How to change MAC address in Linux, how to enable and disable automatic MAC change (spoofing) in Linux
About what a MAC address is and how to view it has already been discussed in the article “How to find the MAC address and How to find the manufacturer by MAC address”.
In this article, we will look at how to change (spoof) the MAC address on your Linux computer, as well as how to disable automatic spoofing of the MAC address.
Why change your MAC address?
The MAC address is (must be) unique for each network interface. By the way, if a device has several network interfaces, then each of them has its own MAC address. For example, laptops have at least two network interfaces: wired and Wi-Fi – each of them has a MAC address. With desktop computers, the situation is usually the same. That is, when we talk about “changing the MAC address”, then you need to understand that there are several of these addresses. By the way, a router or a switch has a unique MAC address for each port, if the device supports wireless networks, then each wireless interface (2.4 GHz and 5 GHz) also has its own MAC address.
So, since the MAC address must be unique, it allows you to uniquely identify the network device. And since this network device is part of your computer, it allows you to uniquely identify your computer. Moreover, the MAC address (also called the hardware, physical address) does not change when the operating system is changed (reinstalled, for example) – it is burned into the network interface.
It is understandable for a hacker to want to hide his MAC address – to prevent the possibility of proving his identity with the person who carried out the attack, but why would ordinary users hide (spoof) their true MAC? For me personally, the answer to this question is not obvious. But the problem, apparently, is important, since in the new Android and iOS firmware, the MAC address is constantly spoofed, i.e. is replaced with a fake one, and new MAC addresses are constantly generated for the same device.
So, in short, the spoofing of the MAC address is needed so that it is not possible to track and identify the device by its MAC address. This is a very real problem, for example, using iSniff-GPS, you can track the previous geographic locations of devices.
But there is a more important reason (than paranoia) to learn about MAC addresses and about ways to spoof or prohibit changes in your system. Based on MAC addresses, user authentication can be performed when connecting through the Captive Portal.
Related: Fast and simple method to bypass Captive Portal (hotspot with authorization on the web-interface)
A few words about the Captive Portal. This is a way to force the user to comply with certain conditions for providing access to the Internet. You can most often come across examples of Captive Portals in public places that provide Internet access services via Wi-Fi to an indefinite circle of persons, but who want to identify the user and/or allow access only to persons with credentials. For example, at the airport, you may need to verify your phone number via SMS to access the free Wi-Fi network. The hotel will provide you with a login and password to access the Internet via Wi-Fi – this ensures that only hotel clients can use Wi-Fi services. This also includes cases of providing access to the global network on a commercial basis.
Due to the peculiarities of the Captive Portals, user identification is performed based on MAC addresses. And starting with NetworkManager 1.4.0 (a popular program for managing network connections in Linux), there is now automatic spoofing of MAC addresses. And in case of incorrect configuration, you may face the problem of Internet access performed through the Captive Portal. There may also be problems with configured MAC filtering in the router.
Well, for hackers, of course, there are reasons to change the MAC-address: for example, to pretend to be another user, and use his open access to the magical world of the Internet via Captive Portals, or to increase anonymity.
Who can see my MAC address?
The MAC address is used to transfer data on the local network. That is, it is not transmitted when connecting to websites and when accessing the global network. There are exceptions though: some vulnerabilities allow someone not on your local network to find out your MAC address (some Nmap scripts can do this).
