NetBIOS: what it is, how it works and how to use in information security
Table of contents
2.2 Datagram distribution service (NetBIOS-DGM)
2.3 Session service (NetBIOS-SSN)
3. NetBIOS name vs Internet host name
6. Wireshark filters for highlighting NetBIOS traffic
8.12 Online scanners on SuIP.biz
Every Windows computer has a computer name. Even if you did not set it, thenthe name generated during the installation of the operating system is written there.
This computer name on the local network can be used as a complete alternative to the local IP address:
- access shares (network folders and printers)
- access running network services (web server, FTP, etc.)
See the article “Windows Computer name: how to change and use” for more details.
It does not require any configuration of the DNS or hosts file, since such name recognition is provided by NetBIOS. We have already encountered NetBIOS, or rather, one of its three services – NBT-NS – in the article “Windows Network Authentication Hacking”. This is one of the services that was used to perform the attack.
That is, NetBIOS is important for Windows, as well as for digging in the Windows architecture, analyzing the network activity of Windows and the security issues of local networks and Windows computers.
Naturally, in the best traditions of Miloserdov.org, the article will contain only the necessary theory and maximum practice – we will ‘probe’ the NetBIOS protocol in Wireshark, the built-in Windows utility and in specialized tools for security auditing. But let's start with the theory.
What is NetBIOS?
NetBIOS is an acronym for Network Basic Input/Output System. It provides services related to the session layer of the OSI model allowing applications on separate computers to communicate over a local area network. As strictly an API, NetBIOS is not a networking protocol. Older operating systems[clarification needed] ran NetBIOS over IEEE 802.2 and IPX/SPX using the NetBIOS Frames (NBF) and NetBIOS over IPX/SPX (NBX) protocols, respectively. In modern networks, NetBIOS normally runs over TCP/IP via the NetBIOS over TCP/IP (NBT) protocol. This results in each computer in the network having both an IP address and a NetBIOS name corresponding to a (possibly different) host name.
Applications can find through NETBIOS the resources they need, establish a connection and send or receive information. NETBIOS uses port 137 for the name service, port 138 for the datagram service, and port 139. For sessions, any session starts with a NETBIOS request, specifying the IP address and determining the TCP port of the remote object, followed by the exchange of NETBIOS messages, after bringing the session to a close. The session exchanges information between two NETBIOS applications. The message length ranges from 0 to 131071 bytes. The simultaneous establishment of several sessions between two objects is acceptable. When organizing IP transport via NETBIOS, the IP datagram is embedded in the NETBIOS packet. Information exchange occurs in this case without establishing a connection between the objects. NETBIOS names must contain IP addresses. So, part of the NETBIOS address can be of the form IP .**.**.**.**, where IP indicates the type of operation (IP via Netbios), and **.**.**.** is an IP- address. NETBIOS system has its own system of commands (call, listen, hang up, send, receive, session status, reset, cancel, adapter status, unlink, remote program load) and primitives for working with datagrams (send datagram, send broadcast datagram, receive datagram , receive broadcast datagram). All NETBIOS end nodes are divided into three types:
- broadcast (“b”) nodes
- point-to-point nodes (“p”);
- nodes of the mixed type ("m").
An IP address can be associated with one of these types. B-nodes communicate with their partner through broadcast requests. P and M nodes use netbios name server (NBNS) and datagram distribution server (NBDD) for this purpose.
NetBIOS Services
NetBIOS provides three distinct services:
- Name service (NetBIOS-NS) for name registration and resolution.
- Datagram distribution service (NetBIOS-DGM) for connectionless communication.
- Session service (NetBIOS-SSN) for connection-oriented communication.
(Note: SMB, an upper layer, is a service that runs on top of the Session Service and the Datagram service, and is not to be confused as a necessary and integral part of NetBIOS itself. It can now run atop TCP with a small adaptation layer that adds a packet length to each SMB message; this is necessary because TCP only provides a byte-stream service with no notion of packet boundaries.)
Name service (NetBIOS-NS)
In order to start sessions or distribute datagrams, an application must register its NetBIOS name using the name service. NetBIOS names are 16 octets in length and vary based on the particular implementation. Frequently, the 16th octet, called the NetBIOS Suffix, designates the type of resource, and can be used to tell other applications what type of services the system offers. In NBT, the name service operates on UDP port 137 (TCP port 137 can also be used, but rarely is).
The name service primitives offered by NetBIOS are:
- Add name – registers a NetBIOS name.
- Add group name – registers a NetBIOS "group" name.
- Delete name – un-registers a NetBIOS name or group name.
- Find name – looks up a NetBIOS name on the network.
NetBIOS name resolution is not supported by Microsoft for Internet Protocol Version 6 (IPv6).
