SMB and Samba Security Audit Tools
Table of contents
1. SMB and network folders discovering. Shares and files enumeration
1.2 SMB discovering via port scanning
1.13 Online scanners on SuIP.biz
2. Man-in-the-middle attack on SMB. Relays
2.4 Ettercap. Ettercap Plugins
3. Brute-force attack on Windows user credentials via SMB
4. SMB post-exploitation tools
5. Nmap scripts for gathering information and auditing SMB
I composed a list of programs that somehow relate to security assessment and hacking of SMB protocol and Windows shares (network folders). A successful attack on SMB network folders can disclose Windows username and password.
I divided the picked up utilities into the following groups:
- SMB and network folders discovering. Shares and files enumeration
- Man-in-the-middle attack on SMB. Relays
- Brute-force attack on Windows user credentials via SMB
- SMB post-exploitation tools
- Nmap scripts for gathering information and auditing SMB
This is a fairly arbitrary division, since some programs can be placed in two groups at once, for example, the program looks for SMB balls on the network and tries different passwords.
1. SMB and network folders discovering. Shares and files enumeration
smbclient utilities
To get these programs, install the smbclient package.
Using the smbtree utility, you can detect Windows computers with shares:
sudo smbtree -N
Using the smbclient utility, you can view the network shared folders available on the computer:
sudo smbclient -L \\ИМЯ-КОМПЬЮТЕРА -N
In addition with smbclient, using the following command, you can connect to the network folder and perform normal file operations:
sudo smbclient //ИМЯ-КОМПЬЮТЕРА/Папка -N
The previous two commands use the -N option to log in without a password. If you want to connect to a folder that requires authentication, use the -U option after which specify the username, and remove the -N option.
SMB discovering via port scanning
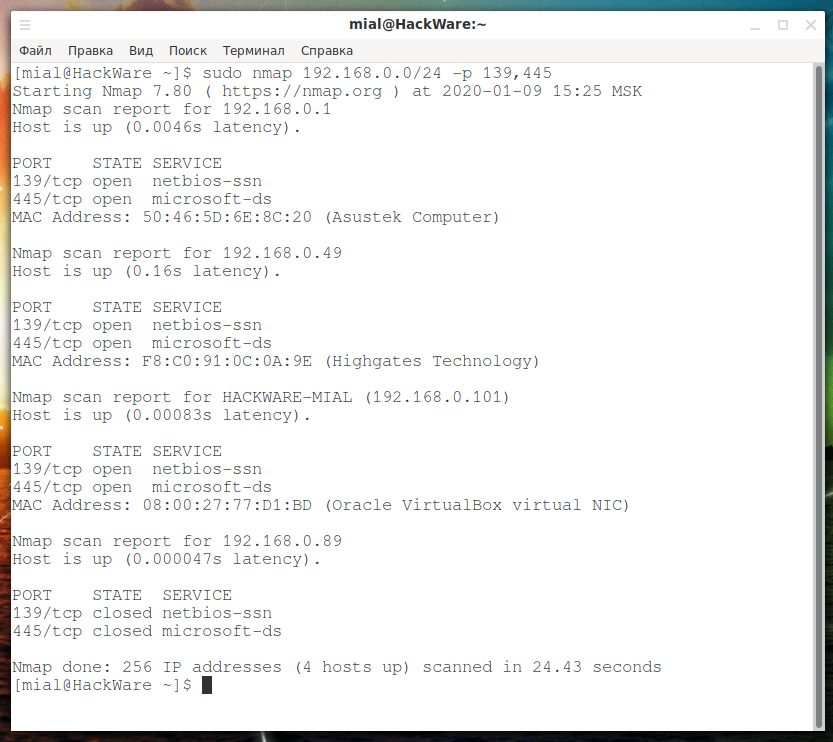
SMB uses ports 445 and 139, so computers with network shares can be searched using Nmap with a command of the form:
sudo nmap NETWORK -p 139,445
For instance:
sudo nmap 192.168.0.0/24 -p 139,445
You can add the -oG <FILE> option to save the results to a file – by the way, we will need such a file with some of the following programs:
sudo nmap 192.168.0.0/24 -p 139,445 -oG portscan445.gnmap
enum4linux
The enum4linux program uses the tools from the Samba package to collect information using Windows shared folders.
num4linux is preinstalled on Kali Linux and BlackArch.
Usage:
enum4linux [options] ip
Options:
-U get userlist
-M get machine list*
-S get sharelist
-P get password policy information
-G get group and member list
-d be detailed, applies to -U and -S
-u user specify username to use (default "")
-p pass specify password to use (default "")
The following options from enum.exe aren't implemented: -L, -N, -D, -f
Additional options:
-a Do all simple enumeration (-U -S -G -P -r -o -n -i).
This opion is enabled if you don't provide any other options.
-h Display this help message and exit
-r enumerate users via RID cycling
-R range RID ranges to enumerate (default: 500-550,1000-1050, implies -r)
-K n Keep searching RIDs until n consective RIDs don't correspond to
a username. Impies RID range ends at 999999. Useful
against DCs.
-l Get some (limited) info via LDAP 389/TCP (for DCs only)
-s file brute force guessing for share names
-k user User(s) that exists on remote system (default: administrator,guest,krbtgt,domain admins,root,bin,none)
Used to get sid with "lookupsid known_username"
Use commas to try several users: "-k admin,user1,user2"
-o Get OS information
-i Get printer information
-w wrkg Specify workgroup manually (usually found automatically)
-n Do an nmblookup (similar to nbtstat)
-v Verbose. Shows full commands being run (net, rpcclient, etc.)
Let’s consider the usage of the most interesting options. Firstly, this option is -a, which means to collect all possible information:
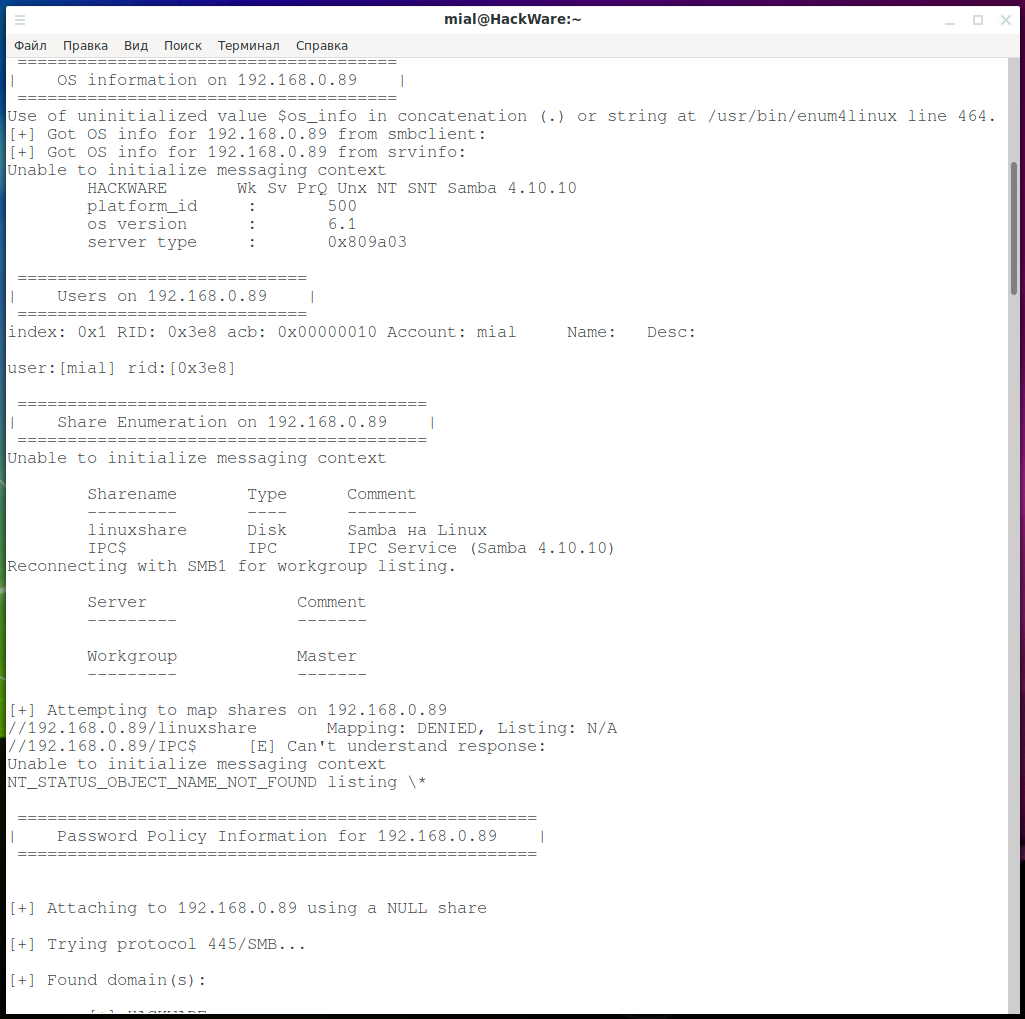
enum4linux -a 192.168.0.1
Some systems are configured to allow anonymous login, but do not allow login without a password – that is, null sessions are prohibited there. To work around this problem, it is enough to specify any username, you can omit the password. Please note that it is important to specify a username not existing on the system where the share is located, otherwise access will not be allowed due to incorrect credentials. The username can be specified with the -u option:
