How to identify hash types – new tools with modern hashes support
In the article “How to identify hash types” we have already got acquainted with such utilities as hashID and HashTag, which determine the hash string by which algorithm it was calculated.
The aforementioned tools still work, but the world does not stand still (and the development of these programs does stand still). Now there are new types of hashes that are not supported or have errors in these tools.
Right now, at the time of writing, two new programs are under active development for identifying hash types. They support more hashing algorithms and are just better than the old tools in everything. This article is devoted to acquaintance with new tools for identifying a hash type.
Why do we need new tools for identifying hash types?
hashID has been deprecated since March 2015, hash-identifier has been deprecated since 2011, Dagon since June 2018, and findmyhash since 2011. All of them do not have at all, or have incorrect, erroneous support for modern hashes such as Keccak/SHA3/Blake2, etc. Also, a tool like hash-identifier, which is completely interactive, has no parameters and is not convenient for use in scripts. findmyhash has a very limited set of detectable hashes. The most interesting tool is hashID (for identifying a hash), but since it hasn't been supported for over 5 years, problems and open PRs (Pull Requests) are piling up, bugs are not fixed, and some features are missing.
All this could have prompted the authors to create new tools with capabilities missing from their predecessors.
Let's look at a comparative table of tools for determining the type of hash:
| Tool | Maintained | Color | Ref. | Library | Lang | #️⃣ | 🔢 |
|---|---|---|---|---|---|---|---|
| haiti | ✅ (2019-now) | ✅ | ✅ | ✅ | 💎 | ✅ | 382 |
| hashID | ❌ (2013-2015) | ❌ | ✅ | ❌ | 🐍 | ⭕️ | 275 |
| hash-identifier | ❌ (2011-2011) | ❌ | ❌ | ❌ | 🐍 | ❌ | ~126 |
| Dagon | ❌ (2017-2018) | ⭕️ | ❌ | ❌ | 🐍 | ⭕️ | ~48 |
| findmyhash | ❌ (2011-2011) | ❌ | ❌ | ❌ | 🐍 | ❌ | ~17 |
| Name-That-Hash | ✅ (2021-now) | ✅ | ✅ | ✅ | 🐍 | ✅ | 365 |
| HashTag | ❌ (2013-2013) | ❌ | ❌ | ❌ | 🐍 | ⭕ | ~137 |
Legend:
- Ref.: showing next to the hash type the corresponding mode of hashcat and hash name of john the ripper
- ✅: function supported
- ❌: function not supported
- ⭕️: function is partially supported
- 💎: the Ruby programming language
- 🐍: the Python programming language
- #: correct support for modern hashes
- 🔢: number of hashes supported
Example hashes
If you need sample hashes for verifying instruments, see the section “Where to see examples of hashes”.
I selected several hashes for analysis:
- SHA3-224
412ef78534ba6ab0e9b1607d3e9767a25c1ea9d5e83176b4c2817a6c
- SHA3-512
7c2dc1d743735d4e069f3bda85b1b7e9172033dfdd8cd599ca094ef8570f3930c3f2c0b7afc8d6152ce4eaad6057a2ff22e71934b3a3dd0fb55a7fc84a53144e
- PKZIP Master Key
f1eff5c0368d10311dcfc419
- CRC32
c762de4a:00000000
- Keccak-512
2fbf5c9080f0a704de2e915ba8fdae6ab00bbc026b2c1c8fa07da1239381c6b7f4dfd399bf9652500da723694a4c719587dd0219cb30eabe61210a8ae4dc0b03
Hashes must be enclosed in single quotes!
Hashes can include special characters that have a special meaning to the shell. This is especially important if you are using Linux. If you do not take this into account, the program for determining the hash type, although it will not report an error, will receive a string different from the one you thought you entered.
Moreover, even in double quotes, the shell treats some characters as special. So to avoid escaping them, put the entire hash in single quotes.
It is not necessary to quote hashes consisting only of letters and numbers, but I prefer to pass all hashes in single quotes.
HAITI
HAITI (HAsh IdenTifIer) is a command line tool (and library) for identifying the type of a given hash. The library is especially good for scripting because you don't have to wrap the command line tool in a subprocess.
Features:
- 382+ hash types detected
- Modern algorithms supported (SHA3, Keccak, Blake2, etc.)
- Hashcat and John the Ripper references
- CLI tool & library
- Color output
- Hackable
A complete list of program options and installation instructions can be found in the program card: https://en.kali.tools/?p=1567
Using the program is very simple - put your hash after the program name:
haiti OPTIONS 'HASH'
Moreover, OPTIONS are not necessary, the default behavior of the program is very balanced and in most cases you will not want to change it with any additional parameters.
