lulzbuster: a tool for quick enumeration of hidden files and folders on sites
Almost every site has files and folders that no links lead to. Among them, very interesting ones may come across, for example, forgotten backup copies of a database or site, phpMyAdmin, entries in administrative panels and other pages that are not intended for general access.
Several articles have already been devoted to the search for hidden files and folders, for example: Searching for admin pages of websites.
In this article we will learn how to use the lulzbuster program, it is very fast, easy to use and stably performs its function. Moreover, the program has such unique functions as the choice of the request method and the choice of the HTTP version.
How to install lulzbuster
Install lulzbuster on Kali Linux
sudo apt install libcurl4 libcurl4-openssl-dev git clone https://github.com/noptrix/lulzbuster cd lulzbuster make lulzbuster sudo make install
Install lulzbuster on BlackArch
sudo pacman -S lulzbuster
How to start search for hidden files with lulzbuster
Please note: the program makes a lot of requests to the site and can cause a malfunction in its work (as it happens during a DoS attack), therefore, scan other people's sites only with the permission of their owner! You were warned!!!
The program has only one required option -s after which you need to specify the target site:
lulzbuster -s https://SITE.RU/
Moreover, the site must be indicated with the protocol (HTTP or HTTPS), for example:
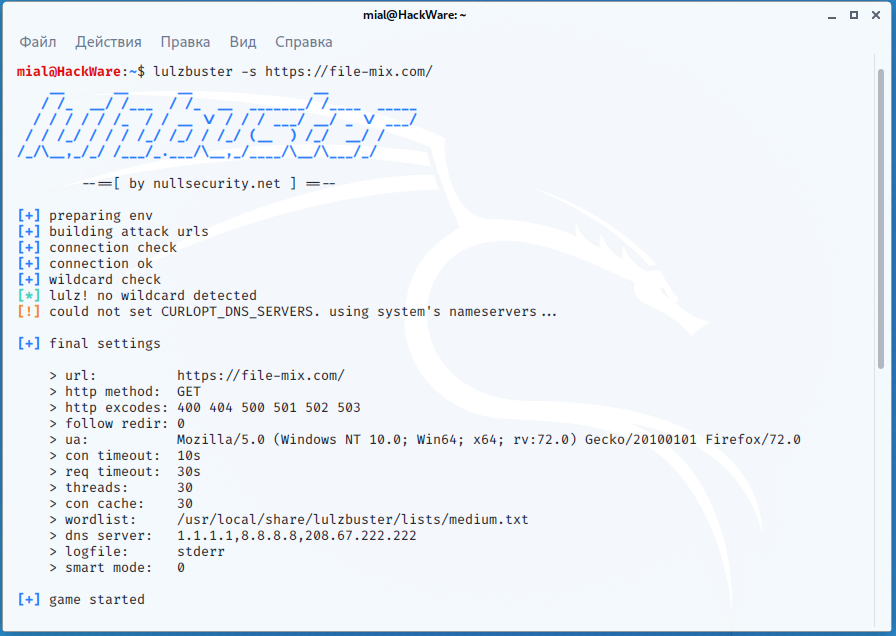
lulzbuster -s https://file-mix.com/
The program will start by displaying its settings – many values are set by default, but they can be changed with the options:
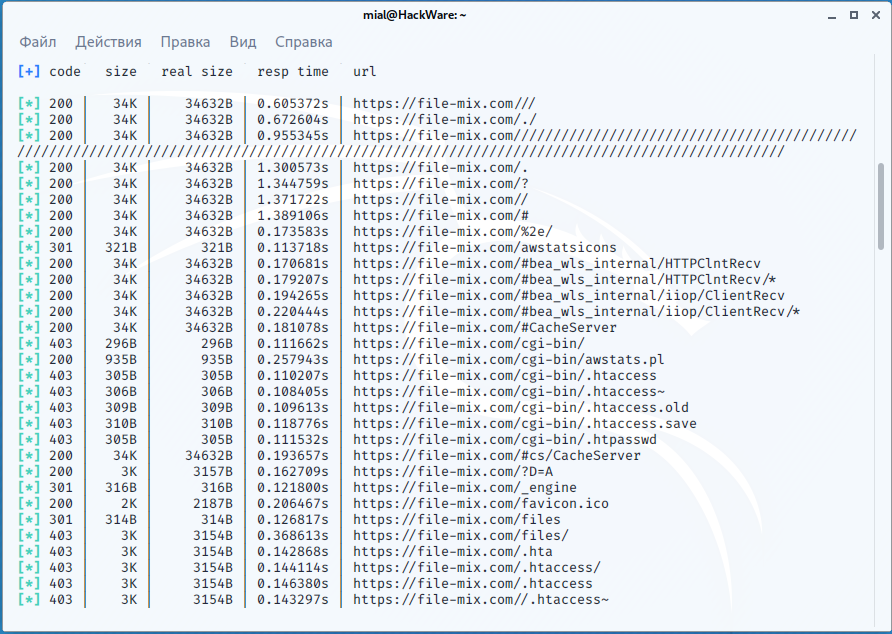
Then the program will start outputting data with the following columns:
- code (HTTP response status code)
- size (size of received data)
- real size
- resp time (response time)
- url (link of the found page)
By default, a medium-sized dictionary is used, and in total three dictionaries are supplied with the program:
- big.txt
- medium.txt
- small.txt
On Kali Linux, these dictionaries are located in the following files:
- /usr/local/share/lulzbuster/lists/big.txt
- /usr/local/share/lulzbuster/lists/medium.txt
- /usr/local/share/lulzbuster/lists/small.txt
To select any of these dictionaries, or your own, use the -w option, for example:
lulzbuster -s https://file-mix.com/ -w /usr/local/share/lulzbuster/listsbig.txt
How to exclude responses with specific status codes