enum4linux -a -u anyuser 192.168.0.101
enum4linux program usually itself correctly defines the workgroup and you do not need to specify it manually. But I was faced with a situation when a host on Linux, where the network folder was configured using Samba, enum4linux could not determine the workgroup and generated a lot of errors. To force a workgroup to be specified, use the -w option:
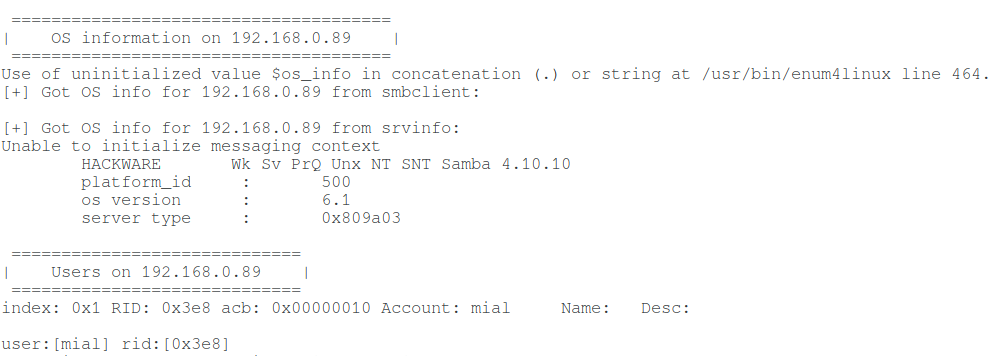
enum4linux -a -w WORKGROUP 192.168.0.89
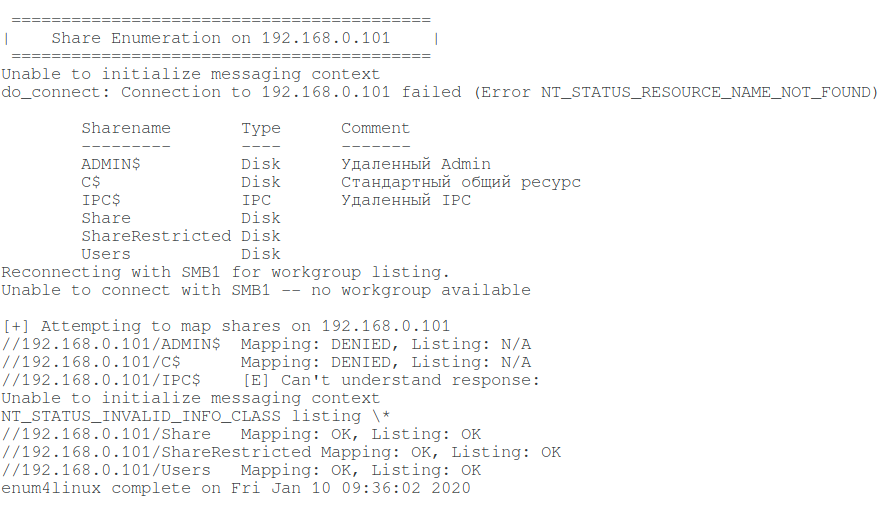
If you only want to get a list of shared folders, then specify the -S option instead of -a:
enum4linux -S -u anyuser 192.168.0.101
If you know the username and password to get access the network folder, then specify the username with the -u option, and the password with the -p option:
enum4linux -S -u ShareOverlord -p 1234 192.168.0.101
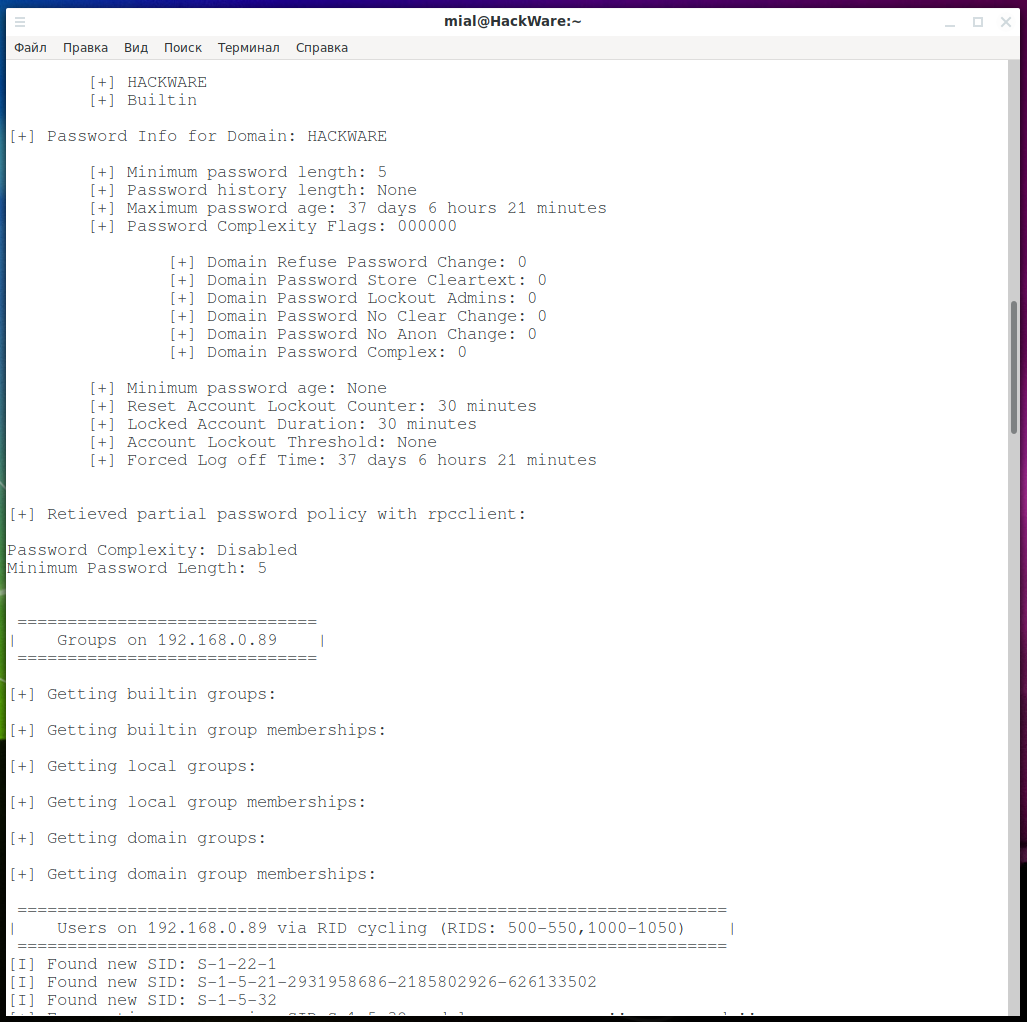
To get only a list of users, specify the -U option; for information about the operating system, use the -o option. Note that the -a option enables these options, and in total it activates the -U -S -G -P -r -o -n -i options.
enum4linux -U -o -w WORKGROUP 192.168.0.89
ACB is present in the user profile – this is an account control block.
The following values can be:
/* Allowable account control bits */ 0x00000001 /* 1 = User account disabled */ 0x00000002 /* 1 = Home directory required */ 0x00000004 /* 1 = User password not required */ 0x00000008 /* 1 = Temporary duplicate account */ 0x00000010 /* 1 = Normal user account */ 0x00000020 /* 1 = MNS logon user account */ 0x00000040 /* 1 = Interdomain trust account */ 0x00000080 /* 1 = Workstation trust account */ 0x00000100 /* 1 = Server trust account (BDC) */ 0x00000200 /* 1 = User password does not expire */ 0x00000400 /* 1 = Account auto locked */ /* only valid for > Windows 2000 */ 0x00000800 /* 1 = Text password encrypted */ 0x00001000 /* 1 = Smart Card required */ 0x00002000 /* 1 = Trusted for Delegation */ 0x00004000 /* 1 = Not delegated */ 0x00008000 /* 1 = Use DES key only */ 0x00010000 /* 1 = Preauth not required */ 0x00020000 /* 1 = Password is expired */ 0x00080000 /* 1 = No authorization data required */
The sum of the bits is used to describe the user.
My examples:
Windows Server:
- 0x00000210 for Administrator (judging by the bits, the password has not expired, normal user)
- 0x00000215 for Guest (judging by the bits, the password has not expired, normal user, locked)
Windows 10:
- 0x00000214 for MiAl (judging by the bits, normal user, no password required – indeed, an account without a password)
- 0x00000214 for Tester (judging by the bits, normal user, no password required – in fact, the password is set)
- 0x00000010 for Administrator (judging by the bits, normal user, standard administrator account)
- 0x00000215 for the Guest (judging by the bits, the password has not expired, normal user, locked)
Values without the two hundredth bit (“Password has not expired”) I have also met in Samba (this is SMB for Linux), for example, 0x00000010.
Apparently 0x00000004 (User password not required) refers to access to a network folder, not an account.
nullinux
Nullinux, using SMB, can list OS information, domain information, network shares, directories, and users. If the username and password are not specified in the command line arguments, then an anonymous login or null session is tried. Nullinux is a wrapper for Samba tools (smbclient and rpcclient) to list hosts using various techniques.
nullinux is preinstalled on BlackArch. To install nullinux on Kali Linux, run the following commands:
sudo apt install python3-pip git clone https://github.com/m8r0wn/nullinux cd nullinux sudo bash setup.sh nullinux -h
Usage:
nullinux TARGET [OPTIONS]
Options:
positional arguments:
target Target server
optional arguments:
-h, --help show this help message and exit
-v Verbose output
Authentication:
-u USERNAME, -U USERNAME
Username
-p PASSWORD, -P PASSWORD
Password
Enumeration:
-shares Enumerate shares only
-users Enumerate users only
-q, -quick Fast user enumeration
-r, -rid Perform RID cycling only
-range RID_RANGE Set Custom RID cycling range (Default: '500-550')
-T MAX_THREADS Max threads for RID cycling (Default: 15)
By default, nullinux will list users and shared folders for all specified hosts. Using the command line arguments, you can configure the enumeration process.
