Revealing the perimeter (CASE)
Today we are picking a server that distributes unwanted software and is the cause of spam. Webmasters will immediately understand the phrase “downgrade traffic” – this is when, instead of linking to a file, you are prompted to download an executable (.exe) file, after which you get an additional half dozen shortcuts and other hard to clean garbage in you PC. Even when you try to download such a file, you are forced to agree to Push subscriptions (spam), and along the way advertise casinos, bookmakers and other prohibited to advertise activity.
Despite the abomination of such “affiliate programs”, in order not to go beyond the scope of the law, we restrict ourselves to collecting information and researching the perimeter. Nevertheless, in my opinion, it turned out to be a rather interesting case.
The most interesting thing is the disclosure of a real IP address for the seemingly absolutely impenetrable protection of CloudFlare. When I tried to determine the real IP address, there was a feeling that the administrator read all the articles about IP disclosure for CloudFlare and did everything right. Indeed, popular tools failed to reveal direct IP address.
How it all started
It all started with this comment:
At first I thought it was a targeted attack – a trojan that would steal passwords and stuff from my computer. I have already started to refresh Assembler and reverse engineering in my head, but VirusTotal has shown that this is banal Adware:
Website with malicious file
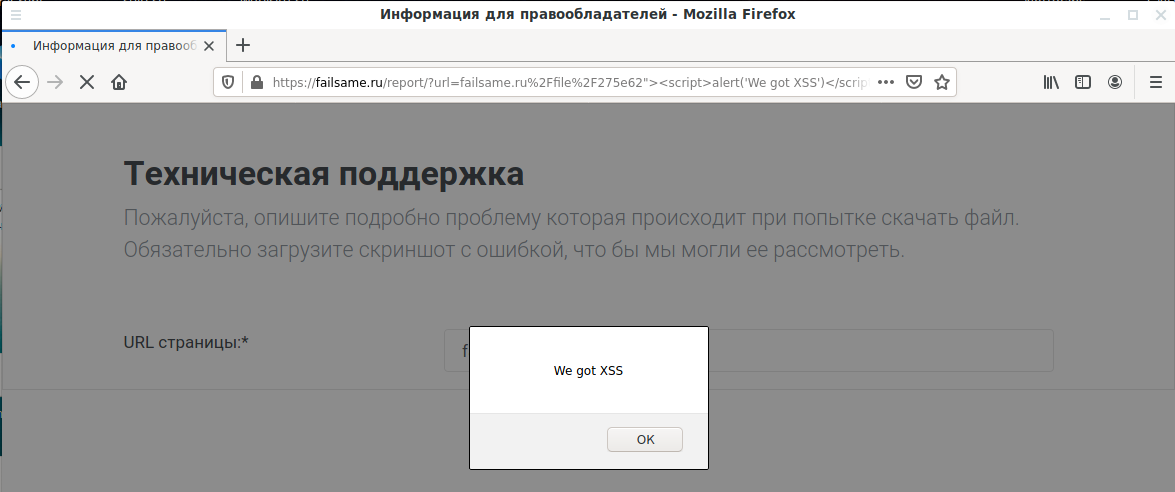
The site made a double impression – on the one hand, the XSS vulnerability was immediately found, that is, as if everything was done in a hurry and carelessly (https://failsame.ru/report/?url=failsame.ru%2Ffile%2F275e62%22%3E%3Cscript%3Ealert(%27We%20got%20XSS%27)%3C/script%3E):
But, on the other hand, two more domains were used to redirect for file download and a characteristic advertisement was shown – that is, not so simple.
By changing the parameter values, you can get different types of files (for example, the installation file for a mobile phone):
curl 'https://failsame.ru/?action=link_open' -d 'fid=47779&type=1' curl 'https://failsame.ru/?action=link_open' -d 'fid=47779&type=2' curl 'https://failsame.ru/?action=link_open' -d 'fid=47779&type=3'
Errors typical of SQL injection were not shown:
curl 'https://failsame.ru/?action=link_open' -d 'fid=47779"&type=3' curl 'https://failsame.ru/?action=link_open' -d "fid=47779'&type=3"
If you specify something other than 1, 2, or 3 as the value of type, then the server did not respond to such a request.
See also “How to analyze POST requests in web browsers”.
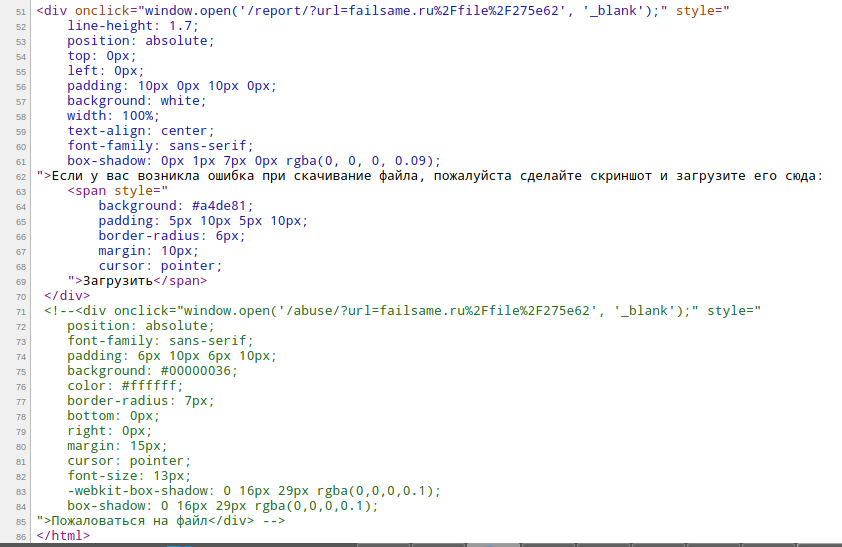
Analysis of the source code allowed us to find another input form: https://failsame.ru/abuse/?url=failsame.ru%2Ffile%2F275e62, as well as several JavaScript scripts.