For example:
haiti 7c2dc1d743735d4e069f3bda85b1b7e9172033dfdd8cd599ca094ef8570f3930c3f2c0b7afc8d6152ce4eaad6057a2ff22e71934b3a3dd0fb55a7fc84a53144e
Output:
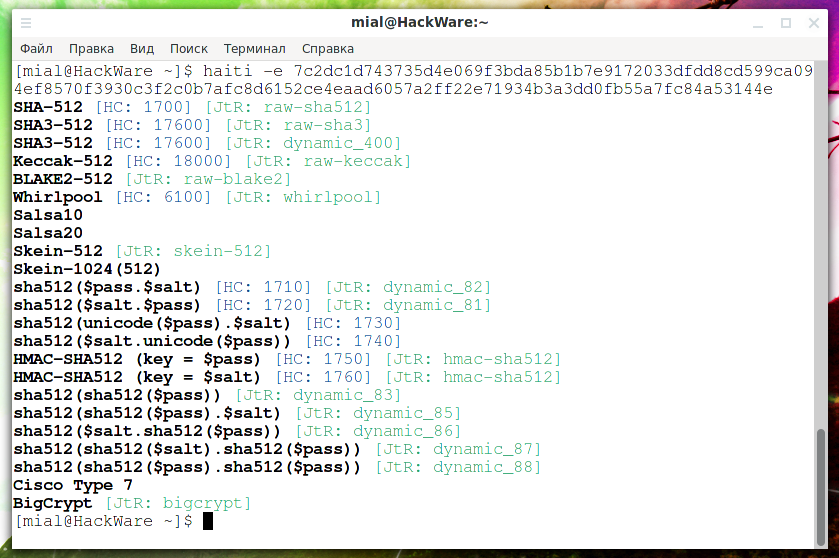
SHA-512 [HC: 1700] [JtR: raw-sha512] SHA3-512 [HC: 17600] [JtR: raw-sha3] SHA3-512 [HC: 17600] [JtR: dynamic_400] Keccak-512 [HC: 18000] [JtR: raw-keccak] BLAKE2-512 [JtR: raw-blake2] Whirlpool [HC: 6100] [JtR: whirlpool] Salsa10 Salsa20 Skein-512 [JtR: skein-512] Skein-1024(512)
Among the output is the correct answer: SHA3-512
In the output, HC is an abbreviation for Hashcat, and subsequent digits (for example, 1700, 17600, and so on) are the mode numbers in this program.
JtR is short for John the Ripper, and the following lines are the name of the hash algorithms for cracking in this program (raw-sha512, raw-sha3, and so on).
Color improves the readability of the output very well, especially if it is large. If you want to disable color output, then use the --no-color option:
haiti --no-color 412ef78534ba6ab0e9b1607d3e9767a25c1ea9d5e83176b4c2817a6c
Although often the output contains more than one guess about the hash type, salted algorithms are excluded by default. To show all possible hashing algorithms, including using a salt, use the -e or --extended option:
haiti -e 7c2dc1d743735d4e069f3bda85b1b7e9172033dfdd8cd599ca094ef8570f3930c3f2c0b7afc8d6152ce4eaad6057a2ff22e71934b3a3dd0fb55a7fc84a53144e
If you only want to know the hash type and information about hashcat and john the ripper modes is superfluous for you, then you can specify the --short option for shortened output:
haiti --short f1eff5c0368d10311dcfc419
Name-That-Hash
From January 2021, almost two years after work on HAITI began, a project called Name-That-Hash emerged because the author needed a Python library for Ciphey. There are now two relevant options for identifying a hash.
Name That Hash defines the type of hash. The program supports MD5, SHA256 and over 300 other hashes.
Features of Name That Hash:
- Popularity Ratings – You will see the most popular hashes first.
- Hash Summaries – Name-that-hash will summarize the basics of using each hash, allowing you to make an informed choice.
- The color output is contrasting and descriptive.
- Output to JSON and API – you can use Name-That-Hash in your project, since the program has an API and a command line interface. Use JSON output or import the program as a Python module!
- Updated – Name-That-Hash is a 2021 project.
- Thoughtfulness – the authors have thought over the functions, interface and options with ease of use in mind.
- Extensibility – add new hashes as quickly as you can edit the text file.
- Working with files – the program reads a file line by line and checks the type of each hash.
- Hash lookup is an extreme mode that tries to extract a hash even if the string contains garbage.
Installation instructions and a complete list of options can be found at https://en.kali.tools/?p=1556.