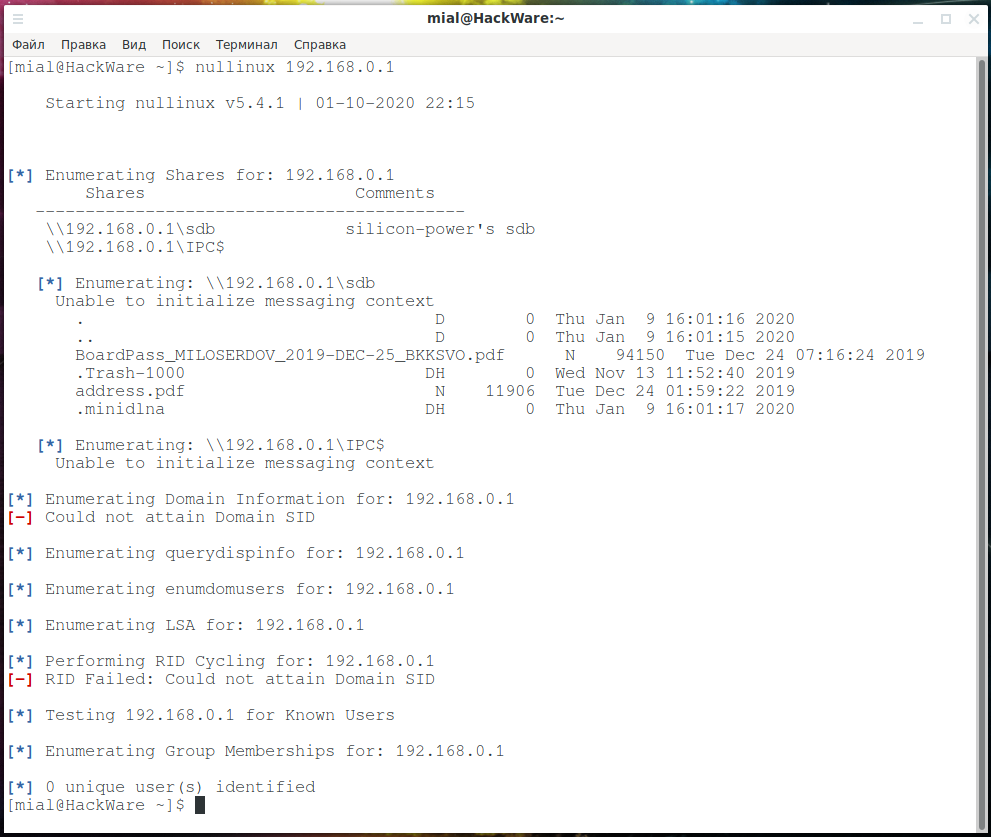
Perform an anonymous connection, a null session for the host (192.168.0.1) with SMB and get information, including network folders and users:
nullinux 192.168.0.1
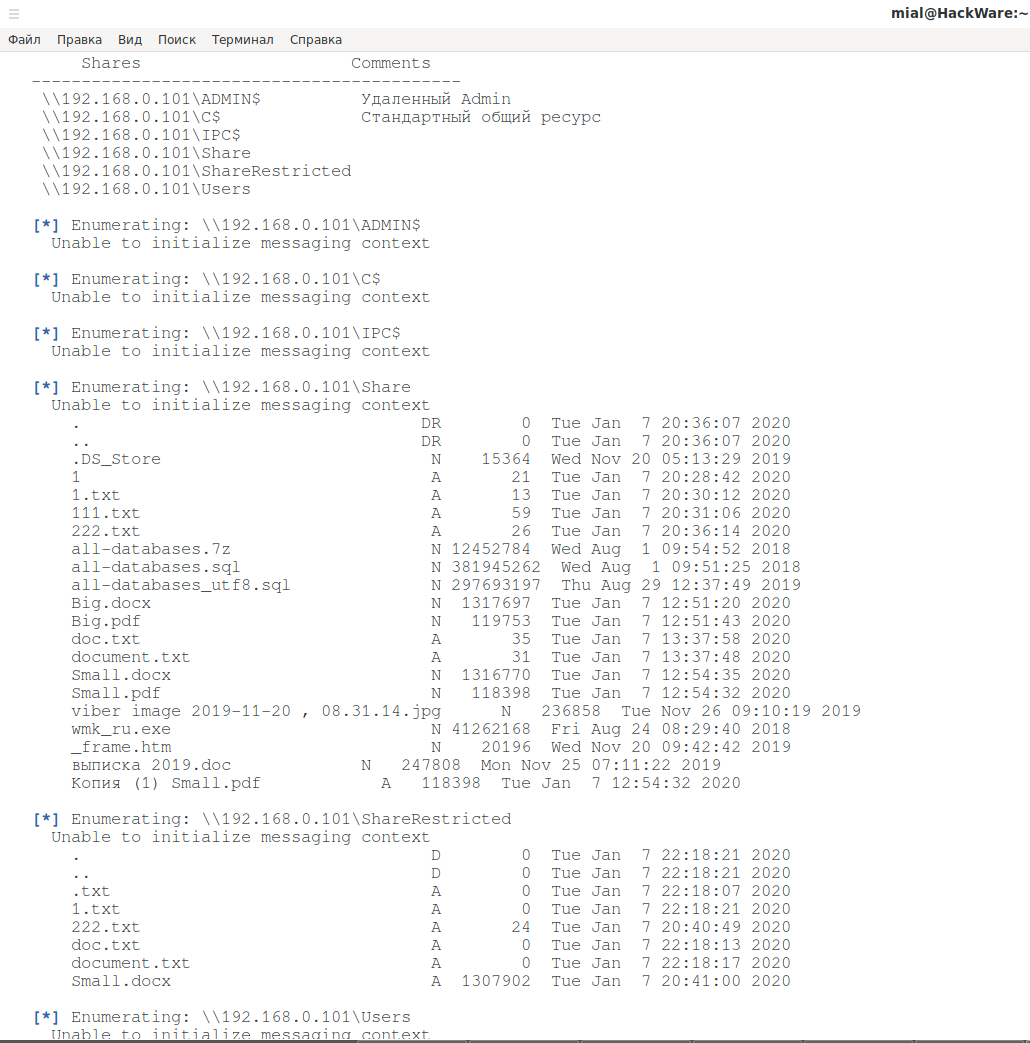
To gather information, connect to a host with a shared folder (192.168.0.101) using the known username (-U ShareOverlord) and password (-P 1234):
nullinux 192.168.0.101 -U ShareOverlord -P 1234
Get a list of shares and their contents (option -shares) for a list of hosts (192.168.0.89,192.168.0.1,192.168.0.101) using a username that does not exist on them (option -p anyuser) for anonymous login to hosts where it is impossible to log in without username:
nullinux 192.168.0.89,192.168.0.1,192.168.0.101 -shares -p anyuser
Let's look at a few more examples of using nullinux, which are described by the author of this program on wiki page.
Enumerate Multiple Hosts at Once
nullinux provides several options for enumerating users and shares from multiple hosts. Although this can be completed with other tools using a bash loop or Interlace, nullinux simplifies this process.
x=0;until [ $x -eq "3" ]; do enum4linux 192.168.1.$x; ((x++)); done
OR
nullinux 192.168.1.1,192.168.1.7
By the way, Interlace manual ‘How to speed up the scanning of numerous web sites with Interlace’.
Creates a nullinux_users.txt File
By using the command line argument “-users”, nullinux will attempt to enumerate users through all available options and display the results on screen. nullinux will compile all users collected during enumeration into a single .txt file, free of duplicates. This nullinux_users.txt file can then be used for password spraying or other internal attacks.
Nullinux can also be set to use non-invasive or lengthy techniques to enumerate users through the "-quick" option. This will perform a quick enumeration of users leaving out brute force options such as known usernames, rid cycling, and enumerating the LSA.
Multi-Threaded RID Cycling
Nullinux will perform RID cycling during the user enumeration process, or as a stand-alone technique, on the target server. This is a multi-threaded process to decrease enumeration time and add functionality to the tool.
nullinux -users 10.0.1.1 nullinux -rid -range 500-600 10.0.1.1
SMB Spider
The smbspider program displays the contents of Windows shares. The program works very quickly and, unlike other tools, it does not have problems when entering folders that do not require a password, but require any username. The program can search for files by certain phrases – this is very useful if a large number of shares (network folders) are found and you need to find a file with sensitive data on them, for example, passwords.txt files.
SMB Spider is installed on BlackArch, on Kali Linux it can be installed with the following commands:
sudo apt install python-pip python-netaddr smbclient cifs-utils ldb-tools libbsd-dev libwbclient-dev libtalloc2 libtdb-dev libtevent-dev libsmbclient-dev sudo pip2 install pysmb pysmbc git clone https://github.com/T-S-A/smbspider cd smbspider/ python2 ./smbspider.py -h
Usage:
smbspider [-h] -ip IPADDRESS -s SHARE [-f SUBFOLDER] [-pa PATTERN]
[-pf PATTERNFILE] [-u USER] [-p PWD] [-d DOMAIN]
[-r RECURSIVE] [-t THREADS]
Optional arguments:
optional arguments:
-h, --help show this help message and exit
-ip IPADDRESS, --ipaddress IPADDRESS
IP Address, IP/CIDR, IP Address File
-s SHARE, --share SHARE
SMB share to spider
-f SUBFOLDER, --subfolder SUBFOLDER
SMB subfolder to spider
-pa PATTERN, --pattern PATTERN
Keyword to search for, i.e., password
-pf PATTERNFILE, --patternfile PATTERNFILE
File of keywords to search for, i.e., password
-u USER, --user USER SMB user to connect with
-p PWD, --pwd PWD SMB password to connect with
-d DOMAIN, --domain DOMAIN
SMB domain to connect with
-r RECURSIVE, --recursive RECURSIVE
Spider subfolders. Set value for depth.