Search for hidden files
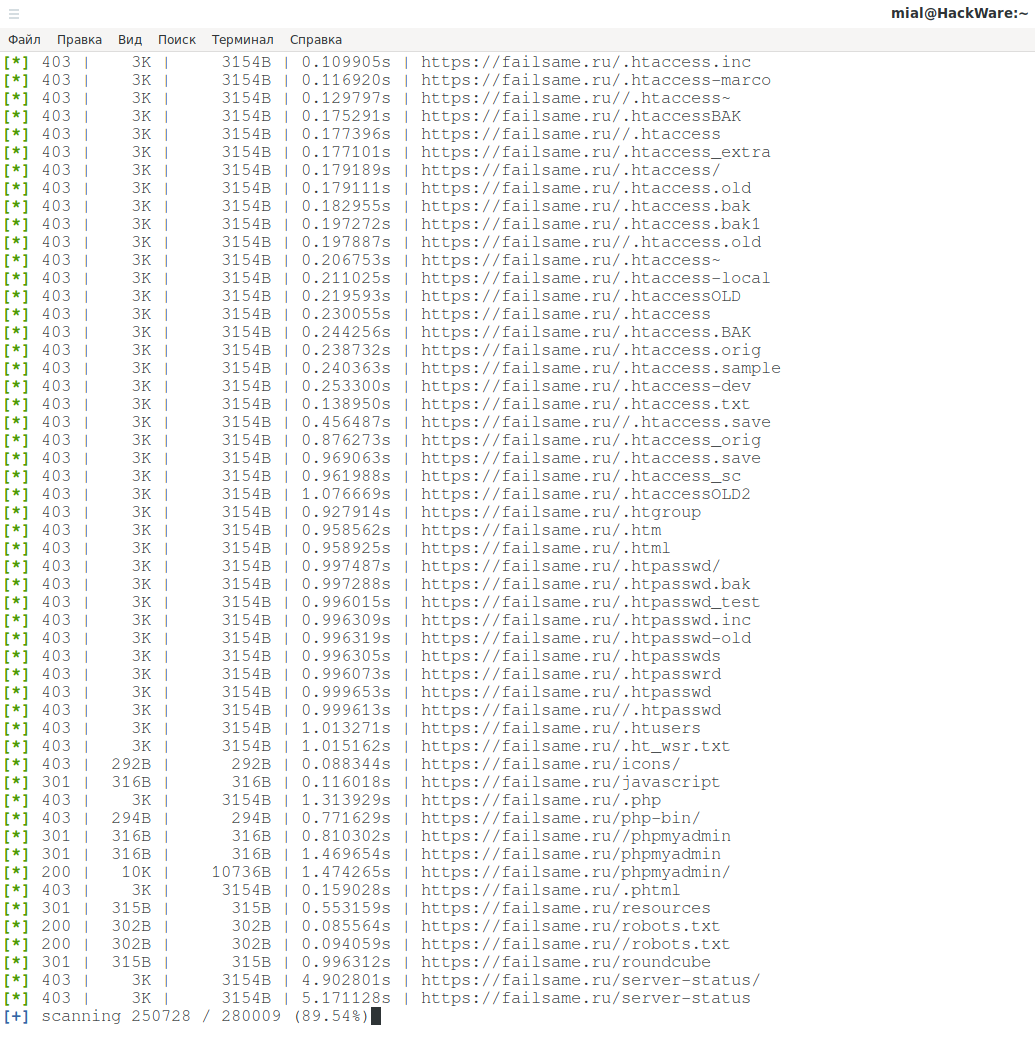
Along with the study of the site, launched lulzbuster to search for interesting files and folders on the site:
lulzbuster -s https://failsame.ru/ -w /usr/share/lulzbuster/lists/big.txt
Among the results were very interesting:
[*] 403 | 294B | 294B | 1.000149s | https://failsame.ru/cgi-bin/ [*] 200 | 691B | 691B | 0.997966s | https://failsame.ru/cgi-bin/awstats.pl [*] 403 | 294B | 294B | 0.771629s | https://failsame.ru/php-bin/ [*] 200 | 10K | 10736B | 1.474265s | https://failsame.ru/phpmyadmin/ [*] 200 | 302B | 302B | 0.085564s | https://failsame.ru/robots.txt [*] 301 | 315B | 315B | 0.996312s | https://failsame.ru/roundcube [*] 200 | 7B | 7B | 3.013992s | https://failsame.ru/test.php [*] 401 | 458B | 458B | 0.853156s | https://failsame.ru/webstat/
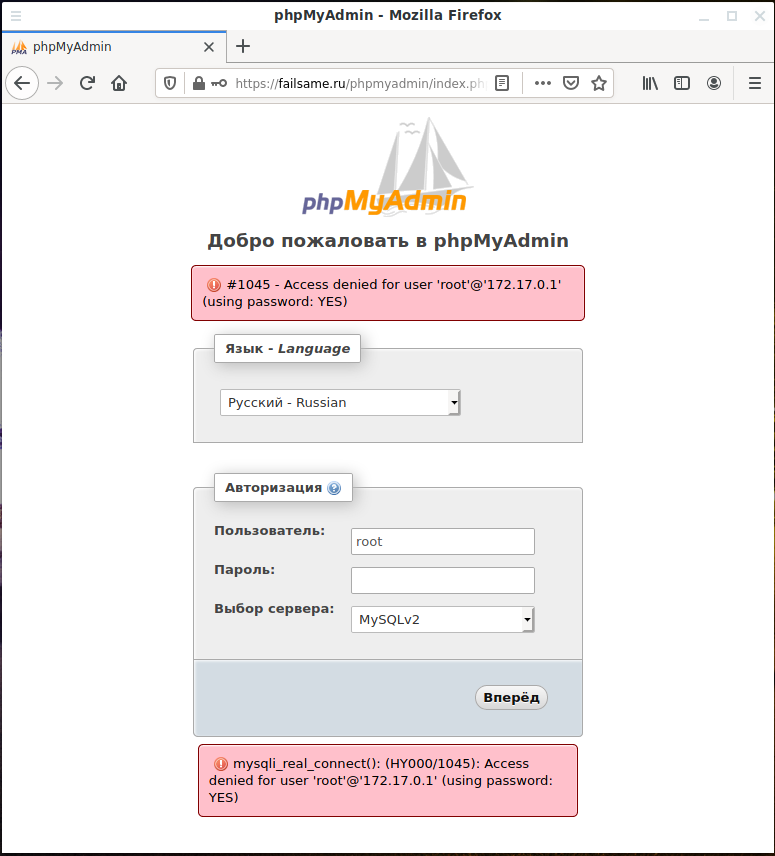
For example, phpmyadmin was discovered on the site:
Since I do not know the password and even the username, I received errors:
#1045 - Access denied for user 'root'@'172.17.0.1' (using password: YES) mysqli_real_connect(): (HY000/1045): Access denied for user 'root'@'172.17.0.1' (using password: YES)