Datagram distribution service (NetBIOS-DGM)
Datagram mode is connectionless; the application is responsible for error detection and recovery. In NBT, the datagram service runs on UDP port 138.
The datagram service primitives offered by NetBIOS are:
- Send Datagram – send a datagram to a remote NetBIOS name.
- Send Broadcast Datagram – send a datagram to all NetBIOS names on the network.
- Receive Datagram – wait for a packet to arrive from a Send Datagram operation.
- Receive Broadcast Datagram – wait for a packet to arrive from a Send Broadcast Datagram operation.
Session service (NetBIOS-SSN)
Session mode lets two computers establish a connection, allows messages to span multiple packets, and provides error detection and recovery. In NBT, the session service runs on TCP port 139.
The session service primitives offered by NetBIOS are:
- Call – opens a session to a remote NetBIOS name.
- Listen – listen for attempts to open a session to a NetBIOS name.
- Hang Up – close a session.
- Send – sends a packet to the computer on the other end of a session.
- Send No Ack – like Send, but doesn't require an acknowledgment.
- Receive – wait for a packet to arrive from a Send on the other end of a session.
In the original protocol used to implement NetworkBIOS services on PC-Network, to establish a session, the initiating computer sends an Open request which is answered by an Open acknowledgment. The computer that started the session will then send a Session Request packet which will prompt either a Session Accept or Session Reject packet.
During an established session, each transmitted packet is answered by either a positive-acknowledgment (ACK) or negative-acknowledgment (NAK) response. A NAK will prompt retransmission of the data. Sessions are closed by the non-initiating computer by sending a close request. The computer that started the session will reply with a close response which prompts the final session closed packet.
NetBIOS name vs Internet host name
When NetBIOS is run in conjunction with Internet protocols (e.g., NBT), each computer may have multiple names: one or more NetBIOS name service names and one or more Internet host names.
NetBIOS name
The NetBIOS name is 16 ASCII characters, however Microsoft limits the host name to 15 characters and reserves the 16th character as a NetBIOS Suffix. This suffix describes the service or name record type such as host record, master browser record, or domain controller record or other services. The host name (or short host name) is specified when Windows networking is installed/configured, the suffixes registered are determined by the individual services supplied by the host. In order to connect to a computer running TCP/IP via its NetBIOS name, the name must be resolved to a network address. Today this is usually an IP address (the NetBIOS name to IP address resolution is often done by either broadcasts or a WINS Server – NetBIOS Name Server). A computer's NetBIOS name is often the same as that computer's host name (see below), although truncated to 15 characters, but it may also be completely different.
NetBIOS names are a sequence of alphanumeric characters. The following characters are explicitly not permitted: \/:*?"<>|. Since Windows 2000, NetBIOS names also had to comply with restrictions on DNS names: they cannot consist entirely of digits, and the hyphen ("-") or full-stop (".") characters may not appear as the first or last character. Since Windows 2000, Microsoft has advised against including any full-stop (".") characters in NetBIOS names, such that applications can use the presence of a full-stop to distinguish domain names from NetBIOS names.
The Windows LMHOSTS file provides a NetBIOS name resolution method that can be used for small networks that do not use a WINS server.
Internet host name
A Windows machine's NetBIOS name is not to be confused with the computer's Internet host name (assuming that the computer is also an Internet host in addition to being a NetBIOS node, which need not necessarily be the case). Generally a computer running Internet protocols (whether it is a Windows machine or not) usually has a host name (also sometimes called a machine name). Originally these names were stored in and provided by a hosts file but today most such names are part of the hierarchical Domain Name System (DNS).
Generally the host name of a Windows computer is based on the NetBIOS name plus the Primary DNS Suffix, which are both set in the System Properties dialog box. There may also be connection-specific suffixes which can be viewed or changed on the DNS tab in Control Panel → Network → TCP/IP → Advanced Properties. Host names are used by applications such as telnet, ftp, web browsers, etc. To connect to a computer running the TCP/IP protocol using its name, the host name must be resolved into an IP address, typically by a DNS server. (It is also possible to operate many TCP/IP-based applications, including the three listed above, using only IP addresses, but this is not the norm.)
How to detect NetBIOS
You can run a regular scan of TCP ports on a LAN using nmap:
sudo nmap _gateway/24
And among the results you can find open TCP port 139:
139/tcp open netbios-ssn
If we are only interested in NetBIOS services, then it’s enough to look for UDP ports 137 and 138 and TCP ports 137 and 139, use Nmap usage tips and compose this command:
sudo nmap -p U:137,138,T:137,139 -sU -sS _gateway/24
The advantage of this approach is that scanning is much faster and additional open UDP ports are found.
