How to find out hostnames for many IP addresses
In this article, we will discuss how to use the HostHunter program, which is able to determine hostnames for a large number of IP addresses. Although HostHunter is primarily designed to work with a large array of IP, you can, if desired, use it to search for hostnames of and a single IP address, since this script uses its own OSINT techniques. We will also look at how to generate files with IP addresses in a format that HostHunter supports in the Linux command line.
We will begin with a review of other techniques to reveal a hostname (domain, site name) from an IP address.
How to map an IP address to a hostname
The first way to get a host name by IP is based on a PTR record. From it, information can be obtained using the nslookup or dig utilities with the -x option:
dig -x 185.117.153.79
Or:
nslookup 185.117.153.79
Another way is based on using a large array of collected data, which can be accessed through securitytrails.com and, for example, SuIP.biz:
How to reveal hostnames of a large number of IP
Here HostHunter comes in handy, this program at the input receives a file with an IP list and searches for the hostname for each of them. This program uses the Hacker Target API and Bing.com.
How to install the HostHunter program in Kali Linux:
git clone https://github.com/SpiderLabs/HostHunter cd HostHunter sudo pip3 install -r requirements.txt sudo pip3 install selenium
When installing in this way, you will need to go to the folder with the program to start:
cd HostHunter
And run like this:
python3 hosthunter.py -h
For future program updates:
cd HostHunter git pull
To install HostHunter on BlackArch:
sudo pacman -S hosthunter
In BlackArch, to launch the script it is enough to specify the name of the program:
hosthunter -h
Usage:
hosthunter [-h] [-V] [-f FORMAT] [-o OUTPUT] [-b] [-sc] targets
Options:
positional arguments:
targets Sets the path of the target IPs file.
optional arguments:
-h, --help show this help message and exit
-V, --version Displays the currenct version.
-f FORMAT, --format FORMAT
Choose between CSV and TXT output file formats.
-o OUTPUT, --output OUTPUT
Sets the path of the output file.
-b, --bing Use Bing.com search engine to discover more hostnames
associated with the target IP addreses.
-sc, --screen-capture
Capture a screen shot of any associated Web
Applications.
The program works only with files containing a list of IP addresses. My address list is saved in the ip.txt file, then to start the program I need to type:
hosthunter ip.txt
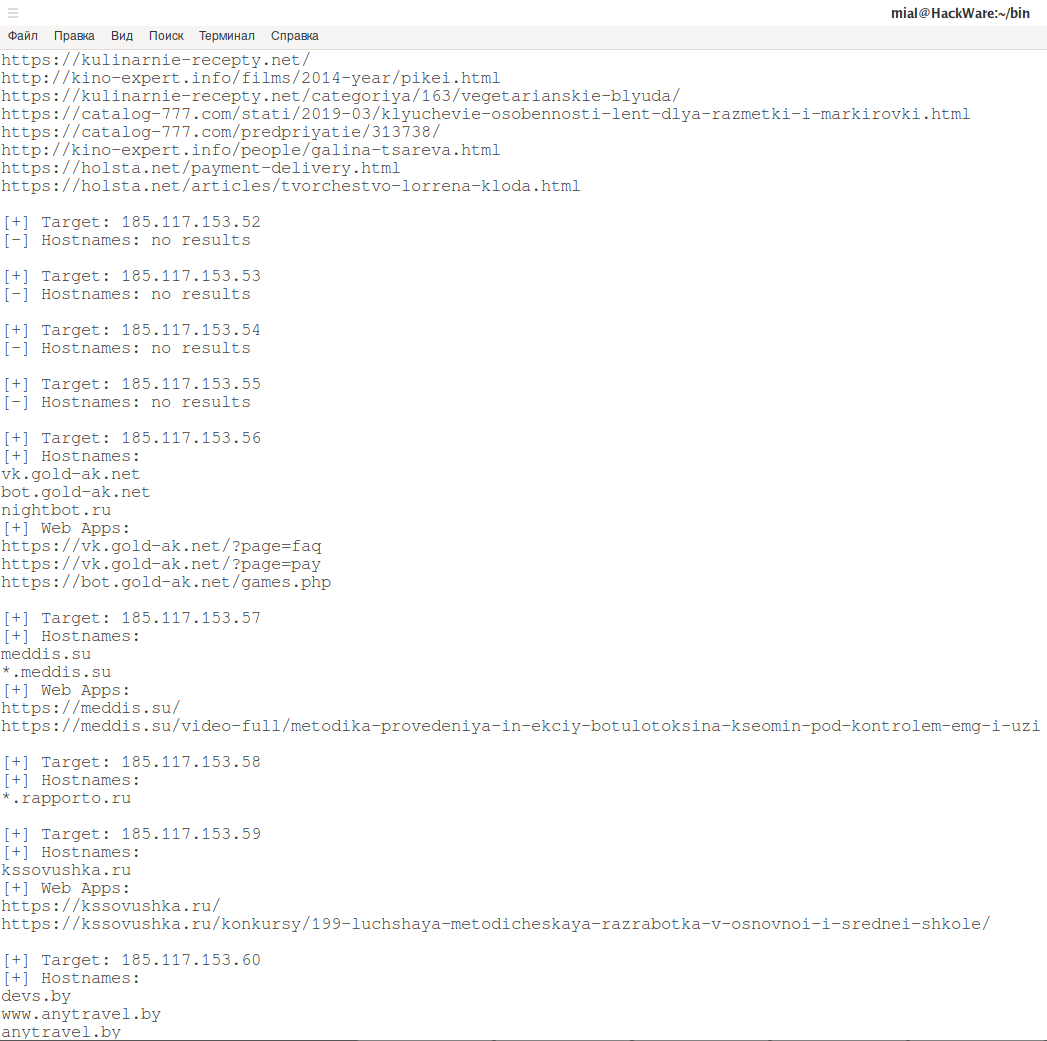
The program started, as you can see, for some IP hostnames exist, and some IP are simply not used:
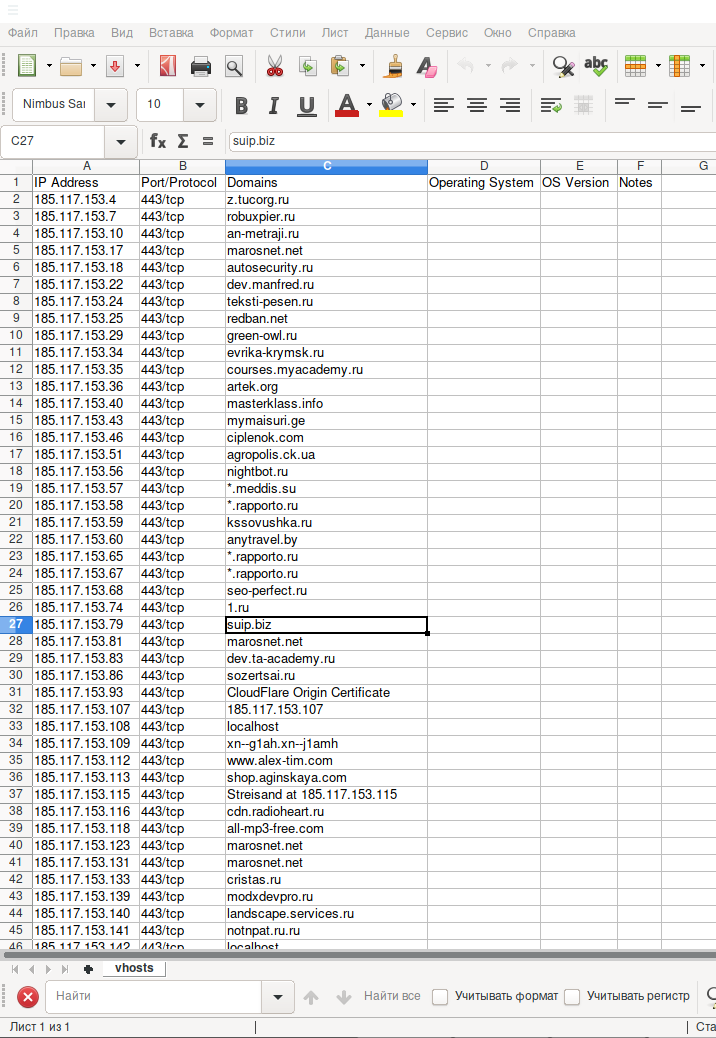
The program saves the results to a .csv file (tables) by default:
The results file contains information only about those IPs for which host name values were found. As you can see, the table provides the fields "Domains", "Operating System", "OS Version", "Notes", but at the moment the collection of this information has not yet been implemented.
