How to check WordPress sites for vulnerabilities (WPScan)
What is specific in vulnerability search on web sites powered by WordPress?
Every web site, using popular content management systems, such as WordPress, has basically the same source code (scripts). This code has already been tested many times. Therefore, using general-purpose scanners for searching, for example, SQL injection, XSS and other popular vulnerabilities in WordPress, is unlikely to give results, as it has already been done many times before us.
Nevertheless, security researchers regularly find vulnerabilities in both the main WordPress code, and in its numerous plug-ins, the themes of the design. This means that you do not need to scan WordPress by general-purpose vulnerability scanner, instead you should use a specialized program.
WPScan is a program to search vulnerability on web sites powered by WordPress
The best program for scanning WordPress is WPScan. This tool is able to determine the version of WordPress, as well as what plug-ins and themes are used, which versions. WPScan has an extensive and up-to-date vulnerability database of these plug-ins and themes. So by comparing the data obtained by scanning with this database, the program tells us about the vulnerabilities that are present on the site under investigation.
How to install WPScan
WPScan is preinstalled in Kali Linux and BlackArch. But if you do not use these operating systems, then you can install WPScan on Linux Mint or in Ubuntu. To do this, run the following commands:
sudo apt update sudo apt install libcurl4-openssl-dev libxml2 libxml2-dev libxslt1-dev ruby-dev build-essential libgmp-dev zlib1g-dev git git clone https://github.com/wpscanteam/wpscan.git cd wpscan sudo gem install bundler && sudo bundle install --without test ./wpscan.rb --help
How to use WPScan
You need to start with updating the database:
sudo wpscan --update
Note: if WPScan was preinstalled in you Linux distro (Kali Linux, BlackArch), you should start your command with wpscan. But if you installed WPScan manually, you should start your command with ./wpscan.rb instead.
WPScan contains several options, you can see the full list on this page: https://en.kali.tools/?p=282
To set the target address, use the -u option, after which you need to specify the site to scan.
Vulnerable can be:
- WordPress itself
- installed plugins
- installed themes
In addition, if you know the names of users, this information can be used for phishing attacks or for brute force (brute-force passwords).
Choosing which information we want to get (plug-ins, themes) is done by the -e flag. After it, you can specify additional options (note: they are used without a dash). These include:
u usernames from id 1 to 10
u[10-20] usernames from id 10 to 20 (you must write [] chars)
p plugins
vp only vulnerable plugins
ap all plugins (can take a long time)
tt timthumbs
t themes
vt only vulnerable themes
at all themes (can take a long time)
Multiple values are allowed : "-e tt,p" will enumerate timthumbs and plugins
If no option is supplied, the default is "vt,tt,u,vp"
For example, if I want to get to know the list of plugins (p), scan only vulnerable themes (vt), and get a list of users (u), my command looks like this:
wpscan -u web_site_URL -e p,vt,u
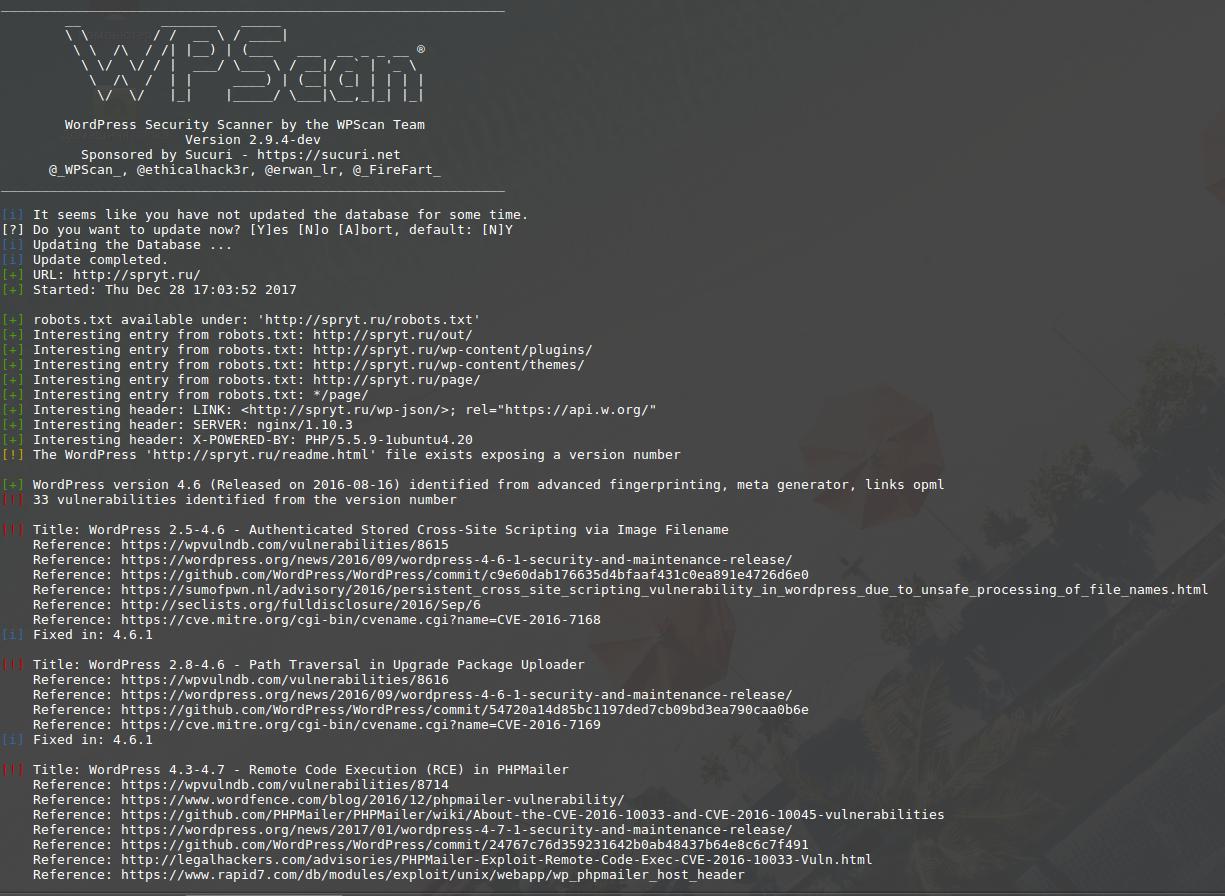
Report example:
The report begins with a list of interesting records from the robots.txt file, interesting headers (can contain data about the server software) and the version of WordPress.