To determine the hash type, specify it with the -t (--text) option:
nth -t 'HASH'
For example:
nth -t '7c2dc1d743735d4e069f3bda85b1b7e9172033dfdd8cd599ca094ef8570f3930c3f2c0b7afc8d6152ce4eaad6057a2ff22e71934b3a3dd0fb55a7fc84a53144e'
Output example:
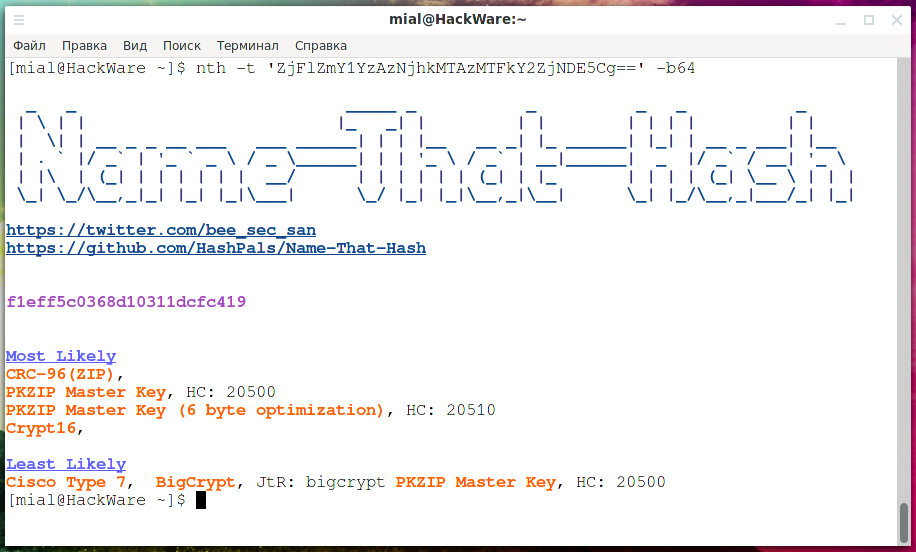
Hashes are divided into two groups:
- Most Likely
- Least Likely
Moreover, in these groups, they are also sorted by frequency of use.
In the output, you can see the already familiar HC and JtR strings with the numbers and names of hashing algorithms in Hashcat and John.
In addition, there is a short description of the application, for example:
- Summary: Used in Bitcoin Blockchain and Shadow Files.
- Summary: Used in Wireguard, Zcash, IPFS and more.
- Summary: Not considered a hash function
Moreover, please note that some entries are hyperlinks (they are underlined with dots) and for more information you can go to web pages. All this is done so that you can navigate the proposed hash types and choose the most suitable one.
To check multiple hashes, use the -f (--file) option:
nth -f 'FILE'
The file format is one hash per line.
One of these options (-t or -f) is required.
If your hashes are Base64 encoded, then use the -b64 (--base64) option. It tells the program to decode Base64 hashes before identifying. For files with mixed Base64 strings and in plain text, the program first tries to decode base64, and if this fails, then it treats the hash as an ordinary plain text string.
Example:
nth -t 'ZjFlZmY1YzAzNjhkMTAzMTFkY2ZjNDE5Cg==' -b64
Please note that the already decoded string is shown as a hash (after the header).
The -e (--extreme) option enables searching for hashes in a string. This mode will get 5d41402abc4b2a76b9719d911017c592 from ####5d41402abc4b2a76b9719d911017c592###.
In theory, the following two commands should give the same result:
nth -t '####5d41402abc4b2a76b9719d911017c592###' -e nth -t '5d41402abc4b2a76b9719d911017c592'
But they turned out differently for me. Therefore, use this mode rather as an experimental one.
Free online hash type detection
The Online hash type detection service has existed for a long time. It works very simply – you enter a hash and you get a hash type. Previously, it relied on the hashID and HashTag utilities. Now the service has been updated and works with the HAITI and Name That Hash utilities – the most up-to-date tools for determining the type of hash.
Service address: https://w-e-b.site/?act=hashtag
Conclusion
As you can see, it is difficult to choose which of the programs is better – HAITI or Name That Hash. You can use one or two. Or if you need JSON output or need API support or a library for defining hashes, then you can choose the one that best suits your needs.
Related articles:
- How to identify hash types (100%)
- Hash-generation software (55%)
- How to hack a Windows password (55%)
- How to decrypt stored Windows passwords using mimikatz and DAPA (55%)
- Comprehensive Guide to John the Ripper. Part 6: How to brute force non-standard hashes (55%)
- Comprehensive Guide to John the Ripper. Part 4: Practical examples of John the Ripper usage (RANDOM - 50%)