IP address (including 0.0.0.0) and by default they will listen for incoming connections on all network interfaces.
It is important to understand that 0.0.0.0 and 127.0.0.1 are completely different things. Although if you ping 0.0.0.0 in Linux, then pings will be sent to 127.0.0.1. In Windows, an attempt to ping 0.0.0.0 will cause a message about a data transfer failure, that is, an unavailable address. The address 0.0.0.0 means “any IP of this computer” and includes 127.0.0.1.
A 0.0.0.0 address usually means that an IP address has not yet been configured or assigned. This address specifies the host that is accessing DHCP to obtain an IP address.
If 0.0.0.0 is specified as a recipient address, then it should be treated as a broadcast address 255.255.255.255.
The address 0.0.0.0 with a mask of 0.0.0.0, that is, 0.0.0.0/0 is used to designate the default route.
This address is not a valid address to assign to a network interface, just like the entire subnet 0.0.0.0/8 (that is, any address starting with a 0.).
If you go to this address in Linux, for example, type the address http://0.0.0.0 in a web browser, then the page of the local web server will open (if it is installed and running). On Windows, such an address will raise an invalid address error.
Also, the address 0.0.0.0 can be used to explicitly indicate that the target host is not reachable.
This information is provided just for reference and to broaden our horizons, and now we continue with our open ports.
*.socket services
On Linux, instead of starting a service on a specific port, you can configure a socket to listen on a port. The scheme of work is as follows: the network service (for example, this can be configured for SSH) is not started by default and, therefore, does not consume system resources. However, its port is being listened to by a system process that would have been running anyway. As soon as a connection request is received on this port (for example, 22), the system process starts the required service, and it starts working as if it had always been enabled. After the connection is terminated, the service is shut down again, and the system process starts listening to the port again.
In this case, the service that will actually work with the incoming connection is not specified as the program that opened the port.
For example, for SSH, netstat will show something like the following (1/init instead of sshd):
Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp6 0 0 :::22
And ss will show something like this:
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
tcp LISTEN 0 128 *:22 *:* users:(("systemd",pid=1,fd=44))
What open ports you need to pay attention to
I mentioned that if a computer gets a malicious program that opens a connection to communicate with an attacker, then it will listen on one of the ports. In this case, for TCP, the connection state will be LISTENING or ESTABLISHED. The UDP protocol is “stateless”, so nothing is outputted for it, but you need to know that information can be exchanged through UDP in the same way.
It should be remembered that legitimate services that are open for access from outside can be attacked, for example, brute-force password or exploitation of vulnerabilities. As far as malware is concerned, it can use any ports. Therefore, there is no ready-made list of ports to look out for. Any port could be a sign of a security problem with your computer.
We need to check which files and services have opened the connection. If the executable file that opened the network connection is located in a dubious place, in folders where programs are usually not installed, then you need to pay special attention to this file.
Trojans and backdoors can act in two ways:
- open a port and wait for an attacker to connect;
- connect to the attacker's remote system.
In the second option, the connection status will NOT be LISTENING – the malware can only be found by a complete analysis of all connections.
Typically, services that only listen on the IP address 127.0.0.1, that is, listen on loopback interfaces, are designed to serve any legitimate programs running on your system.
How to block access to ports on a computer?
Use a firewall to configure port access.
Many antiviruses now have firewalls. Inbound settings control which services listening on the port are allowed to connect to. These rules will not take effect if any service initiates the connection itself – for such cases, rules for outbound connections are configured.
If some program other than the system one asks for access to the network, then you should understand why it needs it.
To open “Windows Defender Firewall”, run at a command prompt:
Firewall.cpl
To open “Windows Defender Firewall with Advanced Security”, at the command prompt, run:
WF.msc
To open “Allow apps communicate through Windows Defender Firewall” run:
explorer 'shell:::{4026492F-2F69-46B8-B9BF-5654FC07E423} -Microsoft.WindowsFirewall\pageConfigureApps'
Related articles:
- How to run PHP script without a web server (56.1%)
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 2) (54.7%)
- IP calculators (54.7%)
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 1) (53.9%)
- How to use zcat to concatenate compressed and plain text files (53.5%)
- Port scanner for Windows (RANDOM - 6.9%)