-t THREADS, --threads THREADS
Number of threads
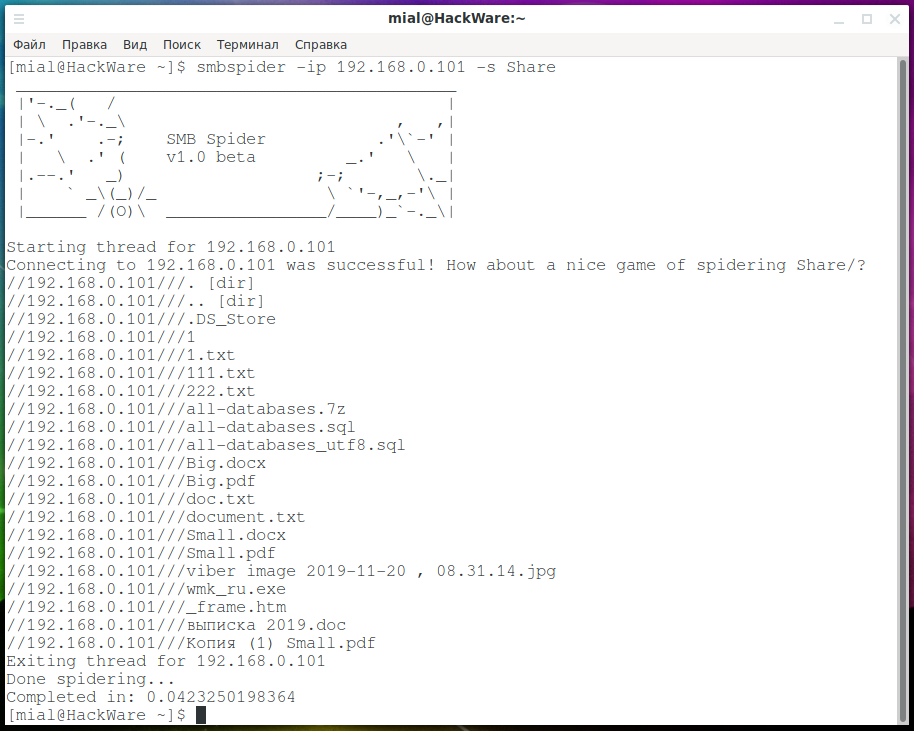
To get the contents of a network folder, specify the -s option with the name of the folder, and the host must be specified after the -ip option:
smbspider -ip 192.168.0.101 -s Share
In the previous example, a null session will be used, if you know the username and password, specify the username after the -u option and the password after -p:
smbspider -ip 192.168.0.101 -s ShareRestricted -u ShareOverlord -p 1234
acccheck
acccheck can verify the credentials of network folders. The program supports working with lists of usernames and passwords, that is, it can be used for brute-force. Also, the program can work with a list of hosts, but it runs too long during my tests.
Like some other tools, this is wrap for ‘smbclient’ binary.
The acccheck program is available on Kali Linux; it can be installed on any other distribution using the following commands:
wget https://labs.portcullis.co.uk/download/acccheck-0-2-1.tar.gz tar xf acccheck-0-2-1.tar.gz rm acccheck-0-2-1.tar.gz cd acccheck-0-2-1/ ./acccheck.pl -h
Usage:
acccheck [options]
Mandatory is one of the following options:
-t [single host IP address] -T [file containing target ip address(es)]
Another options:
-p [single password] -P [file containing passwords] -u [single user] -U [file containing usernames] -v [verbose mode]
This program can be used both for checking credentials on one host, and for checking many hosts whether the username and password for accessing the network folders are suitable for them.
Example of checking credentials on a single host:
./acccheck.pl -t 192.168.0.101 -u ShareOverlord -p 1234
To mass check if the existing SMB credentials are suitable for some host on the network, first create a file with a list of hosts:
echo -e 192.168.0.{0..255}"\n" | sed 's/ //' > ~/test/hosts.txt
And the next command starts scanning the network shares and brute-force credentials for the entire local network:
./acccheck.pl -T ~/test/hosts.txt -U ~/test/logins.txt -P ~/test/passwords.txt
In Kali Linux, use the acccehck executable name instead of ./acccheck.pl, for example:
acccehck -t 192.168.0.101 -U logins.txt -P passwords.txt
If End of Scan is displayed, for example:
./acccheck.pl -t 192.168.0.101 -u ShareOverlord -p 12345 End of Scan
So a computer with SMB was found, but valid credentials were not found.
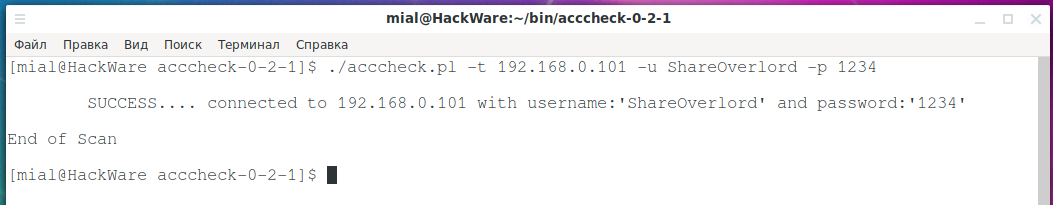
If the credentials is valid, then the output is approximately the following:
./acccheck.pl -t 192.168.0.101 -u ShareOverlord -p 1234
SUCCESS.... connected to 192.168.0.101 with username:'ShareOverlord' and password:'1234'
End of Scan
Credninja
[COMING SOON]
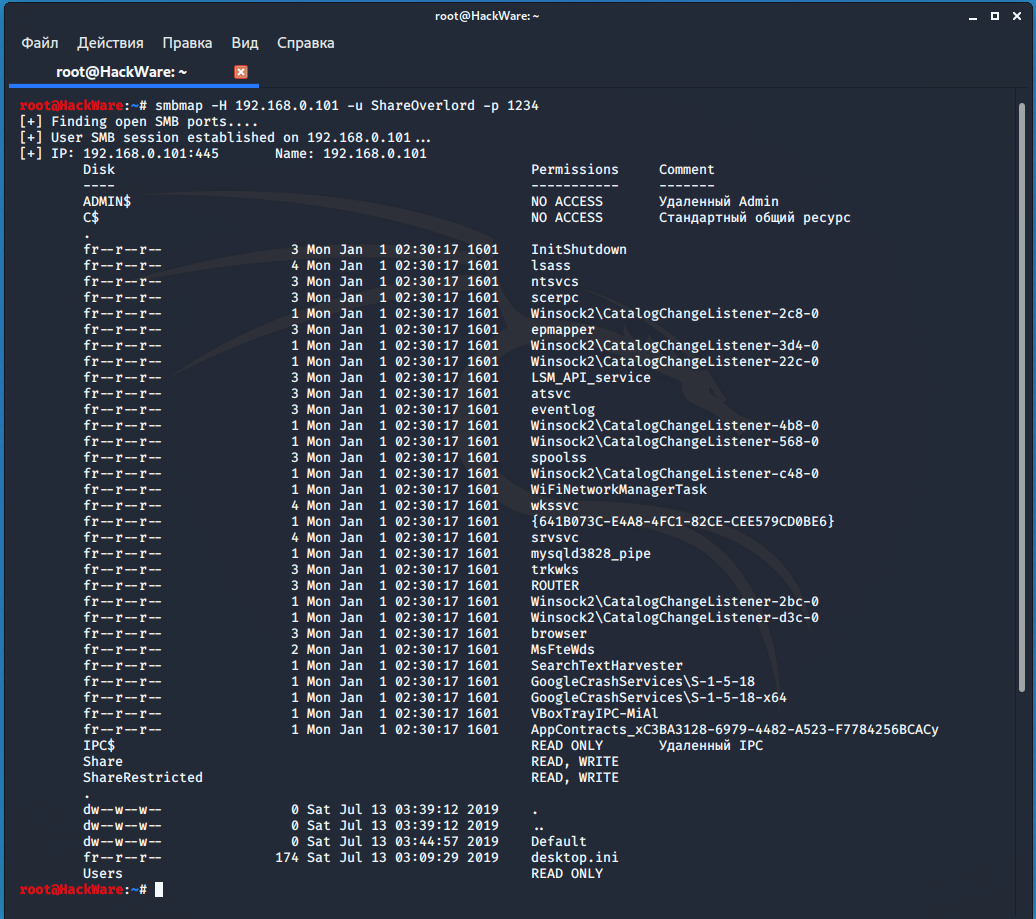
SMBMap
SMBMap allows users to enumerate samba share drives across an entire domain. List share drives, drive permissions, share contents, upload/download functionality, file name auto-download pattern matching, and even execute remote commands. This tool was designed with pen testing in mind, and is intended to simplify searching for potentially sensitive data across large networks.
SMBMap is preinstalled on Kali Linux and BlackArch.
Usage:
smbmap [-h] (-H HOST | --host-file FILE) [-u USERNAME] [-p PASSWORD] [-s SHARE] [-d DOMAIN] [-P PORT] [-v] [-x COMMAND] [--mode CMDMODE] [-L | -R [PATH] | -r [PATH]]
[-A PATTERN | -g] [--dir-only] [-q] [--depth DEPTH] [-F PATTERN] [--search-path PATH] [--download PATH] [--upload SRC DST] [--delete PATH TO FILE] [--skip]
Options:
optional arguments:
-h, --help show this help message and exit
Main arguments:
-H HOST IP of host
--host-file FILE File containing a list of hosts
-u USERNAME Username, if omitted null session assumed
-p PASSWORD Password or NTLM hash
-s SHARE Specify a share (default C$), ex 'C$'
-d DOMAIN Domain name (default WORKGROUP)
-P PORT SMB port (default 445)
-v Return the OS version of the remote host
Command Execution:
Options for executing commands on the specified host
-x COMMAND Execute a command ex. 'ipconfig /all'
--mode CMDMODE Set the execution method, wmi or psexec, default wmi
Shard drive Search:
Options for searching/enumerating the share of the specified host(s)
-L List all drives on the specified host
-R [PATH] Recursively list dirs, and files (no share\path lists ALL shares), ex. 'C$\Finance'
-r [PATH] List contents of directory, default is to list root of all shares, ex. -r 'C$\Documents and Settings\Administrator\Documents'
-A PATTERN Define a file name pattern (regex) that auto downloads a file on a match (requires -R or -r), not case sensitive, ex '(web|global).(asax|config)'
-g Make the output grep friendly, used with -r or -R (otherwise it outputs nothing)
--dir-only List only directories, ommit files.
-q Quiet verbose output. Only shows shares you have READ or WRITE on, and suppresses file listing when performing a search (-A).