It was not in vain that I made an attempt to log in – I got the IP address 172.17.0.1, however, at the moment there is no sense in it: it is a local IP. And quite typical for Docker. That is, even if I find the real IP address of the server, it is very likely that the MySQL service listens only on the local (or loopback) interface and is not accessible from the WAN.
By the way, let's move on to find a real IP of the site.
Finding a Direct IP Site behind CloudFlare
I took advantage of the whole arsenal described in the articles:
- How to find out if a site is behind CloudFlare or not
- How to bypass Cloudflare, Incapsula, SUCURI and another WAF
- How to find out the real IP of a site in Cloudflare
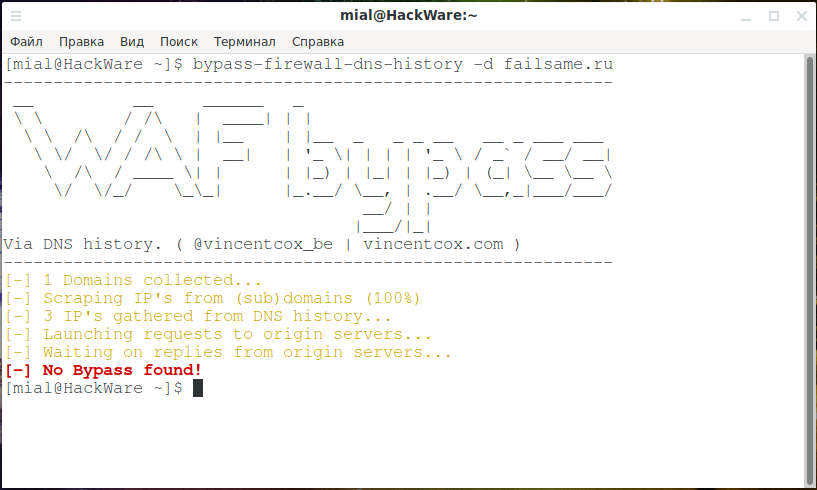
But neither Bypass firewalls by abusing DNS history:
bypass-firewall-dns-history -d failsame.ru
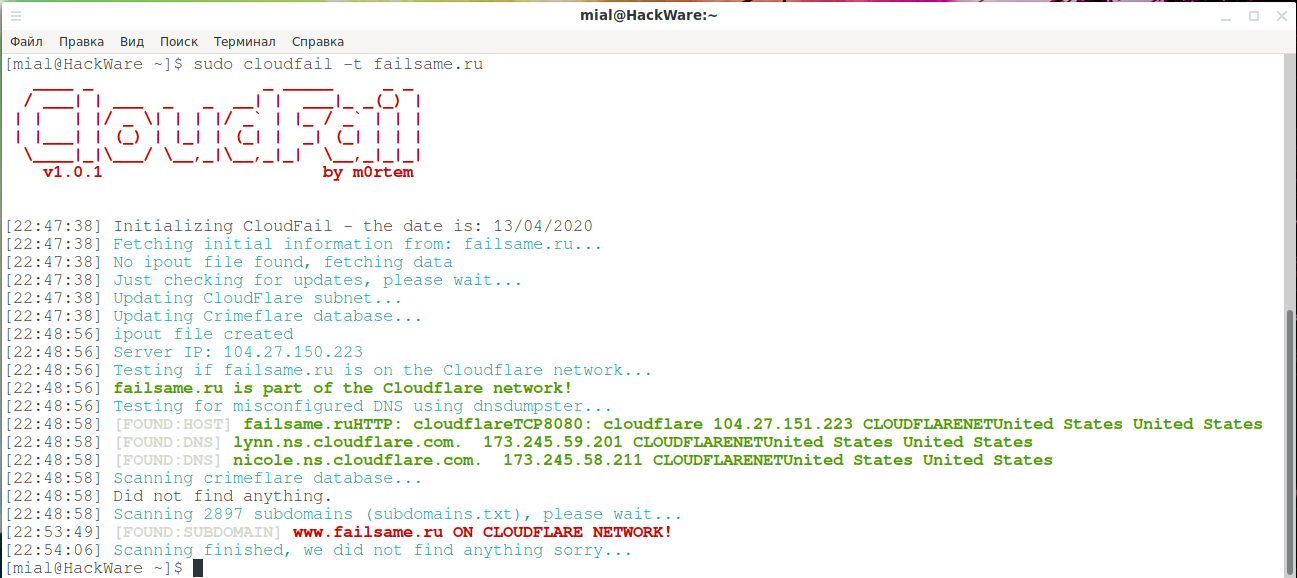
Not even CloudFail yielded results:
sudo cloudfail -t failsame.ru
Modus operandi: find the whole net of sites of the same type
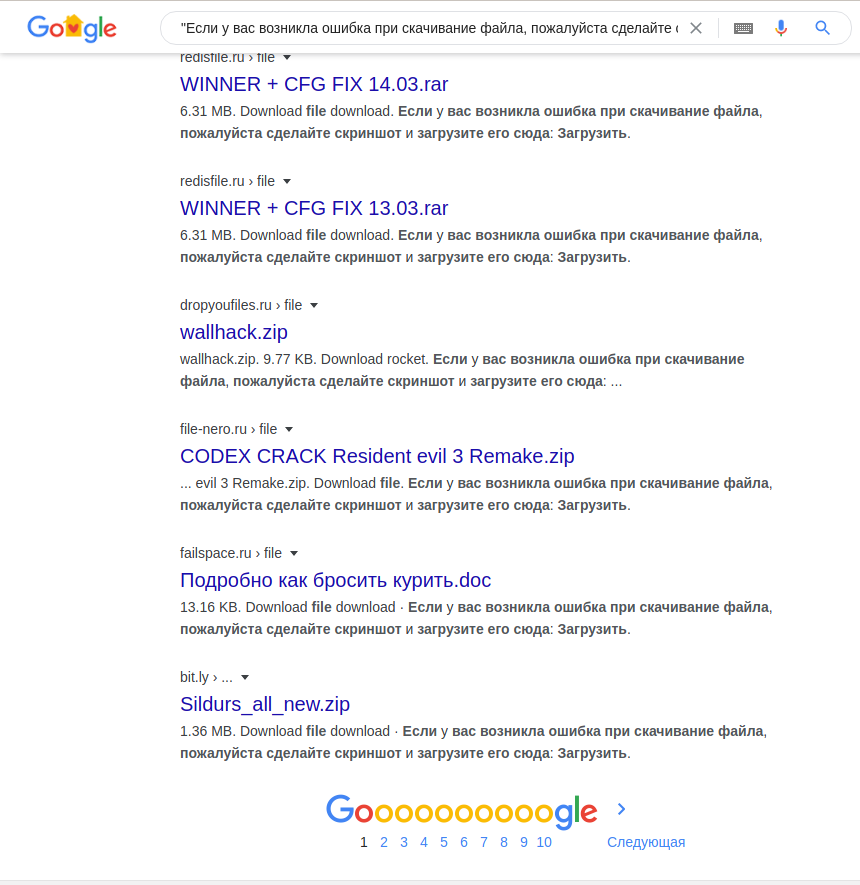
We recall about modus operandi – people usually act the same way. Therefore, we take the phrase from the site, put it in double quotes and look for it in Google (there is a spelling error, but you need to leave it as it is):
"Если у вас возникла ошибка при скачивание файла, пожалуйста сделайте скриншот и загрузите его сюда»
Immediately find the entire net of sites:
There are a lot of domains there, I selectively tried some of them, but none of them revealed the real IP address of the server.
Find the main site
I looked at the file https://failsame.ru/robots.txt (it was found using lulzbuster, but could be found using Nikto, or without any third-party programs – this is a typical file for each site).
And he saw there:
User-agent: * Disallow: /?page=login Disallow: /?page=registration Disallow: /search/ Disallow: /cart/ Disallow: */?s= Disallow: *sort= Disallow: *view= Disallow: *utm= Allow: /?page=login Allow: /?page=registration Crawl-Delay: 5 Sitemap: https://file-mix.com/sitemap.xml Host: https://file-mix.com
Let me remind you that this is the file for the failsame.ru domain, and the file-mix.com domain is mentioned in the robots.txt file. It turned out that this is the main site. And finally, everything fell into place:
- this is a file hosting service that instead of the source file produces an .exe file
- there you can register as a file distributor and try to earn something by posting spam. Or try to earn on referrals, telling stories, “how I earned 4000 yesterday”.