By default, links that returned the following HTTP response codes are not shown: 400,404,500,501,502,503. You can change this list by adding or removing any codes. The -x option is used for this, the response codes themselves must be listed with a comma:
lulzbuster -s https://SITE.com/ -x 400,404,500,501,502,503,403,405
How to save lulzbuster results to a file
By default, lulzbuster outputs information to standard error (stderr). You can specify a file to save the results with the -l option:
lulzbuster -s https://file-mix.com/ -w /usr/local/share/lulzbuster/lists/small.txt -l ~/file-mix.com-url.txt
Please note that it is better to specify the absolute path to the file, because otherwise the file will be saved relative to the lulzbuster working directory.
How to add an extension for scanned files
Using the -A <STRING> option, you can add any words separated by a comma (for example, /,.php,~bak).
How to scan with lulzbuster through Tor
If not already done, install and start the Tor service:
sudo apt install tor sudo systemctl start tor
Now, add -p socks5://localhost:9050 to your lulzbuster command, for example:
lulzbuster -s https://file-mix.com/ -p socks5://localhost:9050
Remember that some sites do not accept at all connections from IP addresses of Tor network.
How to scan with lulzbuster through a proxy
Several types of proxies are supported. To see the available options, run the command:
lulzbuster -p ?
Output Example:
[+] available proxy schemes
> http
> https
> socks4
> socks4a
> socks5
> socks5h
For proxies, use the following options:
-p <addr> - proxy address (format: <scheme>://<host>:<port>) -P <creds> - proxy auth credentials (format: <user>:<pass>)
How to scan in lulzbuster if certificate is invalid
It happens that the certificate is expired, or the IP address is scanned, in this case, web browsers show a warning, and lulzbuster stops the scan with an error:
[-] could not connect to:
To perform a scan even though the certificate is incorrect, use the -i option:
lulzbuster -s https://koronavirus.info/ -i
Smart mode of lulzbuster
The smart mode, which includes skipping false positives, shows more information, etc., enabled by the -S option:
lulzbuster -s https://file-mix.com/ -S
Use smart mode only if speed is not your top priority!
How to change User Agent in lulzbuster
Lulzbuster already has a large list of built-in user agents. To list them, run the command:
lulzbuster -X
You can specify any User Agent value using the -u <LINE> option.