--depth DEPTH Traverse a directory tree to a specific depth
File Content Search:
Options for searching the content of files
-F PATTERN File content search, -F '[Pp]assword' (requires admin access to execute commands, and PowerShell on victim host)
--search-path PATH Specify drive/path to search (used with -F, default C:\Users), ex 'D:\HR\'
Filesystem interaction:
Options for interacting with the specified host's filesystem
--download PATH Download a file from the remote system, ex.'C$\temp\passwords.txt'
--upload SRC DST Upload a file to the remote system ex. '/tmp/payload.exe C$\temp\payload.exe'
--delete PATH TO FILE
Delete a remote file, ex. 'C$\temp\msf.exe'
--skip Skip delete file confirmation prompt
SMBMap usage example:
smbmap -H 192.168.0.101 -u ShareOverlord -p 1234
If you specify the -v option, information about the host operating system with a network folder will be displayed:
smbmap -H 192.168.0.101 -u ShareOverlord -p 1234 -v
SPARTA
SPARTA is a Python-based graphical user interface (GUI) application that simplifies penetration testing of network infrastructure, assisting the penetration tester in the scanning and enumeration phase. It allows you to save time for the tester thanks to a simple graphical interface and the output of the received information in a readable form. The less time is spent on typing commands and tuning instruments, the more time can be spent focusing on analyzing the results.
Among others features, the program perform security auditing of SMB and brute-force SMB.
SMBCrunch
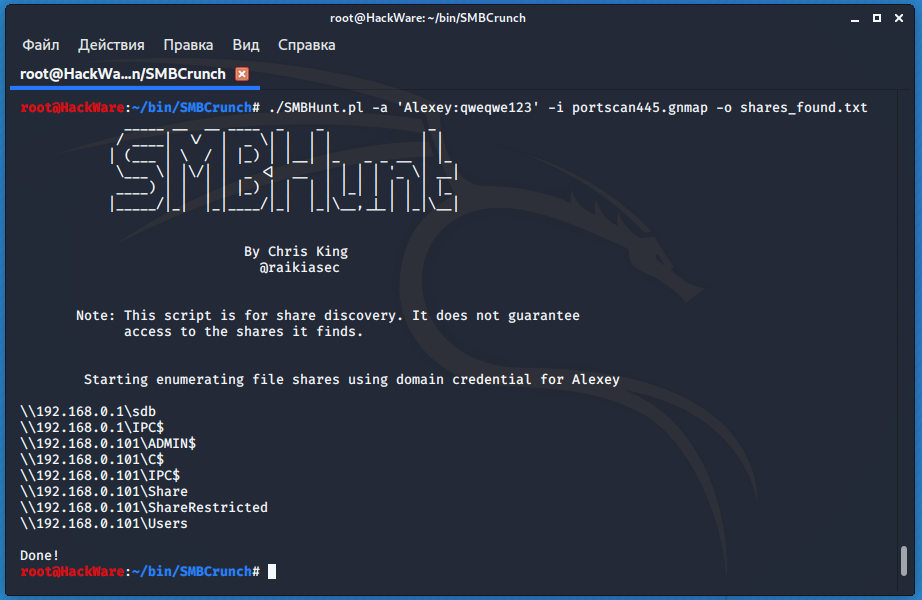
SMBCrunch is 3 tools that work together to gather information about Windows file shares (network folders). Tool Names:
- SMBHunt – searches for computers with network folders and lists shares
- SMBList – composes file lists of specified network folders based on the file generated by SMBHunt
- SMBGrab – grabs files from network folders based on the file generated by the SMBList program. Searching and filtering data can be done with grep.
These scripts can be used separately, but it is more convenient to use them one after another, transferring the generated files from one program to another.
SMBCrunch is preinstalled on BlackArch, to install on Kali Linux run:
git clone https://github.com/Raikia/SMBCrunch cd SMBCrunch/ ./SMBHunt.pl -h
There are two required options for SMBHunt.pl. The first is -i, after which you need to specify either the host, or the file with the list of hosts, or the file with the Nmap scan results. The second required option is -a, after it you must specify either a file with user credentials, or one pair of credentials. The username and password must be divided by a colon; if they are specified in the file, then one pair per line. After the -o option, you can specify a file to save data:
An example of connecting to a specific host:
./SMBHunt.pl -a 'Alexey:qweqwe123' -i 192.168.0.101 -o shares_found.txt
And this is an example of preliminary scanning and gathering information from all hosts on which the open port 445 is found:
sudo nmap 192.168.0.0/24 -p 139,445 -oG portscan445.gnmap ./SMBHunt.pl -a 'Alexey:qweqwe123' -i portscan445.gnmap -o shares_found.txt
The program SMBList.pl also has two required options. After the -c option, you need to specify a username and password, or a file with credentials. After the -s option, specify the file that was generated by the previous program. After the -o option, you can specify the name of the directory where the compiled lists of files on network folders will be saved:
./SMBList.pl -c 'Alexey:qweqwe123' -s shares_found.txt -o share_listing -m 150
A complete list of all files in network folders is collected in the file share_listing/ALL_COMBINED_RESULTS.txt, and separate files for each network folder are compiled.
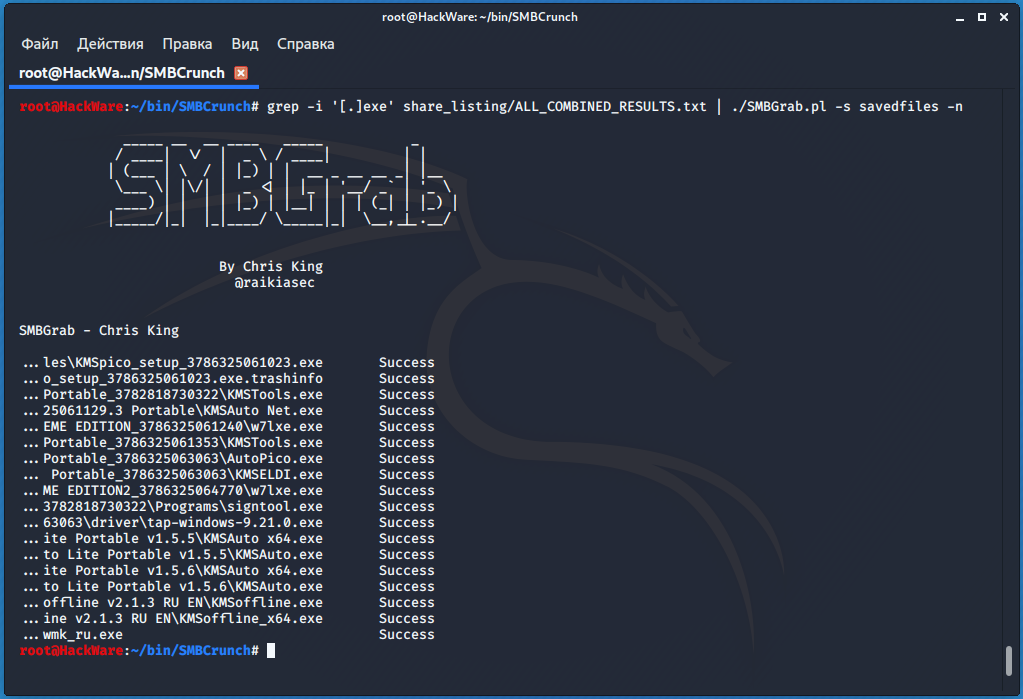
The SMBGrab.pl script accepts a list of files not through an option, but through standard input. Thanks to this approach, grep can filter the files you need to download.
In the following example, only lines containing 'password.txt' will be found in the file share_listing/ALL_COMBINED_RESULTS.txt, these lines will be piped to the SMBGrab.pl program and it will save them to the savedfiles directory:
grep -i 'password.txt' share_listing/ALL_COMBINED_RESULTS.txt | ./SMBGrab.pl -s savedfiles
Please note that by default, SMBGrab.pl adds information about this file (download, creation timestamps, etc.) to each file. And it adds to any files – including binary ones. To keep the files in their original form, specify the -n option. An example of a command in which .exe files are downloaded and saved in their original form:
grep -i '[.]exe' share_listing/ALL_COMBINED_RESULTS.txt | ./SMBGrab.pl -s savedfiles -n
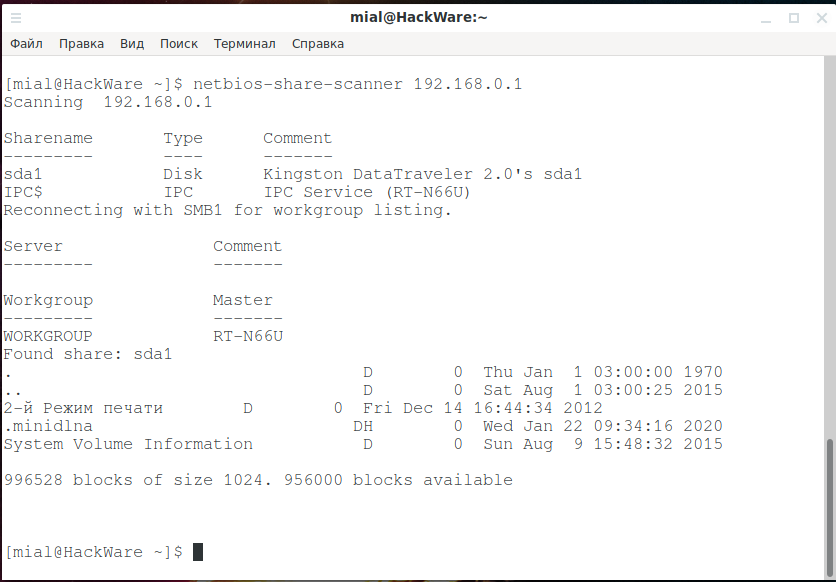
NetBIOS Share Scanner
NetBIOS Share Scanner can be used to check Windows workstations and servers if they have available shared resources.