The analysis of this file also did not produce results, and I decided to do the trick with mail – the point is that the server sends us an email, for example, to confirm the email address, and we look at the IP address of the sending server. A confirmation email is not sent, but a password reset email has arrived.
Using email to reveal IP address behind CloudFlare
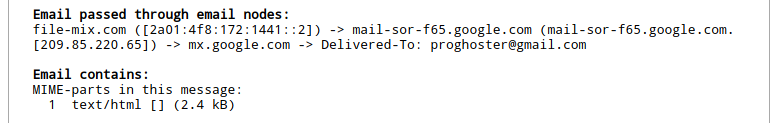
I took advantage of the help of the online service “Extracting all information from an e-mail letter” and received the following:
Email passed through email nodes: file-mix.com ([2a01:4f8:172:1441::2]) -> mail-sor-f65.google.com (mail-sor-f65.google.com. [209.85.220.65]) -> mx.google.com -> Delivered-To: proghoster@gmail.com Email contains: MIME-parts in this message: 1 text/html [] (2.4 kB)
The source is the domain file-mix.com, and its IP address is IPv6 address 2a01:4f8:172:1441::2.
The site does not have an IP address, but only IPv6?
If you have not seen it, then read the articles:
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 1)
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 2)
I’m checking whether the target site is working on IPv6 2a01:4f8:172:1441::2
curl [2a01:4f8:172:1441::2] -H 'Host: file-mix.com'
I got an error:
curl: (7) Couldn't connect to server
since my current ISP does not support IPv6.
I found a server with IPv6 and checked. Unfortunately, instead of the title page of the destination site, I saw the source code of the default page of the Apache HTTP web server on Debian.
That is, the site has some other IP or IPv6 address.
Do not forget to check the HTTPS protocol:
curl [2a01:4f8:172:1441::2]:443 -H 'Host: file-mix.com'
There is also “Apache2 Debian Default Page: It works”.
We try to scan open ports using Nmap:
sudo nmap -6 2a01:4f8:172:1441::2
Received:
setup_target: failed to determine route to 2a01:4f8:172:1441::2 WARNING: No targets were specified, so 0 hosts scanned.
And hell, I don’t have IPv6!!!
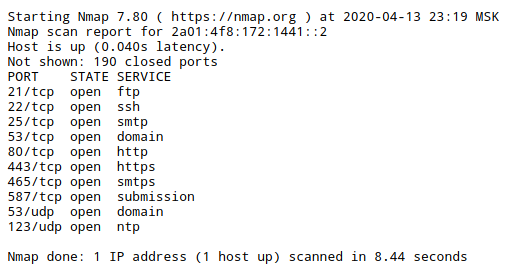
I used the online service “IPv6 addresses Port scaning”: https://w-e-b.site/?act=nmap-ipv6
Result:
PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 25/tcp open smtp 53/tcp open domain 80/tcp open http 443/tcp open https 465/tcp open smtps 587/tcp open submission 53/udp open domain 123/udp open ntp
The result gave rise to some optimism.
DNS queries to the server on IPv6
When a site hides behind CloudFlare, it uses CloudFlare name servers, which do not show the real IP of the site and do not allow ANY in DNS queries. For instance:
dig file-mix.com ANY
will return:
file-mix.com. 3788 IN HINFO "RFC8482" ""
Trying to find the IP address of the mail mail.* subdomain:
dig mail.file-mix.com
Also will not return anything useful:
file-mix.com. 1799 IN SOA lynn.ns.cloudflare.com. dns.cloudflare.com. 2032284449 10000 2400 604800 3600
We look at MX records:
dig file-mix.com MX
Result:
file-mix.com. 299 IN MX 10 emx.mail.ru.