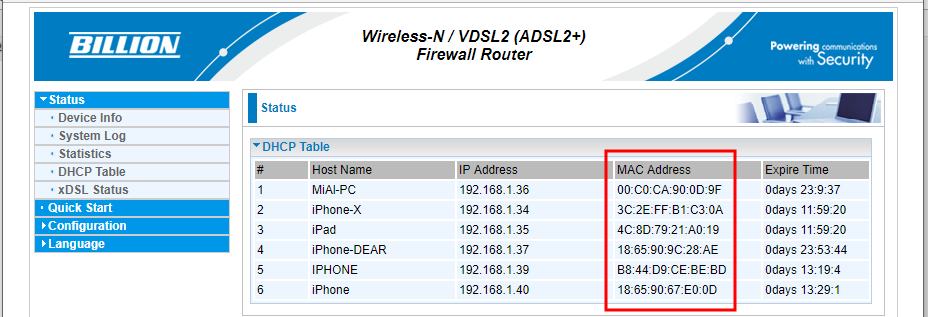
That is, if you connect to the router via a local network, then the router knows your MAC address (and can keep a log of connections, including storing the MAC address), but if you open a site on the Internet, then the site owner cannot find out your MAC address…
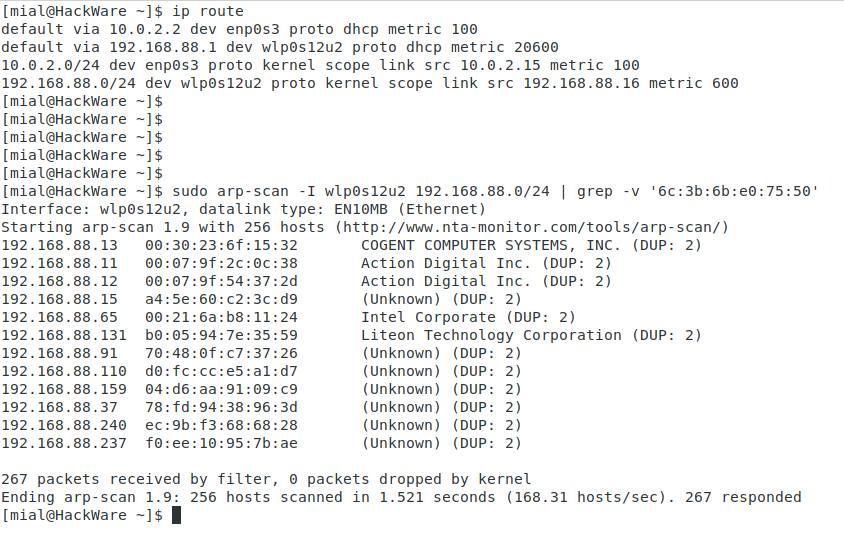
All devices on the local network can see each other's MAC addresses (there are many scanners that can get this data). An example of a local network scan done with arp-scan:
A slightly different situation with wireless network interfaces. If you are connected to an access point (router), then all the rules of the local network work: the router and other devices can find out your MAC address. But also anyone who is within range of your Wi-Fi signal (phone, laptop) can find out your MAC address.
Spoofing (hiding) MAC addresses in NetworkManager
NetworkManager can remap MAC set by other programs
Starting with NetworkManager 1.4.0, this program supports MAC spoofing and has many different options.
In order for us to understand them, we need to understand some concepts.
First, there are network adapters:
- wired (ethernet);
- wireless (wifi).
MAC rules are configured separately for each group.
Second, a wireless adapter can be in two states:
- scan (search, not connected to the network), it is set using the wifi.scan-rand-mac-address property, by default set to “yes”, which means that it sets an arbitrary MAC address during scanning. Another valid value is “no”;
- connected to the network, it is set using the wifi.cloned-mac-address property, the default is “preserve”.
The following values (modes) are available for the wired interface (set by the ethernet.cloned-mac-address property) and the wireless interface in the connected state (set by the wifi.cloned-mac-address property):
- an explicitly specified MAC address (i.e. you can write down the desired value that will be assigned to the network interface)
- permanent: use the burned MAC address
- preserve: do not change the MAC address of the device after activation (for example, if the MAC was changed by another program, then the current address will be used)
- random: generate a random value for each connection
- stable: similar to random – i.e. generate a random value for each connection, BUT when connecting to the same network, the same value will be generated
- NULL/Unset: This is the default value that allows you to roll back to the global default. If no global settings are set, then NetworkManager rolls back to “preserve”.
If you are trying to change the MAC in other ways and you are not successful, it is quite possible that NetworkManager is to blame, which changes the MAC according to its own rules. Since most Linux distributions with a graphical interface have NetworkManager installed and running by default, in order to solve your problem, you must first understand how NetworkManager works and by what rules.
NetworkManager configuration files
NetworkManager configuration, including MAC related settings, can be done in the /etc/NetworkManager/NetworkManager.conf file or by adding an additional .conf file to the /etc/NetworkManager/conf.d directory (the .conf file can have any name). The second option is highly recommended, because when upgrading NetworkManager usually replaces the main .conf file and if you make changes to /etc/NetworkManager/NetworkManager.conf, the settings you made will be overwritten (lost).