You can use another Nmap usage tip to collect service banners, for this we add the -sV --script=banner options:
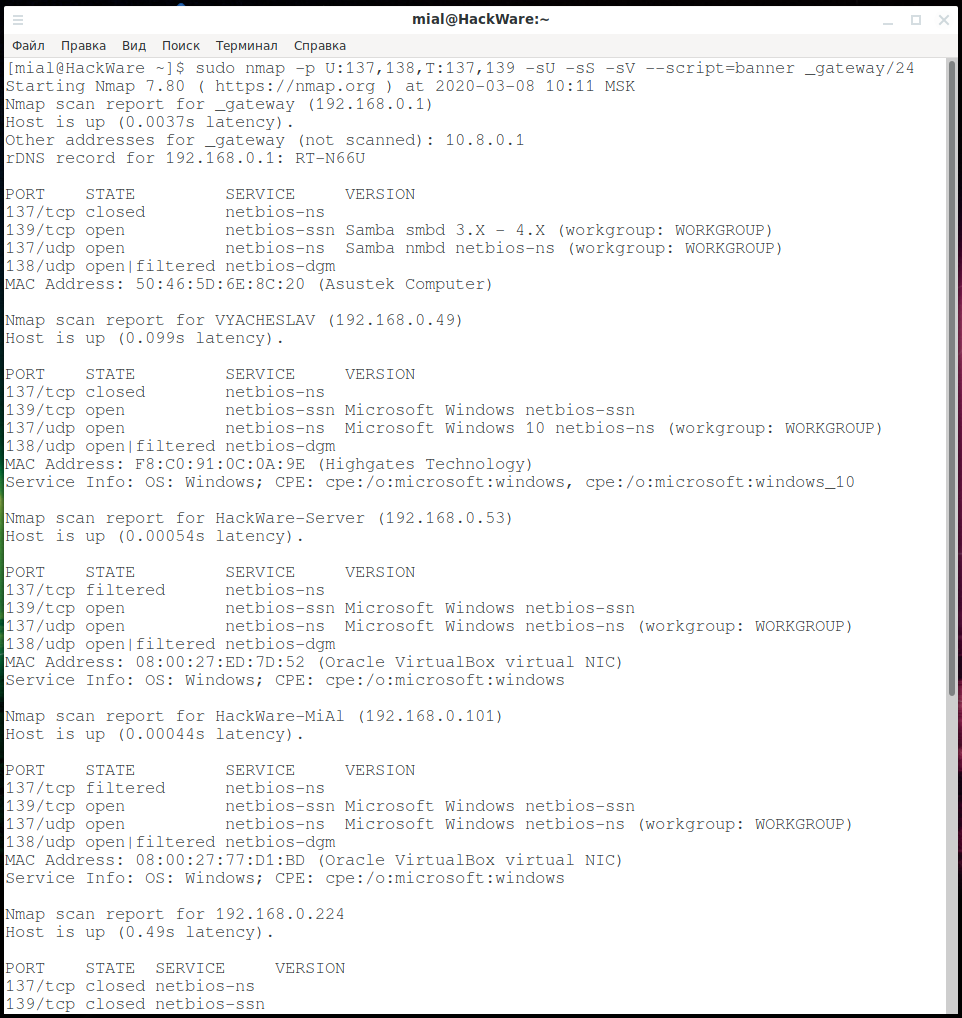
sudo nmap -p U:137,138,T:137,139 -sU -sS -sV --script=banner _gateway/24
Thanks to the last command, we additionally discovered:
- used workgroup (WORKGROUP)
- operating system for some devices (Windows 10)
- some open ports are associated with Samba smbd 3.X - 4.X
Additionally, you can use Nmap scripts (NSE) – I found 4 scripts that are related to NetBIOS:
nbd-info
Displays protocol and block device information from NBD servers.
nbstat
Attempts to retrieve the target's NetBIOS names and MAC address.
broadcast-netbios-master-browser
Attempts to discover master browsers and the domains they manage.
nbns-interfaces
Retrieves IP addresses of the target's network interfaces via NetBIOS NS. Additional network interfaces may reveal more information about the target, including finding paths to hidden non-routed networks via multihomed systems.
To use them during a scan, the command is approximately the following:
sudo nmap -p U:137,138,T:137,139 -sU -sS --script nbstat,nbd-info,broadcast-netbios-master-browser,nbns-interfaces _gateway/24
Results:
nbtstat
The nbtstat program is designed to display NetBIOS protocol statistics and current TCP/IP connections using NBT (NetBIOS over TCP/IP). The nbtstat program is preinstalled on Windows, that is, it does not need to be downloaded and installed, but it must be run on the command line. See “How to set up the PowerShell environment on Windows and Linux”.
Usage:
NBTSTAT [ [-a RemoteName] [-A IP address] [-c] [-n]
[-r] [-R] [-RR] [-s] [-S] [interval] ]
Options:
-a (adapter status) Lists the remote machine's name table given its name
-A (Adapter status) Lists the remote machine's name table given its
IP address.
