Kodachi (OS for anonymity, security and anti-forensics) – is questionable!
First acquaintance with Kodachi
Well… I was going to write a manual about Linux Kodachi. But as I became acquainted, I realized that I do not like Kodachi and raises questions of trust in this OS. It’s not a matter of taste – decoration or sticky widgets – there's no accounting for taste. The point is practicality.
1. Open ports on Kodachi
Open ports on Linux can be viewed with the command:
ss -tulpn
This is what the output of this command looks like on my home-working computer, where the Linux distribution was installed 2 years ago (Arch Linux + BlackArch repositories):
That is, there are no open ports.
This is what the open ports on Kali Linux look like, which I use to write instructions:
There are no open ports either. And this is logical since any port should open only if the user who uses the computer really needs it. The operating system (any) by default should not have any open ports, because:
1) risk of exploitation/brute-force service on this port and computer compromise
2) the risk is that it is a running backdoor (trojan) that is waiting for an incoming connection.
For this reason, Kali Linux even has a special policy: autorun is not allowed for all network services by default. In Arch Linux and derivatives, similarly – almost all services, even the display manager, require explicit instructions for autorun.
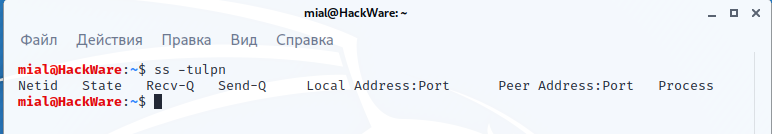
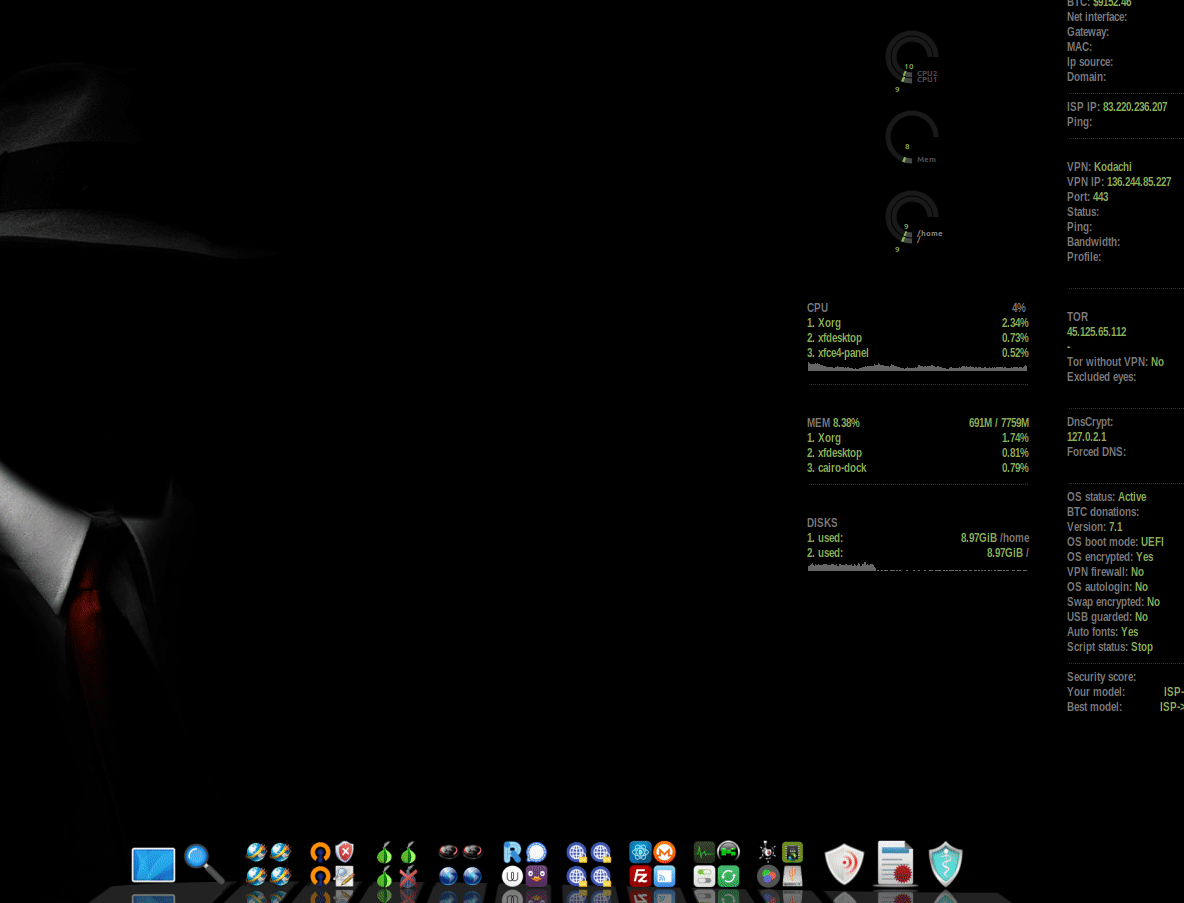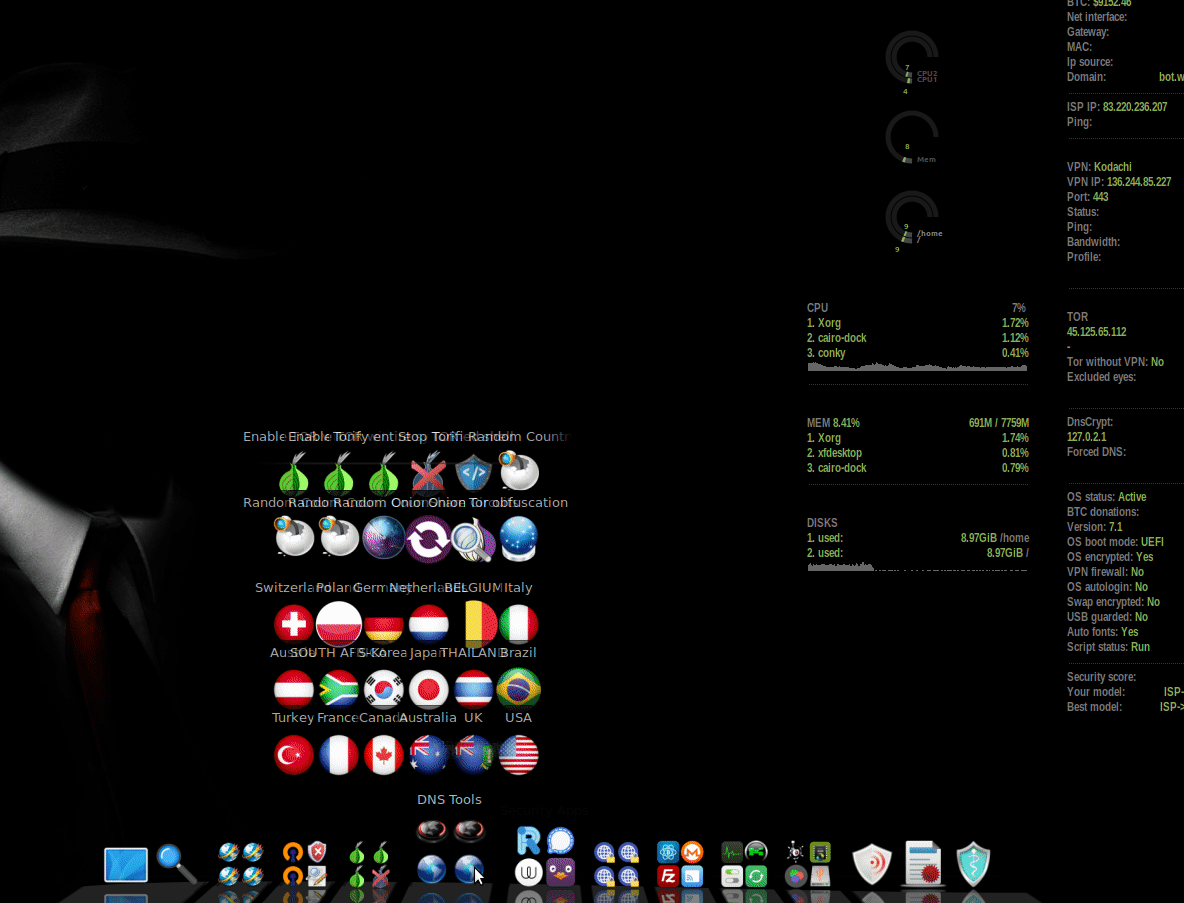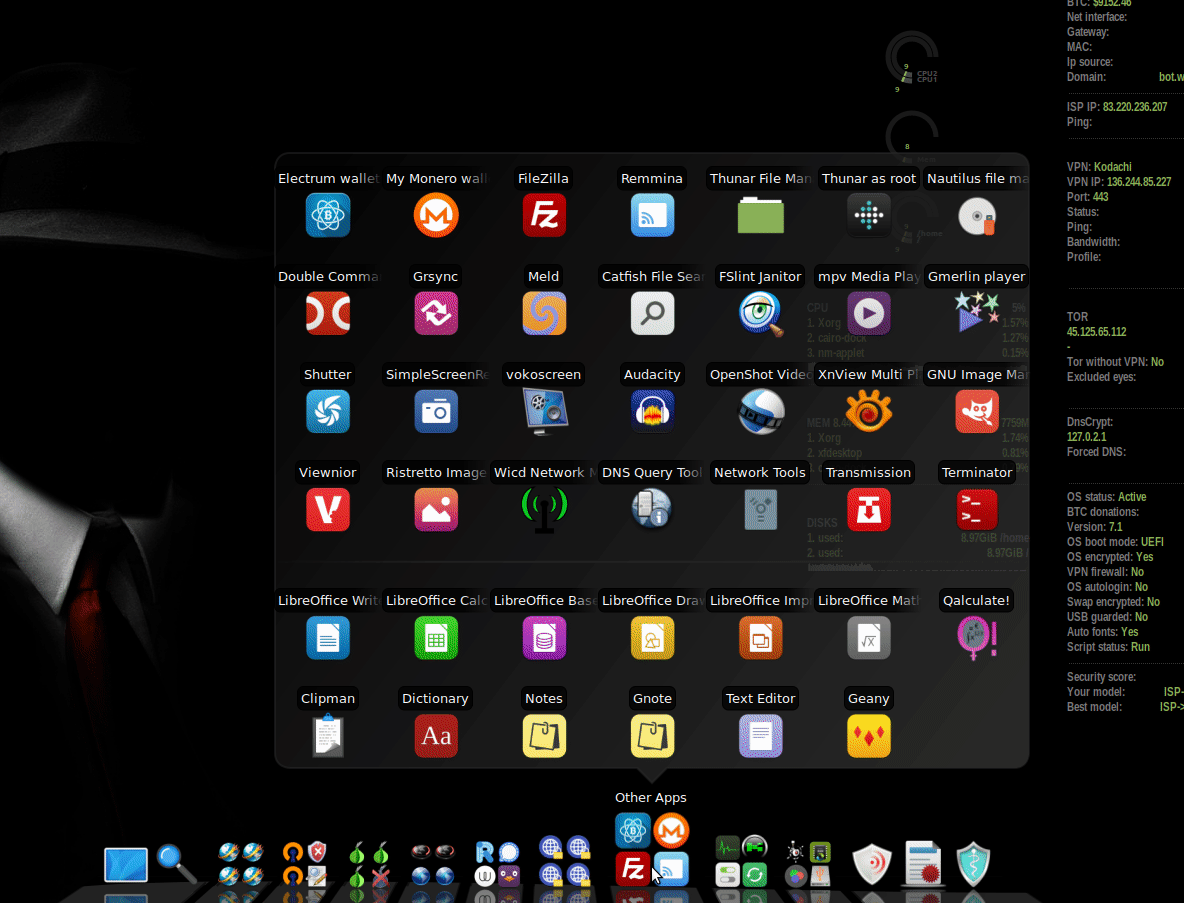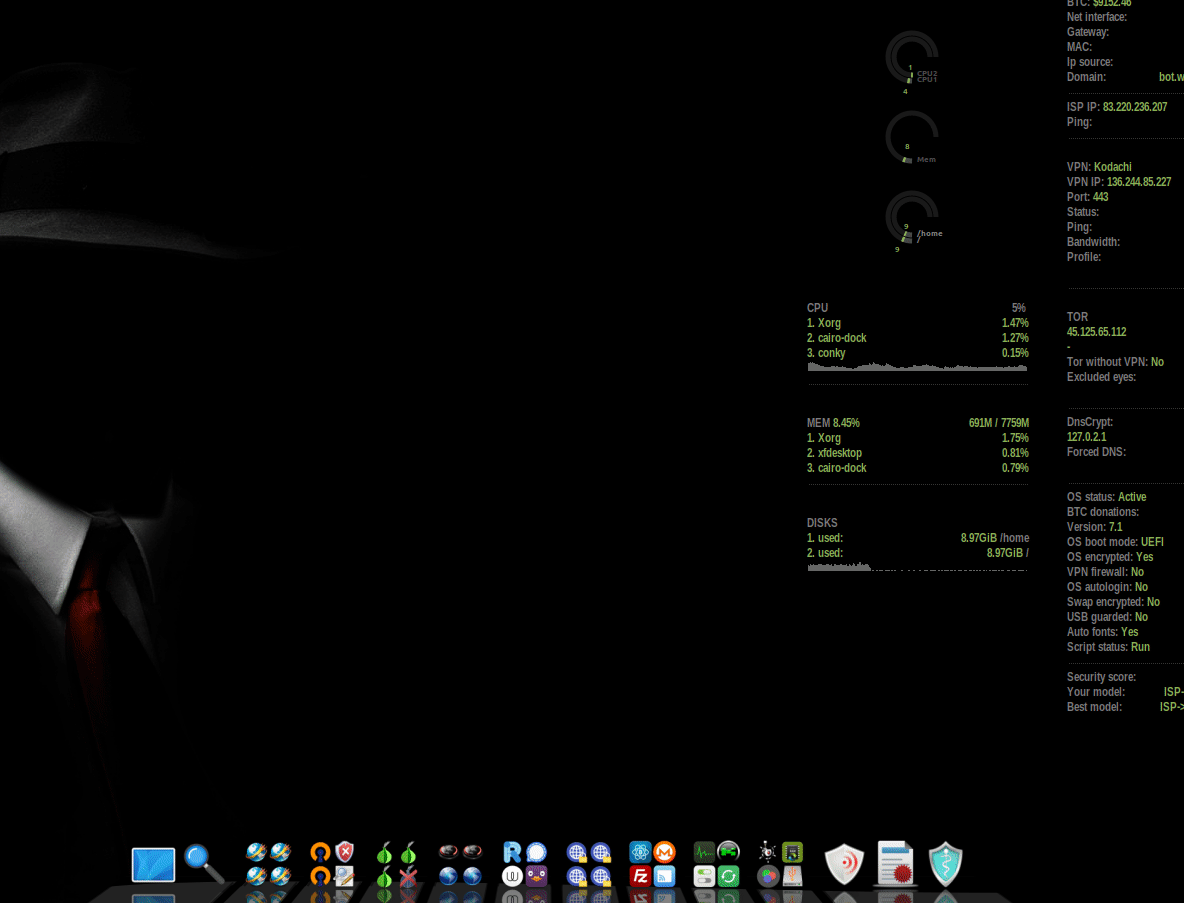
Here's what open port checking looks like in Kodachi:
You can ignore the open ports that are listening on local addresses. But wait… since by default Kodachi is connected via VPN, then connections to the port on local IP can come from the local network.