Launch Example:
netbios-share-scanner 192.168.0.1
Installation manual, as well as additional examples of use: https://en.kali.tools/?p=1729
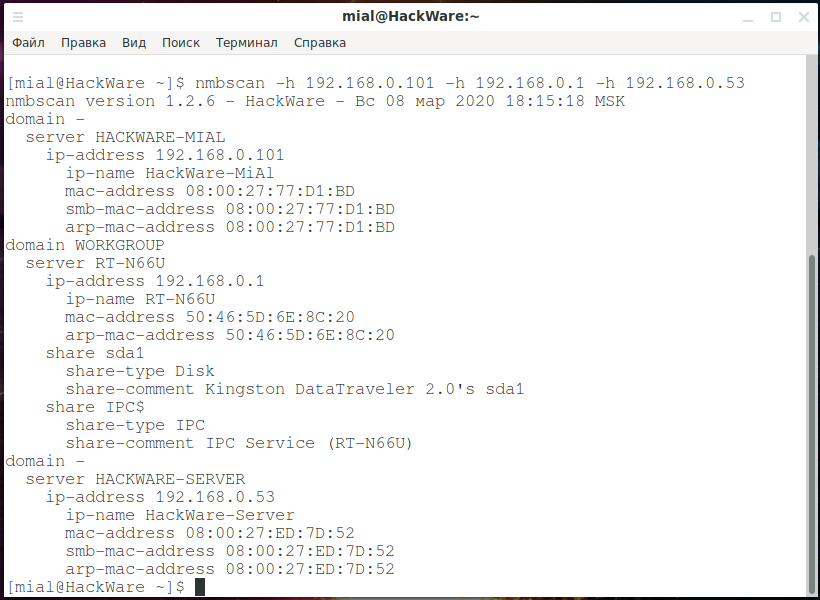
NMBscan
NMBscan scans the shares of a SMB/NetBIOS network, using the NMB/SMB/NetBIOS protocols. It is useful for acquiring information on a local area network for such purposes as security auditing.
It can obtain such information as NMB/SMB/NetBIOS/Windows hostname, IP address, IP hostname, ethernet MAC address, Windows username, NMB/SMB/NetBIOS/Windows domain name, and master browser.
It can discover all the NMB/SMB/NetBIOS/Windows hosts on a local area network by using the hosts lists maintained by master browsers.
Installation manual: https://en.kali.tools/?p=1736
Launch Example:
nmbscan -h 192.168.0.101 -h 192.168.0.1 -h 192.168.0.53
To scan a subnet (very slow):
nmbscan -h 192.168.0.{1..255}
Online scanners on SuIP.biz
The NetBIOS, SMB (NetBIOS) and Samba (Linux) online scanner uses a number of the tools described above to collect primary information on NetBIOS and SMB (Samba). It is enough to specify the IP address of the target and several tools will start scanning at once, which will show the version of running services, the computer name and workgroup (domain), try to perform an anonymous login and show shared folders if they are available.



2. Man-in-the-middle attack on SMB. Relays
Responder
Responder is a tool for performing a man-in-the-middle attack against authentication methods in Windows. This program includes the LLMNR, NBT-NS and MDNS poisoner to redirect requests and authentication hashes traffic. The program also includes HTTP/SMB/MSSQL/FTP/LDAP authentication rogue servers that support authentication methods such as NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and basic HTTP authentication, for which the Responder acts as a relay.
That is, the Responder intercepts usernames and authentication hashes on the network with Windows computers. After breaking the hash, the user password is revealed.
To launch an attack, you need to run a command of the form:
sudo responder -I INTERFACE -rPvf
Where instead of the word INTERFACE you need to specify the name of the network interface in your system on which you want to carry out the attack.
For more details, as well as a way to crack authentication hashes, see the article “Windows Network Authentication Hacking”.
Inveigh
[COMING SOON…]
Intercepter-ng
Intercepter-NG is a multifunctional network toolkit for IT professionals of various types. The main goal is to restore interesting data from the network stream and perform various kinds of man-in-the-middle attacks (MiTM). In addition, the program allows you to detect ARP spoofing (can be used to detect MiTM), identify and exploit some types of vulnerabilities, brute-force login credentials for network services. The program can work both with live traffic flow and analyze files with captured traffic to detect files and credentials.
SMB related features:
- Reconstructing files from SMB
- SMB relay
- SMB Hijack (interception)
Ettercap. Ettercap Plugins
Ettercap is a comprehensive man-in-the-middle (MiTM) attack kit. It is able to sniff live connections, filter on the fly the contents of the transmitted data and many other tricks. It supports active and passive tampering of many protocols and includes many functions for network and host analysis.
Among the Ettercap plugins, there are two plugins aimed at attacking the SMB protocol.
smb_clear
It forces the client to send smb password in clear text distorting protocol negotiations. You must be in the middle of the connection to use it successfully. It hooks the smb dissector, so you will keep it active. If you use it against a Windows client, then the result is unlikely to be successful. Try it against *nix smbclient.
smb_down
It forces the client not to use NTLM2 password exchange during smb authentication. Thus, hashes are obtained that can easily be cracked in LC4. You must be in the middle of the connection to use it successfully. It hooks the smb dissector, so you will keep it active.
MITMf
MITMf is a framework for Man-In-The-Middle attacks. This tool is based on sergio-proxy and is an attempt to revive and update this project.
SMB related modules:
SMBTrap : Exploits the 'SMB Trap' vulnerability on a connected client SMBAuth : Invokes an SMB authentication prompt
Netcreds
Net-Creds carefully sniffs passwords and hashes from the interface or from the pcap file. Combines fragmented packets and does not rely on ports to identify the service. It supports SMB protocol.
3. Brute-force attack on Windows user credentials via SMB
patator
The patator program is designed for brute-force credentials and is one of the most flexible to configure.
For online brute-force login and user password to access the network shared folder (and therefore the Windows user credentials), run a command of the form:
./patator.py smb_login host=192.168.0.101 user=FILE0 password=FILE1 0=/root/logins.txt 1=/root/passwords.txt -x ignore:fgrep='STATUS_LOGON_FAILURE'
In this command:
- ./patator.py is the name of the executable file, depending on the installation method it may be patator
- smb_login is SMB brute force module
- host=192.168.0.101 is IP address of the computer with SMB. You can specify a file with hosts (more precisely, the file placeholder number)
- user=FILE0 is username for brute force. Instead of a name, a placeholder with a pointer to file number 0
- password=FILE1 is password for brute force. Instead of a single password, a placeholder is written with a pointer to the file number 1
- 0=/root/logins.txt is path to file number 0
- 1=/root/passwords.txt is path to file number 1
- -x ignore:fgrep='STATUS_LOGON_FAILURE' means do not display attempts, in response to which the line STATUS_LOGON_FAILURE was received
Result:
That is, two pairs of credentials were found:
- ShareOverlord:1234
- Alexey:qweqwe123
Obtained computer name and version of Windows:
- \HACKWARE-MIAL (Windows 10.0 Build 18362)
Another account was found for which the message STATUS_ACCOUNT_RESTRICTION was received:
- mial:
The message said that there are account restrictions for the mial user. The reason is that the username and password are correct (empty password), but users without a password are not allowed on this computer.
Hydra
The hydra program supports a huge number of services, thanks to its speed and reliability, it has earned well-deserved appreciation among penetration testers.
Example command to start the brute force SMB:
hydra smb://192.168.0.101 -L /root/logins.txt -P /root/passwords.txt
To say true, I did not succeed due to an error:
[ERROR] invalid reply from target smb://192.168.0.101:445/
Medusa
Medusa is a fast, parallel, and modular login brute-forcer. The goal is to support as many services on which remote authentication as possible.
Example command launch:
medusa -M smbnt -h 192.168.0.101 -U /root/logins.txt -P /root/passwords.txt
I got an error:
ERROR: SMB Protocol Negotiation Failed with host: 192.168.0.101
The reason for it, most likely, is that on the host where I want to brute-force the username and password of Windows users, support for the SMB 1 protocol is disabled. In Medusa, you can specify the authentication method:
medusa -M smbnt -h 192.168.0.101 -U /root/logins.txt -P /root/passwords.txt -m AUTH:NTLMv2
In this case, another error occurs:
FATAL: NTLMv2 support currently disabled. The default authentication mode of LMv2 should work in all cases that NTLMv2 is required.
The essence of the message is that NTLMv2 is disabled, and LMv2 should be enough for us.
APT2
APT2 is a suite of tools for automated penetration testing.
Modules for SMB security audit:
+--------------------------------+--------+------+-----------------------------------------------------------------------------+ | Module | Type | Safe | Description | +--------------------------------+--------+------+-----------------------------------------------------------------------------+ | exploit_hydrasmbpassword | action | 2 | Attempt to bruteforce SMB passwords | | scan_msf_smbuserenum | action | 5 | Get List of Users From SMB | | scan_msf_snmpenumshares | action | 5 | Enumerate SMB Shares via LanManager OID Values | | scan_nmap_smbshares | action | 5 | NMap SMB Share Scan | | scan_nmap_smbsigning | action | 5 | NMap SMB-Signing Scan | | scan_rpcclient_userenum | action | 5 | Get List of Users From SMB | | scan_searchsmbshare | action | 4 | Search files on SMB Shares | | scan_smbclient_nullsession | action | 5 | Test for NULL Session | +--------------------------------+--------+------+-----------------------------------------------------------------------------+
BruteSpray
BruteSpray accepts the results of nmap GNMAP/XML scans and, using Medusa, automatically brute-force services using dictionaries with standard logins and passwords. BruteSpray can even find non-standard ports using the -sV option inside Nmap.
[COMING SOON…]
4. SMB post-exploitation tools
CrackMapExec is an all-in-one tool for testing the Windows/Active Directory environment. It is inspired/based on previous developments, including, as a submodule, it includes the PowerSploit repository.
The program can enumerate logged-in users and index SMB shared folders, perform psexec-style attacks, automatic Mimikatz/Shellcode/DLL injections into memory using Powershell, dumping NTDS.dit and more!