How to disable changing MAC address in Kali Linux
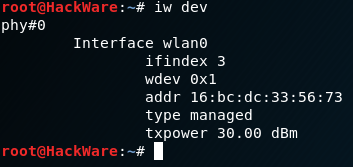
If you connect a wireless card to Kali Linux and check the properties of the wireless interface with the command:
iw dev
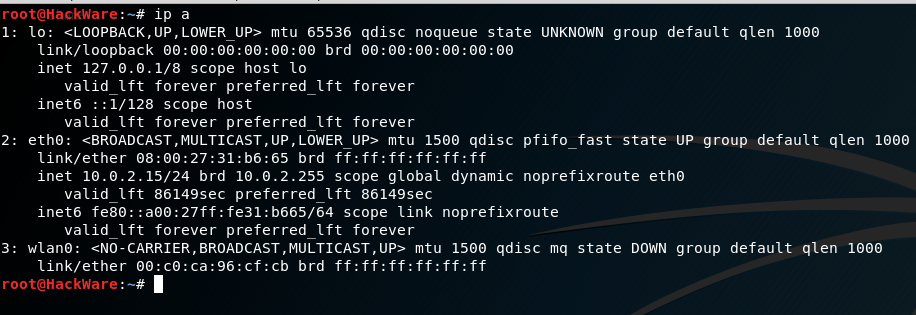
then you will see that the MAC address is different from the one written on the wireless adapter (you can also check here and make sure that the displayed hardware address does not match the manufacturer of the device).
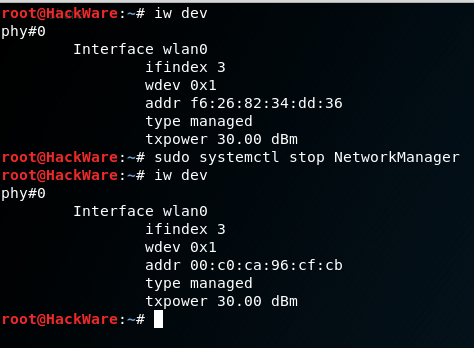
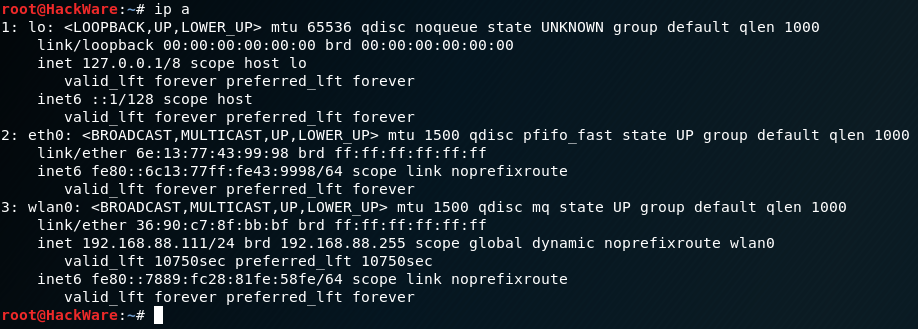
We already know that NetworkManager, by default, substitutes the hardware address during scanning, but uses the permanent MAC (if you did not change it, then it uses the true address burned into the device) when connecting. We connect to any network and see our true address. We disconnect from the network and again see that the address has been changed to a random one:
This is not some special Kali Linux feature, this is the default behavior of NetworkManager with default settings.
If you want to change this behavior, there are two ways:
- configure NetworkManager
- disable NetworkManager and use other methods to connect
If you stop NetworkManager:
sudo systemctl stop NetworkManager
Then MAC stops being replaced:
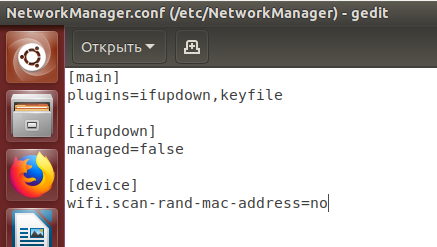
If you want to make sure that the MAC does not change when NetworkManager is running, then create a file /etc/NetworkManager/conf.d/mac.conf
sudo gedit /etc/NetworkManager/conf.d/mac.conf
And add the lines there:
[device] wifi.scan-rand-mac-address=no
Restart the NetworkManager service:
sudo systemctl restart NetworkManager
Now, even on an unconnected adapter, the MAC does not change:
How to make the MAC change every time you connect in Kali Linux
If you want the MAC address to be changed every time you connect, but at the same time the same MAC is used when connecting to the same network, then in the file /etc/NetworkManager/conf.d/mac.conf:
sudo gedit /etc/NetworkManager/conf.d/mac.conf
Add the lines:
[connection] ethernet.cloned-mac-address=stable wifi.cloned-mac-address=stable
The ethernet.cloned-mac-address and wifi.cloned-mac-address lines can be added individually or together.