We look at TXT records:
dig file-mix.com TXT
Result:
file-mix.com. 299 IN TXT "ca3-8a88c11989fb426eaa9c8d677381d258" file-mix.com. 299 IN TXT "v=spf1 redirect=_spf.mail.ru"
SOA record:
dig file-mix.com SOA
also did not give anything useful:
file-mix.com. 3599 IN SOA lynn.ns.cloudflare.com. dns.cloudflare.com. 2032284449 10000 2400 604800 3600
Once again we were convinced that CloudFlare hides the real DNS records. But we know the IPv6 address of the server, which has something to do with the target site. And on this server a DNS server is running. We will make a request to this DNS for the site we are interested in:
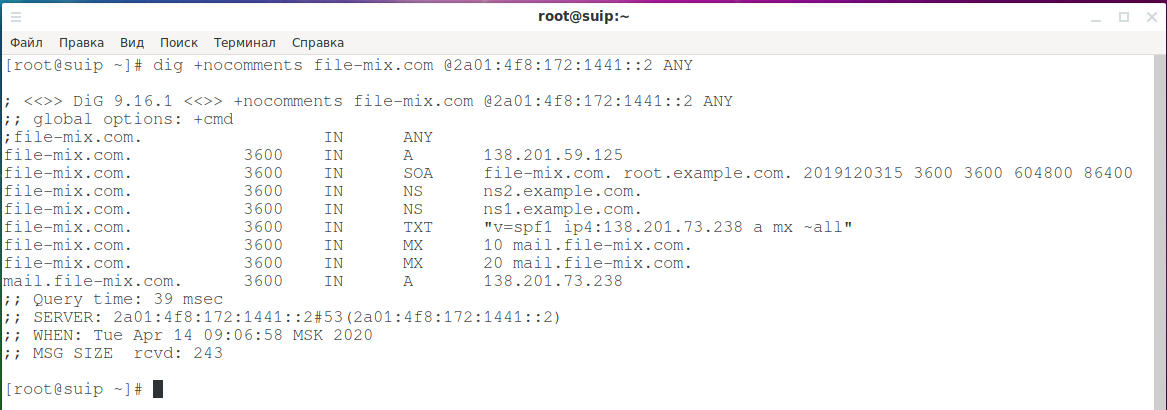
dig +nocomments file-mix.com @2a01:4f8:172:1441::2 ANY
And bingo, DNS server revealed everything:
; <<>> DiG 9.16.1 <<>> +nocomments file-mix.com @2a01:4f8:172:1441::2 ANY ;; global options: +cmd ;file-mix.com. IN ANY file-mix.com. 3600 IN A 138.201.59.125 file-mix.com. 3600 IN SOA file-mix.com. root.example.com. 2019120315 3600 3600 604800 86400 file-mix.com. 3600 IN NS ns2.example.com. file-mix.com. 3600 IN NS ns1.example.com. file-mix.com. 3600 IN TXT "v=spf1 ip4:138.201.73.238 a mx ~all" file-mix.com. 3600 IN MX 10 mail.file-mix.com. file-mix.com. 3600 IN MX 20 mail.file-mix.com. mail.file-mix.com. 3600 IN A 138.201.73.238 ;; Query time: 39 msec ;; SERVER: 2a01:4f8:172:1441::2#53(2a01:4f8:172:1441::2) ;; WHEN: Tue Apr 14 09:06:58 MSK 2020 ;; MSG SIZE rcvd: 243
We immediately get 2 IP addresses:
- 138.201.59.125 (the site itself)
- 138.201.73.238 (mail server)
These lines indicate that the configuration is not completed:
- root.example.com
- ns2.example.com
- ns1.example.com
Do not forget the failsame.ru domain from which it all began:
dig +nocomments failsame.ru @2a01:4f8:172:1441::2 ANY
Nothing was found.
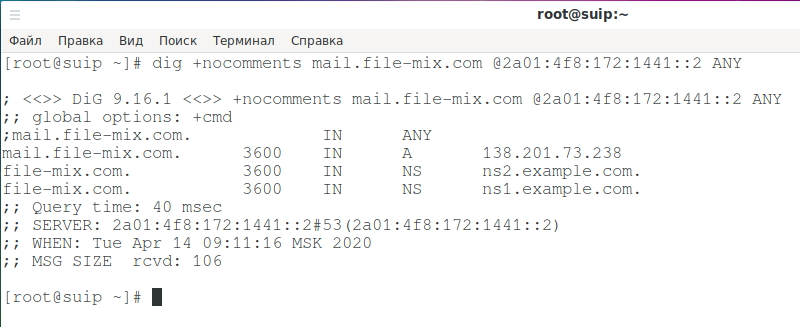
Also check the mail subdomain:
dig +nocomments mail.file-mix.com @2a01:4f8:172:1441::2 ANY
We confirm that we found a real IP site
We do a check:
curl 138.201.59.125 -H 'Host: file-mix.com'
In the answer we see the source code of file-mix.com.
The web server on 138.201.73.238 shows some kind of test site, let's try to cause an error:
curl 138.201.73.238:443
We get:
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>400 Bad Request</title> </head><body> <h1>Bad Request</h1> <p>Your browser sent a request that this server could not understand.<br /> Reason: You're speaking plain HTTP to an SSL-enabled server port.<br /> Instead use the HTTPS scheme to access this URL, please.<br /> </p> <hr> <address>Apache/2.4.25 (Debian) Server at fail-space.ru Port 443</address> </body></html>
The error mentions the fail-space.ru domain, that is, this site is served on this web server.
Looking for IPv6 address neighbors
When renting a VPS server, IPv6 is usually issued sequentially, so it makes sense to try scanning a small subnet:
sudo nmap -6 2a01:4f8:172:1441::/112
What is the disclosure of a real IP site for?
CloudFlare is a proxy between the site and the user, which also acts as a file firewall and a bot filter. Through CloudFlare, you can only access the web server and it is not possible to find out what other services are running on the target server. Now that we know the real IP addresses, we can perform a full service scan:
sudo nmap -p- 138.201.59.125
The following results were obtained:
Host is up (0.66s latency). Not shown: 65522 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 25/tcp open smtp 53/tcp open domain 80/tcp open http 110/tcp open pop3 143/tcp open imap 443/tcp open https 465/tcp open smtps 587/tcp open submission 993/tcp open imaps 995/tcp open pop3s 1500/tcp open vlsi-lm
Scanning the second IP address:
sudo nmap -p- 138.201.73.238
It gave the following:
Host is up (0.35s latency). Not shown: 65523 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 25/tcp open smtp 53/tcp open domain 80/tcp open http 110/tcp open pop3 143/tcp open imap 443/tcp open https 465/tcp open smtps 587/tcp open submission 993/tcp open imaps 995/tcp open pop3s
So, in addition to phpMyAdmin and roundcube, the links to which we found earlier, at our disposal for brute force, exploitation and vulnerability auditing the following service:
- FTP
- SSH
- SMTP(S)
- POP3(S)
- IMAP(S)
And in addition the login page on port 1500 (isp manager): http://138.201.59.125:1500 (by the way, https://file-mix.com:1500 does not work!).