When restarting, the program will ask:
vhosts.csv file already exists, would you like to overwrite it? Answer with [Y]es or [N]o : Y
That is, the vhosts.csv file with the results already exists, you can select the option to overwrite this file (Y) or stop the launch (N).
Using the option -f TXT, you can set the text format to save the received data:
hosthunter -f TXT ip.txt
Note that when using the -f TXT option, the data is also saved to the vhosts.csv file — only the file format (contents) changes — the found hosts are saved there without any additional information — one hostname per line.
By the way, using the -o option you can specify a different filename for the output file:
hosthunter -o hostnames_list.csv ip.txt
And with the -b option, you can enable the Bing module for an additional search result:
hosthunter -b ip.txt
An example of using the -b option:
There are a few more results and sometimes new hosts actually appear in them, but sometimes only links to internal pages are added.
With this option, additional data is saved to the webapps.txt file.
The ability to collect screenshots has been added to the program as a beta function. To enable this module, use the -sc option:
hosthunter -sc ip.txt
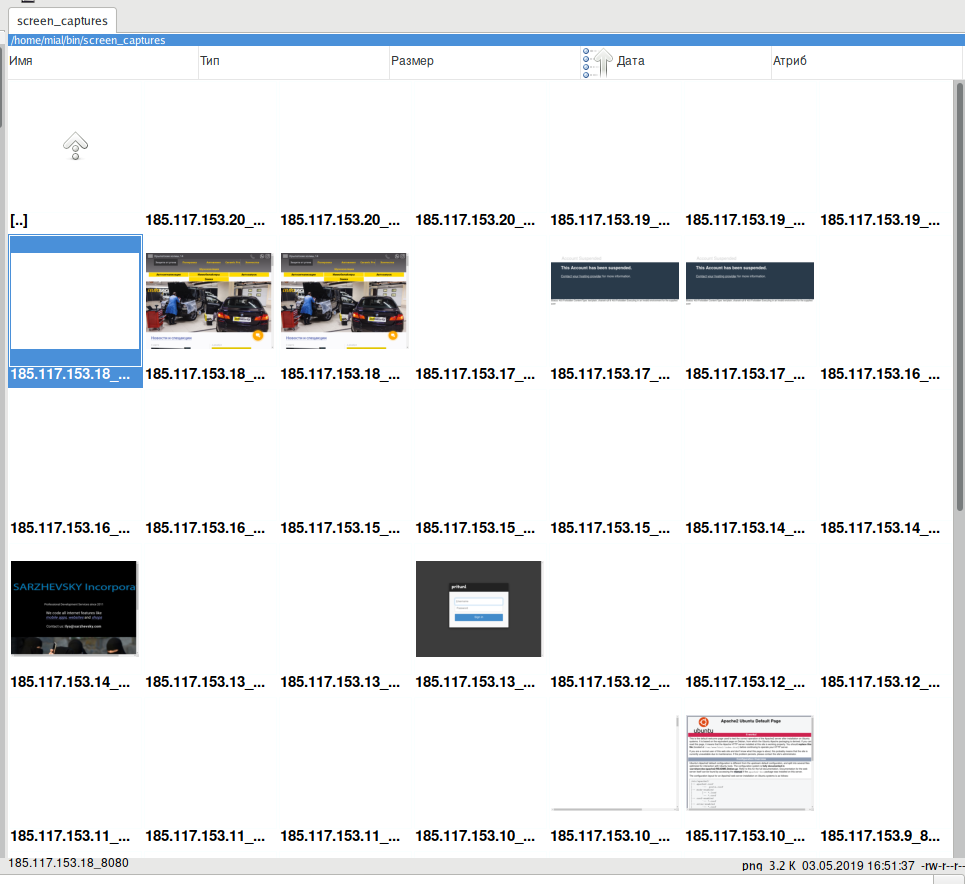
Screenshots are saved in the ./screen_captures/ folder. Sample of collected screenshots:
As you can see, an attempt is made to take a screenshot from each IP address, regardless of whether it was possible for it to find out the hostname or not. For each IP, an attempt is made to obtain a screenshot on ports 80, 443, 8080.