Let's check the current values:
ip link
Let's restart the service:
sudo systemctl restart NetworkManager
Let's connect to wired and wireless networks. Now let's check the MAC values again:
As you can see, the MAC for both wired and wireless interfaces have been tampered with.
As already mentioned, the same addresses will be generated for the same networks, if you want different MACs every time, even for the same networks, then the lines should look like this:
[connection] ethernet.cloned-mac-address=random wifi.cloned-mac-address=random
How to set up automatic MAC spoofing in Ubuntu and Linux Mint
Ubuntu and Linux Mint use versions of NetworkManager that support automatic MAC address spoofing. However, if you connect your Wi-Fi card to Ubuntu or Linux Mint, you will see a real MAC. This is because the /etc/NetworkManager/NetworkManager.conf file says not to spoof:
To change this, open the file:
sudo gedit /etc/NetworkManager/NetworkManager.conf
And remove the lines:
[device] wifi.scan-rand-mac-address=no
or comment them out to look like this:
#[device] #wifi.scan-rand-mac-address=no
or change no to yes:
[device] wifi.scan-rand-mac-address=yes
And restart NetworkManager:
sudo systemctl restart NetworkManager
Similarly, you can add lines to spoof MAC (these settings create a new address for each connection, but when connecting to the same networks, the same address is used):
[connection] ethernet.cloned-mac-address=stable wifi.cloned-mac-address=stable
How to set a specific MAC address
Open the file /etc/NetworkManager/conf.d/mac.conf
sudo gedit /etc/NetworkManager/conf.d/mac.conf
If you want to change the MAC for the wired connection, then add the lines:
[connection] ethernet.cloned-mac-address=NEW_MAC
If you want to change the MAC for the wireless connection, then add the lines:
[connection] wifi.cloned-mac-address=NEW_MAC
Note: replace NEW_MAC with the actual desired MAC address.
If you want to change the MAC for both wired and wireless connections, you can use both entries at once:
[connection] ethernet.cloned-mac-address=NEW_MAC wifi.cloned-mac-address=NEW_MAC2
Please note that the peculiarity of this method is that the MAC changes only after connecting to the network. Before connecting to networks, the interfaces will have their original MAC addresses. Except, possibly, the Wi-Fi interface, since, as already described earlier, MAC spoofing is set for it by default. To cancel spoofing, as mentioned earlier, add the following lines to the config file:
[device] wifi.scan-rand-mac-address=no
For the changes to take effect, restart the service:
sudo systemctl restart NetworkManager
Programs to change the MAC address
NetworkManager is not the only one able to change the MAC address – in fact, there are quite a few ways to do this, including using specialized programs and system services. Some of these methods will be discussed below. So that we can track the results made, NetworkManager is configured as follows:
[device] wifi.scan-rand-mac-address=no
With these lines, we tell NetworkManager not to spoof the MAC when scanning wireless networks.
Since the ethernet.cloned-mac-address and wifi.cloned-mac-address parameters are missing in the NetworkManager settings, the default value “preserve” will be used, which sets the current MAC address to be used for connections, even if it has been changed by other programs.
I will perform the following examples in Kali Linux. I will change the settings for the Wi-Fi adapter.
The peculiarity of the subsequent methods is that the changes are lost after a system reboot, or after disconnecting-connecting the device to the computer.
Changing MAC with iproute2
We will use the ip program which is included in the iproute2 package.
Let's start by checking the current MAC address with the command:
ip link show INTERFACE_NAME
Where INTERFACE_NAME is the name of the specific network interface that you want to view. If you do not know the name, or want to see all the interfaces, then the command can be run like this:
ip link show
At the moment we are interested in the part that follows “link/ether” and represents the 6-byte number. It will look something like this:
link/ether 00:c0:ca:96:cf:cb
The first step in spoofing a MAC address is to put the interface down. This is done with the command:
sudo ip link set dev INTERFACE_NAME down
Where INTERFACE_NAME replace with the real name. In my case, this is wlan0, then the real command looks like this:
sudo ip link set dev wlan0 down
Next, we go directly to MAC spoofing. Any hexadecimal value can be used, but some networks may be configured not to assign IP addresses to clients whose MAC address does not match any known vendor. In these cases, so that you can successfully connect to the network, use any real vendor's MAC prefix (the first three bytes) and use arbitrary values for the next three bytes.