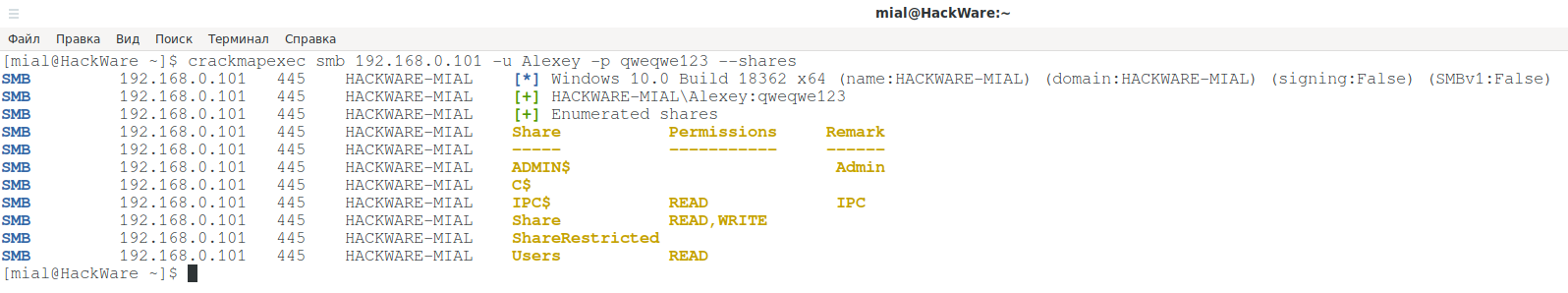
An example of listing shared folders:
crackmapexec smb 192.168.0.101 -u Alexey -p qweqwe123 --shares
keimpx
It can be used to quickly check for valid credentials across a network over SMB. Credentials can be:
- Combination of user / plain-text password.
- Combination of user / NTLM hash.
- Combination of user / NTLM logon session token.
If any valid credentials are discovered across the network after its attack phase, the user is asked to choose which host to connect to and which valid credentials to use. They will then be provided with an interactive SMB shell where the user can:
- Spawn an interactive command prompt.
- Navigate through the remote SMB shares: list, upload, download files, create, remove files, etc.
- Deploy and undeploy their own services, for instance, a backdoor listening on a TCP port for incoming connections.
- List users details, domains and password policy.
Scan the subnet (-t 192.168.0.0/24) by checking the validity of the username (-U Alexey) and password (-P qweqwe123) for all hosts with shares:
python3 ./keimpx.py -t 192.168.0.0/24 -U Alexey -P qweqwe123
Connect to the remote host (-t 192.168.0.101) using the username (-U Alexey) and password (-P qweqwe123):
python3 ./keimpx.py -t 192.168.0.101 -U Alexey -P qweqwe123
As a result, the specified credentials will be checked for correctness. If they are correct, you will be prompted to connect and open an interactive shell to interact with the remote system.
Pupy
Pupy is an open source tool for remote administration and subsequent operation (post-exploitation), working on various platforms (Windows, Linux, OSX, Android).
SMB Modules:
CATEGORY NAME HELP ----------------------------------------------------------------------------------------------------- admin shares List Local And Remote Shared Folder And Permission admin smbspider Walk Through A Smb Directory And Recursively Search A String Into Files admin smb Copy Files Via Smb Protocol admin psexec Launch Remote Commands Using Smbexec Or Wmiexec
5. Nmap scripts for gathering information and auditing SMB
There are quite a few Nmap scripts for SMB analysis or information gathering. Usually they are quite specific (for example, checking for a specific vulnerability or for infection with a specific backdoor) and/or outdated. Nevertheless, some scripts provide unique information, for example, versions of SMB dialects supported by a computer with network folders. Another reason to get acquainted with NSE (Nmap scripts) is that among real servers there are quite old ones.
The script name is specified after the --script option. Moreover, you can engage all SMB scripts, because the names support wildcards:
sudo nmap --script "smb-*" HOST
But the completion of the previous command never happened for me… Therefore, I specify one script at a time.
Each time the script is run, Nmap scans the ports: unless otherwise specified by the options, the 1000 most common ports are checked. This can be time consuming, especially when sequentially checking with several scripts. Without port scanning scripts will not work, that is, you cannot specify the -sn option. But the scanning time can be reduced if you specify only one port – TCP port 445, which is bind by SMB.
Examples of gathering information about SMB using Nmap scripts.
I tested on 4 different systems: two Windows 10 computers with different settings (with permission to enter with and without password; with SMB 1 support and without), one Linux system with Samba and one router with Samba. Only a few scripts worked for me – they are all listed below. However, you may be more fortunate and find older machines where scripts come in handy, so the following is a complete table of Nmap scripts related to SMB.
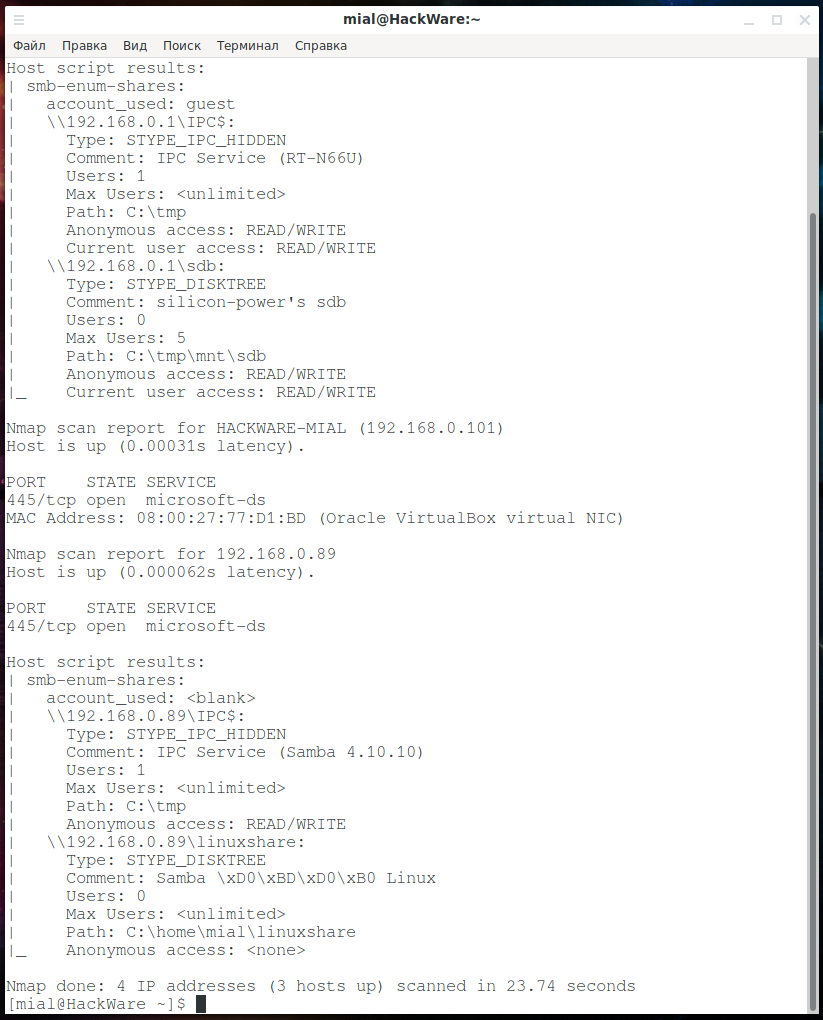
smb-enum-shares. Listing network folders on a host:
sudo nmap -p 445 --script smb-enum-shares 192.168.0.1 192.168.0.101 192.168.0.49 192.168.0.89
smb-protocols. Getting information about supported protocols:
sudo nmap -p 445 --script smb-protocols 192.168.0.1 192.168.0.101 192.168.0.49 192.168.0.89
smb2-capabilities. Checking the capabilities of the SMB 2 protocol:
sudo nmap -p 445 --script smb2-capabilities 192.168.0.1 192.168.0.101 192.168.0.49 192.168.0.89
smb2-security-mode. Security Mode Settings:
sudo nmap -p 445 --script smb2-security-mode 192.168.0.1 192.168.0.101 192.168.0.49 192.168.0.89
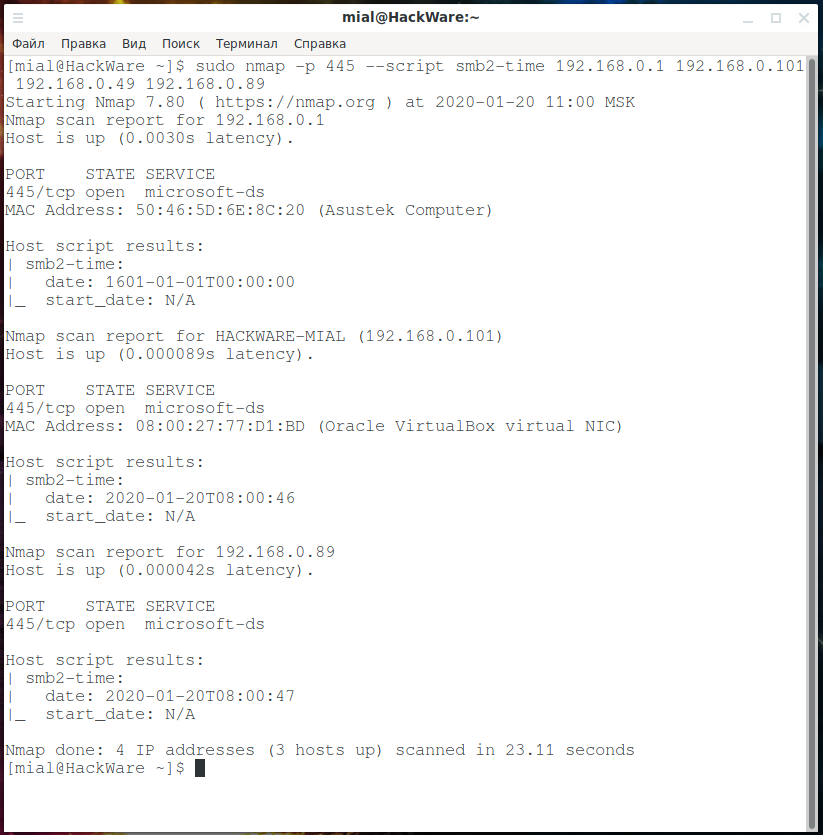
smb2-time. Getting time via SMB:
sudo nmap -p 445 --script smb2-time 192.168.0.1 192.168.0.101 192.168.0.49 192.168.0.89
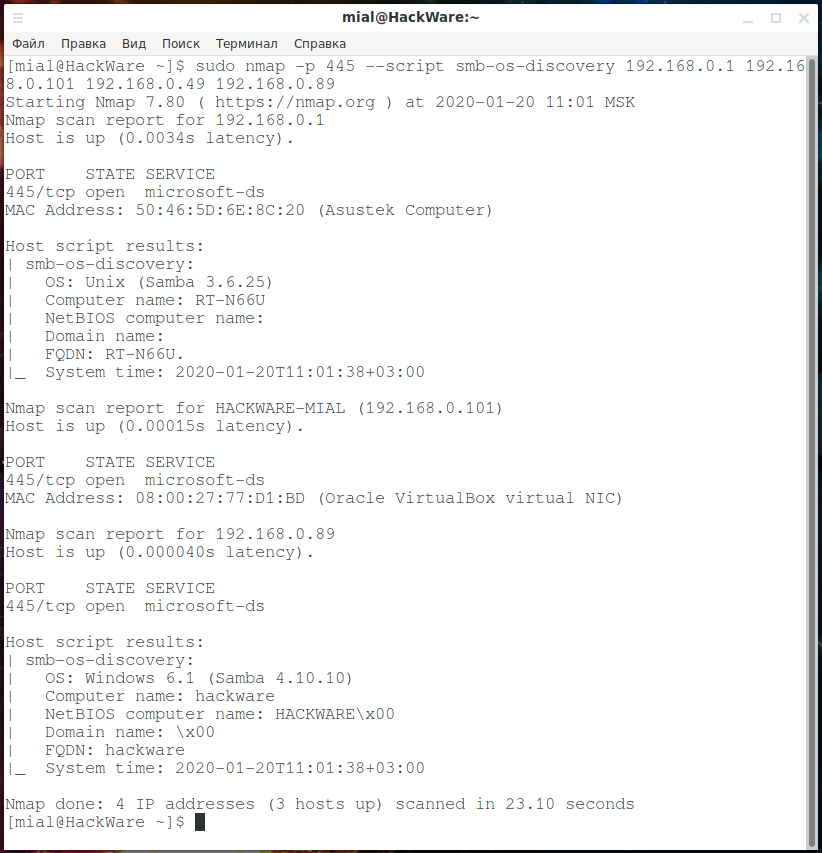
smb-os-discovery. Operating System Information:
sudo nmap -p 445 --script smb-os-discovery 192.168.0.1 192.168.0.101 192.168.0.49 192.168.0.89
Arguments can be passed to some scripts (see the details for each specific script), the --script-args option is used for this, for example: --script-args='smbusername=Alexey,smbpassword=qweqwe123'
Below is a table with all Nmap scripts (NSE) for checking or gathering information about SMB.