But the open ports on 0.0.0.0 (open to everyone on IP networks) and [::] (open to everyone on IPv6 networks) deserve particular concern.
There should be no ports open to the whole world in ordinary distributions (by default), and even in a security-oriented distribution, this is generally unacceptable.
Ports are normally scanned from an external computer - some are marked as open|filtered, and one is simply open:
sudo nmap -sV --script=banner -sU -p 68,123,631,5353,39953 192.168.43.234
Even if these are not backdoors, then this is not normal, at least because such a set of ports is a fingerprint by which it can be determined the remote user is working on Kodachi. The set of ports if every installation is the same, only the last one changes. I understand that a VPN connection opens a port (most likely the last random port is used for a VPN). But why the rest?
2. NOT easy
There are already many similar distributions, so Kodachi is characterized by the author as “no setup or Linux knowledge is required”.
I have knowledge of Linux, I read all the documentation on Kodachi – I DO NOT UNDERSTAND how to use Kodachi…
Here's an overview of the shortcuts on the main screen:
I don’t know if everything is clear to you there – I haven’t figured it out yet.
3. Not good anonymity model
VPN is a good technology when used correctly (creating virtual private networks, encrypting traffic), but it is not suitable for anonymity. Kodachi intensively uses VPN.
Moreover, each Kodachi user has his own identifier – this is written in the documentation. The identifier is needed not for tracking users, but for the ban of those who abuse and overtake too much traffic. The fact is that VPNs are used on servers for which the author of Kodachi pays. It can be understood, without this measure, all VPNs would quickly become unusable due to the fact that several users would download torrents or movies through them. As the author himself says, Kodachi is provided for anonymous surfing and not for heavy daily file and movies downloads.
But anonymity, which begins with an identifier… is like anonymity in a Telegram, which begins with registration by phone number and search by address book… IDK why many accept it, but I do not need such anonymity!
4. Not good distribution base
Xubuntu is taken as base distribution, that is, in fact, Ubuntu. If you installed the latest versions of Ubuntu, you might have noticed how many shortcuts there are for different cloud services that most do not need. It seems that this is Windows, which runs a virus that has installed a couple of dozen shortcuts.
It got to the point that Linux Mint (based on Ubuntu) BLOCKS the Snap installation (developed by Canonical Ltd.), which behaves like a real trojan – it is installed hidden, overwrites part of the packages secretly and secretly connects to remote servers. This was said last year (https://blog.linuxmint.com/?p=3766) and was repeated again in this year (https://blog.linuxmint.com/?p=3906).
My personal use of Ubuntu evoked only negative emotions. Constantly occurring errors and the proposal to send a report – I already had a similar OS, it was called Windows '98.
5. Not good desktop environment tuning
The distribution uses XFCE, but it is made to look like GNOME 3. Result: it is almost impossible to find and open a minimized application. In general, the feeling of the desktop: "show off ahead usability".
Conclusion
I don’t draw any far-reaching conclusions because of the availability of open ports – perhaps partly due to poor configuration, and partly inherited from Ubuntu. Although the situation needs further investigation.
Moreover, I will consider Kodachi in details and will write manual! With a discussion of the features and advantages of this distribution. Ones need to understand the pros, cons and risks of various tools and apply them when it is most appropriate.
Related articles:
- Anonymous scanning through Tor with Nmap, sqlmap or WPScan (50%)
- Free easy way to hide IP in Linux (50%)
- How to install and run Tor Browser on Kali Linux (50%)
- How to install VeraCrypt on Linux (50%)
- How to install Tor and create Tor hidden service on Windows (50%)
- How NOT to do phishing attacks (CASE) (RANDOM - 50%)



Great article Alex!
Thanks for every post you make, you are one of the people I love to read in netsec and you make it so simple, even if english is not your first language (neither is mine).
Keep it going!
P.S.: Do you have twitter account where you post interesting stuff too? Sorry to bother.