-c (cache) Lists NBT's cache of remote [machine] names and their IP addresses
-n (names) Lists local NetBIOS names.
-r (resolved) Lists names resolved by broadcast and via WINS
-R (Reload) Purges and reloads the remote cache name table
-S (Sessions) Lists sessions table with the destination IP addresses
-s (sessions) Lists sessions table converting destination IP
addresses to computer NETBIOS names.
-RR (ReleaseRefresh) Sends Name Release packets to WINS and then, starts Refresh
RemoteName Remote host machine name.
IP address Dotted decimal representation of the IP address.
interval Redisplays selected statistics, pausing interval seconds
between each display. Press Ctrl+C to stop redisplaying
statistics.
Let’s consider examples of using nbtstat.
To find out the host name by IP address, use the -A option:
nbtstat -A 192.168.0.53
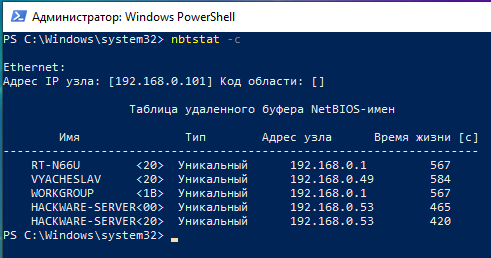
To view the names of computers and their IPs stored in the cache use the -c option:
nbtstat -c
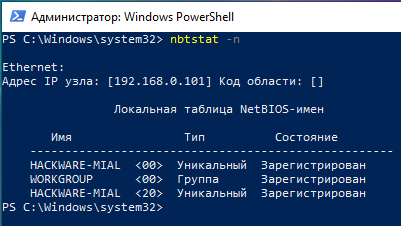
To find out the name of the current computer use nbtstat with the -n option:
nbtstat -n
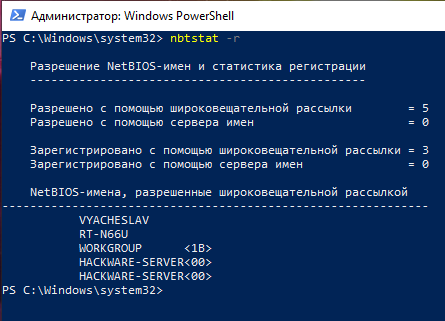
To list names resolved by broadcast and via WINS run the command:
nbtstat -r