If the version of WordPress is vulnerable, it lists all known vulnerabilities, they indicate the version numbers in which WordPress is susceptible to attack, and versions where the vulnerability is fixed. Also links to additional information are given.
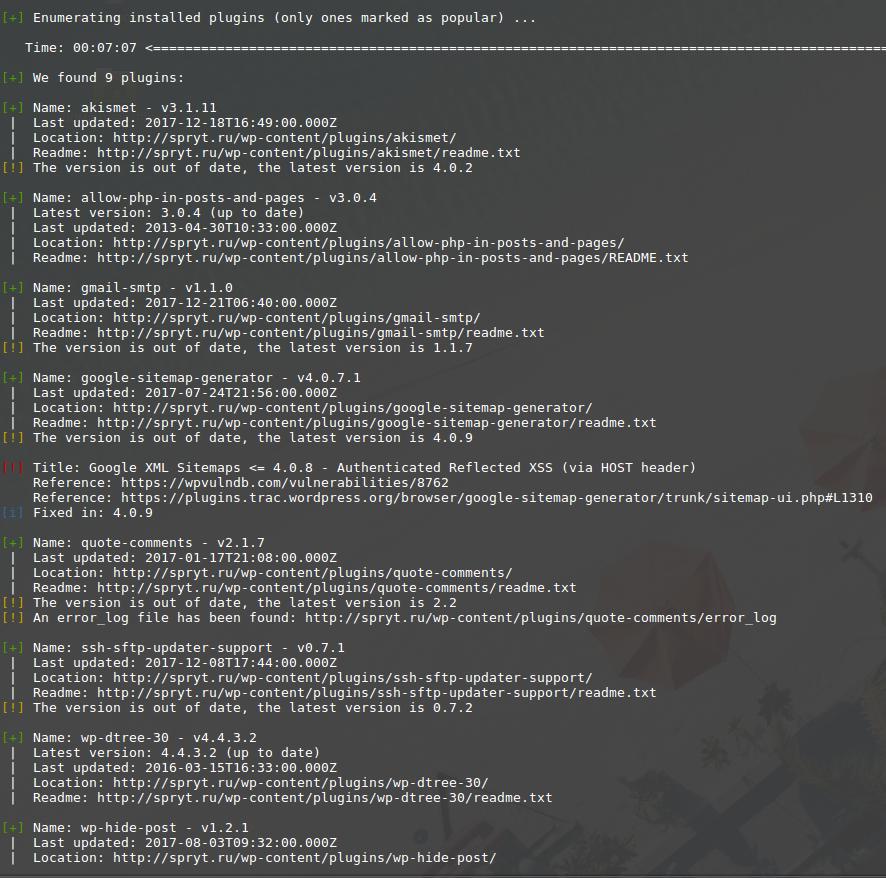
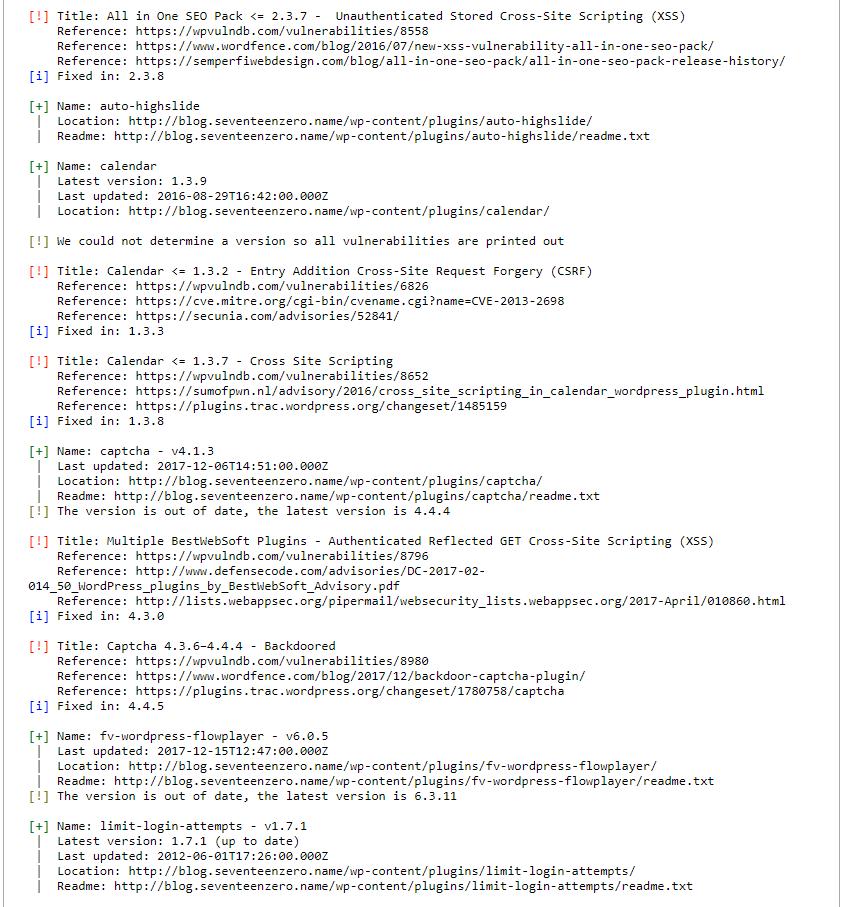
Next comes the list of installed plugins:
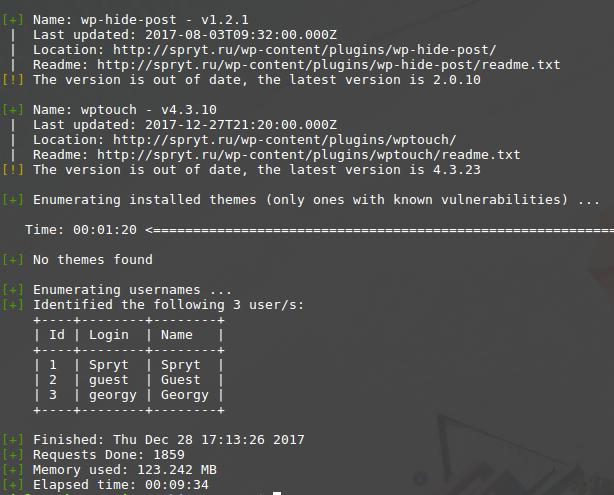
If the plugin known as vulnerable, then information about this vulnerability is displayed. If the version of the plug-in could not be determined, then information about all the vulnerable versions is displayed. Also links to additional information are given.
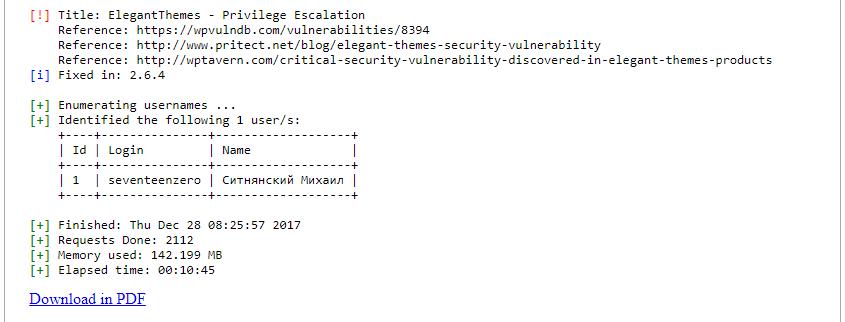
At the very end the names of users are shown to us:
If you find a vulnerable plug-in or theme on your site, then update them as quickly as possible. If there are no updates for them, the best solution is to remove them as soon as possible.
Free online vulnerability search service in WordPress (WPScan online)
WPScan does not work on Windows. Therefore, if you want to scan your site but can not cope with Linux, then you can use the following free online service for scanning WordPress with WPScan:. There you just enter the address of your site and wait for the scan to finish (10-20 minutes).
Example of a scan report: https://suip.biz/?act=report&id=051259e552d3cb579178acf64c0c960b
You can download your report in PDF to your computer for further analyze. Example of a report in PDF: https://suip.biz/?act=report&id=051259e552d3cb579178acf64c0c960b&pdf
Related articles:
- 5 free and simple steps to secure WordPress web sites (100%)
- How to Install and run WPScan on Windows (100%)
- JavaScript Attacks: how to bypass Social Locker for WordPress (CASE) (100%)
- Best Kali Linux tools in WSL (Windows Subsystem for Linux) (Part 1) (100%)
- Anonymous scanning through Tor with Nmap, sqlmap or WPScan (50%)
- badKarma: Advanced Network Reconnaissance Assistant (RANDOM - 50%)