| Script Name | Description |
|---|---|
| smb-brute |
Attempts to guess username/password combinations over SMB, storing discovered combinations for use in other scripts. Every attempt will be made to get a valid list of users and to verify each username before actually using them. When a username is discovered, besides being printed, it is also saved in the Nmap registry so other Nmap scripts can use it. That means that if you're going to run |
| smb-double-pulsar-backdoor |
Checks if the target machine is running the Double Pulsar SMB backdoor. |
| smb-enum-domains |
Attempts to enumerate domains on a system, along with their policies. This generally requires credentials, except against Windows 2000. In addition to the actual domain, the "Builtin" domain is generally displayed. Windows returns this in the list of domains, but its policies don't appear to be used anywhere. |
| smb-enum-groups |
Obtains a list of groups from the remote Windows system, as well as a list of the group's users. This works similarly to |
| smb-enum-processes |
Pulls a list of processes from the remote server over SMB. This will determine all running processes, their process IDs, and their parent processes. It is done by querying the remote registry service, which is disabled by default on Vista; on all other Windows versions, it requires Administrator privileges. |
| smb-enum-services |
Retrieves the list of services running on a remote Windows system. Each service attribute contains service name, display name and service status of each service. |
| smb-enum-sessions |
Enumerates the users logged into a system either locally or through an SMB share. The local users can be logged on either physically on the machine, or through a terminal services session. Connections to a SMB share are, for example, people connected to fileshares or making RPC calls. Nmap's connection will also show up, and is generally identified by the one that connected "0 seconds ago". |
| smb-enum-shares |
Attempts to list shares using the |
| smb-enum-users |
Attempts to enumerate the users on a remote Windows system, with as much information as possible, through two different techniques (both over MSRPC, which uses port 445 or 139; see |
| smb-flood |
Exhausts a remote SMB server's connection limit by by opening as many connections as we can. Most implementations of SMB have a hard global limit of 11 connections for user accounts and 10 connections for anonymous. Once that limit is reached, further connections are denied. This script exploits that limit by taking up all the connections and holding them. |
| smb-ls |
Attempts to retrieve useful information about files shared on SMB volumes. The output is intended to resemble the output of the UNIX |
| smb-mbenum |
Queries information managed by the Windows Master Browser. |
| smb-os-discovery |
Attempts to determine the operating system, computer name, domain, workgroup, and current time over the SMB protocol (ports 445 or 139). This is done by starting a session with the anonymous account (or with a proper user account, if one is given; it likely doesn't make a difference); in response to a session starting, the server will send back all this information. |
| smb-print-text |
Attempts to print text on a shared printer by calling Print Spooler Service RPC functions. |
| smb-protocols |
Attempts to list the supported protocols and dialects of a SMB server. |
| smb-psexec |
Implements remote process execution similar to the Sysinternals' psexec tool, allowing a user to run a series of programs on a remote machine and read the output. This is great for gathering information about servers, running the same tool on a range of system, or even installing a backdoor on a collection of computers. |
| smb-security-mode |
Returns information about the SMB security level determined by SMB. |
| smb-server-stats |
Attempts to grab the server's statistics over SMB and MSRPC, which uses TCP ports 445 or 139. |
| smb-system-info |
Pulls back information about the remote system from the registry. Getting all of the information requires an administrative account, although a user account will still get a lot of it. Guest probably won't get any, nor will anonymous. This goes for all operating systems, including Windows 2000. |
| smb-vuln-conficker |
Detects Microsoft Windows systems infected by the Conficker worm. This check is dangerous and it may crash systems. |
| smb-vuln-cve-2017-7494 |
Checks if target machines are vulnerable to the arbitrary shared library load vulnerability CVE-2017-7494. |
| smb-vuln-cve2009-3103 |
Detects Microsoft Windows systems vulnerable to denial of service (CVE-2009-3103). This script will crash the service if it is vulnerable. |
| smb-vuln-ms06-025 |
Detects Microsoft Windows systems with Ras RPC service vulnerable to MS06-025. |
| smb-vuln-ms07-029 |
Detects Microsoft Windows systems with Dns Server RPC vulnerable to MS07-029. |
| smb-vuln-ms08-067 |
Detects Microsoft Windows systems vulnerable to the remote code execution vulnerability known as MS08-067. This check is dangerous and it may crash systems. |
| smb-vuln-ms10-054 |
Tests whether target machines are vulnerable to the ms10-054 SMB remote memory corruption vulnerability. |
| smb-vuln-ms10-061 |
Tests whether target machines are vulnerable to ms10-061 Printer Spooler impersonation vulnerability. |
| smb-vuln-ms17-010 |
Attempts to detect if a Microsoft SMBv1 server is vulnerable to a remote code execution vulnerability (ms17-010, a.k.a. EternalBlue). The vulnerability is actively exploited by WannaCry and Petya ransomware and other malware. |
| smb-vuln-regsvc-dos |
Checks if a Microsoft Windows 2000 system is vulnerable to a crash in regsvc caused by a null pointer dereference. This check will crash the service if it is vulnerable and requires a guest account or higher to work. |
| smb-vuln-webexec |
A critical remote code execution vulnerability exists in WebExService (WebExec). |
| smb-webexec-exploit |
Attempts to run a command via WebExService, using the WebExec vulnerability. Given a Windows account (local or domain), this will start an arbitrary executable with SYSTEM privileges over the SMB protocol. |
| smb2-capabilities |
Attempts to list the supported capabilities in a SMBv2 server for each enabled dialect. |
| smb2-security-mode |
Determines the message signing configuration in SMBv2 servers for all supported dialects. |
| smb2-time |
Attempts to obtain the current system date and the start date of a SMB2 server. |
| smb2-vuln-uptime |
Attempts to detect missing patches in Windows systems by checking the uptime returned during the SMB2 protocol negotiation. |
6. Other programs
Here are collected programs that either did not work during my testing, or were not tested for other reasons.
snarf-mitm
Man-in-the-middle attack engine on SMB/relay.
samba-testsuite
Samba Testing Toolkit
smb-nat
Netbios Audit Tool
smbexec
Psexec style fast attack with samba tools.
smbrelay
Toolkit for attacking SMB/HTTP on an SMB relay.
This is a program for Windows. Website Address: http://www.tarasco.org/security/smbrelay/
NetworkOpenedFiles
NetworkOpenedFiles is a simple tool for Windows that displays the list of all files that are currently opened by other computers on your network. For every opened filename, the following information is displayed: Filename, user name, computer name (On Windows 7/2008 or later), Permissions information (Read/Write/Create), locks count, file owner, file size, file attributes, and more…
Web site: http://www.nirsoft.net/utils/network_opened_files.html
This is a program from NirSoft, that is, it is working. But I did not check it, because the functionality is not very interesting.
smbnetfs
A small C program that mounts Microsoft network neighborhood in one directory.
pdgmail
A dictionary-based password attack tool that targets Windows authentication using the SMB protocol.
sambascan
Allows you to search for a network or a number of hosts network folders SMB. It will also list the contents of the public balloon to be found.
smbbf
Brute-force password smb.
smb4k
Samba Advanced Network Folder Browser (SMB).
smbc
samba-commander is a samba web browser with a curses interface.
Related articles:
- RDP Security Audit (62.8%)
- sshprank: SSH mass-scanner, login cracker and banner grabber (50.6%)
- How to hack routers in Windows (Router Scan by Stas’M manual) (50.4%)
- Best Kali Linux tools in WSL (Windows Subsystem for Linux) (Part 1) (50.2%)
- Pass-the-hash attack (how to use NTLM without cracking a password) (43.1%)
- How to reset MySQL or MariaDB root password on Windows (RANDOM - 0.2%)