You can also use random User Agents from the built-in, for this, specify the -U option.
lulzbuster with http authentication and header passing
It is possible to perform scans with lulzbuster with HTTP authentication or sending HTTP headers (for example, cookies). This can be done with the following options:
-c <str> - pass custom header(s) (e.g. 'Cookie: foo=bar; lol=lulz') -a <creds> - http auth credentials (format: <user>:<pass>)
Scan speed and timeout of lulzbuster
Using the -t <NUMBER> option, you can specify the number of scanning threads.
The following timeout options are also available:
-D <num> - num seconds for delay between requests (default: 0)
-C <num> - num seconds for connect timeout (default: 10)
-R <num> - num seconds for request timeout (default: 30)
-T <num> - num seconds to give up and exit lulzbuster completely
(default: none)
Scanning with POST, HEAD, PUT, DELETE and another HTTP request methods
By default, scanning is performed using the GET method, but you can select a different HTTP request method.
To list all available methods, run the command:
lulzbuster -h ?
Output Example:
[+] available HTTP requests types
> HEAD
> GET
> POST
> PUT
> DELETE
> OPTIONS
The desired type of HTTP requests is indicated by the -h <TYPE> option.
How to scan different versions of HTTP
The HTTP protocol has several versions and you can choose the one you want to use. To do this, use the option -j <NUMBER>.
To see the available versions of HTTP, run the command:
lulzbuster -j ?
Output Example:
[+] available http versions
> 1.0
> 1.1
> 2.0
> 3.0
All lulzbuster options
Usage
lulzbuster -s <arg> [opts] | <misc>
Options:
target options
-s <url> - start url to begin scan with
http options
-h <type> - http request type (default: GET) - ? to list types
-x <code> - exclude http status codes (default: 400,404,500,501,502,503
multi codes separated by ',')
-f - follow http redirects. hint: better try appending a '/'
with '-A' option first instead of using '-f'
-F <num> - num level to follow http redirects (default: 0)
-u <str> - user-agent string (default: built-in windows firefox)
-U - use random built-in user-agents
-c <str> - pass custom header(s) (e.g. 'Cookie: foo=bar; lol=lulz')
-a <creds> - http auth credentials (format: <user>:<pass>)
-r - turn on auto update referrer
-j <num> - define http version (default: curl's default) - ? to list
timeout options
-D <num> - num seconds for delay between requests (default: 0)
-C <num> - num seconds for connect timeout (default: 10)
-R <num> - num seconds for request timeout (default: 30)
-T <num> - num seconds to give up and exit lulzbuster completely
(default: none)
tuning options
-t <num> - num threads for concurrent scanning (default: 30)
-g <num> - num connection cache size for curl (default: 30)
note: this value should always equal to -t's value
other options
-w <file> - wordlist file
(default: /usr/share/lulzbuster/lists/medium.txt)
-A <str> - append any words separated by comma (e.g. '/,.php,~bak)
-p <addr> - proxy address (format: <scheme>://<host>:<port>) - ? to
list supported schemes
-P <creds> - proxy auth credentials (format: <user>:<pass>)
-i - insecure mode (skips ssl/tls cert verification)
-S - smart mode aka eliminate false-positives, more infos,
etc. (use this if speed is not your 1st priority!)
-n <str> - nameservers (default: '1.1.1.1,8.8.8.8,208.67.222.222'
multi separated by '.')
-l <file> - log found paths and valid urls to file
misc
-X - print built-in user-agents
-V - print version of lulzbuster and exit
-H - print this help and exit
Conclusion
So lulzbuster is another great tool for websites pentest.
An example of the use of this program, see the case “Revealing the perimeter”.
Related articles:
- How to open and exploit .DS_Store (63.9%)
- How to analyze POST requests in web browsers (58.4%)
- How to discover subdomains without brute-force (58.4%)
- FinalRecon: a simple and fast tool to gather information about web sites, works on Windows (56.6%)
- How to use User Agent to attack websites (55.5%)
- How to hack Wi-Fi with a regular adapter without monitor mode (RANDOM - 2.5%)