To change the MAC, we need to run the command:
sudo ip link set dev INTERFACE_NAME address XX:XX:XX:XX:XX:XX
Where XX:XX:XX:XX:XX:XX is the desired new MAC.
For example, I want to set the hardware address EC:9B:F3:68:68:28 for my adapter, then the command looks like this:
sudo ip link set dev wlan0 address EC:9B:F3:68:68:28
The final step is to return the interface to the up state. This can be done with a command like:
sudo ip link set dev INTERFACE_NAME up
For my system, the real command is:
sudo ip link set dev wlan0 up
If you want to check if the MAC has really changed, just run the command again:
ip link show INTERFACE_NAME
The value after “link/ether” should be the one you set.
Change MAC with macchanger
Another method is using macchanger (also known as the GNU MAC Changer). This program offers various functions, such as changing the address so that it matches a specific manufacturer, or completely randomizing it.
Install macchanger – it is usually present in the official repositories and is installed by default in Kali Linux.
At the moment of changing the MAC, the device should not be used (be connected in any way, or have an up status). To set an interface down:
sudo ip link set dev INTERFACE down
For spoofing, you need to specify the name of the interface, in each next command replace wlan0 with the name of the interface whose MAC you want to change.
To find out the MAC values, run the command with the -s option:
macchanger -s wlan0
It will output something like:
Current MAC: 00:c0:ca:96:cf:cb (ALFA, INC.) Permanent MAC: 00:c0:ca:96:cf:cb (ALFA, INC.)
The line “Current MAC” means the address at the moment, and “Permanent MAC” means the permanent (real) address.
To spoof a MAC address to a completely arbitrary address (option -r):
sudo macchanger -r wlan0
The following will be displayed:
Current MAC: 00:c0:ca:96:cf:cb (ALFA, INC.) Permanent MAC: 00:c0:ca:96:cf:cb (ALFA, INC.) New MAC: 66:98:08:45:c5:de (unknown)
The first two lines have already been explained, the line “New MAC” means a new address.
To randomize only the bytes that determine the uniqueness of the device, the current MAC address (i.e. if you check the MAC address, it will be registered as from the same vendor), run the command (option -e):
sudo macchanger -e wlan0
To set the MAC address to a specific value, run:
sudo macchanger --mac=XX:XX:XX:XX:XX:XX wlan0
Here XX:XX:XX:XX:XX:XX is the MAC you want to change to.
Finally, to return the MAC address to the original, constant value burned-in in the hardware (option -p):
sudo macchanger -p wlan0
After changing the MAC address, return the network interface to the up state:
sudo ip link set dev INTERFACE up
To list all known vendors and their MAC addresses:
macchanger -l
To list all vendors with the string “Intel” in their name:
macchanger --list=Intel
Conclusion
Once again I will draw your attention to the fact that since NetworkManager is present and works by default in most distributions with a graphical interface, then if you cannot change the address, or, on the contrary, an unexpected change of address occurs, then first of all refer to the NetworkManager settings, since on most distributions, this service is enabled by default.
Currently NetworkManager provides quite a lot of MAC spoofing capabilities, including changing to a random address, or to a specific one. A special feature of NetworkManager is the division into “scan” and “connected” modes, i.e. you may not see that the settings you made have already taken effect until you connect to any network. NetworkManager supports masked MAC address generation (not covered in this article).
If after changing the MAC you have connection problems (you cannot connect to networks – wired or wireless), then this means that the network has a prohibition to connect with MAC from an unknown vendor (manufacturer). In this case, you need to use the first three octets (bytes) of any real vendor, the remaining three octets can be arbitrary.
Related: Why does VirtualBox lose connection when changing MAC address (SOLVED)
Related articles:
- Linux Wi-Fi Cheat Sheet: Tips and Troubleshooting (45%)
- Alfa AWUS052NH – Kali Linux Compatible USB Adapter (37.8%)
- Best Kali Linux Compatible USB Wi-Fi adapters 2018 (37.8%)
- How to increase TX-Power of Wi-Fi adapters in Kali Linux (37.8%)
- USB Wi-Fi Adapters with monitor mode and wireless injection (100% compatible with Kali Linux) 2022 (37.8%)
- What to select: Tor, VPN, or proxy? (RANDOM - 13.6%)