In general, entertainment for the whole evening!
Trophy analysis
As I said, we will limit ourselves to analyzing the perimeter, but this does not mean that we do not have trophies! There are trophies!
The lulzbuster tool gave us an interesting link https://failsame.ru/cgi-bin/awstats.pl, which gives an error 403:
Forbidden You don't have permission to access /cgi-bin/ on this server.
When analyzing the file-mix.com domain:
lulzbuster -s https://file-mix.com/ -w /usr/share/lulzbuster/lists/big.txt
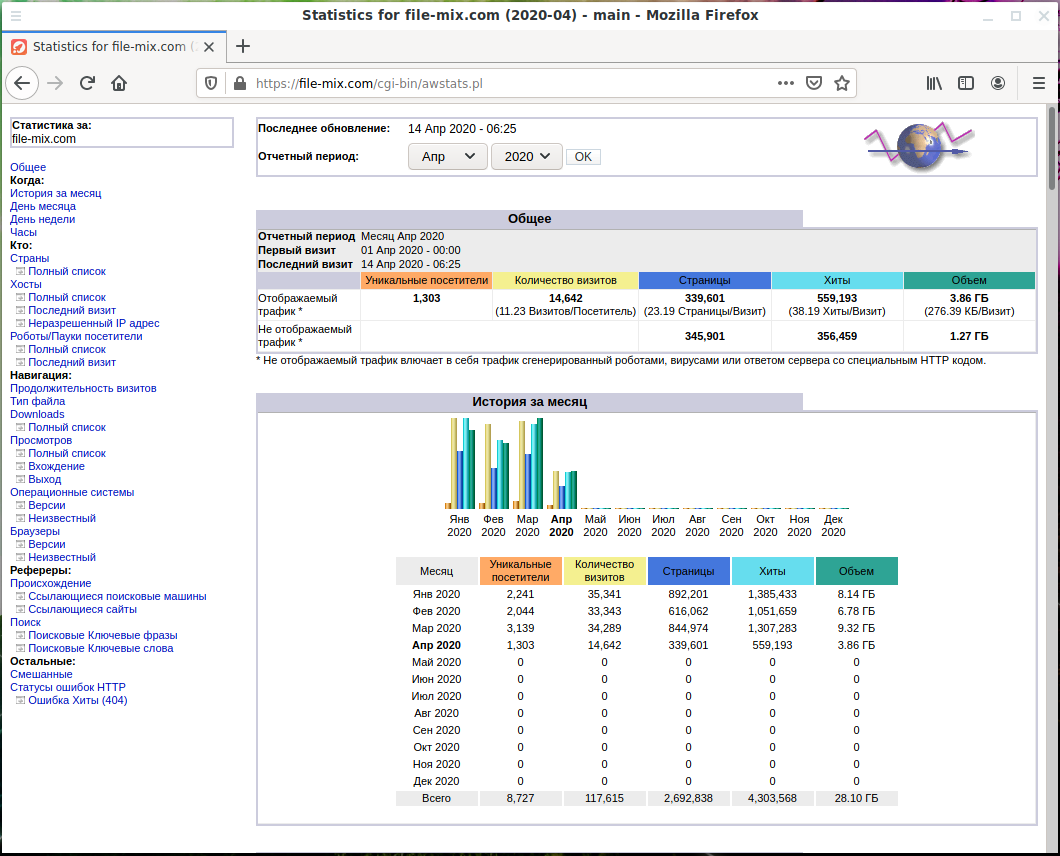
found a similar link https://file-mix.com/cgi-bin/awstats.pl, and there:
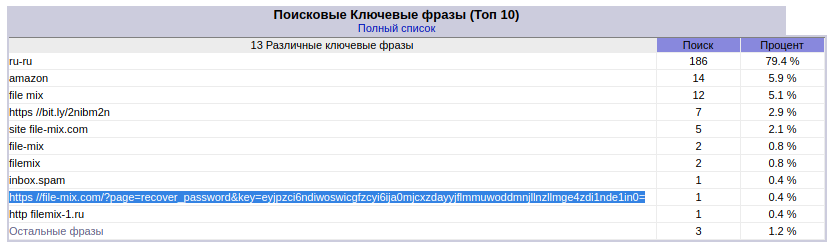
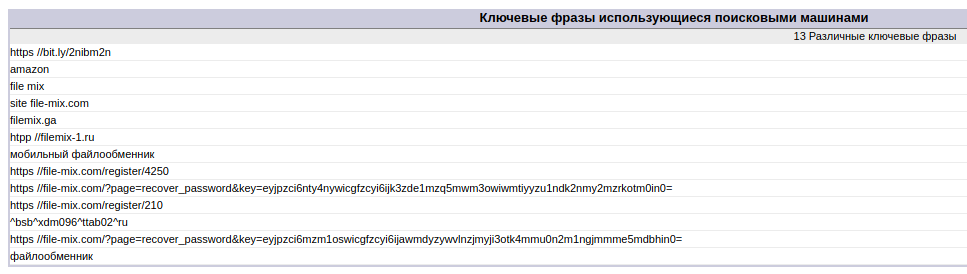
And there are statistics accessible without a password. Analysis of search queries gives us links to reset the password (I don’t know how to explain this fact, but many people actually copy-paste the website URL into Google and click on the link provided):
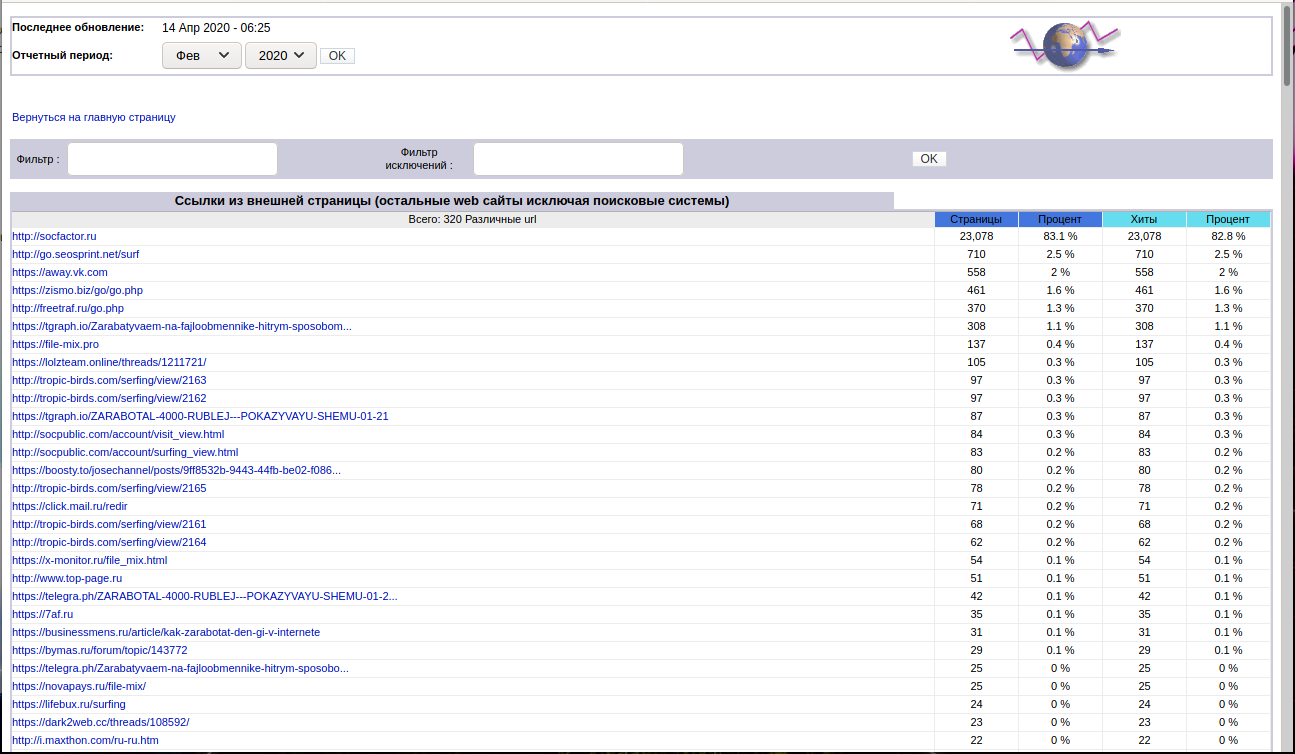
The analysis of referrers allows us to evaluate the ways of “promotion” (these are sites for cheating social signals and performing penny tasks like “enter such string in the search engine, open such a website and so on”):
- http://socfactor.ru
- http://go.seosprint.net/surf
- https://zismo.biz/go/go.php
- http://freetraf.ru/go.php
Also, traffic from tgraph.io (Telegram), where gullible schoolchildren are told how “I earned 4000 yesterday” and “earning money on the Internet without knowing anything”:
There are also links from “hacker” forums from the “darknet” where schoolchildren shows each other “tricky schemes of earning”.
In general, spam, trash, once again spam, trash, scam, spam, spam. That is, a reference example of inefficient spending of time and the best years of life.
And on the other hand: users who have downloaded the file and spend time cleaning the computer from adware and plug-ins, administrators and moderators who clean sites and forums from spam.
And in the center of all this is the reviewed site that advertises casinos, bookmakers, other very dubious things, imposes Push subscriptions, motivates the distribution of copyrighted files and dangerous files.
Related articles:
- How to bypass Cloudflare, Incapsula, SUCURI and another WAF (68.3%)
- Utilities for information gathering, OSINT and network analysis in Windows and Linux (57.9%)
- How to find out if a site is behind CloudFlare or not (54.8%)
- Text sniffing by the sound of the pressed buttons (53.8%)
- How to find out the Autonomous system on the IP and how to find out all the Autonomous System IPs (52.9%)
- Nmap usage tips (RANDOM - 50.5%)


Great forensic asssement …