If you want to extract only the hosts from the vhosts.csv file, then for this execute the command:
awk -F '","' '{print $3}' vhosts.csv
Some lines can contain several hosts at once, separated by commas, if you want each host to be on a separate line, do this:
awk -F '","' '{print $3}' vhosts.csv | tr "," "\n"
If you really need it, you can even use HostHunter to search for the hostname of a single IP address:
echo '185.117.153.79' | hosthunter /dev/stdin
This trick will not work if the vhosts.csv file is already present.
How to make a list of IP addresses – each address on a new line
HostHunter only supports files in which each IP is listed on a separate line – using masks and ranges notations is not supported.
Such IP lists can be compiled during the perimeter investigation process. But sometimes you need to generate such files if you know the target range. Take this example: the SuIP.biz site is hosted on IP 185.117.153.79, for some reason, I want to know which hosts are its neighbors. That is, I am interested in all hosts that are in the range from 185.117.153.1 to 185.117.255.
In this case, to generate an IP list, you can use the Bash shell property as ranges. If you specify two characters through two points in curly brackets, the shell itself lists all the options in this range. To make it clear, here are some examples:
echo {a..c}
a b c
echo {a..x}
a b c d e f g h i j k l m n o p q r s t u v w x
echo {x..g}
x w v u t s r q p o n m l k j i h g
echo {0..7}
0 1 2 3 4 5 6 7
I think everything is obvious in them.
To generate a list of IP addresses in the range 185.117.153.1-255 you can run:
echo 185.117.153.{1..255}
But the problem is that the addresses are separated by a space, not a newline character. Therefore, we need to replace each space with a newline symblol:
echo 185.117.153.{1..255} | tr " " "\n"
Now that we have verified that everything works as we expected, we redirect the output to save the addresses to a file:
echo 185.117.153.{1..255} | tr " " "\n" > ip.txt
If ranges are needed in other octets, this is done in a similar way. For example, I want to create an address range of 185.117.151-155.1-255, then:
echo 185.117.{151..155}.{1..255} | tr " " "\n"
If the range is specified using a mask, for example: 185.117.153.0/20, then not everyone can say easy which addresses are included there, use the sipcalc program for this:
sipcalc 185.117.153.0/20
You will see something like this:
-[ipv4 : 185.117.153.0/20] - 0 [CIDR] Host address - 185.117.153.0 Host address (decimal) - 3111491840 Host address (hex) - B9759900 Network address - 185.117.144.0 Network mask - 255.255.240.0 Network mask (bits) - 20 Network mask (hex) - FFFFF000 Broadcast address - 185.117.159.255 Cisco wildcard - 0.0.15.255 Addresses in network - 4096 Network range - 185.117.144.0 - 185.117.159.255 Usable range - 185.117.144.1 - 185.117.159.254
In this output, find the line beginning with the Network range — it will contain the range in a clearer notation, for example, 185.117.144.0 - 185.117.159.255.
Related articles:
- FinalRecon: a simple and fast tool to gather information about web sites, works on Windows (96.8%)
- How to search subdomains and build graphs of network structure with Amass (94%)
- Perimeter analysis for website security audit (93.9%)
- The fastest subdomains enumeration and monitoring (also works on Windows!) (84.7%)
- TIDoS-Framework: Web Application Information Gathering and Manual Scanning Platform (67.8%)
- sqlmap usage guide. Part 1: Basic web-site checks (GET) (RANDOM - 28.8%)