Wireshark filters for highlighting NetBIOS traffic
Wireshark supports almost all network protocols (see “Wireshark Filters”), including NetBIOS protocols.
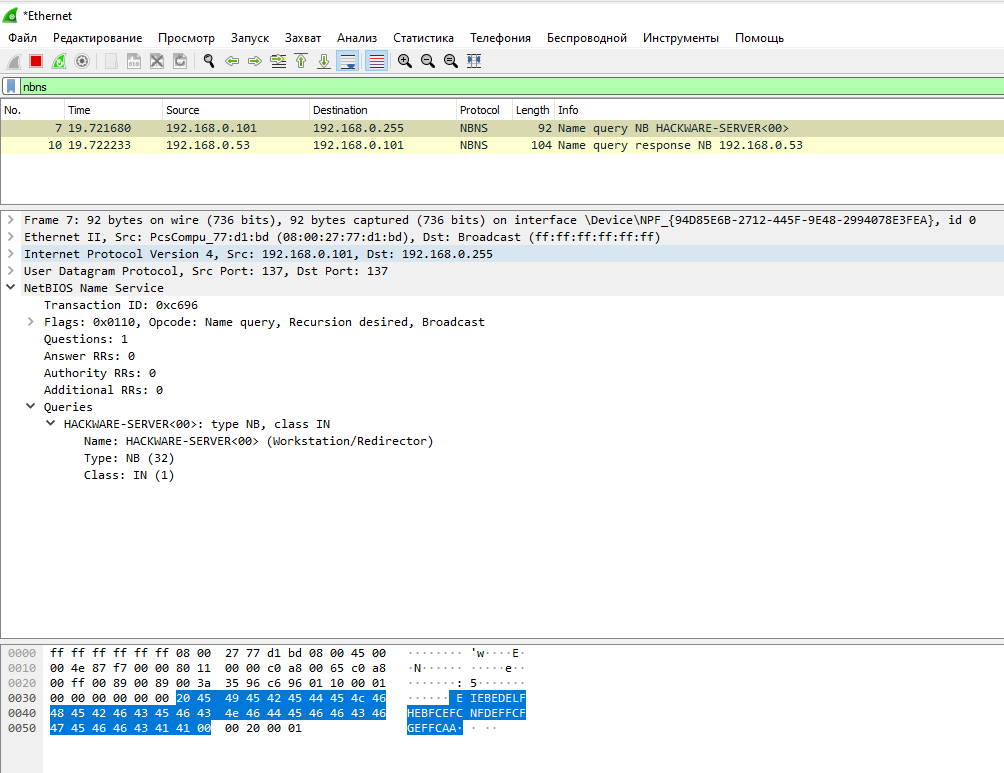
Wireshark Filter for Name Service (NetBIOS-NS):
nbns
A broadcast request to determine the IP address by computer name:
Received response:
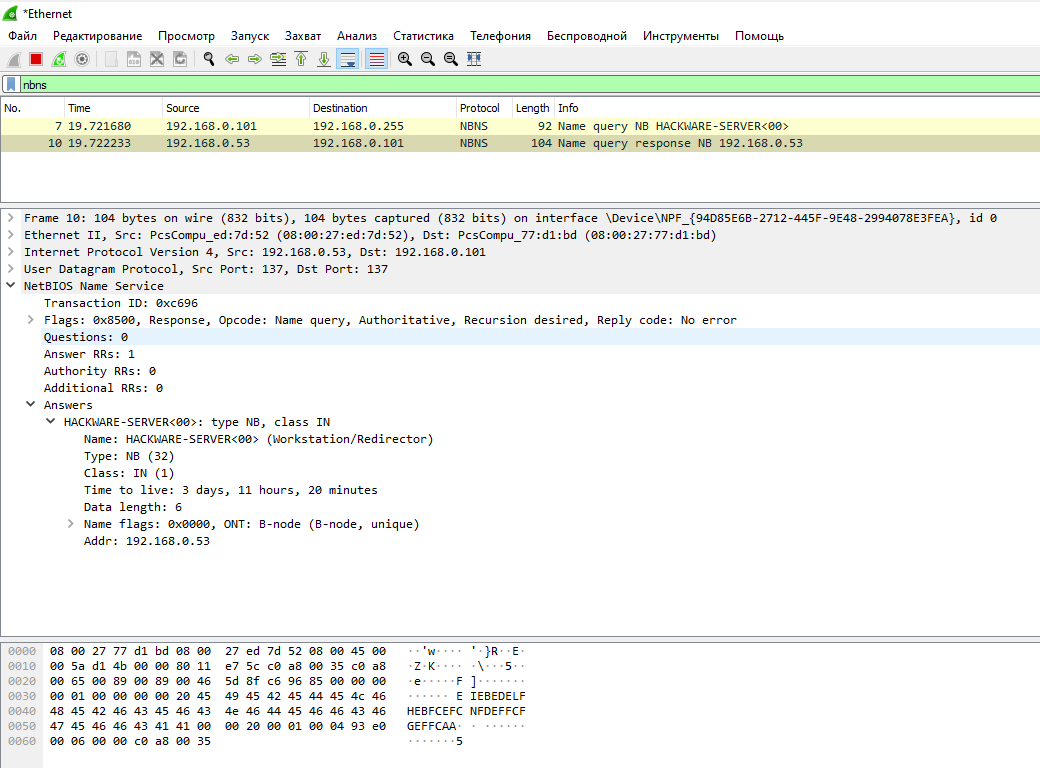
A request to a specific host to obtain its host name:
Received response:
Wireshark Filter for Datagram Distribution Service (NetBIOS-DGM):
nbdgm
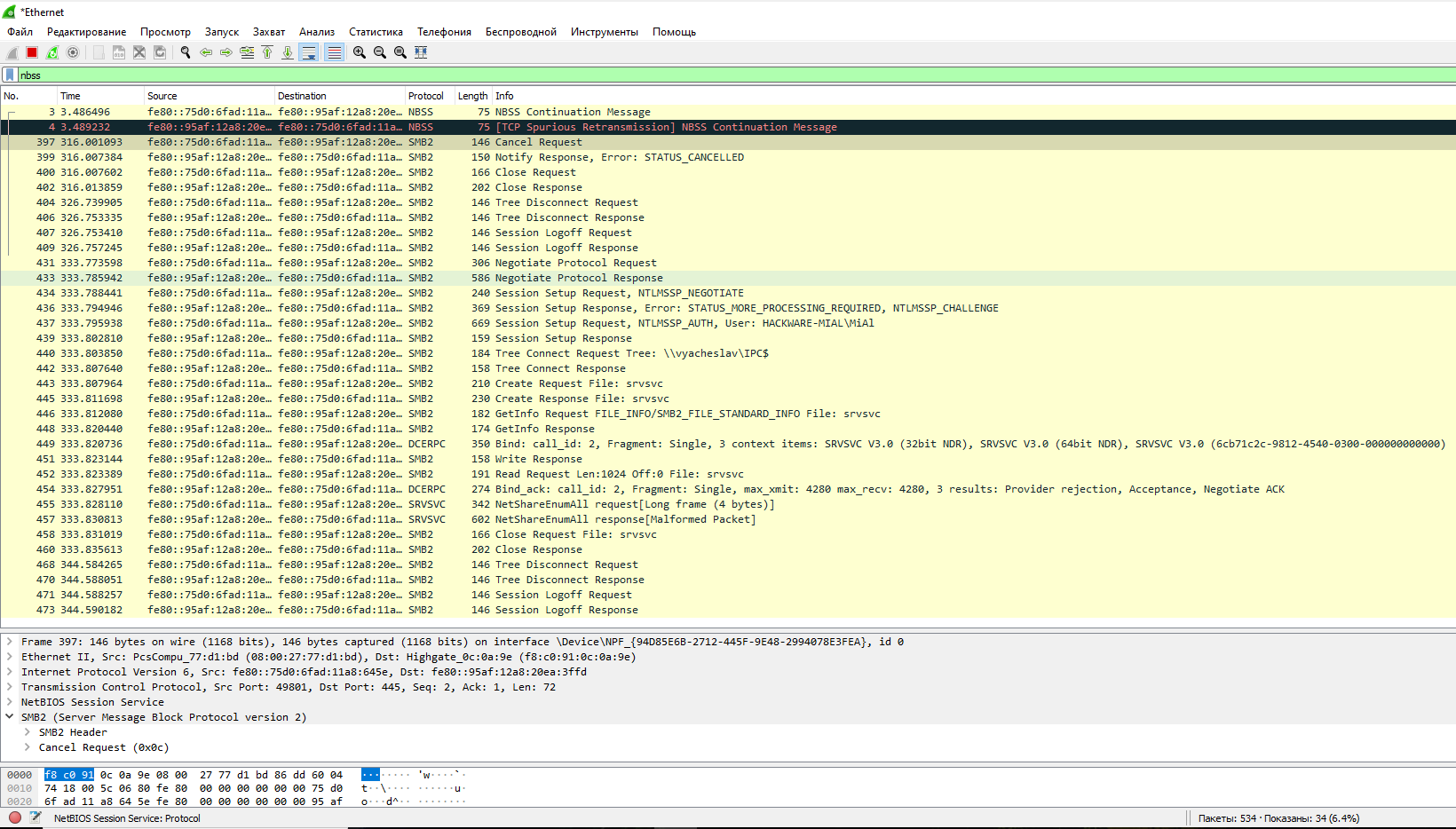
Wireshark Filter for Session Service (NetBIOS-SSN):
nbss
To filter all NetBIOS traffic:
nbns or nbdgm or nbss
LMHOSTS file
The LMHOSTS (LAN Manager Hosts) file is used to enable Domain Name Resolution under Windows when other methods, such as WINS, fail. It is used in conjunction with workgroups and domains. If you are looking for a simple, general mechanism for the local specification of IP addresses for specific hostnames (server names), use the HOSTS file, not the LMHOSTS file.
The file, if it exists, is read as the LMHOSTS setting file. A sample file (lmhosts.sam) is provided. It contains documentation for manually configuring the file.
File Locations: in Windows NT 4.0, Windows 2000, Windows XP, Vista, 7, 8, 10, Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2016+ the file is located in %windir%\system32\drivers\etc\, and a sample file (lmhosts.sam) is installed here. Note that %windir% is an environment variable pointing to the Windows installation directory, usually C:\Windows.
The syntax for the LMHOSTS file is the same as for HOSTS, i.e.:
IP_ADDRESS HOST_NAME
NetBIOS exploitation
NetBIOS security audit program can be divided into 2 groups:
- NetBIOS spoofing to perform man-in-the-middle attacks
- NetBIOS scan to collect information
The programs for scanning NetBIOS are mostly abandoned, since almost all information (name, IP, MAC address) can be gathered either by the standard Windows utility or by the Nmap scanner.
As for NetBIOS spoofing tools, there are quite a few mordern programs among them, usually including spoofing of NetBIOS services as part of a complex attack.
The following is a brief overview of the tools, since the scanning tools are too simple to talk about them much, and the spoofing tools are too complex to be considered in this article – each of them deserves its own article or even a few tutorials on their various functions.
