How to find out if a site is behind CloudFlare or not
How to utilize misconfigured DNS and old database records to find hidden IP's behind the CloudFlare network, said in articles:
- How to find out the real IP of a site in Cloudflare
- Database of hidden site's IP behind CloudFlare. Searching for sites belong to the same CloudFlare account
In this note, we will learn how to check whether a site is using CloudFlare or not?
Does a site use name servers of CloudFlare
One of the signs that the site stays behind CloudFlare is usage of the CloudFlare name servers, which look like *.ns.cloudflare.com
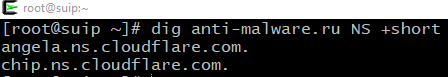
Name Servers of a site can be viewed with the dig command, running it as follows:
dig DOMAIN NS +short
Where the word DOMAIN should be replaced with a domain name, for example:
dig anti-malware.ru NS +short angela.ns.cloudflare.com. chip.ns.cloudflare.com.
Alternatively, you can use whois command with filtering out the excess information:
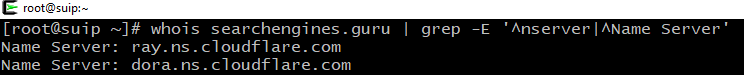
whois DOMAIN | grep -E '^nserver|^Name Server'
Example:
whois searchengines.guru | grep -E '^nserver|^Name Server' Name Server: ray.ns.cloudflare.com Name Server: dora.ns.cloudflare.com
Does a site use the CloudFlare IP?
The second, even more reliable way to find out whether a site is protected with CloudFlare is to check if the IP of the site of interest belongs to this organization.
IP of a site can be found as follows:
dig DOMAIN +short
Example:
dig searchengines.guru +short 104.20.122.18 104.20.123.18
One or more IP addresses can be displayed, use anyone for analysis.
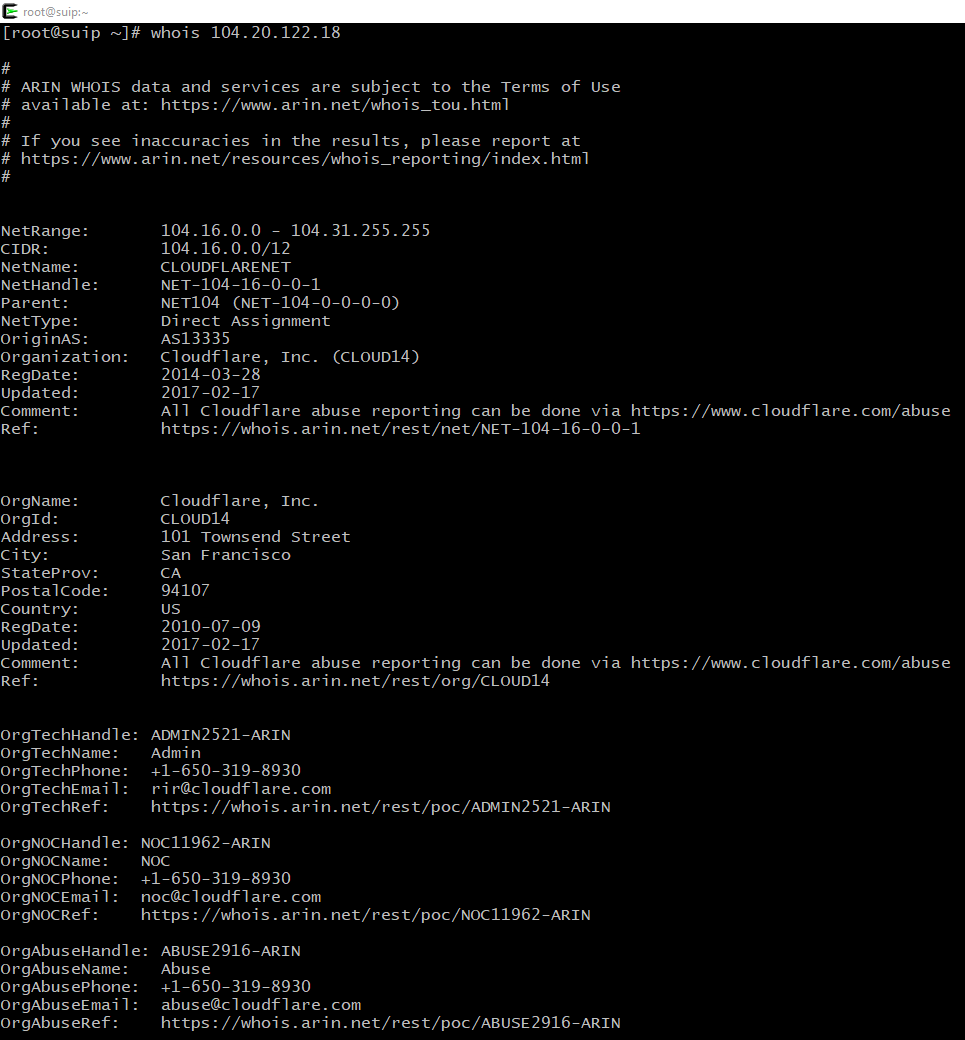
Check the received IP with the whois command like that:
whois IP_address
Example:
whois 104.20.122.18
If a ‘Cloudflare, Inc.’ string is present in the information received, then the target site uses the CloudFlare IP and, therefore, is protected by this network.
Online service to check if a site is using CloudFlare
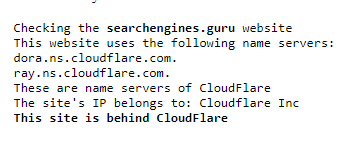
The described methods are automated in the online service, you just enter a domain name of a site and it will check its NS records and its IP for belonging to Cloudflare.
Instead of whois, the GeoLite2-ASN database is used, but it does not change the essence.
Output example of the service:
Related articles:
- Revealing the perimeter (CASE) (88.5%)
- How to find out the Autonomous system on the IP and how to find out all the Autonomous System IPs (83.4%)
- How to find out the real IP of a site in Cloudflare (69.2%)
- How to bypass Cloudflare, Incapsula, SUCURI and another WAF (69.2%)
- Utilities for information gathering, OSINT and network analysis in Windows and Linux (62.8%)
- How to obfuscate JavaScript code (RANDOM - 1.3%)