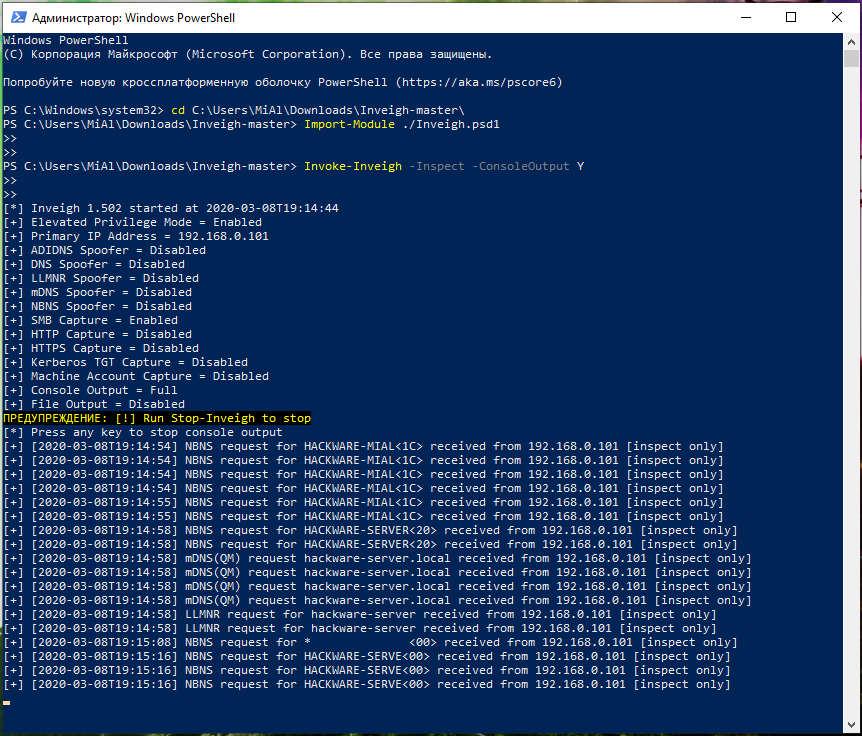
Invoke-inveigh
Inveigh is a PowerShell ADIDNS/LLMNR/NBNS/mDNS/DNS spoofer and a man-in-the-middle attack tool designed to help penetration testers/red timers that are limited to Windows.
Inveigh tutorials are being prepared for this program for Miloserdov.org website.
An example of starting an inspectation without attack:
Import-Module ./Inveigh.psd1 Invoke-Inveigh -Inspect -ConsoleOutput Y
Response
Responder is a tool for performing a man-in-the-middle attack against authentication methods in Windows. This program includes the LLMNR, NBT-NS and MDNS poisoner, thanks to which traffic is redirected with requests and authentication hashes. The program also includes HTTP/SMB/MSSQL/FTP/LDAP authentication rogue servers that support authentication methods such as NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and basic HTTP authentication, for which the Responder acts as a relay.
Detailed instructions for using the Responder ‘Windows Network Authentication Hacking’.
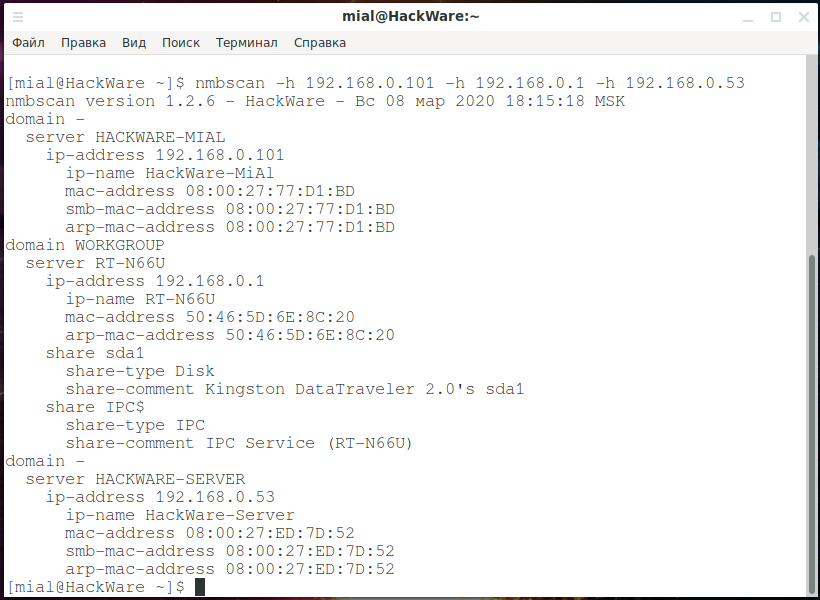
NMBscan
NMBscan scans the shares of a SMB/NetBIOS network, using the NMB/SMB/NetBIOS protocols. It is useful for acquiring information on a local area network for such purposes as security auditing.
It can obtain such information as NMB/SMB/NetBIOS/Windows hostname, IP address, IP hostname, ethernet MAC address, Windows username, NMB/SMB/NetBIOS/Windows domain name, and master browser.
It can discover all the NMB/SMB/NetBIOS/Windows hosts on a local area network by using the hosts lists maintained by master browsers.
Installation manual: https://en.kali.tools/?p=1736
Launch Example:
nmbscan -h 192.168.0.101 -h 192.168.0.1 -h 192.168.0.53
To scan a subnet (very slow):
nmbscan -h 192.168.0.{1..255}
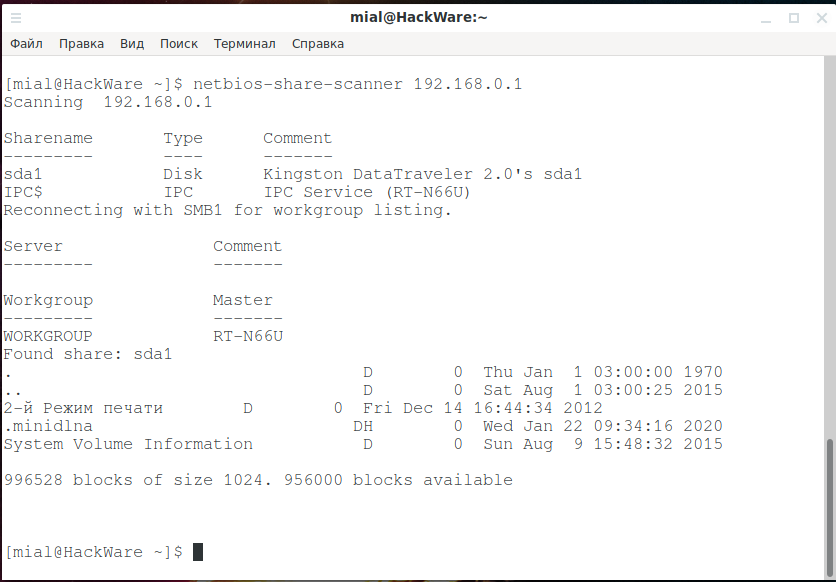
NetBIOS Share Scanner
NetBIOS Share Scanner can be used to check Windows workstations and servers if they have available shared resources.
Launch Example:
netbios-share-scanner 192.168.0.1
Installation manual, as well as additional examples of use: https://en.kali.tools/?p=1729
NBTscan
NBTscan is an IP scanning program for retrieving NetBIOS name information.
Scans the whole 192.168.1.0/24 network:
nbtscan -r 192.168.1.0/24

Installation manual, as well as additional examples of use: https://en.kali.tools/?p=1723

nbtscan-unixwiz
nbtscan-unixwiz is a command line tool that scans for open NETBIOS name servers on a local or remote TCP/IP network, the first step in finding open shares. It is based on the functionality of the standard Windows nbtstat tool, but it can work not only with a single address, but also with a range of addresses.
The tool has a version for Windows and Linux.
Scan a range of IP addresses (192.168.0.100-110) without performing reverse name resolutions (-n):
nbtscan-unixwiz -n 192.168.0.100-110
Scan the specified IP addresses (192.168.1.36 192.168.1.60 192.168.1.61 192.168.1.63), display all received information (-f), make 3 attempts per IP address (-t 3):
nbtscan-unixwiz -f -t 3 192.168.1.36 192.168.1.60 192.168.1.61 192.168.1.63

Installation manual, as well as additional examples of use: https://en.kali.tools/?p=1744
fakenetbios
A family of tools designed to simulate Windows hosts (NetBIOS) on a LAN (local area network).
Link: https://github.com/mubix/FakeNetBIOS
nbnspoof
NetBIOS Services Name Spoofer.
The source code of the program (written in Python2).
nbtenum
A utility for Windows that can be used to list NetBIOS information from a single host or range of hosts. To run on Windows.
Source code: http://dl.packetstormsecurity.net/Win/NBTEnum33.zip
nbtool
Several tools for exploring, attacking and communicating with NetBIOS and DNS.
Link: https://wiki.skullsecurity.org/Nbtool
nbname
Decodes and displays all the names of NetBIOS packets received on UDP port 137 and more! To run on Windows.
Link: ftp://ftp.mrynet.com/operatingsystems/DEC/vmsone/vmsone.com/~decuslib/vmssig/vmslt01b/net/nbname.exe
The last program did not work for me.
Online scanners on SuIP.biz
The NetBIOS, SMB (NetBIOS) and Samba (Linux) online scanner uses a number of the tools described above to collect primary information on NetBIOS and SMB (Samba). It is enough to specify the IP address of the target and several tools will start scanning at once, which will show the version of running services, the computer name and workgroup (domain), try to perform an anonymous login and show shared folders if they are available.



Related articles:
- VNC Security Audit (78.4%)
- Introduction to IPv6 Addresses: How to Use and How to Explore the Network (Part 2) (68%)
- How to use PsExec tools to run commands and manage remote Windows systems (65.7%)
- Windows Computer name: how to change and use (61.6%)
- How to switch between Internet connections in Windows (54.8%)
- Kali Linux Meta-packages (RANDOM - 50%)







Really Cool and informative